SODA-IIoT4Factory: Blockchain to keep the A.I. of your Intrusion Detection System up-to-date
•
1 like•198 views
Co-designed with FPC Ingénierie, SODA-IIoT4Factory offers a secure way to update CyPRES rule engines & cyber security/attack models. CyPRES is an intelligent IDS that strengthens industrial information systems. It learns then verifies the operation and behaviour of the system to the lowest level of detail. It detects the first signs of attacks before damage is incurred.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
Presentation by M. Charlier and B. Quoitin, UMONSTowards Large-Scale, High-Density Indoor Ultra Wideband Geolocation Systems

Towards Large-Scale, High-Density Indoor Ultra Wideband Geolocation SystemsAgence du Numérique (AdN)
Presentation by MSc. Denis Bruno Viríssimo, Researcher, iptApplying IoT to the Management of Natural Disasters Risk NIAGRISK - A digital...

Applying IoT to the Management of Natural Disasters Risk NIAGRISK - A digital...Agence du Numérique (AdN)
More Related Content
What's hot
Presentation by M. Charlier and B. Quoitin, UMONSTowards Large-Scale, High-Density Indoor Ultra Wideband Geolocation Systems

Towards Large-Scale, High-Density Indoor Ultra Wideband Geolocation SystemsAgence du Numérique (AdN)
Presentation by MSc. Denis Bruno Viríssimo, Researcher, iptApplying IoT to the Management of Natural Disasters Risk NIAGRISK - A digital...

Applying IoT to the Management of Natural Disasters Risk NIAGRISK - A digital...Agence du Numérique (AdN)
What's hot (20)
The cellular network: a vital link in the world of drones

The cellular network: a vital link in the world of drones
Experimenting with Real Application-specific QoS Guarantees in a Large-scale ...

Experimenting with Real Application-specific QoS Guarantees in a Large-scale ...
FIWARE MEXICO WorkShop 2016 - 7. Example of FIWARE Applications by INFOTEC

FIWARE MEXICO WorkShop 2016 - 7. Example of FIWARE Applications by INFOTEC
Towards Large-Scale, High-Density Indoor Ultra Wideband Geolocation Systems

Towards Large-Scale, High-Density Indoor Ultra Wideband Geolocation Systems
11th International Conference on Networks & Communications (NeCoM 2019)

11th International Conference on Networks & Communications (NeCoM 2019)
11th International Conference on Networks & Communications (NeCoM 2019)

11th International Conference on Networks & Communications (NeCoM 2019)
11th International Conference on Networks & Communications (NeCoM 2019)

11th International Conference on Networks & Communications (NeCoM 2019)
FIWARE Global Summit - BIIOT: Blockchain In Internet of Things

FIWARE Global Summit - BIIOT: Blockchain In Internet of Things
Ieee 2020 21 iot in pondicherry,final year projects in pondicherry,project ce...

Ieee 2020 21 iot in pondicherry,final year projects in pondicherry,project ce...
Applying IoT to the Management of Natural Disasters Risk NIAGRISK - A digital...

Applying IoT to the Management of Natural Disasters Risk NIAGRISK - A digital...
Internet of (weather) things on a grassroot LoRaWAN network

Internet of (weather) things on a grassroot LoRaWAN network
Similar to SODA-IIoT4Factory: Blockchain to keep the A.I. of your Intrusion Detection System up-to-date
To Get any Project for CSE, IT ECE, EEE Contact Me @ 09666155510, 09849539085 or mail us - ieeefinalsemprojects@gmail.com-Visit Our Website: www.finalyearprojects.orgIEEE 2014 DOTNET NETWORKING PROJECTS Network intrusion detection system using...

IEEE 2014 DOTNET NETWORKING PROJECTS Network intrusion detection system using...IEEEMEMTECHSTUDENTPROJECTS
To Get any Project for CSE, IT ECE, EEE Contact Me @ 09666155510, 09849539085 or mail us - ieeefinalsemprojects@gmail.com-Visit Our Website: www.finalyearprojects.org2014 IEEE DOTNET NETWORKING PROJECT Network intrusion detection system using ...

