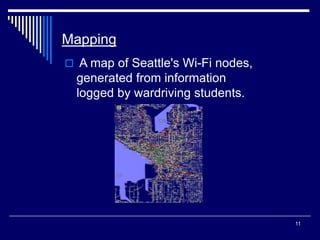
WarDriving involves using a vehicle or walking to detect and map wireless networks in an area. It originated from the term "WarDialing" which was popularized in the movie WarGames. A typical WarDriver uses a laptop or PDA equipped with wireless detection software like NetStumbler, MiniStumbler, or Kismet to passively detect network access points and log their locations. The results are often mapped to analyze wireless security issues and raise awareness, though some legal questions remain about temporarily associating with networks without permission.