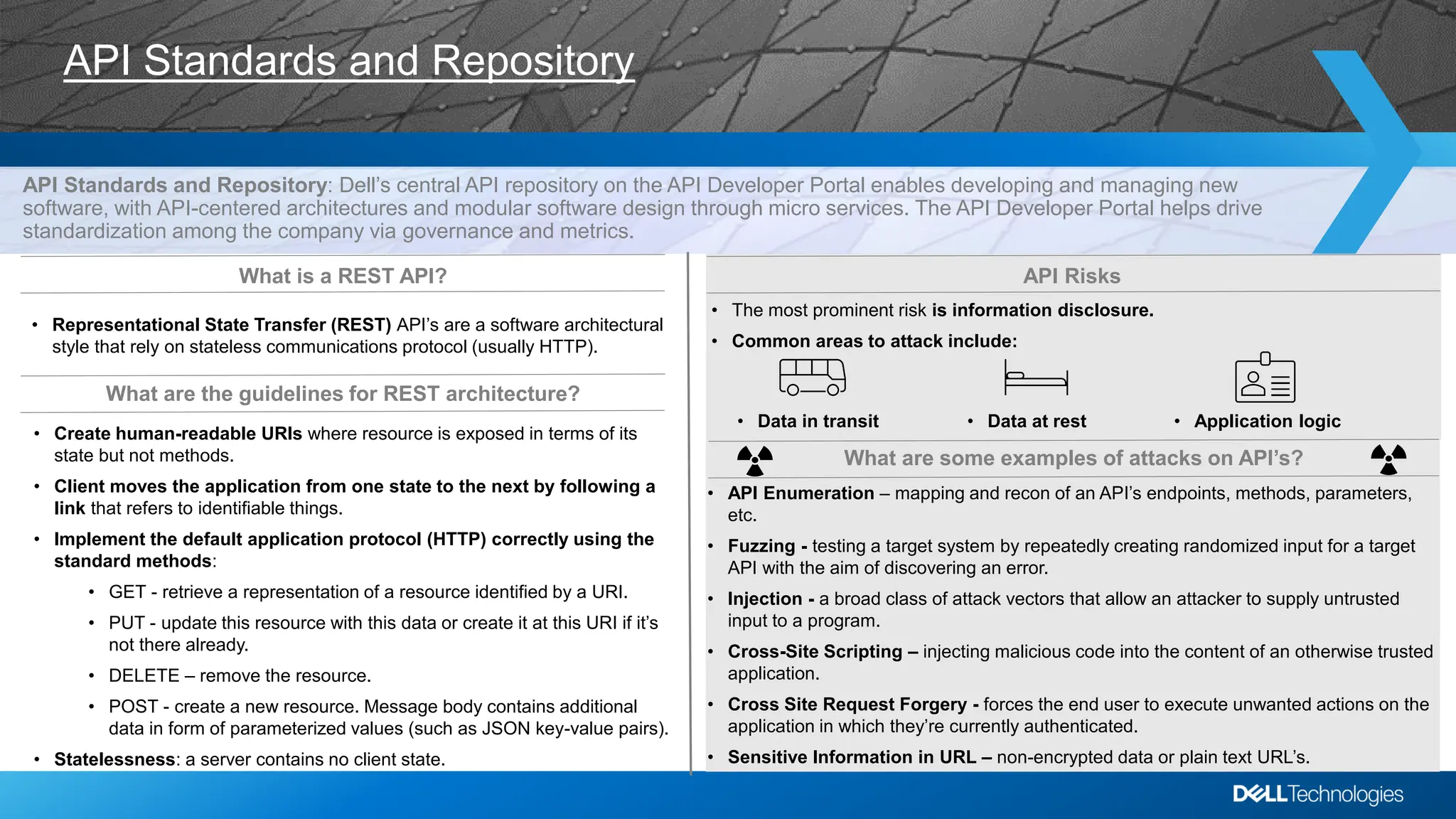
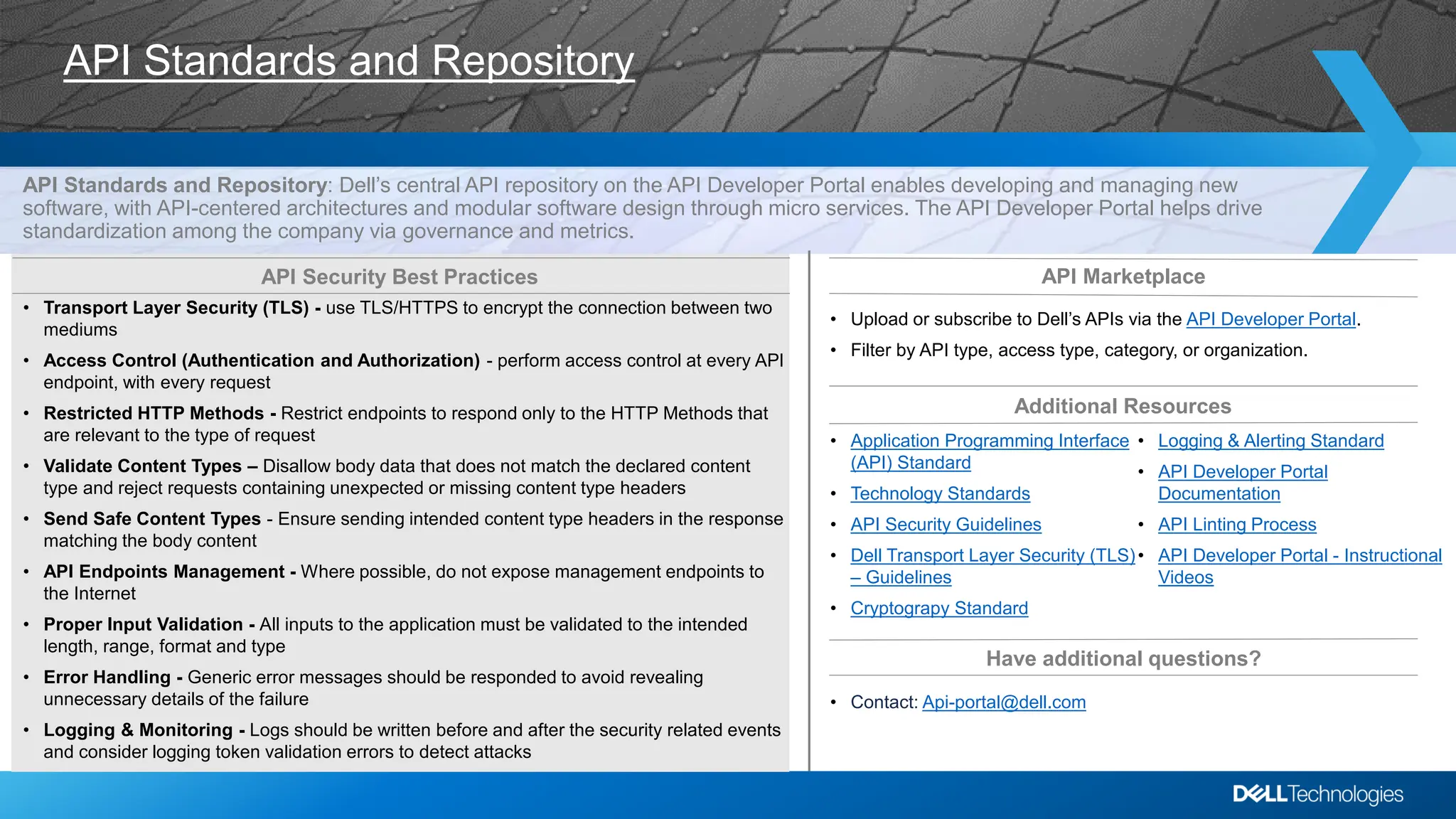
Dell's API Developer Portal centralizes API standards, facilitating software development with an emphasis on microservices and governance. It outlines REST API guidelines, emphasizes risks such as information disclosure, and offers security best practices to mitigate API vulnerabilities. Additional resources and access to Dell's APIs are available through the portal.