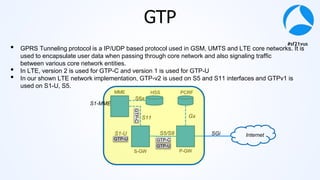
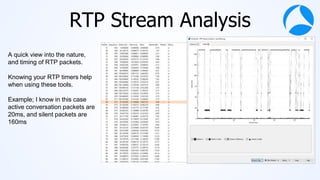
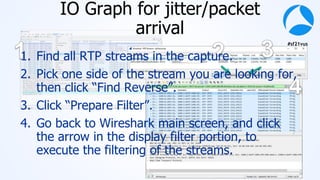
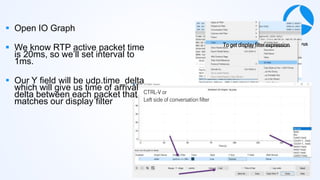
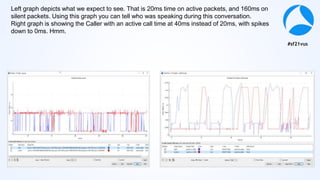
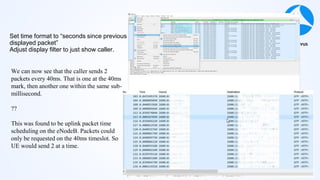
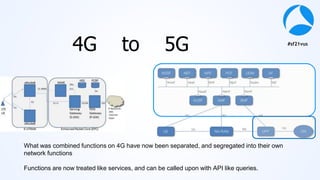
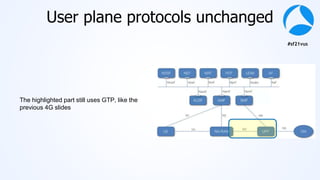
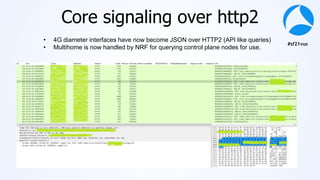
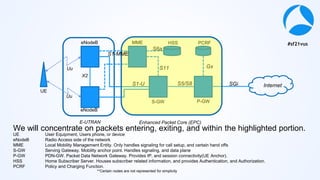
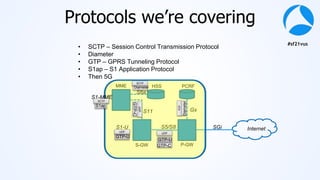
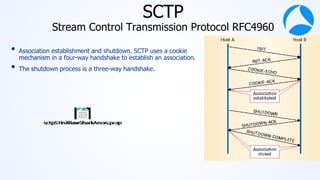
Mark Stout from T-Mobile presented on using Wireshark to analyze LTE and 5G network protocols. He discussed the key protocols used including SCTP, Diameter, GTP, and S1AP. He explained how these protocols are used between different network elements like the UE, eNodeB, MME, S-GW and P-GW. He also provided tips on setting up Wireshark profiles to effectively analyze packets for these protocols.






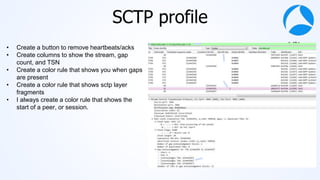



![#sf21vus
Diameter
• All data delivered by diameter is in the form of AVPs (Attribute Value Pairs). Some of these AVP values are used
by the Diameter protocol itself, while others deliver data associated with particular applications that employ
Diameter.
• Ability to exchange messages and deliver AVPs ( Attribute Value Pairs)
• Capabilities negotiation
• Error notification
• Extensibility, required in [RFC2989], through addition of new applications, commands, and AVPs
• Basic services necessary for applications, such as the handling of user sessions or accounting](https://image.slidesharecdn.com/06-221208115706-67dbe1ee/85/06-pptx-17-320.jpg)