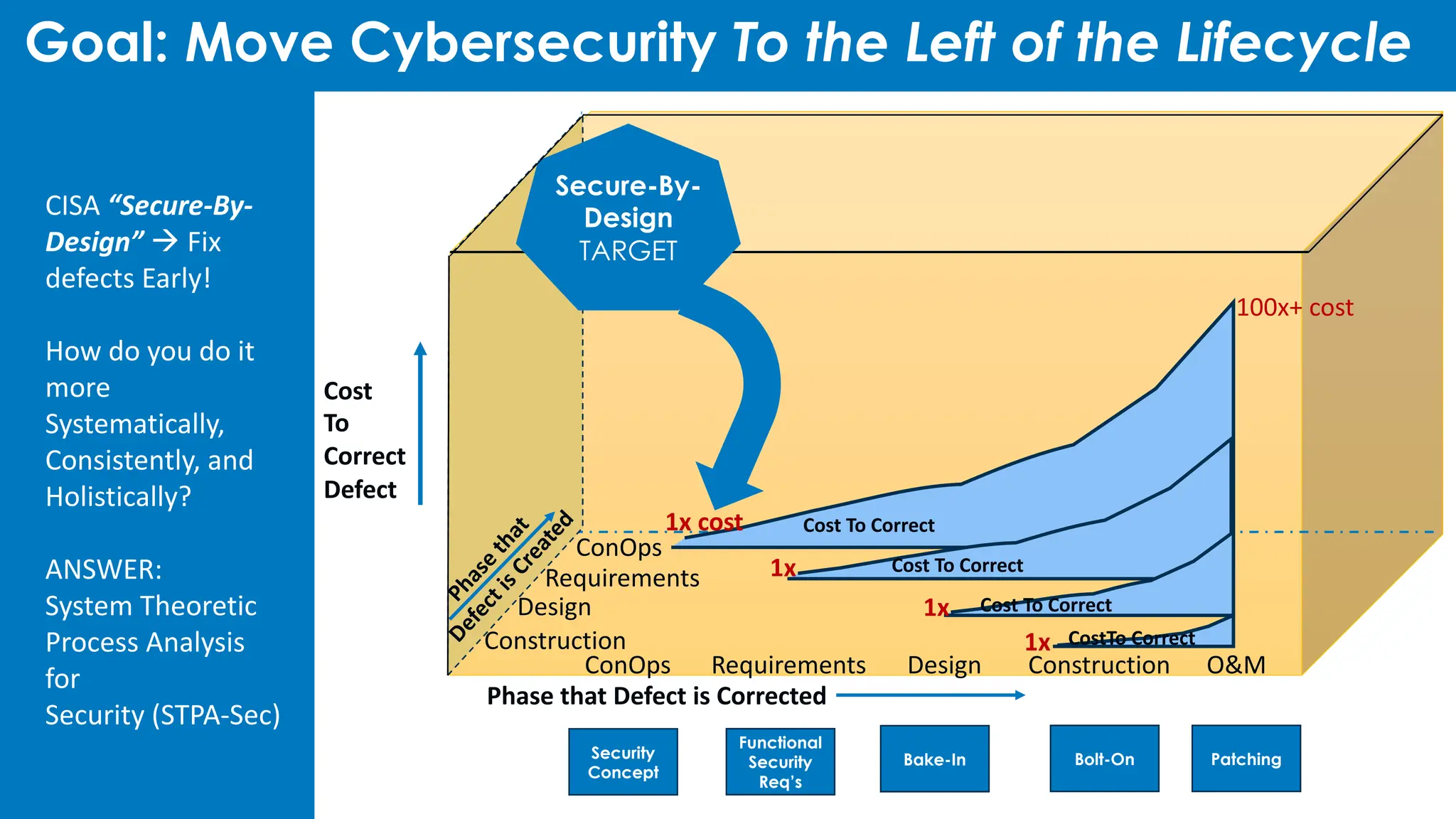
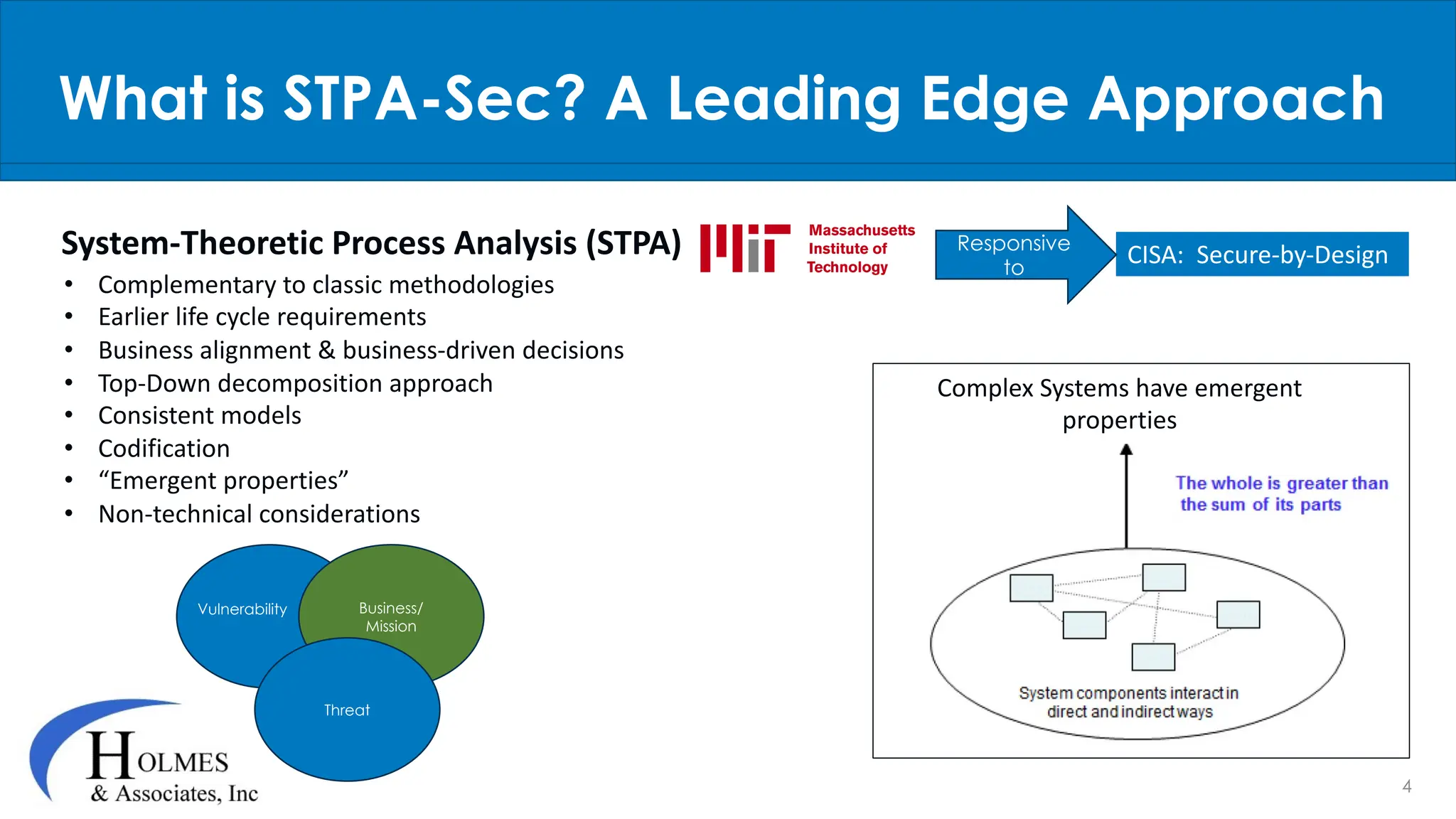
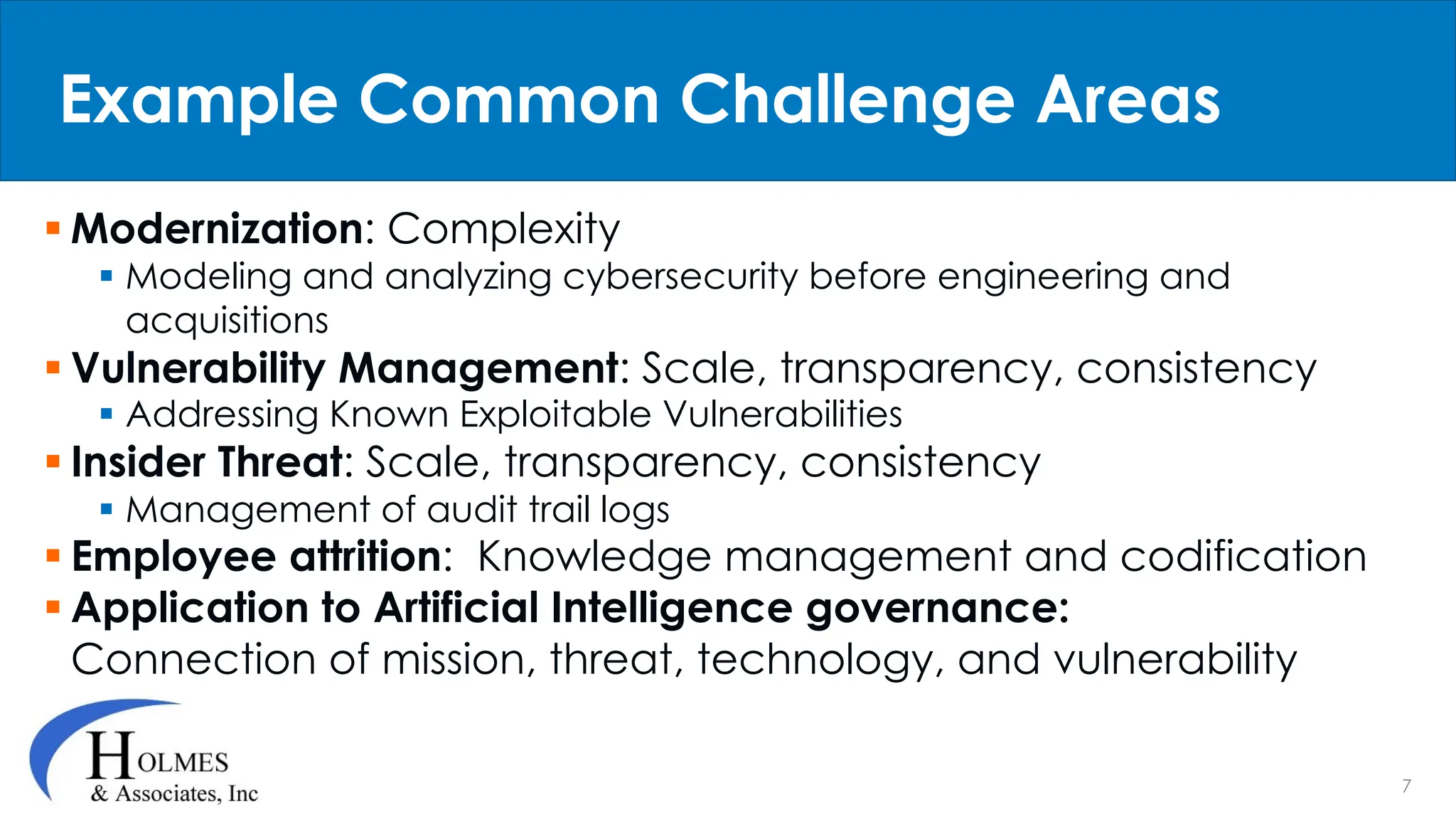
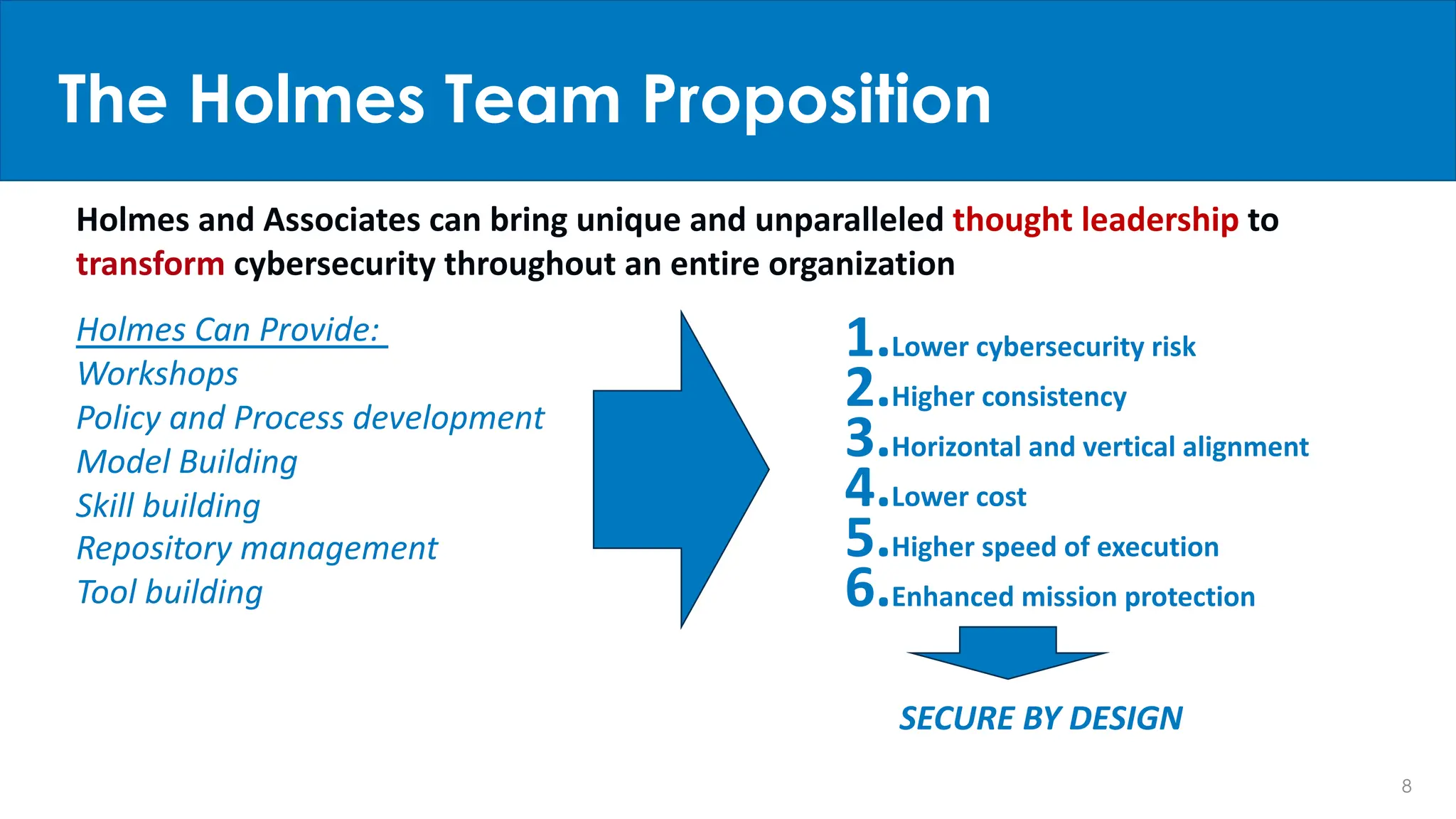
Holmes and Associates, Inc. emphasizes the importance of incorporating cybersecurity earlier in the lifecycle through their methodology, STPA-SEC, which seeks to reduce costs and vulnerabilities effectively. The firm draws on significant experience, including its application to high-profile Air Force programs, to position cybersecurity as a systematic and holistic aspect of organizational transformation. Their services aim to lower cybersecurity risks and improve consistency, speed, and mission protection through workshops and strategic policy development.