The document discusses the evolving landscape of fraud, emphasizing how traditional detection systems are insufficient against increasingly sophisticated cybercriminal tactics. It highlights the significant financial impact of fraud across various sectors and suggests a holistic, real-time data-driven approach to effectively detect and counteract fraudulent activities. Companies are encouraged to integrate structured and unstructured data for better contextual understanding and response capabilities in order to mitigate losses and protect customer interests.







![Day 1 [10:30 PM]
Successful login:
Usual IP address (FL)
Day 1 [10:30 PM]
Successful login:
Usual IP address (FL)
Day 2 [8:07 AM]
NY ATM withdrawal
Day 2 [8:07 AM]
NY ATM withdrawal
Day 2 [5:52 PM]
Failed login x2
New IP address (1)
Day 2 [5:52 PM]
Failed login x2
New IP address (1)
Day 3 [7:17 PM]
Successful login:
New IP address (2)
Day 3 [7:17 PM]
Successful login:
New IP address (2)
Day 5 [11:30 PM]
Successful login:
Usual IP address (FL)
Day 5 [11:30 PM]
Successful login:
Usual IP address (FL)
Day 6 [5:20 PM]
Funds transfer ($1):
Unknown recipient
Day 6 [5:20 PM]
Funds transfer ($1):
Unknown recipient
Day 4 [3:38 AM]
Mobile banking:
Authorize new device login
Day 4 [3:38 AM]
Mobile banking:
Authorize new device login
Day 5 [12:34 PM]
Password change:
New IP address (3)
Day 5 [12:34 PM]
Password change:
New IP address (3)
Day 10 [4:30 AM]
Funds transfer ($5k):
Unknown recipient
Day 10 [4:30 AM]
Funds transfer ($5k):
Unknown recipient
Day 2 [2:43 PM]
Onboard purchase:
United Airlines
Day 2 [2:43 PM]
Onboard purchase:
United Airlines
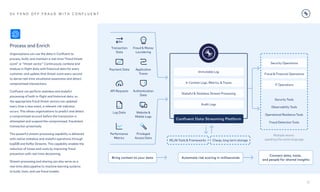
Capturing and understanding contextual and situational data
can help identify a fraudulent actor before an unauthorized
transaction is even invoked. Identifying unusual, erratic, or
incongruent changes to the contextual data for an account can
help prevent malevolent activities before they occur by possibly
locking the user’s account or taking other preventative action.
Let’s consider the example of payment fraud.
To understand when payment fraud happens, you need to
know more than just the fact that a transaction has occurred.
To know whether that transaction was legitimate or
fraudulent, it becomes very important to understand the
context around that transaction. To this end it becomes critical
to collect and analyze all the information that can provide that
context, regardless of which systems or data sources may
contain that data, to create the appropriate risk score.
The illustration above highlights some of the contextual data that may be critical to informing a fraud detection decision including:
Failed login attempts Did the user attempt to log in
multiple times before gaining access to the system?
Change of password Did the user change their
password recently?
User geolocation Is the user making the request in
a location that is different from their usual location?
User device/software info Is the user using a device or
software version that is new or different?
User network address info Is this request coming from
a new or different IP address or host for this user?
New payment recipient Is the user sending this payment
to a new or unknown recipient?
Amount of transaction Is the amount of this transaction
unusual for this user based on their historical patterns?
Time/Day of transaction Is the time of this transaction
unusual for this user?
Context Matters
8
02 How to counteract fraud
Day 4 [6:30 AM]
Airport Taxi card swipe
Day 4 [6:30 AM]
Airport Taxi card swipe](https://image.slidesharecdn.com/20230526-eb-puttingfraudincontext-240823024011-47e8a280/85/20230526-EB-Putting_Fraud_In_Context-pdf-8-320.jpg)