Shift Left continous Testing.pptx
•Download as PPTX, PDF•
0 likes•7 views
Shift left
Report
Share
Report
Share
Recommended
More Related Content
Similar to Shift Left continous Testing.pptx
Similar to Shift Left continous Testing.pptx (20)
Implementing an Application Security Pipeline in Jenkins

Implementing an Application Security Pipeline in Jenkins
Cybersecurity overview - Open source compliance seminar

Cybersecurity overview - Open source compliance seminar
Filling your AppSec Toolbox - Which Tools, When to Use Them, and Why

Filling your AppSec Toolbox - Which Tools, When to Use Them, and Why
Web Application Security for Continuous Delivery Pipelines

Web Application Security for Continuous Delivery Pipelines
Recently uploaded
Recently uploaded (20)
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Azure Monitor & Application Insight to monitor Infrastructure & Application

Azure Monitor & Application Insight to monitor Infrastructure & Application
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Shift Left continous Testing.pptx
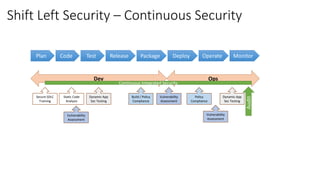
- 1. Shift Left Security – Continuous Security Plan Code Test Package Release Deploy Monitor Operate Dev Ops Continuous Integrated Security Audit Secure SDLC Training Static Code Analysis Vulnerability Assessment Dynamic App Sec Testing Build / Policy Compliance Vulnerability Assessment Vulnerability Assessment Policy Compliance Dynamic App Sec Testing
- 2. CODE BUILD TEST DEPLOY OPERATE MONITOR Manage digital supply chain Automated Software Composition Analysis Automated Container Image Scanning Scan artifact and source code repositories Threat modeling Security Requirements Security SLA cloud providers Risk Analysis Automated Security Testing Automated Static Testing Integrate security tests with unit testing Run-Time application security testing Establish Security Mindset Perform Security Training Establish Security Satellites Perform Continuous Assurance Manual Security Testing Manual Penetration Testing Manual Security Verifications Secrets management Security Configuration Automation Automated Remediation Practice Incident Response Continuous Monitoring Security Controls Application behaviour Ci/CD security metrics System metrics Security SLAs Centralised dashboards Self-service capabilities for dev and ops Continuous feedback from prod to dev Secure the Ci/CD pipeline