1whitepaper graphics
•
0 likes•159 views
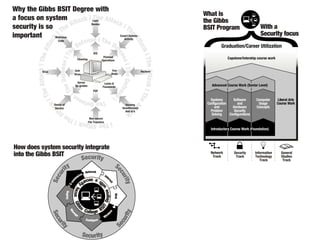
The document discusses the Gibbs BSIT program with a focus on security. It offers tracks in network security, security, and information technology as well as general studies and liberal arts coursework. Students learn systems configuration, problem solving, software and hardware security configurations, and computer usage concepts. Advanced coursework includes capstone and internship experiences. The program prepares students for careers utilizing their skills upon graduation. It explains how system security is integrated into the BSIT degree and why this focus is important.
Report
Share
Report
Share
Download to read offline
Recommended
13.Anton-Position-Security-Considerations-23June2015[1]![13.Anton-Position-Security-Considerations-23June2015[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![13.Anton-Position-Security-Considerations-23June2015[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The document discusses security considerations and concerns for standardization of software defined networking. It notes computing trends driving network changes and constraints faced. Industry is said to be taking the same approach and architecture but security drivers may not be quite the same. The document discusses using a defense in depth model with baseline security models, integrity checks, and physical security. It also discusses accomplishing security without failing standards from various organizations and using a flexible security model while remembering physical security. It summarizes that a flexible approach is needed given advancing technology and existing best practices should be leveraged, but a more complex risk mitigation matrix may be required long term which will be difficult for industries to address.
1 - HKT Reporting.pdf

This document summarizes the results of a vulnerability assessment performed on the networks of 6 schools by HKT. It found that around 25% of systems had web services, with an average risk score of 54 and scores ranging from 20 to 78. Manual review found that 33% of vulnerabilities were high or critical risks. Common high risk issues included SQL injection, cross-site scripting, and outdated software with known vulnerabilities. The document discusses ongoing challenges in security management like complexity, recruitment, and funding. It proposes a security-centric approach with centralized monitoring, automation, and remote support provided by a managed security service partner.
3 - Interaction between Cyber Security and School IT Policy .pdf

This document discusses the interaction between cyber security and school IT policy. It outlines various IT systems, applications, and devices used in schools, such as servers, networks, cloud services, and devices. It stresses the importance of having proper IT policies to govern operation, systems and applications, control, security, and management. The document provides examples of key policies including acceptable use, network, data protection, backup, email, and disaster recovery policies. It also discusses guidelines and rules around issues like passwords, verification, training, manuals, and applications. Finally, it provides tips for effective policy making like understanding needs, problems, requirements, training users, and ongoing evaluation.
Why a new cybersecurity paradigm for IoTs

The quick surge of the number of connected IoTs on the internet is posing a huge threat in terms of cybersecurity. Numerous classic device manufacturers are starting to connect their products to the internet without thinking about 2 major issues:
- Security
- Data protection
At Genki, we think the connected devices paradigm needs to change, here is why and how.
Vanson Bourne Infographic: IT Security

Vanson Bourne Infographic: What price IT Security? Responses of 100 senior IT decision-makers in UK commercial enterprises (1000+ employees)
Cloud Computing Security V1.2

This is an introduction of a paper with the same title submitted and presented at the 10th International Symposium on Pervasive Systems, Algorithms, and Networks. The paper is available in the conference proceedings.
Networking overview

Network is not about connection between two or computer within network but it is concerned more on securing it from Intruders.
PhD-Guidance-in-Neural-Networks

FRESH TECHNIQUES
IN NEURAL NETWORKS
MAJOR APPLICATIONS IN NEURAL NETWORKS
ADVANCED TOPICS
IN NEURAL NETWORKS
Recommended
13.Anton-Position-Security-Considerations-23June2015[1]![13.Anton-Position-Security-Considerations-23June2015[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![13.Anton-Position-Security-Considerations-23June2015[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The document discusses security considerations and concerns for standardization of software defined networking. It notes computing trends driving network changes and constraints faced. Industry is said to be taking the same approach and architecture but security drivers may not be quite the same. The document discusses using a defense in depth model with baseline security models, integrity checks, and physical security. It also discusses accomplishing security without failing standards from various organizations and using a flexible security model while remembering physical security. It summarizes that a flexible approach is needed given advancing technology and existing best practices should be leveraged, but a more complex risk mitigation matrix may be required long term which will be difficult for industries to address.
1 - HKT Reporting.pdf

