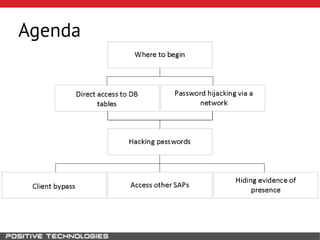
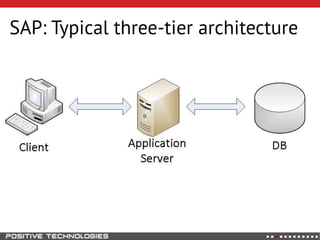
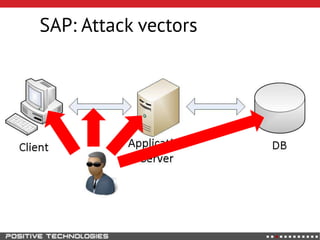
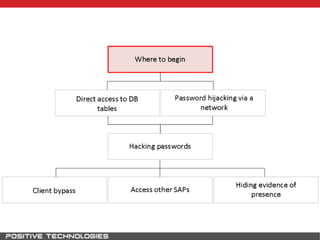
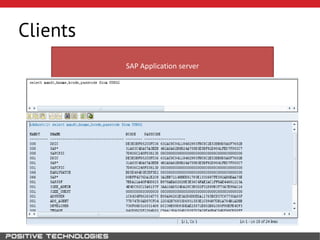
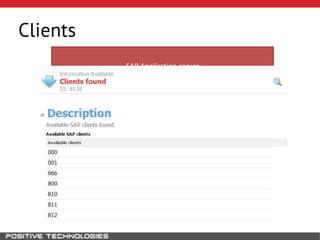
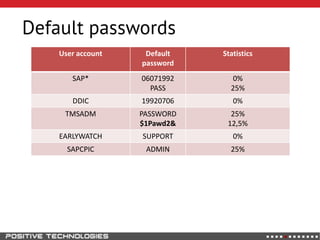
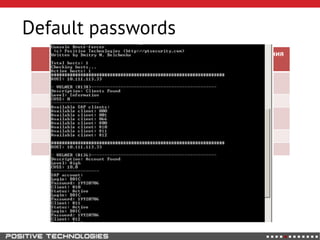
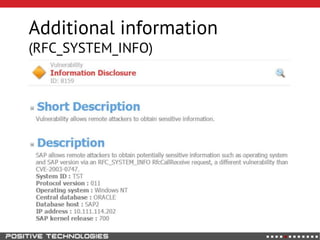
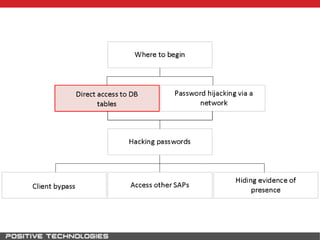
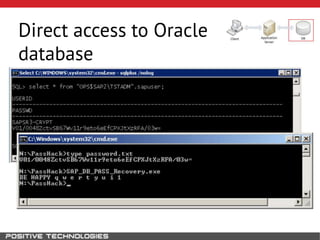
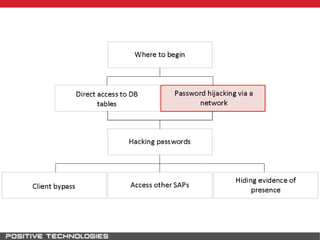
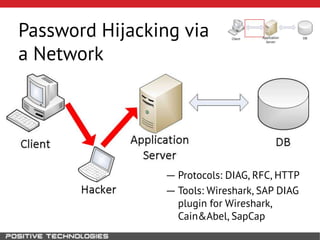
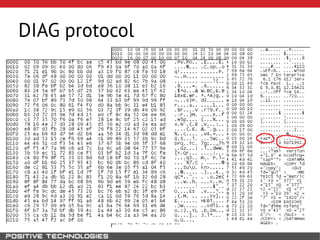
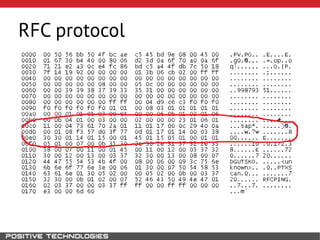
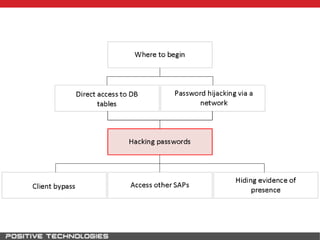
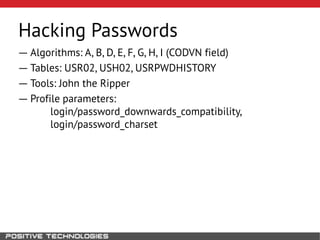
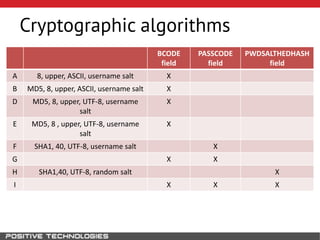
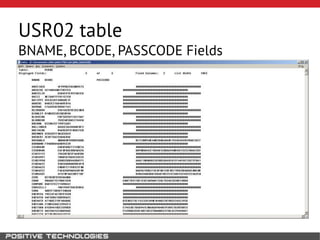
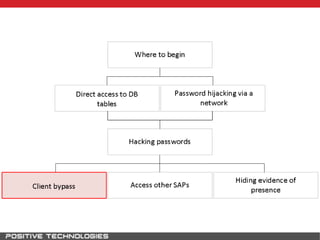
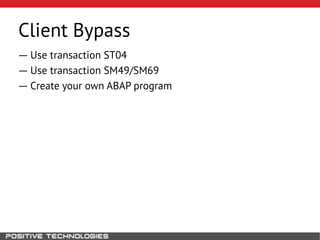
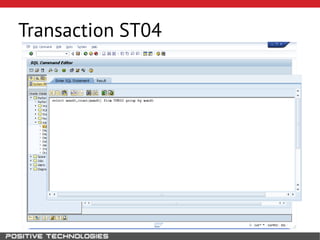
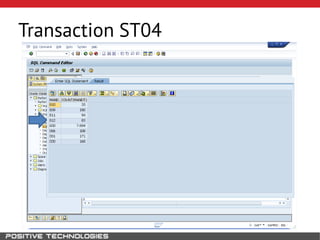
