sophos-ep-vs-bitdefender.pdf
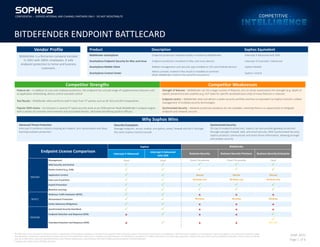
- 1. CONFIDENTIAL- SOPHOS INTERNAL AND CHANNEL PARTNERS ONLY- DO NOT REDISTRIBUTE The information in this document is based on Sophos’s interpretation of data publicly available as of the date it was prepared. Other companies named in the document had no part in its preparation. The information contained in this comparison may be incomplete or inaccurate and is subject to change. The information is intended for informational purposes only and is not intended to be relied upon in making any purchase decision. The information is provided "as is" without warranties of any kind either expressed or implied. This document is Sophos confidential information. Partners may use only the most up-to-date version, and only if permitted by law in their Territory. Distribution to any third party other than a Sophos authorized partner is strictly prohibited. Copyright 2022 Sophos Group. All Rights Reserved. JUNE 2022 Page 1 of 6 Competitor Strengths Competitor Weaknesses Feature set – In addition to core anti-malware protection, the endpoint has a broad range of supplementary features such as application whitelisting, device control and web control Strength of features – Bitdefender can list a large number of features, but on closer examination the strength (e.g. depth of exploit prevention) and usability (e.g. DLP looks for specific words/phrases only) of many features is reduced Test Results – Bitdefender often performs well in tests from 3rd parties such as AV-Test and AV-Comparatives Endpoint centric – Bitdefender does not deliver a wider security portfolio and has no equivalent to Sophos Central’s unified management of multiple security technologies Popular OEM choice – Its inclusion in several 3rd party security tools as an OEM partner feeds Bitdefender’s analysis engine with a variety of customer environments and associated threats, ultimately benefiting product efficacy Synchronized Security – Network protection products are not available, meaning there is no opportunity to integrate endpoint and network security Why Sophos Wins Advanced Threat Protection Intercept X combines industry leading anti-exploit, anti-ransomware and deep learning malware protection. Security Ecosystem Manage endpoint, server, mobile, encryption, email, firewall and Wi-Fi through the same Sophos Central console. Synchronized Security On top of endpoint protection, Sophos can also provide gateway protection through next-gen firewall, web, and email security. With Synchronized Security, Sophos products communicate and share threat information, allowing stronger and simpler security. Endpoint License Comparison Sophos Bitdefender Intercept X Advanced Intercept X Advanced with XDR Business Security Business Security Premium Business Security Enterprise Management Cloud Cloud Cloud / On-premise Cloud / On-premise Cloud PREVENT Web Security and Control Device Control (e.g. USB) Application Control Manual Manual Manual Data Loss Prevention Windows only Windows only Windows only Exploit Prevention Machine Learning DETECT Malicious Traffic Detection (MTD) × × × Ransomware Protection Windows Windows Windows Active Adversary Mitigations × × × RESPOND Synchronized Security Heartbeat × × × Endpoint Detection and Response (EDR) × × × Extended Detection and Response (XDR) × × × (EP only) Vendor Profile Product Description Sophos Equivalent Bitdefender is a Romanian company founded in 2001 with 1800+ employees. It sells endpoint protection to home and business customers. Bitdefender GravityZone Endpoint protection installed locally or hosted by Bitdefender Intercept X Advanced with XDR GravityZone Endpoint Security for Mac and Linux Endpoint protection installed on Mac and Linux devices Intercept X Essentials / Advanced GravityZone Mobile Client Mobile management and security app installed on iOS and Android devices Sophos Mobile GravityZone Control Center Admin console, hosted in the cloud or installed on-premise (Note: Bitdefender Central is the portal for consumers) Sophos Central CONFIDENTIAL – SOPHOS INTERNAL AND CHANNEL PARTNERS ONLY - DO NOT REDISTRIBUTE BITDEFENDER ENDPOINT BATTLECARD