This document summarizes the results of a vulnerability assessment performed on the networks of 6 schools by HKT. It found that around 25% of systems had web services, with an average risk score of 54 and scores ranging from 20 to 78. Manual review found that 33% of vulnerabilities were high or critical risks. Common high risk issues included SQL injection, cross-site scripting, and outdated software with known vulnerabilities. The document discusses ongoing challenges in security management like complexity, recruitment, and funding. It proposes a security-centric approach with centralized monitoring, automation, and remote support provided by a managed security service partner.
3 - Interaction between Cyber Security and School IT Policy .pdf

This document discusses the interaction between cyber security and school IT policy. It outlines various IT systems, applications, and devices used in schools, such as servers, networks, cloud services, and devices. It stresses the importance of having proper IT policies to govern operation, systems and applications, control, security, and management. The document provides examples of key policies including acceptable use, network, data protection, backup, email, and disaster recovery policies. It also discusses guidelines and rules around issues like passwords, verification, training, manuals, and applications. Finally, it provides tips for effective policy making like understanding needs, problems, requirements, training users, and ongoing evaluation.
Why a new cybersecurity paradigm for IoTs

The quick surge of the number of connected IoTs on the internet is posing a huge threat in terms of cybersecurity. Numerous classic device manufacturers are starting to connect their products to the internet without thinking about 2 major issues:
- Security
- Data protection
At Genki, we think the connected devices paradigm needs to change, here is why and how.
Vanson Bourne Infographic: IT Security

Vanson Bourne Infographic: What price IT Security? Responses of 100 senior IT decision-makers in UK commercial enterprises (1000+ employees)
Cloud Computing Security V1.2

This is an introduction of a paper with the same title submitted and presented at the 10th International Symposium on Pervasive Systems, Algorithms, and Networks. The paper is available in the conference proceedings.
Networking overview

Network is not about connection between two or computer within network but it is concerned more on securing it from Intruders.
PhD-Guidance-in-Neural-Networks

FRESH TECHNIQUES
IN NEURAL NETWORKS
MAJOR APPLICATIONS IN NEURAL NETWORKS
ADVANCED TOPICS
IN NEURAL NETWORKS
BannersBroker

Banners Broker is an online advertising company that sells banner impressions as a way to earn revenue online. It discusses the large size of the online advertising industry at $500 billion dollars. The document provides information about how online advertising works, including contextual targeting of ads based on relevant website content and geo-targeting ads to specific countries or cities. It also outlines how advertisers, publishers, and their combination called an Ad-Pub Combo can participate in the program.
ecolab eco97fin

This document provides a summary of a company's financial discussion and analysis for the years 1998, 1997, and 1996. Some key points:
- Net sales increased 15% in 1998 to nearly $1.9 billion, with double-digit growth in both US and international operations. Business acquisitions accounted for about half the growth.
- Operating income was a record $262 million in 1998, up 20% from 1997. The operating margin reached a new high of 13.9%.
- Income from continuing operations rose 15% to a record $155 million, or $1.15 per diluted share.
- Net income totaled $193 million, or $1.44 per diluted share, compared to
Rails + mongo db

This document discusses using MongoDB with Rails applications. It provides an overview of MongoDB concepts like documents, collections, references, and embeds. It also covers using the Mongoid ORM with Rails to interact with MongoDB, including modeling, persistence, querying, references, and embeds. The document concludes by mentioning cloud hosting on MongoHQ and notes that Rails and MongoDB are a good combination.
Unit 1 2.0

The document provides definitions and examples of literary devices including simile, hover, laggard, collaborate, and imagery. It also defines internal conflict, external conflict, and proper adjectives. For each term, an image is included and the reader is prompted to write a sentence using the underlined term.
A Discourse on e-Discovery - MCS Management Services

ECA/EDA (early case/data assessment) techniques are disrupting e-discovery workflow. This is an overview of how the latest ECA techniques will be a game changer for you and your firm.
My ITDi Summer MOOC preso

You can join us live or watch the recordings! Here is the schedule:
http://www.wiziq.com/courses/courseware-learner.aspx?cInfo=MP7Z4Xew36%2fhLyQnd0LGl5bs9WZX6b%2fuKBybgbMySOhDJ41d7l8RGqMWAmmegqJr5%2fEMdxh63pUXdKqoc2sk3ask9wlTYXzIi98WRdWAzjplTMHowxVh5SxCY5ti5AB5TEOWn6JvyDakAQV5lVLocfJwxwdQ4MazLnZ%2beo2Kg9Y%3d
In Search of Simplicity: Redesigning the Digital Bleek and Lloyd

