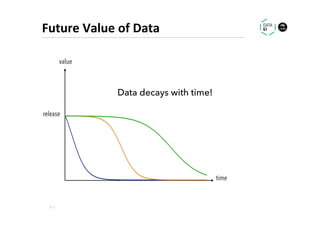
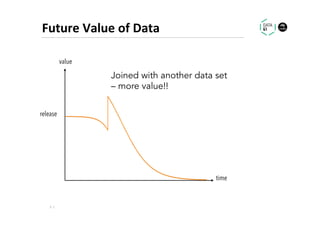
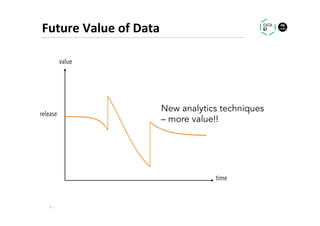
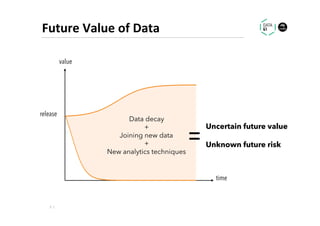
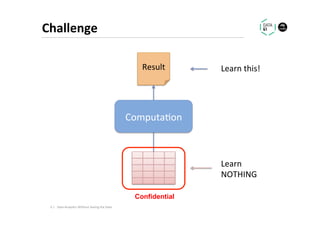
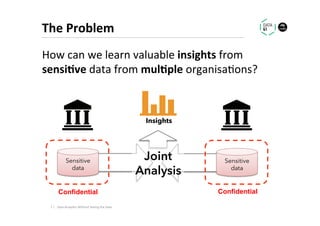
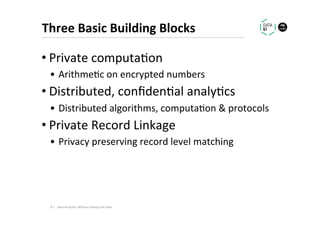
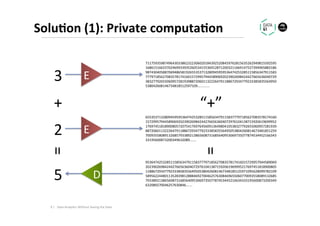
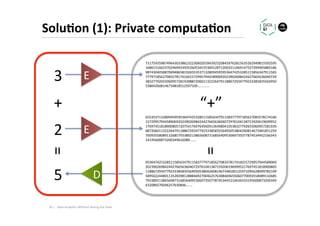
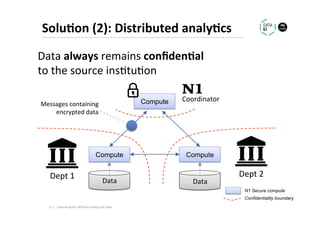
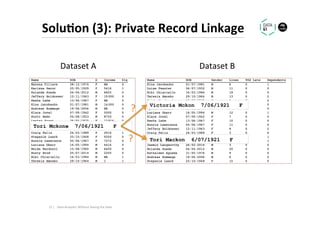
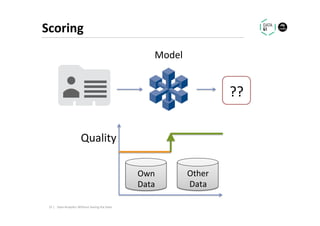
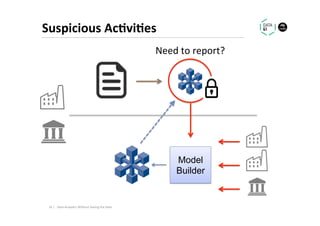
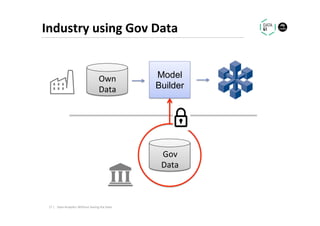
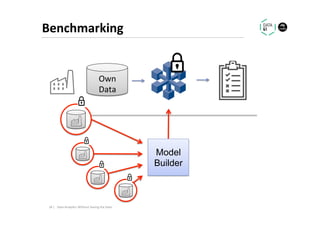
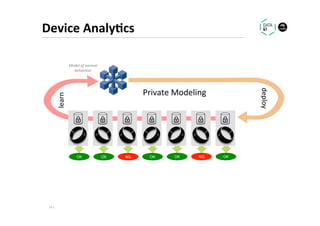
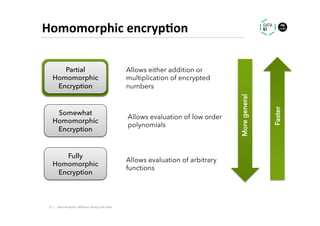
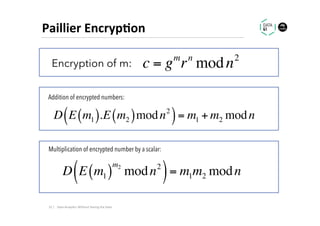
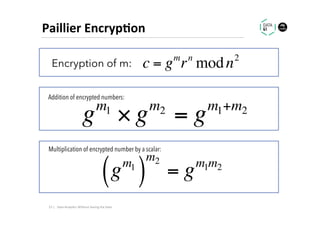
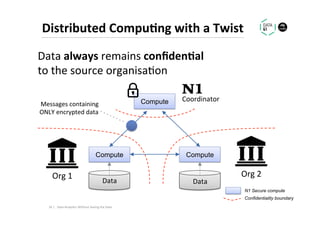
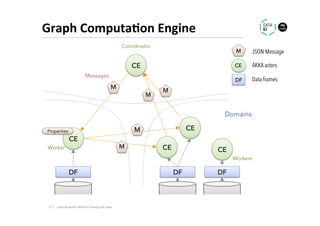
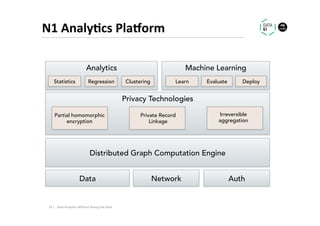
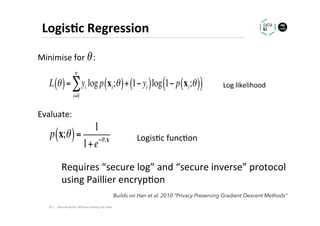
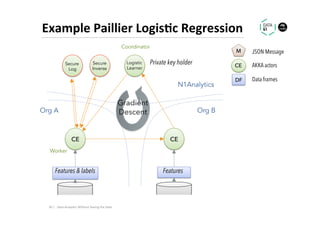
