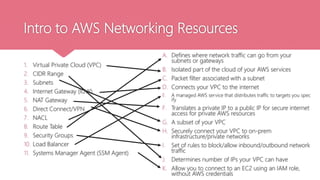
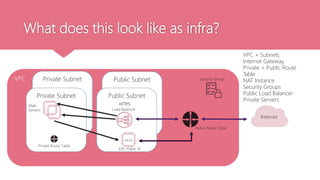
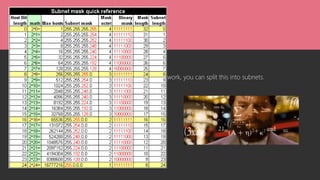
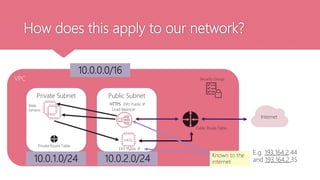
This document provides an agenda for a two-day AWS networking workshop. It introduces Franca as the platform engineer and outlines the code of conduct. The agenda covers networking concepts like VPCs, subnets, security groups and more. It explains what AWS is and the shared responsibility model. Key networking resources like internet gateways, NAT gateways, and route tables are defined. CIDR ranges and IP addressing are also explained. Hands-on activities are planned to help attendees create and understand cloud networking infrastructure on AWS.