The document provides an overview of elliptic curve cryptography including:
1. It discusses the evolution of cryptography from ancient times to modern algorithms like RSA, AES, and Diffie-Hellman key exchange.
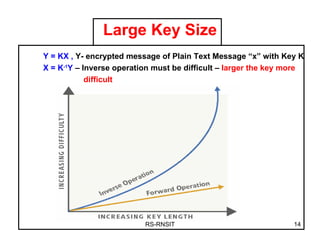
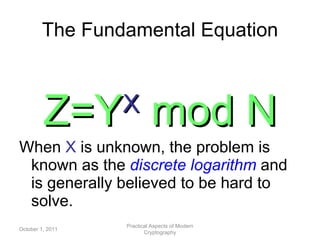
2. It introduces elliptic curve cryptography as an alternative that provides the same level of security with smaller key sizes due to the difficulty of solving the elliptic curve discrete logarithm problem.
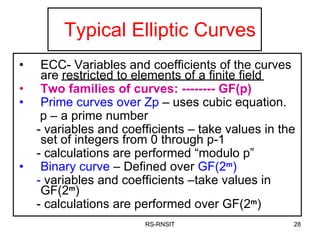
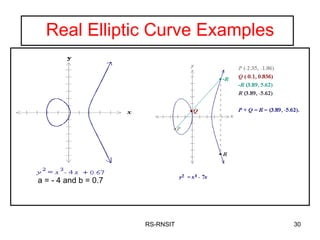
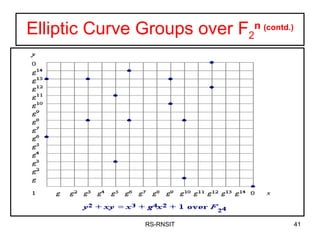
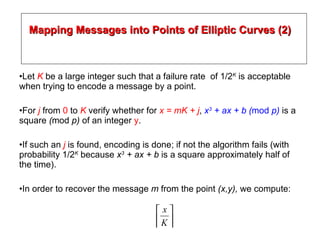
3. It provides examples of elliptic curve groups over prime fields and binary fields, showing how points on the curve satisfy the elliptic curve equation over a finite field.

![Cryptography Definitions 1 . Cryptography (or cryptology ; from Greek κρυπτός, kryptos , "hidden, secret "; and γράφειν , graphein , "writing", or -λογία , -logia , "study", respectively) [1] is the practice and study of hiding information . Modern cryptography intersects the disciplines of mathematics, computer science , and electrical engineering . 2 . Cryptography is the science of information security . The word is derived from the Greek kryptos , meaning hidden. Cryptography is closely related to the disciplines of cryptology and cryptanalysis 3. Discipline or techniques employed in protecting integrity or secrecy of electronic messages by converting them into unreadable (cipher text) form. Only the use of a secret key can convert the cipher text back into human readable (clear text) form. Cryptography software and/or hardware devices use mathematical formulas (algorithms) to change text from one form to another. Source: Internet](https://image.slidesharecdn.com/ecc-mysoreuniv-sept2011-111001114525-phpapp02/85/Mathematics-Towards-Elliptic-Curve-Cryptography-by-Dr-R-Srinivasan-2-320.jpg)















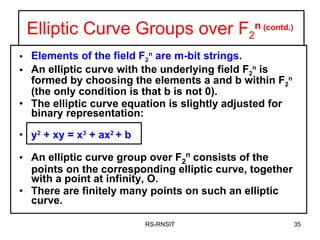
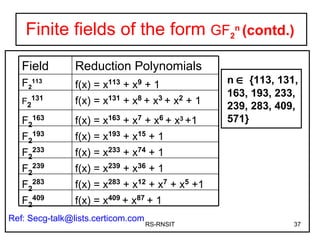
![Finite fields of the form GF 2 n (contd.) Computational considerations: A polynomial f(x) in GF(2 n ) is; f(X) = a n-1 x n-I + a n-2 x n-2 + ….a 1 x + a 0 Uniquely represented by its ‘n’ coefficients (a n-1 , a n-2 , ………a 0 ). a i {0,1} Thus every polynomial in GF(2 n ) can be represented by an n-bit number the coefficients and variables are in finite field Addition: { a n-1 x n-I + a n-2 x n-2 + ….a 1 x + a 0 } +{b n-1 x n-I + b n-2 x n-2 + ….b 1 x + b 0 } = r n-1 x n-I + r n-2 x n-2 + ….r 1 x + r 0 with ri [ai + bi] mod 2 RS-RNSIT](https://image.slidesharecdn.com/ecc-mysoreuniv-sept2011-111001114525-phpapp02/85/Mathematics-Towards-Elliptic-Curve-Cryptography-by-Dr-R-Srinivasan-36-320.jpg)
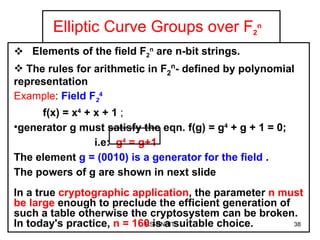
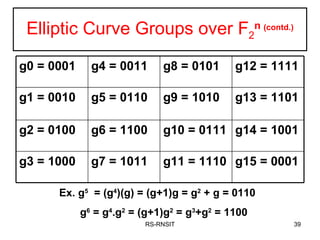