DESIDOC Journal of Library & Information Technology: Special Issue on Digital Preservation original submission.
Publication URL: http://goo.gl/yUERj
BibTeX Citation
@article{D2524,
author = {Lighton Phiri and Hussein Suleman},
title = {In Search of Simplicity: Redesigning the Digital Bleek and Lloyd},
journal = {DESIDOC Journal of Library & Information Technology},
volume = {32},
number = {4},
year = {2012},
keywords = {},
abstract = {The Digital Bleek and Lloyd is a collection of digitised historical artefacts on the Bushman people ofSouthern Africa. The underlying software was initially designed to enable access from as many people aspossible so usage requirements were minimal – it was not even necessary to use a web server or database.However, the system was not focused on preservation, extensibility, or reusability. In this article, it is arguedthat such desirable attributes could manifest themselves in a natural evolution of the Bleek and Lloyd softwaresystem in the direction of greater simplicity. A case study demonstrates that this is indeed feasible in the caseof the Digital Bleek and Lloyd and potentially more generally applicable in digital libraries.},
issn = {0976-4658}, url = {http://publications.drdo.gov.in/ojs/index.php/djlit/article/view/2524}
}
I got the news

The document discusses how audiences source news in the digital age. It notes that audiences now have many options for accessing news from around the world through various online news broadcasters and YouTube. It also discusses how digital technology and new online news providers have changed audience behaviors and business models, putting economic pressure on traditional newspapers. The document also outlines the main institutions that gather and present news content in the UK, such as the BBC, ITN, and Sky, as well as additional sources of news like news agencies, press releases, social media, and citizen journalism.
Bri’ann merit

This document contains summaries of three passages. The first is about Martin Luther King Jr. and his efforts to promote civil rights through nonviolent protests and speeches. The second is about a man named Jimmy Valentine who turned his life around after being released from prison. The third summarizes the sinking of the Titanic, including how it was thought to be unsinkable but hit an iceberg, causing it to sink and forcing people onto lifeboats.
SaaS case Study Mortgage Industry

An early stage mortgage company wanted to develop a complex SaaS loan pricing and search application quickly. Ekartha delivered the application in under 5 months, significantly reducing the company's operations costs and allowing rapid scaling. The well-architected multi-tenant solution provided a competitive advantage through an intuitive interface and high-performance search engine. The application had over 99% uptime and was praised as the most comprehensive in the industry.
Cold war in the 60's

The document summarizes key events of the Cold War in the 1960s, including John F. Kennedy becoming president of the US in 1960 while Fidel Castro led Cuba and Nikita Khrushchev governed Russia. It describes the strategic placement of nuclear weapons and how Russia aligned with Cuba for protection. It then discusses the failed Bay of Pigs invasion of Cuba in 1961 and the ensuing Cuban Missile Crisis in 1962, where Russia agreed to remove missiles from Cuba and the US secretly withdrew warheads from Turkey and Italy in a triumph for Kennedy.
La manta de dayana

Dayana es una niña de 10 años que vive en un pequeño pueblo. Su familia es pobre y su única posesión de valor es una manta tejida a mano por su abuela. Un día, Dayana pierde la manta y se siente muy triste porque era lo único que le quedaba de su abuela.
[TEDxHUFS] 한글과 다시 소통하다 강병인![[TEDxHUFS] 한글과 다시 소통하다 강병인](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[TEDxHUFS] 한글과 다시 소통하다 강병인](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The document discusses reconnecting with the Korean language and viewing Korean in a new light. It mentions communicating in Korean again and looking at Korean anew. The author's name is given as Kang Byeong-in.
Project: Improving Reputation of The Favelas. Brazil

This 3 minute and 30 second song titled "Magalenha" is performed by Brazilian musician Sergio Mendes. Released in 1967, the bossa nova track features Mendes' signature style of blending Brazilian rhythms with jazz and pop influences. The upbeat melody and playful instrumentation create a lively, danceable sound that helped popularize bossa nova internationally.
GSU IT Program Fact Sheet

This document summarizes the Bachelor of Science in Information Technology program at Governors State University (GSU). The program prepares students for careers in fields like information security, digital forensics, virtualization, and cloud computing. Students take courses in areas like IT project management, computer networks, and IT seminars. They also choose selective courses across concentrations in operating systems, information security, network infrastructure, ethical hacking, digital forensics, and virtualization/cloud computing. Graduates will be ready for jobs as computer systems analysts, administrators, and specialists or for graduate study in related fields. The program offers hands-on learning and collaboration with other programs at an affordable cost.
120321 IAPS Some things Prep Heads need to know about ICT

This document discusses topics related to developing an ICT strategy for a school, including who should make ICT budget decisions, key principles of ICT strategy like reliability and security of the network, other strategic issues, and how technology may impact the future of teaching and learning. The document provides guidance on forming an ICT strategy group and setting strategic priorities based on educational needs to inform technology investments.
Securing the ‘Wild Wild West’: USM for Universities