2014 IEEE DOTNET NETWORKING PROJECT Network intrusion detection system using ...IEEEFINALSEMSTUDENTSPROJECTS
Similar to SODA-IIoT4Factory: Blockchain to keep the A.I. of your Intrusion Detection System up-to-date (20)
IoT Cyber+Physical+Social Engineering Attack Security (v0.1.6 / sep2020)

IoT Cyber+Physical+Social Engineering Attack Security (v0.1.6 / sep2020)
How stuxnet spreads – a study of infection paths in best practice systems

How stuxnet spreads – a study of infection paths in best practice systems
Transforming Smart Building Cybersecurity Strategy for the Age of IoT

Transforming Smart Building Cybersecurity Strategy for the Age of IoT
IEEE 2014 DOTNET NETWORKING PROJECTS Network intrusion detection system using...

IEEE 2014 DOTNET NETWORKING PROJECTS Network intrusion detection system using...
2014 IEEE DOTNET NETWORKING PROJECT Network intrusion detection system using ...

2014 IEEE DOTNET NETWORKING PROJECT Network intrusion detection system using ...
Domain 7 of CEH Mobile Platform, IoT, and OT Hacking.pptx

Domain 7 of CEH Mobile Platform, IoT, and OT Hacking.pptx
Critical Infrastructure Assessment Techniques to Prevent Threats and Vulnerab...

Critical Infrastructure Assessment Techniques to Prevent Threats and Vulnerab...
Ot ics cyberattaques dans les organisations industrielles 

Ot ics cyberattaques dans les organisations industrielles
Sb securing-industrial-control-systems-with-fortinet

Sb securing-industrial-control-systems-with-fortinet
Augmentation of a SCADA based firewall against foreign hacking devices 

Augmentation of a SCADA based firewall against foreign hacking devices
Detect Network Threat Using SNORT Intrusion Detection System

Detect Network Threat Using SNORT Intrusion Detection System
Engineering Internship Report - Network Intrusion Detection And Prevention Us...

Engineering Internship Report - Network Intrusion Detection And Prevention Us...
More from Nabil Bouzerna
More from Nabil Bouzerna (12)
Nabil bouzerna - Mémoire d'ingénieur / Master Thesis ENSIIE - ADVESTIGO - 2007 

Nabil bouzerna - Mémoire d'ingénieur / Master Thesis ENSIIE - ADVESTIGO - 2007
Bitcoin: A Peer-to-Peer Electronic Cash System (traduction fr)

Bitcoin: A Peer-to-Peer Electronic Cash System (traduction fr)
La plateforme CHESS un outil pour l’analyse comparative des technologies de c...

La plateforme CHESS un outil pour l’analyse comparative des technologies de c...
Audition France Stratégie du 9 mars 2017 "Blockchain : les cas d'usage à l'ép...

Audition France Stratégie du 9 mars 2017 "Blockchain : les cas d'usage à l'ép...
Expocrise - L’exploitation des médias sociaux avant, pendant et après la cris...

Expocrise - L’exploitation des médias sociaux avant, pendant et après la cris...
Quaero a research and innovation program addressing automatic processing of m...

Quaero a research and innovation program addressing automatic processing of m...
Future@SystemX - Nabil Bouzerna - Experiment IMM Project

Future@SystemX - Nabil Bouzerna - Experiment IMM Project
ESILV Nabil Bouzerna Architecture de systèmes de traitement de l'information ...

ESILV Nabil Bouzerna Architecture de systèmes de traitement de l'information ...
Recently uploaded
ICT role in 21st century education
Role of ICT in education
Is importance to you knowing ICT role in 21st century education and it's challenges.pdf

ICT role in 21st century education and it's challenges.pdfIslamia university of Rahim Yar khan campus
Recently uploaded (20)
BDSM⚡Call Girls in Sector 93 Noida Escorts >༒8448380779 Escort Service

BDSM⚡Call Girls in Sector 93 Noida Escorts >༒8448380779 Escort Service
AWS Data Engineer Associate (DEA-C01) Exam Dumps 2024.pdf

AWS Data Engineer Associate (DEA-C01) Exam Dumps 2024.pdf
BDSM⚡Call Girls in Sector 97 Noida Escorts >༒8448380779 Escort Service

BDSM⚡Call Girls in Sector 97 Noida Escorts >༒8448380779 Escort Service
If this Giant Must Walk: A Manifesto for a New Nigeria

If this Giant Must Walk: A Manifesto for a New Nigeria
No Advance 8868886958 Chandigarh Call Girls , Indian Call Girls For Full Nigh...

No Advance 8868886958 Chandigarh Call Girls , Indian Call Girls For Full Nigh...
SaaStr Workshop Wednesday w/ Lucas Price, Yardstick

SaaStr Workshop Wednesday w/ Lucas Price, Yardstick
Busty Desi⚡Call Girls in Sector 51 Noida Escorts >༒8448380779 Escort Service-...

