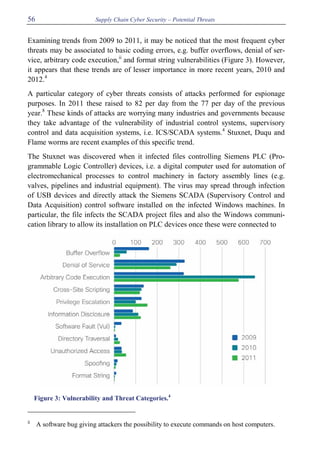
This document discusses potential cyber threats to supply chains. It begins by defining cybercrime and noting the increasing rates of cyber attacks. Supply chains rely heavily on information and communication technologies, making them vulnerable targets. The document then develops three scenarios of how cybercrime could jeopardize supply chain security and European well-being by disrupting flows of critical supplies like oil, food, and pharmaceuticals. It concludes by noting the limited existing research on this topic and implications for managers and EU agencies.