Securing the IT environment in today’s college or university is no task for the faint of heart. Find out how AlienVault helped Marquette University
Cybersecurity and Privacy in ESG Digital Transformation

[Content]
Part I.
1. ESG Ecosystem
ESG Management Matters?
ESG Investment Matters?
ESG Knowledge Map
2. ESG DX & Cybersecurity
ESG Digital Transformation (DX)
The Fourth Wave of Environmentalism
Cybersecurity Matters?
3. Cybersecurity & Privacy Protection in ESG
ESG Cybersecurity & Privacy Matters?
ESG Cybersecurity & Privacy Reporting Standard
ESG Performance Score - Materiality Comparisons Across Industries
Global Standard for Reporting Cybersecurity & Privacy
Global Government Regulations of Personal Information
Cybersecurity & Privacy Reporting Standard Development
Part II.
1. Cybersecurity & Privacy Protection by Zeus & Xanadu
Zeus Cybersecurity Solution
Zeus Cybersecurity Solution Demo for Defense Against Cyber Attacks
Xanadu Big Data NoSQL DB/Cloud Computing Solution Demo for Protection against Ransomware
Xanadu-Blockchain Integration Demo for Secure Health Data Sharing
2. AI, Blockchain, IoT for ESG DX
AI Innovation State Of The Art
Blockchain State Of The Art: Issues with Public Chain
IoT Innovation State Of The Art: 5G & Edge AI
AI Blockchain IoT for ESG Digital Transformation AT A Glance
3. AI, Blockchain, IoT for Cybersecurity & Privacy Protection
Cyber Attack Surface
AI, Blockchain, IoT GDPR Compliance AT A Glance
Cybersecurity & Privacy in AI + Blockchain + IoT Integration
Cybersecurity & Privacy Innovation Insights from Patents
AI Patents in Cybersecurity & Privacy Protection
Cybersecurity & Privacy Innovation Insights from Patents
More Related Content
Viewers also liked
BannersBroker

Banners Broker is an online advertising company that sells banner impressions as a way to earn revenue online. It discusses the large size of the online advertising industry at $500 billion dollars. The document provides information about how online advertising works, including contextual targeting of ads based on relevant website content and geo-targeting ads to specific countries or cities. It also outlines how advertisers, publishers, and their combination called an Ad-Pub Combo can participate in the program.
ecolab eco97fin

This document provides a summary of a company's financial discussion and analysis for the years 1998, 1997, and 1996. Some key points:
- Net sales increased 15% in 1998 to nearly $1.9 billion, with double-digit growth in both US and international operations. Business acquisitions accounted for about half the growth.
- Operating income was a record $262 million in 1998, up 20% from 1997. The operating margin reached a new high of 13.9%.
- Income from continuing operations rose 15% to a record $155 million, or $1.15 per diluted share.
- Net income totaled $193 million, or $1.44 per diluted share, compared to
Rails + mongo db

This document discusses using MongoDB with Rails applications. It provides an overview of MongoDB concepts like documents, collections, references, and embeds. It also covers using the Mongoid ORM with Rails to interact with MongoDB, including modeling, persistence, querying, references, and embeds. The document concludes by mentioning cloud hosting on MongoHQ and notes that Rails and MongoDB are a good combination.
Unit 1 2.0

The document provides definitions and examples of literary devices including simile, hover, laggard, collaborate, and imagery. It also defines internal conflict, external conflict, and proper adjectives. For each term, an image is included and the reader is prompted to write a sentence using the underlined term.
A Discourse on e-Discovery - MCS Management Services

ECA/EDA (early case/data assessment) techniques are disrupting e-discovery workflow. This is an overview of how the latest ECA techniques will be a game changer for you and your firm.
My ITDi Summer MOOC preso

You can join us live or watch the recordings! Here is the schedule:
http://www.wiziq.com/courses/courseware-learner.aspx?cInfo=MP7Z4Xew36%2fhLyQnd0LGl5bs9WZX6b%2fuKBybgbMySOhDJ41d7l8RGqMWAmmegqJr5%2fEMdxh63pUXdKqoc2sk3ask9wlTYXzIi98WRdWAzjplTMHowxVh5SxCY5ti5AB5TEOWn6JvyDakAQV5lVLocfJwxwdQ4MazLnZ%2beo2Kg9Y%3d
In Search of Simplicity: Redesigning the Digital Bleek and Lloyd