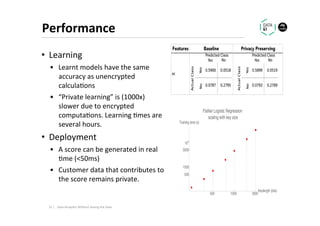
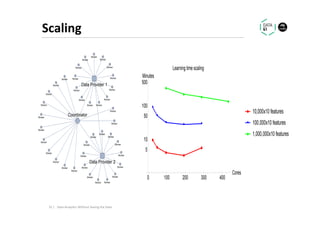
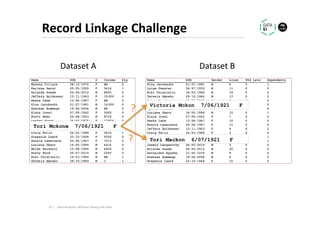
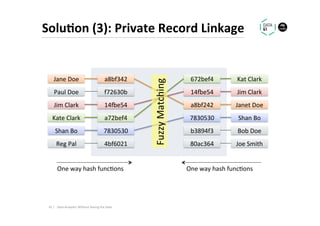
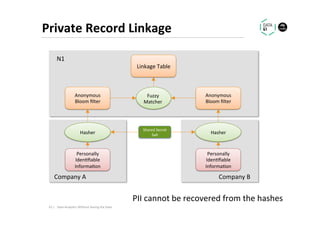
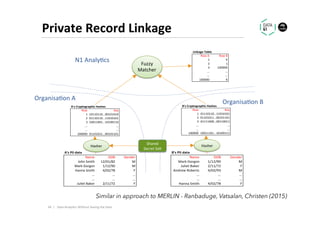
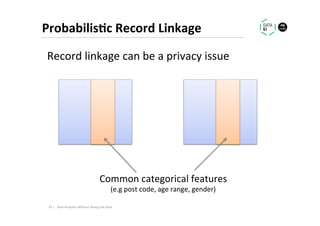
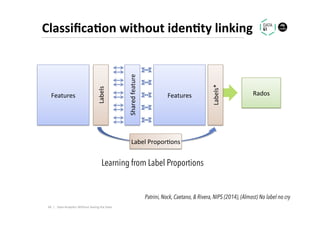
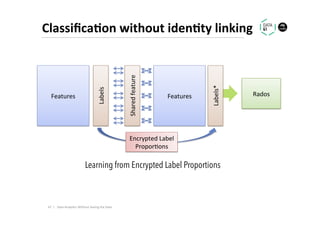
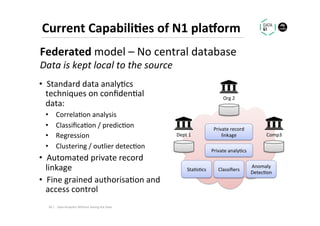
The document discusses methods for data analytics using sensitive data without compromising privacy, emphasizing techniques like private computation, distributed analytics, and secure record linkage. It outlines challenges associated with data decay and the increasing importance of merging datasets for enhanced insights, while proposing solutions to retain confidentiality during analysis. Additionally, it highlights various encryption methods, along with applications and performance metrics, particularly in learning and scoring models.