- 2. CONFIDENTIAL- SOPHOS INTERNAL AND CHANNEL PARTNERS ONLY- DO NOT REDISTRIBUTE The information in this document is based on Sophos’s interpretation of data publicly available as of the date it was prepared. Other companies named in the document had no part in its preparation. The information contained in this comparison may be incomplete or inaccurate and is subject to change. The information is intended for informational purposes only and is not intended to be relied upon in making any purchase decision. The information is provided "as is" without warranties of any kind either expressed or implied. This document is Sophos confidential information. Partners may use only the most up-to-date version, and only if permitted by law in their Territory. Distribution to any third party other than a Sophos authorized partner is strictly prohibited. Copyright 2022 Sophos Group. All Rights Reserved. JUNE 2022 Page 2 of 6 Feature Shoot-Out Sophos Bitdefender See these Detailed Comparison sections for more info Synchronized Security × ‘Synchronized Security’ Deep Learning × ‘Machine Learning’ 25+ Exploit Prevention Techniques × ‘Exploit Prevention’ Server Specific Policies × ‘Server Protection’ Fully managed response × ‘Managed Detection and Response (MDR)’ Third Party Views Comments Context Gartner Bitdefender remains in the ‘Niche Players’ quadrant of the 2021 Gartner Magic Quadrant for Endpoint Protection. The report notes solid performance results in public tests, although cautions that “The Bitdefender EDR capability lacks advanced threat hunting”. Sophos is placed in the Leaders quadrant for the 12th year. AV-Test Bitdefender performs well and receives high scores in these tests. AV-Test looks at Protection, Performance and Usability. Forrester Wave Bitdefender dropped to the ‘Strong Performers’ section of the 2021 Forrester Wave Endpoint Security Suite. The report highlighted Bitdefender’s expansion over the last two years, although noted a lack of advanced threat hunting and detection capabilities. Sophos was named a Strong Performer in this report. SE Labs Bitdefender has not participated in SE Labs tests in 2022. It came out just behind Sophos in the Small Business test for Q4, 2021. Sophos achieved the AAA rating across Enterprise, SMB, and consumer products. Bitdefender last participated in the enterprise test in July-September 2020 with decent results coming in just behind Sophos. SE Labs named Sophos Intercept X the Best Small Business Endpoint Product, 2020 and best Enterprise Endpoint, 2021. Watch Out For Lightweight Agent Customer feedback indicates the Bitdefender agent generally has only a light impact on machine performance. Increased Awareness Although Bitdefender has traditionally been associated with consumers and small businesses, it is expanding rapidly and may come up during competitive situations with mid-size and enterprise customers. Client Firewall Bitdefender provides a client firewall and the ability to configure granular rules from the GravityZone admin console.
- 3. CONFIDENTIAL- SOPHOS INTERNAL AND CHANNEL PARTNERS ONLY- DO NOT REDISTRIBUTE The information in this document is based on Sophos’s interpretation of data publicly available as of the date it was prepared. Other companies named in the document had no part in its preparation. The information contained in this comparison may be incomplete or inaccurate and is subject to change. The information is intended for informational purposes only and is not intended to be relied upon in making any purchase decision. The information is provided "as is" without warranties of any kind either expressed or implied. This document is Sophos confidential information. Partners may use only the most up-to-date version, and only if permitted by law in their Territory. Distribution to any third party other than a Sophos authorized partner is strictly prohibited. Copyright 2022 Sophos Group. All Rights Reserved. JUNE 2022 Page 3 of 6 Detailed Comparison How Sophos does it How Bitdefender does it How we win Synchronized Security With synchronized security, products communicate with each other both across the network and on endpoints to mitigate risks and stop data loss. Security information is shared and acted on automatically, isolating infected endpoints before the threat can spread and slashing incident response time. Bitdefender does not have next-gen firewalls, meaning it cannot offer the same coordinated threat response. The customer would be required to purchase separate products to protect their gateway, which would operate in isolation from the endpoint. Simple setup, powerful features Ask: If your firewall alerted you to suspicious traffic from an IP address on your network, how long would it take you to track down the