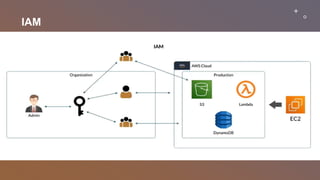
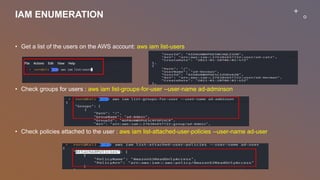
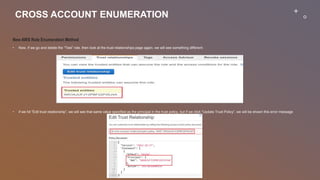
This document provides an overview of penetration testing on AWS environments. It discusses the key areas to focus on when penetration testing AWS infrastructure and applications, including external infrastructure, applications, internal infrastructure, and AWS configurations. It also outlines services that can be tested without prior approval and limitations on testing AWS-managed infrastructure. The document then covers starting penetration testing activities, accessing AWS with IAM credentials, enumerating IAM users, groups, and policies, and new methods for enumerating cross-account roles between AWS accounts.