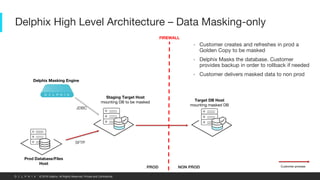
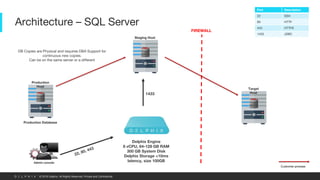
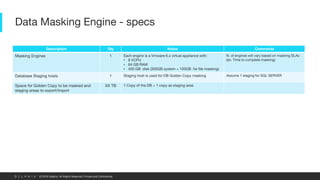
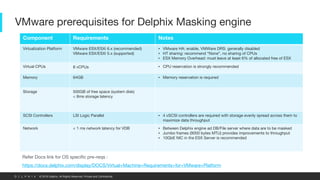
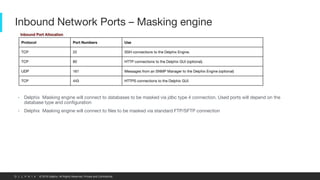
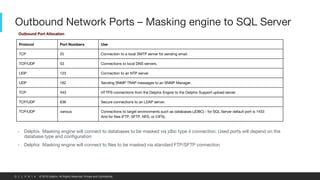
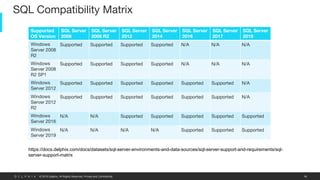
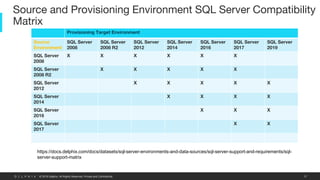
This document provides an overview of a proposed data masking architecture using Delphix. It includes diagrams of the high-level architecture and data flow. The key components are a production database, Delphix masking engine, and non-production target database. The process involves creating a golden copy of the production data, masking it using the Delphix engine, and delivering the masked data to non-production. It also provides specifications for the masking engines, prerequisites, networking requirements, and best practices for configuring masking jobs and optimizing performance.