DESIDOC Journal of Library & Information Technology: Special Issue on Digital Preservation original submission.
Publication URL: http://goo.gl/yUERj
BibTeX Citation
@article{D2524,
author = {Lighton Phiri and Hussein Suleman},
title = {In Search of Simplicity: Redesigning the Digital Bleek and Lloyd},
journal = {DESIDOC Journal of Library & Information Technology},
volume = {32},
number = {4},
year = {2012},
keywords = {},
abstract = {The Digital Bleek and Lloyd is a collection of digitised historical artefacts on the Bushman people ofSouthern Africa. The underlying software was initially designed to enable access from as many people aspossible so usage requirements were minimal – it was not even necessary to use a web server or database.However, the system was not focused on preservation, extensibility, or reusability. In this article, it is arguedthat such desirable attributes could manifest themselves in a natural evolution of the Bleek and Lloyd softwaresystem in the direction of greater simplicity. A case study demonstrates that this is indeed feasible in the caseof the Digital Bleek and Lloyd and potentially more generally applicable in digital libraries.},
issn = {0976-4658}, url = {http://publications.drdo.gov.in/ojs/index.php/djlit/article/view/2524}
}
I got the news

The document discusses how audiences source news in the digital age. It notes that audiences now have many options for accessing news from around the world through various online news broadcasters and YouTube. It also discusses how digital technology and new online news providers have changed audience behaviors and business models, putting economic pressure on traditional newspapers. The document also outlines the main institutions that gather and present news content in the UK, such as the BBC, ITN, and Sky, as well as additional sources of news like news agencies, press releases, social media, and citizen journalism.
Bri’ann merit

This document contains summaries of three passages. The first is about Martin Luther King Jr. and his efforts to promote civil rights through nonviolent protests and speeches. The second is about a man named Jimmy Valentine who turned his life around after being released from prison. The third summarizes the sinking of the Titanic, including how it was thought to be unsinkable but hit an iceberg, causing it to sink and forcing people onto lifeboats.
SaaS case Study Mortgage Industry

An early stage mortgage company wanted to develop a complex SaaS loan pricing and search application quickly. Ekartha delivered the application in under 5 months, significantly reducing the company's operations costs and allowing rapid scaling. The well-architected multi-tenant solution provided a competitive advantage through an intuitive interface and high-performance search engine. The application had over 99% uptime and was praised as the most comprehensive in the industry.
Cold war in the 60's

The document summarizes key events of the Cold War in the 1960s, including John F. Kennedy becoming president of the US in 1960 while Fidel Castro led Cuba and Nikita Khrushchev governed Russia. It describes the strategic placement of nuclear weapons and how Russia aligned with Cuba for protection. It then discusses the failed Bay of Pigs invasion of Cuba in 1961 and the ensuing Cuban Missile Crisis in 1962, where Russia agreed to remove missiles from Cuba and the US secretly withdrew warheads from Turkey and Italy in a triumph for Kennedy.
La manta de dayana

Dayana es una niña de 10 años que vive en un pequeño pueblo. Su familia es pobre y su única posesión de valor es una manta tejida a mano por su abuela. Un día, Dayana pierde la manta y se siente muy triste porque era lo único que le quedaba de su abuela.
[TEDxHUFS] 한글과 다시 소통하다 강병인![[TEDxHUFS] 한글과 다시 소통하다 강병인](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[TEDxHUFS] 한글과 다시 소통하다 강병인](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The document discusses reconnecting with the Korean language and viewing Korean in a new light. It mentions communicating in Korean again and looking at Korean anew. The author's name is given as Kang Byeong-in.
Project: Improving Reputation of The Favelas. Brazil

This 3 minute and 30 second song titled "Magalenha" is performed by Brazilian musician Sergio Mendes. Released in 1967, the bossa nova track features Mendes' signature style of blending Brazilian rhythms with jazz and pop influences. The upbeat melody and playful instrumentation create a lively, danceable sound that helped popularize bossa nova internationally.
Viewers also liked (18)
A Discourse on e-Discovery - MCS Management Services

A Discourse on e-Discovery - MCS Management Services
In Search of Simplicity: Redesigning the Digital Bleek and Lloyd

In Search of Simplicity: Redesigning the Digital Bleek and Lloyd
Project: Improving Reputation of The Favelas. Brazil

Project: Improving Reputation of The Favelas. Brazil
Similar to 1whitepaper graphics
GSU IT Program Fact Sheet

This document summarizes the Bachelor of Science in Information Technology program at Governors State University (GSU). The program prepares students for careers in fields like information security, digital forensics, virtualization, and cloud computing. Students take courses in areas like IT project management, computer networks, and IT seminars. They also choose selective courses across concentrations in operating systems, information security, network infrastructure, ethical hacking, digital forensics, and virtualization/cloud computing. Graduates will be ready for jobs as computer systems analysts, administrators, and specialists or for graduate study in related fields. The program offers hands-on learning and collaboration with other programs at an affordable cost.
120321 IAPS Some things Prep Heads need to know about ICT

