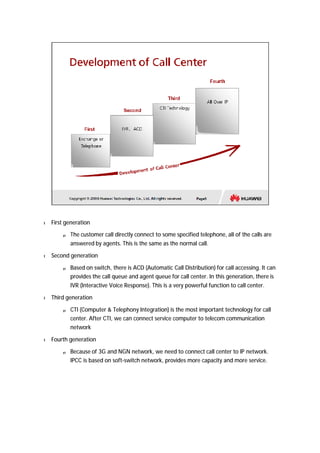
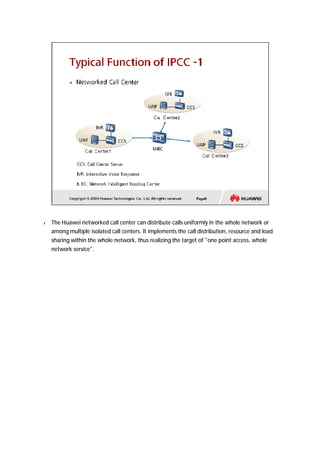
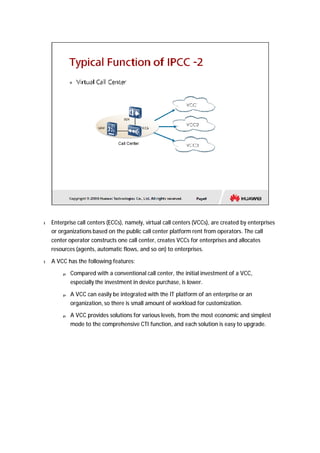
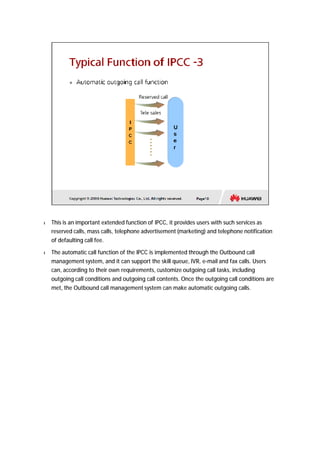
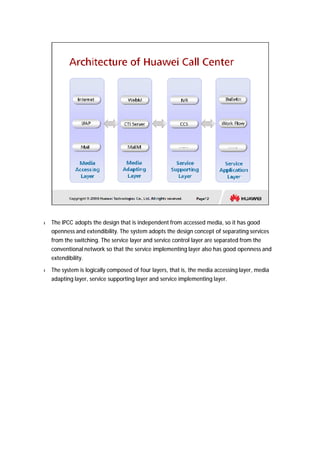
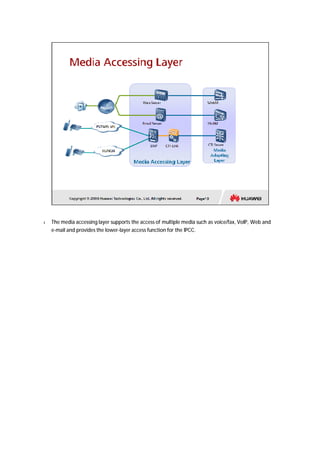
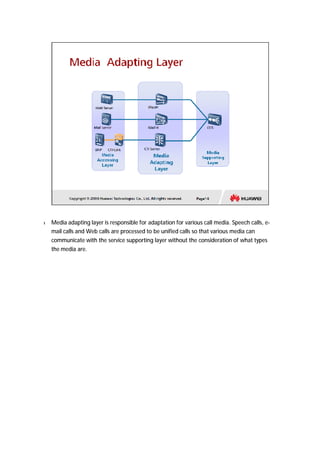
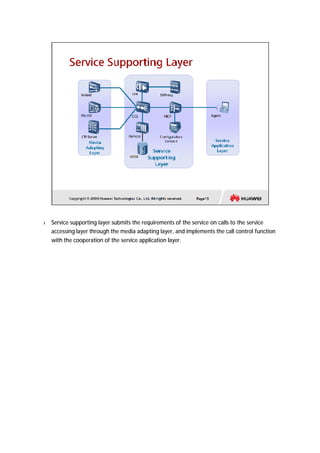
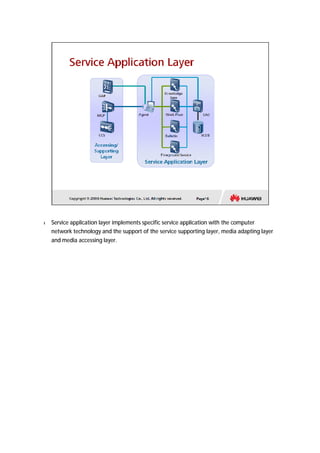
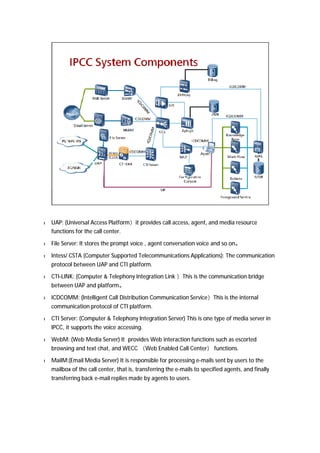
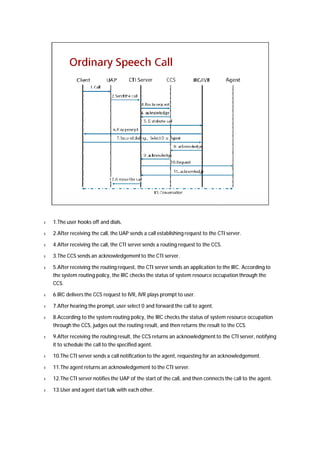
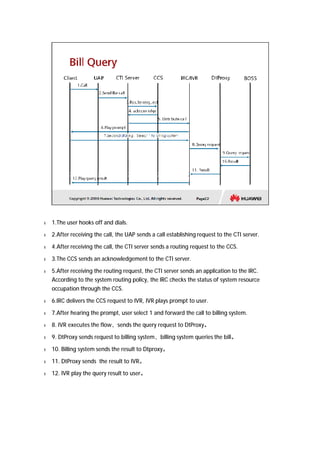
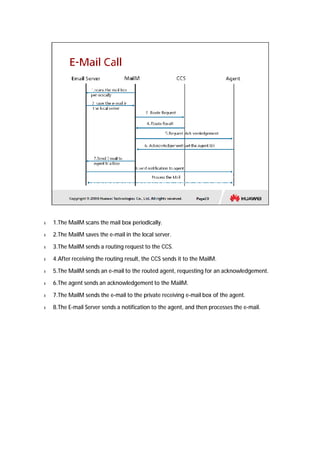
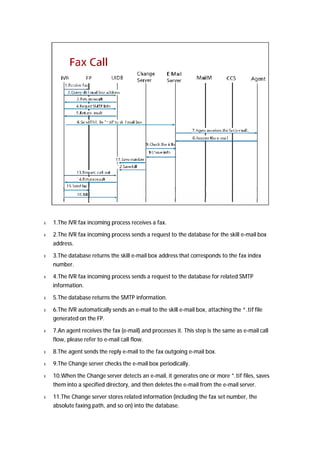
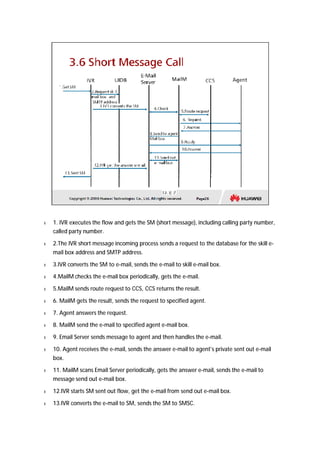
The document provides an overview of call centers and IPCC (Internet Protocol Contact Center) systems. It discusses the evolution of call centers from earlier generations to IP-based systems. It also summarizes the typical components and architecture of an IPCC system, including media servers, databases, and call flows. Key components include the UAP (Universal Access Platform) for call handling, CCS (Call Center Server) for call management, IVR (Interactive Voice Response) for automated services, and various media servers. The document outlines sample call flows for voice, email, fax, and SMS interactions with the IPCC system.