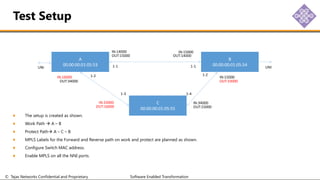
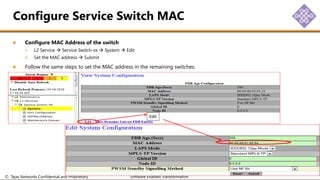
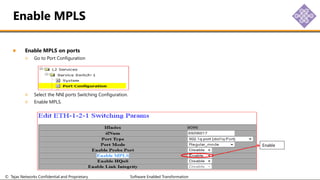
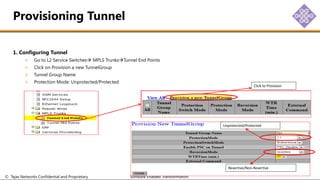
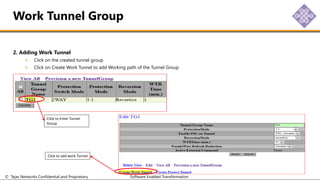
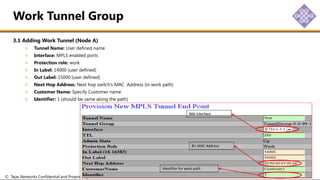
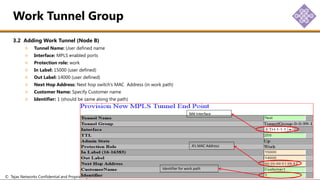
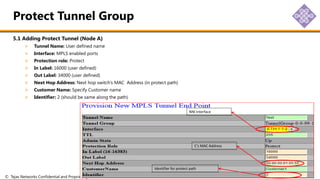
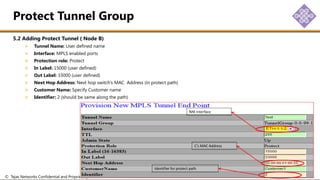
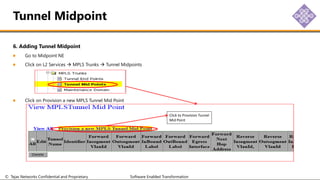
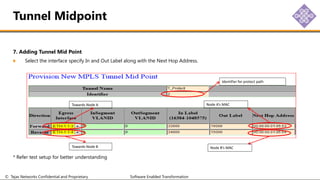
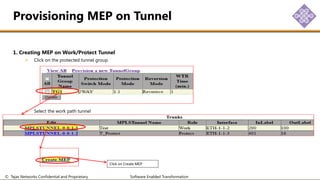
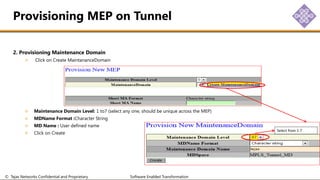
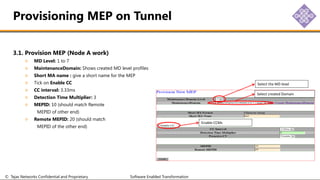
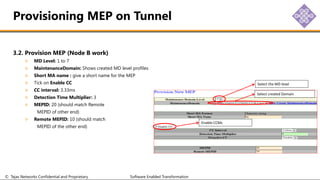
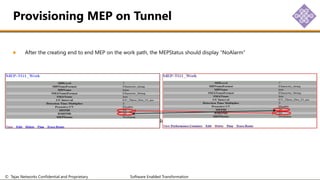
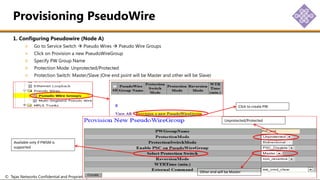
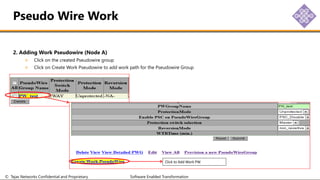
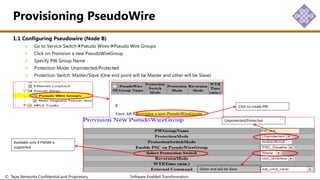
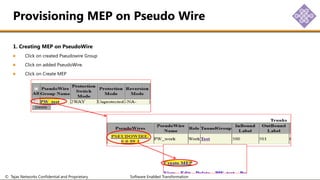
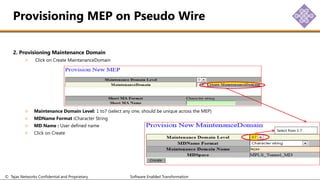
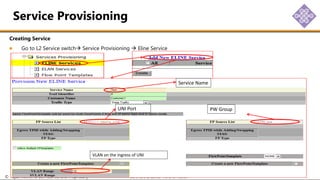
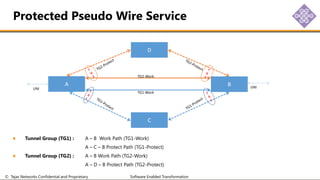
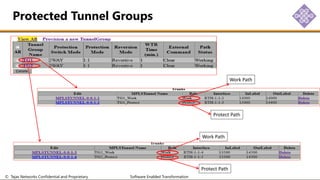
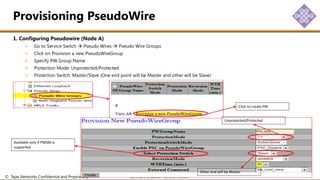
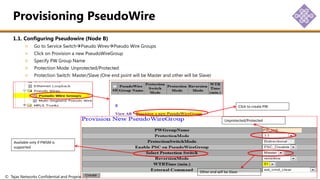
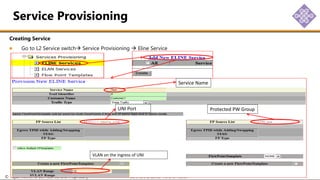
The document outlines the procedures for configuring MPLS tunneling, establishing maintenance endpoints (MEPs), and provisioning pseudowires in a network setup involving multiple nodes. It provides detailed steps for creating work and protect tunnels, configuring MAC addresses, and setting up service switches and pseudowires, ensuring redundancy and service reliability. The emphasis is on maintaining consistent identifiers across the network to ensure proper service provisioning and monitoring.