More Related Content
Similar to CompleteID Validation
Similar to CompleteID Validation (20)
CompleteID Validation
- 1. CompleteID™ Validation
DataProc’s CompleteID™ system combines the best available data partners into one coherent and
standardized platform for all your Lifeline processing needs. Through our integrated network of
data sources and Fraud Prevention Partners, DataProc uses the combined knowledge of over 300
years to make accurate, audit-able, real-time decisions through a collective consciousness.
Let DataProc provide worry-free, front-end compliance that screens out fraud before it even gets
into your system. Through our unique series of integrated database checks - applicants are
screened, identified and assessed with a real-time approval decision that’s backed by transparent
log files for USAC and FCC reporting.
Real-Time Compliance and Validation from nearly any computer device.
DataProc’s real-time compliance lets you to take phone distribution back to the streets!
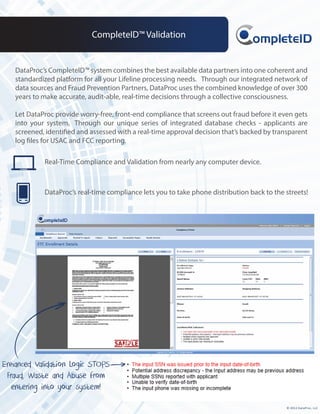
Enhanced Validation Logic STOPS
Fraud, Waste and Abuse from
entering into your system!
© 2012 DataProc, LLC
- 2. Service Availability and Tribal Availability Validation utilizing NPA/NXX, Zip Code and DataProc’s
own CompleteID™ Tribal Locater service to maintain your service areas.
Subsidy Validation utilizing State and Federal program databases as they become available to ETCs
participating in Lifeline.
Subscriber Address Validation utilizing Melissa Data to ensure that all applicants meet FCC
mandated residence requirements.
Duplicate Address Validation to ensure that all Multi-Household Subscribers properly complete
FCC mandated worksheet requirements.
Duplicate Subscriber Validation utilizing B/OSS and DataProc’s own CompleteID™ Duplicate
Identification service based on advanced algorithm logic and unique person identifiers.
Identity Fraud Validation utilizing LexisNexis to prevent unauthorized individuals from scamming
their way into your system.
13140 Coit Road, Suite 475
Dallas, TX 75240
855-DAT-PROC
Info@Data-Proc.com © 2012 DataProc, LLC