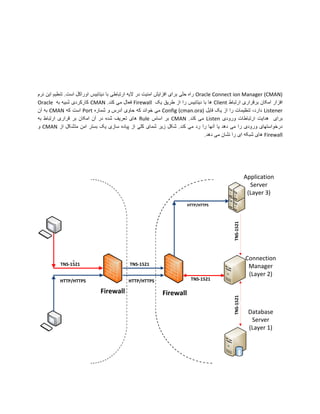
Oracle Connection Manager (CMAN) is used to proxy connections between clients and databases. It listens for connections from clients and application servers, and establishes connections to databases. CMAN uses rules defined in its configuration file to determine whether to accept or drop incoming connection requests based on source/destination IP addresses and ports. It also supports encryption and checksumming of connections using settings in the sqlnet.ora file.