Busty Desi⚡Call Girls in Sector 51 Noida Escorts >༒8448380779 Escort Service-...
Uncommon Grace The Autobiography of Isaac Folorunso

Uncommon Grace The Autobiography of Isaac Folorunso
The workplace ecosystem of the future 24.4.2024 Fabritius_share ii.pdf

The workplace ecosystem of the future 24.4.2024 Fabritius_share ii.pdf
ICT role in 21st century education and it's challenges.pdf

ICT role in 21st century education and it's challenges.pdf
Dreaming Music Video Treatment _ Project & Portfolio III

Dreaming Music Video Treatment _ Project & Portfolio III
Sector 62, Noida Call girls :8448380779 Noida Escorts | 100% verified

Sector 62, Noida Call girls :8448380779 Noida Escorts | 100% verified
Aesthetic Colaba Mumbai Cst Call girls 📞 7738631006 Grant road Call Girls ❤️-...

Aesthetic Colaba Mumbai Cst Call girls 📞 7738631006 Grant road Call Girls ❤️-...
Bring back lost lover in USA, Canada ,Uk ,Australia ,London Lost Love Spell C...

Bring back lost lover in USA, Canada ,Uk ,Australia ,London Lost Love Spell C...
Air breathing and respiratory adaptations in diver animals

Air breathing and respiratory adaptations in diver animals
SODA-IIoT4Factory: Blockchain to keep the A.I. of your Intrusion Detection System up-to-date
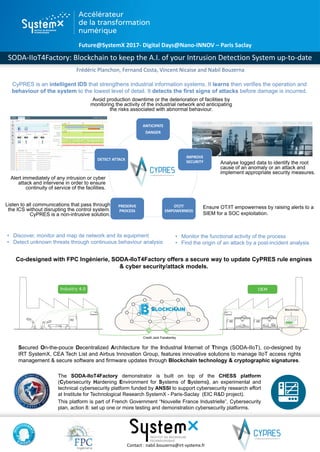
- 1. 11 ANTICIPATE DANGER IMPROVE SECURITY OT/IT EMPOWERNESS PRESERVE PROCESS DETECT ATTACK Future@SystemX 2017- Digital Days@Nano-INNOV – Paris Saclay SODA-IIoT4Factory: Blockchain to keep the A.I. of your Intrusion Detection System up-to-date Contact : nabil.bouzerna@irt-systemx.fr The SODA-IIoT4Factory demonstrator is built on top of the CHESS platform (Cybersecurity Hardening Environment for Systems of Systems), an experimental and technical cybersecurity platform funded by ANSSI to support cybersecurity research effort at Institute for Technological Research SystemX - Paris-Saclay (EIC R&D project). This platform is part of French Government “Nouvelle France Industrielle”, Cybersecurity plan, action 8: set up one or more testing and demonstration cybersecurity platforms. Secured On-the-pouce Decentralized Architecture for the Industrial Internet of Things (SODA-IIoT), co-designed by IRT SystemX, CEA Tech List and Airbus Innovation Group, features innovative solutions to manage IIoT access rights management & secure software and firmware updates through Blockchain technology & cryptographic signatures. Analyse logged data to identify the root cause of an anomaly or an attack and implement appropriate security measures. CyPRES is an intelligent IDS that strengthens industrial information systems. It learns then verifies the operation and behaviour of the system to the lowest level of detail. It detects the first signs of attacks before damage is incurred. Alert immediately of any intrusion or cyber attack and intervene in order to ensure continuity of service of the facilities. Listen to all communications that pass through the ICS without disrupting the control system. CyPRES is a non-intrusive solution. Ensure OT/IT empowerness by raising alerts to a SIEM for a SOC exploitation. Avoid production downtime or the deterioration of facilities by monitoring the activity of the industrial network and anticipating the risks associated with abnormal behaviour. Co-designed with FPC Ingénierie, SODA-IIoT4Factory offers a secure way to update CyPRES rule engines & cyber security/attack models. • Discover, monitor and map de network and its equipment • Detect unknown threats through continuous behaviour analysis • Monitor the functional activity of the process • Find the origin of an attack by a post-incident analysis Frédéric Planchon, Fernand Costa, Vincent Nicaise and Nabil Bouzerna Credit Jack Fazakerley
