Embed presentation

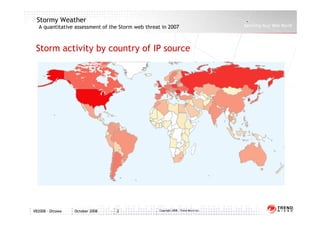








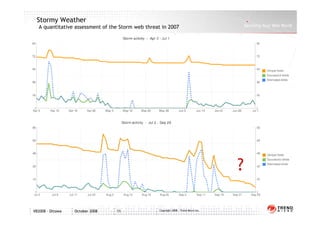


This document analyzes the Storm botnet threat in 2007. It describes how Storm infects computers through malicious email attachments and website visits, turning the computers into remotely controlled "botnets". The botnets are then rented out to generate spam emails and launch denial-of-service attacks. Storm also sells personal data mined from infected computers. To avoid detection, Storm uses rootkits, regular code updates, and techniques like decentralized control and frequent code replacement. The document lists several Storm outbreaks in 2007 and includes graphs showing spam volume and the country of origin for Storm-infected IP addresses.