This document discusses topics related to developing an ICT strategy for a school, including who should make ICT budget decisions, key principles of ICT strategy like reliability and security of the network, other strategic issues, and how technology may impact the future of teaching and learning. The document provides guidance on forming an ICT strategy group and setting strategic priorities based on educational needs to inform technology investments.
Securing the ‘Wild Wild West’: USM for Universities

Securing the IT environment in today’s college or university is no task for the faint of heart. Find out how AlienVault helped Marquette University
Cybersecurity and Privacy in ESG Digital Transformation

[Content]
Part I.
1. ESG Ecosystem
ESG Management Matters?
ESG Investment Matters?
ESG Knowledge Map
2. ESG DX & Cybersecurity
ESG Digital Transformation (DX)
The Fourth Wave of Environmentalism
Cybersecurity Matters?
3. Cybersecurity & Privacy Protection in ESG
ESG Cybersecurity & Privacy Matters?
ESG Cybersecurity & Privacy Reporting Standard
ESG Performance Score - Materiality Comparisons Across Industries
Global Standard for Reporting Cybersecurity & Privacy
Global Government Regulations of Personal Information
Cybersecurity & Privacy Reporting Standard Development
Part II.
1. Cybersecurity & Privacy Protection by Zeus & Xanadu
Zeus Cybersecurity Solution
Zeus Cybersecurity Solution Demo for Defense Against Cyber Attacks
Xanadu Big Data NoSQL DB/Cloud Computing Solution Demo for Protection against Ransomware
Xanadu-Blockchain Integration Demo for Secure Health Data Sharing
2. AI, Blockchain, IoT for ESG DX
AI Innovation State Of The Art
Blockchain State Of The Art: Issues with Public Chain
IoT Innovation State Of The Art: 5G & Edge AI
AI Blockchain IoT for ESG Digital Transformation AT A Glance
3. AI, Blockchain, IoT for Cybersecurity & Privacy Protection
Cyber Attack Surface
AI, Blockchain, IoT GDPR Compliance AT A Glance
Cybersecurity & Privacy in AI + Blockchain + IoT Integration
Cybersecurity & Privacy Innovation Insights from Patents
AI Patents in Cybersecurity & Privacy Protection
Cybersecurity & Privacy Innovation Insights from Patents
Saint leo university Cybersecurity

Study Metro help international students to study in USA and Abroad Countries , Call our adviser at 91-8088-867-867 or visit www.studymetro.com
Cisco ite ds

The document summarizes the Cisco Networking Academy's IT Essentials curriculum. IT Essentials provides an introduction to computer hardware, software, networking, and security skills needed for entry-level ICT careers. The hands-on course teaches students how to assemble and troubleshoot computers, install operating systems, connect to networks, and pursue CompTIA A+ certification to advance their careers in information technology fields.
2008: Web Application Security Tutorial

This document discusses web application security and summarizes key topics from a presentation on the subject. It introduces the Open Web Application Security Project (OWASP) Top 10 list of vulnerabilities, covering Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF) in more detail. It also discusses security frameworks like ISO 27001 and the Payment Card Industry Data Security Standard (PCI DSS). The presentation emphasizes the importance of validating all user input to prevent injection attacks.
Ajit - Immune IT: Moving from Security to Immunity - ClubHack2008

The document discusses moving from a focus on security to immunity in IT systems. It defines security as confidentiality, integrity and availability (CIA) and outlines how immunity can be achieved by integrating security considerations into each phase of the engineering process, from requirements gathering to deployment. This embedded, holistic approach to security ownership can result in systems with immunity from threats and vulnerabilities.
Immune IT: Moving from Security to Immunity

The document discusses moving from a focus on security to immunity in IT systems. It defines security as confidentiality, integrity and availability (CIA) and outlines how immunity can be achieved by integrating security considerations into each phase of the engineering process, from requirements gathering to deployment. This embedded, integrated approach to security ownership can provide immunity rather than just addressing security as an isolated afterthought.
What BACnet/SC can do to improve BAS cybersecurity, and what it won’t do

How should we protect building automation systems from cybersecurity threats? Jim Butler is a BACnet IT Working Group convener and the first BACnet Testing Laboratories Manager, CTO of Cimetrics.
Metholodogies and Security Standards

This document discusses security standards and methodologies. It provides an overview of organizations that create standards, what types of topics standards may cover, and why there are so many standards. It then summarizes some specific security standards and methodologies like ISO 17799, COBIT, OCTAVE, and others. The document aims to give an introduction to common security standards and considerations in developing standards.
Cybersecurity Summit AHR20 Protect Cimetrics