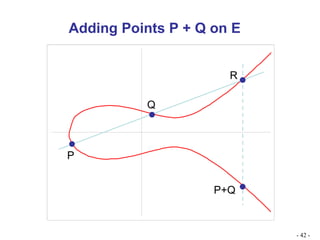
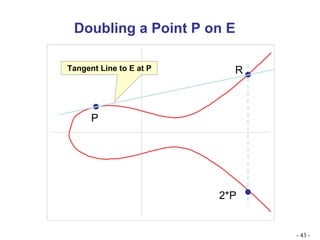
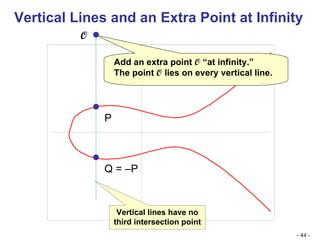
![Algebraic Description of Addition Calculation of Addition over elliptic curves: For two distinct points P = (x p , y p ) and Q = (x Q , y Q ) not negative to each other, Slope of the line ‘l’ that joins them is : = (y Q – y P )/ (x Q – x p ) We can express R = P + Q as follows: x R = 2 – x p – x Q ------------- Eqn1 y R = - y p + (x p – x R ) ----Eqn 2 To add a point to itself, P + P = 2P = R, when y p 0, the expressions are: x R = {[3x 2 p + a]/2y p } 2 – 2 x p y R = {[ 3x 2 p + a]/ 2y p } (x p – x R ) - y p](https://image.slidesharecdn.com/ecc-mysoreuniv-sept2011-111001114525-phpapp02/85/Mathematics-Towards-Elliptic-Curve-Cryptography-by-Dr-R-Srinivasan-47-320.jpg)
![Algebraic Description of Addition (contd.) Actually: = (y Q – y P )/ (x Q – x p ) mod p if P Q and = {[3x 2 p + a]/2y p } mod p if P = Q Example: P = (3, 10) and Q = (9,7) in E 23 (1,1) in y 2 = x 3 + x + 1 = (7-10/9-3)mod 23 = 11 x R = (11 2 -3-9)mod23 = 17 y R = [11(3-17)-10]mod23 =20 So (P+Q) = (17,20) To find 2P = P + P: = [{3(3 2 ) + 1}/2x10] mod23 = (1/4)mod23 Multiplicative inverse of 4 under Z 23 , = (1/4)mid23 = 6 [to check(6x4)mod23 = 1] with xP= xQ = 3 and yP = 10 and substituting in Eqns 1 and 2 on last slide: x R = (6 2 – 3 - 3)mod23 = 30mod23 = 7 y R = {6(3-7) – 10} mod23 = (-34) mod 23 = 12 the point corresponding to 2P = (7, 12)](https://image.slidesharecdn.com/ecc-mysoreuniv-sept2011-111001114525-phpapp02/85/Mathematics-Towards-Elliptic-Curve-Cryptography-by-Dr-R-Srinivasan-48-320.jpg)

![RS-RNSIT Elliptic Curve Digital Signature Algorithm (ECDSA) Proposed by Abdalla , Bellare and Rogaway in 1999. Entity A has domain parameters D = (q, a, b, G, n, h) and public key Q A and private key d A . And entity B has authentic copies of D and Q A . To sign a message m, A does the following: Select a random integer k from [1,n-1]. Compute kG = (x 1 ,y 1 ) and r = x 1 mod n. If r = 0 then go to step 1. Compute k -1 mod n. Compute e = SHA-1(m). Compute s = k -1 {e + d A . r} mod n. If s = 0 then go to step 1. A's signature for the message m is (r, s).](https://image.slidesharecdn.com/ecc-mysoreuniv-sept2011-111001114525-phpapp02/85/Mathematics-Towards-Elliptic-Curve-Cryptography-by-Dr-R-Srinivasan-53-320.jpg)
![RS-RNSIT Elliptic Curve Digital Signature Algorithm (ECDSA) To verify A's signature (r, s) on m, B performs the following steps: Verify that r and s are integers in [1,n-1]. Compute e = SHA-1(m). Compute w = s -1 mod n. Compute u 1 = ew mod n and u 2 = rw mod n. Compute (x 1 ,y 1 ) = u 1 G+ u 2 Q A Compute v = x 1 mod n. Accept the signature if and only if v = r. SHA-1 denotes the 160-bit hash function](https://image.slidesharecdn.com/ecc-mysoreuniv-sept2011-111001114525-phpapp02/85/Mathematics-Towards-Elliptic-Curve-Cryptography-by-Dr-R-Srinivasan-54-320.jpg)
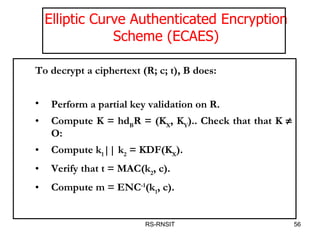
![RS-RNSIT Analogue of the DSA, proposed by Scott Vanstone in 1992. To encrypt a message m for B, A performs : Select a random integer r from [1,n-1]. Compute R = rG. Compute K = hrQ B = (K X , K Y ). Check that K O: Compute k 1 || k 2 = KDF(K X ). Compute c = (k 1 , m). Compute t = MAC(k 2 , c). Send (R; c; t) to B. ENC a symmetric encryption scheme such as Triple-DES MAC denotes a message authentication code (MAC) algorithm “ RFC 2104 ” ; KDF a key derivation function Elliptic Curve Authenticated Encryption Scheme (ECAES)](https://image.slidesharecdn.com/ecc-mysoreuniv-sept2011-111001114525-phpapp02/85/Mathematics-Towards-Elliptic-Curve-Cryptography-by-Dr-R-Srinivasan-55-320.jpg)