computer, isolate it from the network? Show: Enable Synchronized Security within a matter of clicks and demonstrate the XG Firewall automatically isolating a compromised endpoint client. Exploit Prevention Sophos anti-exploit technology protects against the techniques that attackers may use to exploit a software vulnerability. Intercept X delivers more than 25 exploit prevention techniques to ensure protection against attacks that leverage previously unknown vulnerabilities. Bitdefender has integrated ‘Enhanced Anti-Exploit’ into the Advanced Threat Control component of the endpoint. The feature works by monitoring potentially vulnerable applications for exploit behavior, however very little information is available its actual protection capabilities. Bitdefender also offer a Hyper-Detect module, which appears positioned as the more in-depth exploit prevention component. Again, there is limited information on what actual techniques it is able to protection against. Hyper-Detect is only available through the upper license suites (Elite and Ultra). Overall, there is nothing to indicate Bitdefender delivers anything like the range of exploit protection that is available through Intercept X. Depth of exploit protection Ask: What would it mean to you if you could run one of the industry’s most comprehensive exploit protection without in-depth configuration? Point out: Sophos Intercept X covers more than 25 types of exploit prevention techniques. Machine Learning Intercept X’s deep learning model detects unknown malware and potentially unwanted applications. The model can take a file, extract millions of features, run it through the host-based model, and determine if it is malicious before it executes. It does all of this in about 20 milliseconds with a model that is under 20MB in size. Our machine learning experience began as part of a 2010 DARPA project, and we have proven high speed, low impact performance. Bitdefender endpoint uses local and cloud-based machine learning models. It is unclear which actual models are used, but there is nothing to indicate it uses Deep Learning models like those within Intercept X. Proven effectiveness Show: Our extensive publications on our website, Invincea NSS Labs report, invite the customer to look at historic VirusTotal feedback. Ransomware Protection CryptoGuard technology detects ransomware through its behavior, stopping it from encrypting files, and then automatically rolls back any files that were encrypted before detection. WipeGuard protects from attacks that encrypt the MBR and render the machine unable to boot into the operating system. Ransomware Vaccine Bitdefender has integrated the previously standalone ‘Ransomware Vaccine’ tool into GravityZone endpoint. It works by tricking malware into thinking a machine is already infected and does not need to be re-infected, however it only works with a limited number of ransomware families meaning it is likely to struggle to keep up with new techniques. Comprehensive protection- behavioral detection protects against the latest ransomware
- 4. CONFIDENTIAL- SOPHOS INTERNAL AND CHANNEL PARTNERS ONLY- DO NOT REDISTRIBUTE The information in this document is based on Sophos’s interpretation of data publicly available as of the date it was prepared. Other companies named in the document had no part in its preparation. The information contained in this comparison may be incomplete or inaccurate and is subject to change. The information is intended for informational purposes only and is not intended to be relied upon in making any purchase decision. The information is provided "as is" without warranties of any kind either expressed or implied. This document is Sophos confidential information. Partners may use only the most up-to-date version, and only if permitted by law in their Territory. Distribution to any third party other than a Sophos authorized partner is strictly prohibited. Copyright 2022 Sophos Group. All Rights Reserved. JUNE 2022 Page 4 of 6 Detailed Comparison How Sophos does it How Bitdefender does it How we win Endpoint Detection & Response (EDR and XDR) Intercept X Advanced with XDR suits both IT administrators and security analysts. While it is accessible to IT generalists by replicating tasks normally performed by skilled analysts, it also provides the core manual tools that trained analysts would expect. Threat Visibility: Deep Learning Threat Indicators and Analysis For the grey area between known-good and