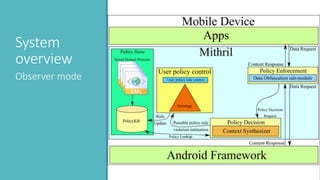
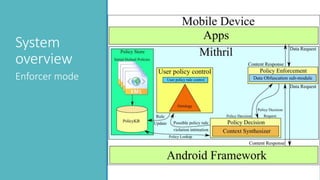
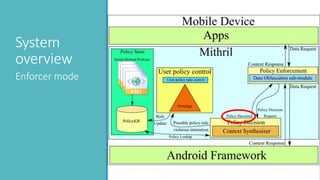
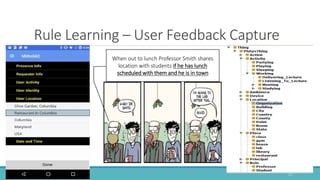
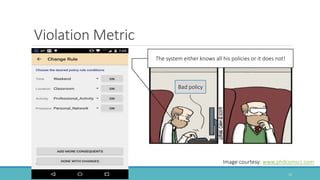
The document introduces Mithril, a framework developed for fine-grained, context-sensitive access control policies on mobile devices, utilizing semantic web technologies. It highlights the importance of user-preferred policy capture and policy enforcement, as well as various rule representations and learning mechanisms. Future work includes validating violation metrics and exploring machine learning for policy generation.