NIST Framework function - Protect. Cybersecurity Summit at AHR20. Jim Butler - BACnet IT-WG. “Reduce the chance of a damaging cyber attack”
Cisco Phy Sec Overview Netversant

This document summarizes Cisco's physical security solutions including converged networking platforms, IP video surveillance cameras, access control systems, and emergency response technologies. It outlines the benefits of convergence for reducing total cost of ownership. Traditional separate systems for data, voice, video and physical security are consolidated onto a single IP network. Cisco provides an open platform to deliver the right security information to the right person at the right time through detection, analysis and response. Product lines include IP cameras, access control gateways, video management software and emergency notification systems.
Microsoft-CISO-Workshop-Security-Strategy-and-Program (1).pdf

The document discusses a CISO workshop agenda to modernize a security strategy and program. It includes:
- An overview of who should attend, such as the CISO, CIO, security directors, and business leaders.
- The agenda covers key context and fundamentals, business alignment, and security disciplines.
- Exercises are included to assess maturity, discuss recommendations, and assign next steps.
- Modules will provide guidance on initiatives like secure identities and access, security operations, and data security.
All Saints Schhol - ICT BTEC Course

This document provides an overview of the BTEC ICT course offered at a school in Dagenham. It describes the various units covered in the two-year course, including mandatory units in communication, computer systems, and optional units in e-commerce, computer networks, multimedia design, and computer animation. Students will complete six units per year to gain skills relevant to careers in computer systems, graphics, or business. The course is graded similarly to A-Levels and aims to provide students with qualifications and skills to succeed in university or future employment.
Safe Internet Banking Cyber Security

10 Simple steps for safe Internet Banking
Cyber Security threats and how to perform internet banking safely
Cybersecurity brochure flyer version-small

Whatcom Community College and Western Washington University have partnered to offer a new 4-year degree in Computer and Information Systems Security (CISS). Students can start with Whatcom's 2-year Associate in Applied Science-Transfer (AAS-T) in Cybersecurity, then transfer to WWU to complete the BS in CISS. The AAS-T prepares students for mid-level IT security jobs, while the BS prepares graduates for advanced, high-paying security roles like network administrator and forensic specialist.
S nandakumar_banglore

The document discusses cyber crimes and IT risk management. It provides a list of common cyber crimes and notes that India ranks 11th in the world for share of malicious computer activity. It also discusses the extent of cyber crimes according to various reports. The document outlines reasons why cyber attacks are possible and provides an overview of solutions to combat cyber crimes, including implementing security systems and processes. It also discusses various IT security frameworks and standards.
S nandakumar

The document discusses cyber crimes and IT risk management. It provides a list of common cyber crimes and notes that India ranks 11th in the world for share of malicious computer activity. It also discusses the extent of cyber crimes according to various reports. The document outlines reasons why cyber attacks are possible and provides solutions to combat cyber crimes, including implementing security systems and processes. It discusses various IT security frameworks and standards such as ISO 27000, COBIT, and NIST.
LOUCA23 Yusuf Hadiwinata Linux Security BestPractice

1) The document discusses a presentation about implementing security best practices on Linux systems. It provides information about the speaker's background and qualifications in cybersecurity and Linux.
2) The presentation covers topics like cybersecurity principles, Linux security hardening techniques, and using the CIS benchmarks and CIS-CAT Lite tool to assess and improve the security of Ubuntu systems.
3) It encourages attendees to ask questions to learn more about securing Linux and have a chance to win prizes from the event sponsor, Biznet Gio.
Similar to 1whitepaper graphics (20)
120321 IAPS Some things Prep Heads need to know about ICT

120321 IAPS Some things Prep Heads need to know about ICT
Securing the ‘Wild Wild West’: USM for Universities

Securing the ‘Wild Wild West’: USM for Universities
Cybersecurity and Privacy in ESG Digital Transformation

Cybersecurity and Privacy in ESG Digital Transformation
Ajit - Immune IT: Moving from Security to Immunity - ClubHack2008

Ajit - Immune IT: Moving from Security to Immunity - ClubHack2008
What BACnet/SC can do to improve BAS cybersecurity, and what it won’t do

What BACnet/SC can do to improve BAS cybersecurity, and what it won’t do
Microsoft-CISO-Workshop-Security-Strategy-and-Program (1).pdf

Microsoft-CISO-Workshop-Security-Strategy-and-Program (1).pdf
LOUCA23 Yusuf Hadiwinata Linux Security BestPractice