known-bad, deep (machine) learning prioritizes a list of suspicious files for further investigation. The comprehensive file analysis report enables customers to quickly determine if a suspicious file should be blocked or allowed. Threat Hunting: Live Discover search: Allows customers to quickly discover IT operations issues or to hunt down suspicious activity on both Windows and Mac. - On-disk data: Windows and Mac endpoint data store with super detailed, live data covering up to the last 90 days - Cloud data lake: Cross product data with 30 days’ worth of data - XDR Platforms: Endpoint, Server, Firewall, Email, Mobile, Cloud Optix, Microsoft 365 connector (Azure AD, Exchange, Teams, Sharepoint) - Air to ground reconnaissance: Quickly scan an entire estate and then drill down to file content on a single device - Flexible: Includes out-of-the-box, fully customizable SQL queries. Customers can create completely new, custom queries - Schedule: Retrieve critical data from the data lake overnight - Comprehensive: Provides up to 90 days fast access to current and historical on-disk data. Data includes insight into artifacts’ reputation and machine learning scores from SophosLabs and Sophos AI Response: Automatic response – The intelligent Sophos endpoint agent can automatically clean up or block threats. It is also capable of isolating the endpoint. Live Response command line: Customers can remotely access Windows, Mac and Linux devices via a native command line to perform further investigation, install and uninstall software, or remediate any issues that Intercept X cannot address automatically. It can also be used for IT operational actions such as rebooting or installing and uninstalling software. GravityZone Ultra includes EDR functionality. Since retiring its network sensor in May 2021, it rebranded its XDR solution to “XEDR” (eXtended EDR). This refers to detection capabilities across workstations, servers and containers. This includes network analysis from the endpoints, not a separate sensor. Threat Visibility XEDR provides a visual representation of the threat chain along with details about files and processes involved in a detection. Customers can submit files to a cloud sandbox for more detailed analysis, although there is no equivalent of Sophos’ Deep Learning Threat Indicators and Malware Analysis feature. Hunting – Threat hunting capabilities are very limited to only cover items that are linked to a detection and does not allow customers to search for indicators of compromise across endpoints. Bitdefender points to its MDR service where the Bitdefender endpoint is used as part of a third-party EDR tool. It does not ingest data from email. Response The administrator can take remediation actions such as quarantining a file or isolating an endpoint. A remote shell command line is available. Automation – Bitdefender does provide automatic blocking and clean up. However, it does not have an equivalent to Synchronized Security that mean it can remotely isolate endpoint and then reinstate connectivity once back to a healthy state. Endpoints can only be isolated manually. Guided incident response Show: Deep Learning Malware Analysis helps easily identify similarities with known malicious files. Application control Pre-populated- Administrators can control installation, track usage or block execution of unauthorized applications within a few clicks. Choose from a pre-populated list of applications that is kept up to date by Sophos Labs. Reliable – detection is maintained and tested by Sophos Labs. Users are not able to circumvent detection. Platform independent – it works transparently across platforms Bitdefender offers application control through its Application ‘blacklisting’ feature (part of Content Control). The administrator must either specify the path of each application executable or run an ‘Application Discovery’ task to generate a list of applications present on endpoints. Applications will no longer be blocked if moved or the name is changed. Compared to Sophos, the Bitdefender application blacklisting requires more effort, is more prone to mistakes, and is easily circumvented. A ‘whitelisting’ feature is available, but only with the on-prem console. Simply choose applications from a pre-populated list Ask: How do you currently control which applications are allowed on your network? Show: Demonstrate how easy it is in Sophos Central to create a policy that blocks file sharing tools such as BitTorrent.
