BIG - base partagée
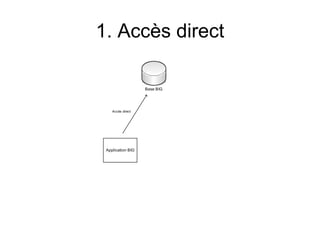
- 1. 1. Accès direct Base BIG Accès direct Application BIG
- 2. 1. Accès direct Base BIG Accès direct Accès direct Application BIG Application BIG • Volume des échanges de données • Conflit des accès concurrentiels => Montée en charge limitée
- 3. 1. Accès H2 direct (H2_FS) Base H2 BIG big.lock.db #FileLock #Fri Jun 15 17:21:34 CEST 2012 id=137f0bc272786623f7a5d61ae5bac67bbaac5eca314 logPos=713184 method=serialized big.h2.db Interrogation big .lock.db Interrogation big .lock.db & & Accès direct Accès direct Application BIG Application BIG • Volume des échanges de données • Conflit des accès concurrentiels => Montée en charge limitée
- 4. 2. Accès H2 par défaut Base H2 BIG big.h2.db Interrogation big .lock.db Application BIG 172.18.12.102 Principes : b) Le premier client H2…
- 5. 2. Accès H2 par défaut Base H2 BIG big.lock.db #FileLock #Wed Jun 13 14:48:04 CEST 2012 id=137e5e2f2ab803cf71b6b520b7b008b17e3e75e3a9e method=file server=172.18.12.102:53053 big.h2.db Accès direct Application BIG Serveur H2 (port 53053) 172.18.12.102 Principes : b) Le premier client H2 utilise un accès direct et expose automatiquement un serveur H2
- 6. 2. Accès H2 par défaut Base H2 BIG big.lock.db #FileLock #Wed Jun 13 14:48:04 CEST 2012 id=137e5e2f2ab803cf71b6b520b7b008b17e3e75e3a9e method=file server=172.18.12.102:53053 big.h2.db Accès direct Interrogation big .lock.db Application BIG Application BIG Serveur H2 (port 53053) 172.18.12.102 Principes : b) Le premier client H2 utilise un accès direct et expose automatiquement un serveur H2 c) Les clients H2 suivants…
- 7. 2. Accès H2 par défaut Base H2 BIG big.lock.db #FileLock #Wed Jun 13 14:48:04 CEST 2012 id=137e5e2f2ab803cf71b6b520b7b008b17e3e75e3a9e method=file server=172.18.12.102:53053 big.h2.db Accès direct Application BIG Application BIG Accès TCP Serveur H2 (port 53053) 172.18.12.102 Principes : b) Le premier client H2 utilise un accès direct et expose automatiquement un serveur H2 c) Les clients H2 suivants se connectent au serveur H2 créé
- 8. 2. Accès H2 par défaut Base H2 BIG big.lock.db #FileLock #Wed Jun 13 14:48:04 CEST 2012 id=137e5e2f2ab803cf71b6b520b7b008b17e3e75e3a9e method=file server=172.18.12.102:53053 big.h2.db Accès direct Application BIG Application BIG Accès TCP Serveur H2 (port 53053) 172.18.12.102 • Performances optimales pour poste autonome • Meilleure gestion de la bande passante et des accès concurrents • Premier client BIG doit disposer d’un bon accès à la base et aux autres clients (qui doivent aussi accéder à la base pour lire big.lock.db)
- 9. 3. Accès H2 serveur (H2_TCP) Base H2 BIG big.lock.db #FileLock #Wed Jun 13 14:48:04 CEST 2012 id=137e5e2f2ab803cf71b6b520b7b008b17e3e75e3a9e method=file big.h2.db Accès direct Serveur H2 (port 53053) 172.18.12.102 Accès TCP Application BIG Application BIG • Accès optimal • Contrôle centralisé des accès ; base pouvant être inaccessible en direct par les clients • Administration minimale (automatisable)