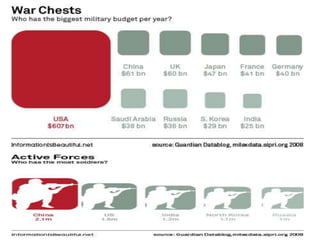
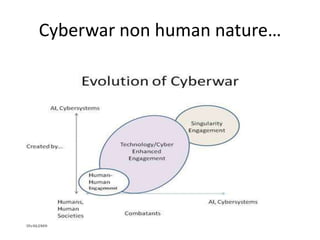
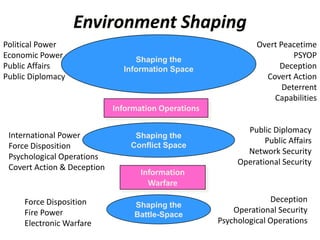
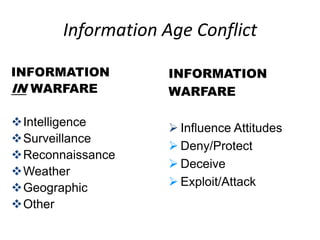
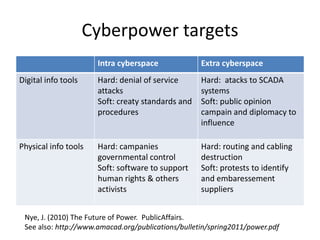
The document discusses the significance of information warfare in the 21st century, focusing on its impact on military strategies and operations driven by advancements in technology and network-centric warfare. It highlights various forms of information operations, such as psychological operations and electronic warfare, while also addressing the vulnerabilities of democracies and organizations to misinformation and cyber threats. Ultimately, it emphasizes that defensive measures against information warfare should involve not just government but also the participation of all organizations at risk.