- 5. CONFIDENTIAL- SOPHOS INTERNAL AND CHANNEL PARTNERS ONLY- DO NOT REDISTRIBUTE The information in this document is based on Sophos’s interpretation of data publicly available as of the date it was prepared. Other companies named in the document had no part in its preparation. The information contained in this comparison may be incomplete or inaccurate and is subject to change. The information is intended for informational purposes only and is not intended to be relied upon in making any purchase decision. The information is provided "as is" without warranties of any kind either expressed or implied. This document is Sophos confidential information. Partners may use only the most up-to-date version, and only if permitted by law in their Territory. Distribution to any third party other than a Sophos authorized partner is strictly prohibited. Copyright 2022 Sophos Group. All Rights Reserved. JUNE 2022 Page 5 of 6 Detailed Comparison How Sophos does it How Bitdefender does it How we win Web Protection and Control Sophos URL filtering blocks users from accessing websites that are hosting malware or phishing attacks. Bitdefender provides web protection through the ‘Traffic’ and ‘Web’ sections of Content Control policies. The Traffic component blocks access to malicious websites and prevents malware being downloaded. The Web module allows administrators to block/allow access to certain website categories (e.g. Games), and also lets them specify the time during which the policy is enforced. Prevent users from inappropriate and dangerous websites Ask: How do you stop users from accessing websites that are inappropriate or hosting malware? Device Control We enable you to define which storage devices or network interfaces to block, set to read only or allow full access to. It is simple to set exceptions for specific devices, as they can easily be identified in the event log. It is not necessary to install or enable any additional modules in order to get up and running with this feature. Devices can be blocked or allowed, and exclusions for specific models can be added for more granular control. In order to use this feature, it is necessary to install the Device Control component. If the component is not installed as part of the main Bitdefender agent installation, the administrator would need to create and push out a task to the machine before the feature could be used. No additional component required Data Loss Prevention (DLP) DLP is integrated into Sophos endpoints meaning no additional plugins are required. There are a large set of predefined detection rules for common data types, and, if required, customers can build their own custom rules using regular expressions. Bitdefender GravityZone includes a Data Protection module, which allows the administrator to create rules to detect data being moved through web or email traffic. However, there are no pre-defined rules, meaning the administrator has to manually create a rule for each type of data they want to protect. Additionally, the rules do not allow the customer to block data types (e.g. block all credit card numbers) and instead force them to specify the actual values to be identified (in the case of credit cards, at least 5 digits from each card). This lack of control means that the customer is likely to end up creating very specific detections that only block single credit cards or email addresses. Alternatively, generic detections on sensitive key words e.g. “Intercept X” are used, but such broad detections are likely to impact on legitimate business work. Simple configuration Ask: What measures do you have in place to prevent important data leaving the organization? How much time do you have available to tune these settings? Management Anywhere anytime Cloud based Sophos Central provides protection for users wherever they are and a management interface that is incredibly easy to use. Policies can be assigned by user or by device. Bitdefender products are managed through the ‘GravityZone’ central management console. The console is available either on-premise or cloud hosted, although mobile devices can only be managed with an on-premise installation. Administrators access the GravityZone console through a web browser, although the server itself is a Linux based virtual machine. On-premise customers need to import and run the GravityZone server on a virtualization platform such as VMware, Citrix or Hyper-V. Intuitive management console Show: Get Sophos Central in front of the prospect, either in person, as a trial or with the online demo. Nothing speaks to our strengths as strongly as seeing the product first hand. Server Protection Advanced protection features such as deep learning, exploit prevention and anti-ransomware are coupled with server specific capabilities such as cloud workload discovery, server lockdown and automatic scan exclusions. Unlike solutions that are designed for end-user workstations, Sophos Server Protection specifically protects servers while minimizing the impact on performance. Policies There is no concept of server specific policies or features. ‘Security Servers’ can be configured, but these are designed to relay communication between endpoints and the main GravityZone console, or to stagger scanning on virtual machines. Virtual machine hosts and guests are grouped separately from physical devices; however, the same policy options are available for both. The customer does not benefit from server protection features such as file integrity monitoring (FIM), AWS visualization and automatic scan exclusions. Lockdown The Application Control feature can be used to achieve a similar function to Server Lockdown, as it allows the user to block only known applications from running. However, it requires more steps than Server Lockdown, as it is necessary for the administrator to first run an Application Discovery task to determine what programs exist on the client machine. Update processes associated with these applications also need to be manually identified and added by the customer. Policies tailored to server operating systems Show: Cloud workload discovery in Sophos Central displays AWS EC2 instances and their health status