LOUCA23 Yusuf Hadiwinata Linux Security BestPractice
More from Valley and Associates
How the Distance Learning Market will Expand in the Coming Years

In the next 10 years the need for distance learning will be realized. Increasing high school graduation classes, expanded needs for an educated workforces beyond the high school level, and the limits of bricks and mortar class rooms will be evident. This presentation will show how the distance learner is presently underserved currently.
Personal brand and Social Media

A presentation to college students for the effective use of social media for personal branding and job hunting.
Social Media Week Reputation Management Presentation

The document provides 10 dos and don'ts for using social media. It advises thinking before posting (don't post without thinking) as posts are public and permanent. It also recommends avoiding discussing protected information, respecting intellectual property, and remembering that any mention of the company (Navy Federal) could be seen publicly. The document concludes by reminding readers to know the social media policy, take required training, and to like and share posts instead of answering questions unless authorized to speak for the company.
Mobile Update 2010

This document summarizes the mobile banking initiative of a financial institution. It launched mobile banking in under a year, enrolling over 140,000 members by April 2010. On average, 1,496 new members signed up daily in the first month. Most used the mobile web for balances and transaction histories. Alerts about low balances and deposits were most common. Younger age groups aged 18-44 used it most. The document outlines growth trends, popular features, and plans to expand capabilities further.
NFCU Blog pitch

Presentation to Management Council about why NFCU needed to have a blog, how it would work, and what they would get out of it.
Successful landing page implementation and use for new business acquisition

A landing page is a webpage that appears after a user clicks an advertisement or link. Its purpose is to motivate the user to take a specific action. Landing pages should be optimized based on where the traffic is coming from and designed to guide users through a conversion funnel. Navy Federal Credit Union's current landing page strategy is ineffective as it does not direct users clearly towards an application and lacks analytics tracking. A better approach would involve creating targeted landing pages for each campaign with compelling design and messaging to match advertisements, minimal distractions, and clear calls to action. Case studies found landing page optimizations can double conversion rates. An effective strategy involves identifying campaigns needing pages, designing pages, implementing pages and analytics, and retiring pages over time while monitoring performance
Analytics Process Review

- Our site receives 16 million visits per month on average, with 18% bouncing and 3 million being non-authenticated. The most popular page is "Contact Us" and 1 million visits are from mobile phones.
- The document discusses integrating various Google products like AdWords, Analytics, Places, and Web Master Tools to optimize site usage, traffic, and search engine optimization. It also addresses fixing issues like dormant URLs, redirecting, and updating site maps.
- A diagram shows how the various Google products interact and influence each other and site management. It indicates the need to better integrate data across products to improve decisions on content, marketing, and site architecture.
Social media presentation

The document discusses online reputation management and how positive and negative experiences can be shared widely through various online channels like social media, reviews sites, blogs, and forums. It notes that unhappy customers will share their negative experiences with more people than those who have positive experiences, so maintaining a good online reputation is important for businesses.
More from Valley and Associates (9)
How the Distance Learning Market will Expand in the Coming Years

How the Distance Learning Market will Expand in the Coming Years
Social Media Week Reputation Management Presentation

Social Media Week Reputation Management Presentation
Successful landing page implementation and use for new business acquisition

Successful landing page implementation and use for new business acquisition
1whitepaper graphics
- 1. What is the Gibbs BSIT Program With a Security focus { Network Track Security Track Information Technology Track General Studies Track Liberal Arts Course Work Systems Configuration and Problem Solving Software and Hardware Security Configurations Computer Usage Concepts Advanced Course Work (Senior Level) Capstone/Intership course work Graduation/Career Utilization Introductory Course Work (Foundation) ecrem m oc-E row kteN Inter net Web Deploy Ma s n s a e lg ee riW Co eun rigf uc rie tyS Sy e t i c r u u r c it e y S S y e ti c r u u r c i t e y S S ye tc iru How does system security integrate into the Gibbs BSIT escu arit hy ti f w oc e u e s rge G D ib T b I s SBCo el egl eThï Ak tc taat ct kA ïe Th hT eï A k t c ta at c t k A ï e T h h T e ï A k t c ta at c t k A ï e T h h T e ï A k t c t a a t ct kA ehT ï ïk Tc ha ettA Why the Gibbs BSIT Degree with a focus on system security is so important Virus Fire Walls Cleaning Anti Virus Hackers Stealing Unauthorized Add in’s Planned Operations Non-secure File Transfers Logic Bombs Locks & Passwords Covert Outside Activity PGP IDS Server Up-grades Denial of Service Malicious Code ïes Thne efe DeD f e en hT se ï ï es Th ne e f D eD ef e e h n T s ï ee ïsne Tf he eD