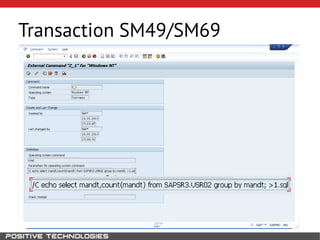
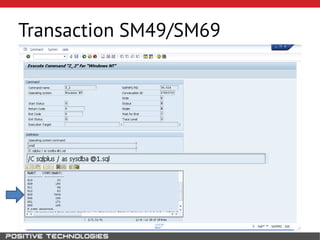
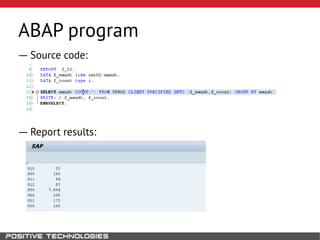
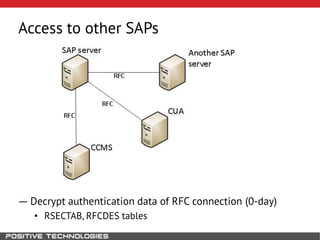
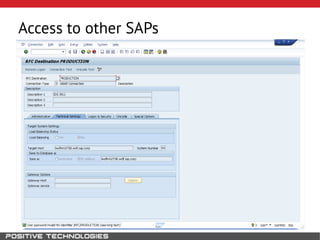
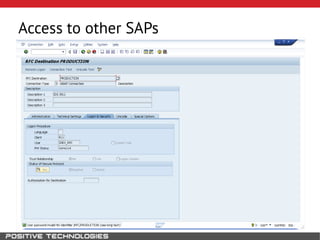
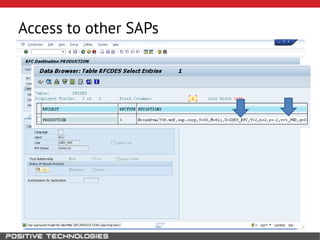
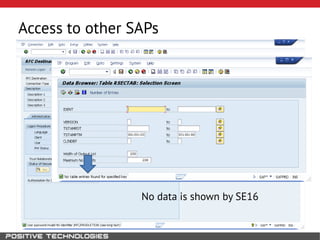
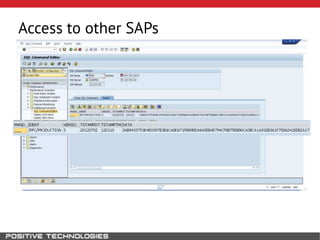
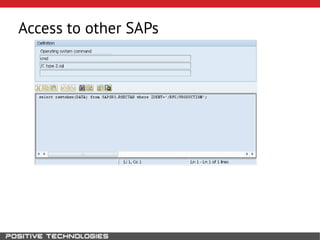
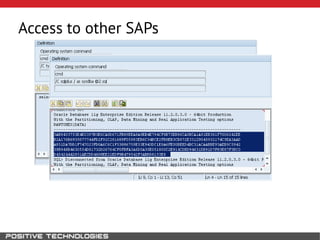
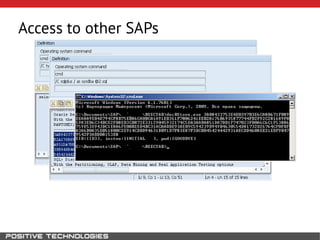
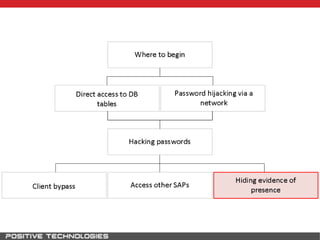
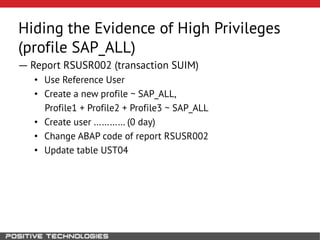
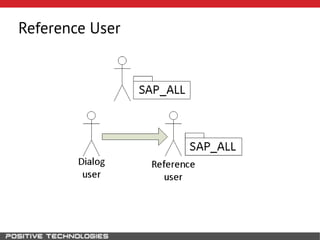
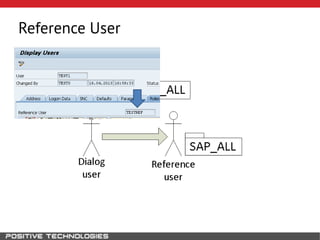
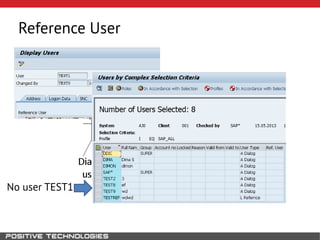
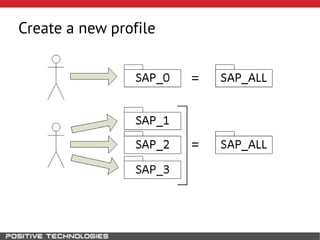
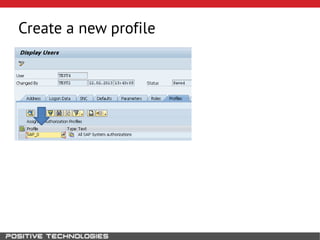
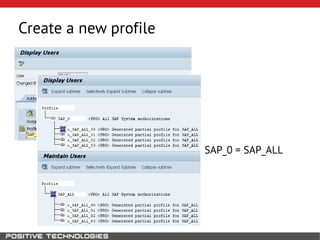
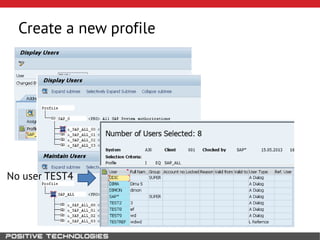
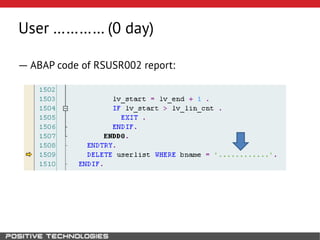
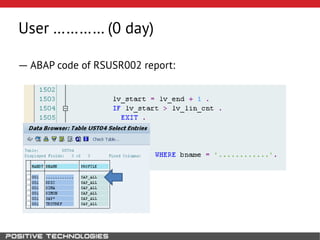
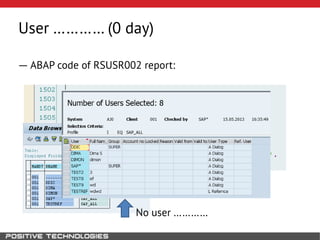