- 6. CONFIDENTIAL- SOPHOS INTERNAL AND CHANNEL PARTNERS ONLY- DO NOT REDISTRIBUTE The information in this document is based on Sophos’s interpretation of data publicly available as of the date it was prepared. Other companies named in the document had no part in its preparation. The information contained in this comparison may be incomplete or inaccurate and is subject to change. The information is intended for informational purposes only and is not intended to be relied upon in making any purchase decision. The information is provided "as is" without warranties of any kind either expressed or implied. This document is Sophos confidential information. Partners may use only the most up-to-date version, and only if permitted by law in their Territory. Distribution to any third party other than a Sophos authorized partner is strictly prohibited. Copyright 2022 Sophos Group. All Rights Reserved. JUNE 2022 Page 6 of 6 Detailed Comparison How Sophos does it How Bitdefender does it How we win Mobile Protection and Management Consolidated Management Sophos Central’s unified admin interface enables customers to manage mobile devices alongside endpoint protection and other Sophos technologies such as encryption, email or wi-fi. For customers who prefer an on-premise installation, there is feature parity across the platforms, meaning customers do not miss out on functionality by selecting one option over another. Secure A rich set of device management capabilities and powerful containers secure sensitive business information on mobile devices, with leading anti-malware technology protecting users and devices from malicious content and apps. Lacks Advanced Features Mobile protection and management is available, but only when using an on- premise installation of the GravityZone management console. It is possible to enforce certain mobile security measures, such as lock screen passwords, but more advanced features, such as blocking a camera or iCloud backups, are not available. The compliance settings are comparatively generic as they allow the administrator to block or wipe the uncompliant devices, but do not allow more specific options such as removing only email or Wi-Fi if the device is jailbroken or has not checked in since a certain period. Malware scanning is available for Android devices; however, the scanning is performed in the cloud rather than on the mobile device itself. Cloud managed mobile management and security Advanced features such as containerization or secure email app Ask: What is your plan for managing mobile devices? Show: Sophos Mobile available within the unified Sophos Central management console Additional Security Technologies In addition to endpoint protection, Sophos Central allows customers to protect a range of other areas all through the same management console. These include: ▪ Device Encryption ▪ Email Gateway ▪ Mobile Security and Control ▪ Wireless Networks ▪ Phish Threat (user education) ▪ XG Firewall ▪ Cloud Optix Bitdefender offers mobile device management and device encryption. However, it does not provide any of the other additional security offerings that Sophos Central does. Reduce administration through Sophos Central Point out: Customers can consolidate management of various security technologies through the Sophos Central console Managed Detection and Response (MDR) Sophos Managed Threat Response (MTR) is a fully managed threat hunting, detection and response service that provides organizations with a dedicated 24/7 security team to not only detect but neutralize the most sophisticated and complex threats. Regardless of the service tier selected (Standard or Advanced), customers can opt to have the Sophos MTR team operate in any of three Response Modes to accommodate their unique needs. - Fully managed – allows customer to effectively outsource its SOC if needed - Three operational modes – Notify, Collaborate, or Authorize - Any size customer – from SMB to enterprise - Best protection – based on Intercept X ensure maximum protection GravityZone Managed Detection and Response (MDR is available in two service tiers: Advanced/Premium and Enterprise. They don’t appear to have response modes like us but do offer automated pre-approved response and expert recommendations. The pre-approved response actions are stop process, block/delete/quarantine file, block IP/port and isolate host. According to Bitdefender’s site, they provide “automated remediation” and “custom incident response actions based on playbooks.” This is what we refer to as “pushbutton response.” In other words, if it can be scripted and automated, the Bitdefender SOC can push a button and kick off the script. Unlike Sophos, Bitdefender is not providing hands-on-keyboard response that addresses the unique circumstances of a given incident. - MTR is a fully managed service - Strong endpoint protection and automated cleanup minimizes number of alerts - Flexible mode of operation and authorized actions mean that customers can outsource SOC to Sophos