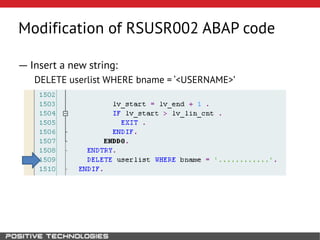
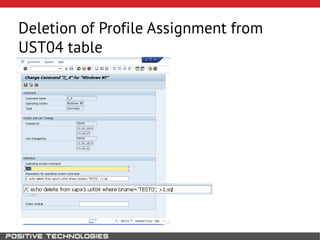
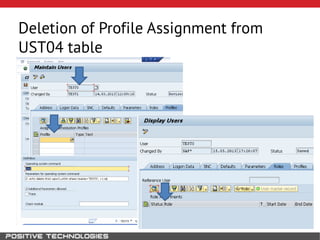
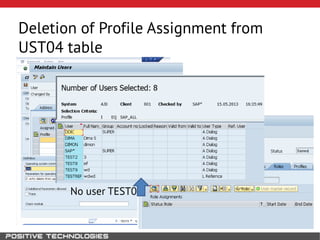
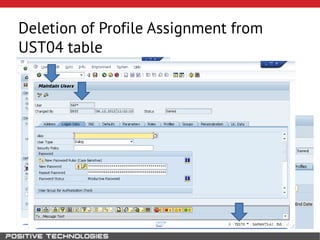
This document outlines an attack methodology for compromising SAP systems. It begins by scanning open ports to identify available clients and services. Default passwords are checked to gain initial access. Tools like MaxPatrol and sapyto are used to gather additional system information from RFC connections. Direct access to the Oracle database is possible if it uses remote OS authentication. Password hijacking can occur via network protocols like DIAG and RFC. Various password encryption algorithms are detailed along with ways to recover passwords using tools like John the Ripper. The document shows how to bypass clients, access other SAP systems via decrypted RFC connections, and hide evidence of high privileges by modifying reports and tables.