Transactions and Concurrency control
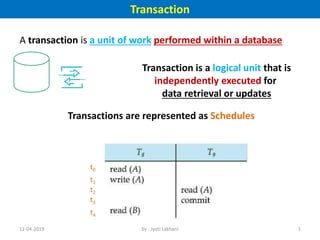
- 1. Transaction A transaction is a unit of work performed within a database Transaction is a logical unit that is independently executed for data retrieval or updates Transactions are represented as Schedules t0 t1 t2 t3 t4 12-04-2019 1by : Jyoti Lakhani
- 2. States of a Transaction 12-04-2019 2by : Jyoti Lakhani
- 3. SQL Transaction is helpful to execute one more statements as a set. SQL Transaction 12-04-2019 3by : Jyoti Lakhani
- 4. States of a Transaction: COMMIT 12-04-2019 4by : Jyoti Lakhani
- 5. States of a Transaction: ROLLBACK 12-04-2019 5by : Jyoti Lakhani
- 6. Complete life cycle of a Transaction 12-04-2019 6by : Jyoti Lakhani
- 7. Properties of a Transaction 12-04-2019 7by : Jyoti Lakhani
- 8. ACID Properties 12-04-2019 8by : Jyoti Lakhani
- 9. ACID Properties: ATOMICITY ATOMICITY A transaction must be fully complete, saved (committed) or completely undone (rolled back). Begin Commit RollBack ALL NONE12-04-2019 9by : Jyoti Lakhani
- 10. ACID Properties: CONSISTANCY CONSISTENCY The transaction must be fully compliant with the state of the database as it was prior to the transaction CONSISTENCY INCONSISTENCY 12-04-2019 10by : Jyoti Lakhani
- 11. ACID Properties: ISOLATION ISOLATION Transaction data must not be available to other transactions until the original transaction is committed or rolled back. 12-04-2019 11by : Jyoti Lakhani
- 12. ACID Properties: DURABILITY DURABILITY Transaction data changes must be available, even in the event of database failure. 12-04-2019 12by : Jyoti Lakhani
- 13. To perform one task at same time by two objects Concurrency 12-04-2019 13by : Jyoti Lakhani
- 14. Concurrent vs Parallel CONCURRENCY Sharing of Resources 12-04-2019 14by : Jyoti Lakhani
- 15. Concurrent vs Parallel 12-04-2019 15by : Jyoti Lakhani
- 16. CONCURRENCY IS A PROBLEM 12-04-2019 16by : Jyoti Lakhani
- 17. Problems of Concurrency 12-04-2019 17by : Jyoti Lakhani
- 18. A=10 A= A+10 =20 A=20 A= A+10 =30 A=30 A=10 Problems of Concurrency: DIRTY READ 12-04-2019 18by : Jyoti Lakhani
- 19. Problems of Concurrency: UNEPEATED READ 12-04-2019 19by : Jyoti Lakhani
- 20. Problems of Concurrency: LOST UPDATE 12-04-2019 20by : Jyoti Lakhani
- 21. Problems of Concurrency: PHANTOM READ 12-04-2019 21by : Jyoti Lakhani
- 22. Problems of Concurrency 12-04-2019 22by : Jyoti Lakhani
- 23. Problems of Concurrency: LOST UPDATE DEAD LOCK 12-04-2019 23by : Jyoti Lakhani
- 24. 12-04-2019 24by : Jyoti Lakhani
- 25. Concurrency control is the procedure in DBMS for managing simultaneous operations without conflicting with each another Concurrency Control: WHAT IS? 12-04-2019 25by : Jyoti Lakhani
- 26. Concurrency Control: PROTOCOLS Concurrency Control Protocols • Locking Protocol •Two Phase Locking Protocol •Time Stamp Protocol 12-04-2019 26by : Jyoti Lakhani
- 27. Concurrency Control: LOCKING PROTOCOL Lock Data Items A lock is a data variable which is associated with a data item Locks helps to – synchronize access to the database items …. by concurrent transactions. Transactions proceed only once the lock request is granted Transactions proceed only once the lock request is granted 12-04-2019 27by : Jyoti Lakhani
- 28. 12-04-2019 by : Jyoti Lakhani 28 Concurrency Control: LOCKING PROTOCOL
- 29. Concurrency Control: LOCKING PROTOCOL • Binary Locks • Shared/ Exclusive Locking 12-04-2019 29by : Jyoti Lakhani
- 30. Concurrency Control: LOCKING PROTOCOL Binary Locking A Binary lock on a data item can either locked or unlocked states 12-04-2019 30by : Jyoti Lakhani
- 31. Concurrency Control: LOCKING PROTOCOL Shared / Exclusive Locks This type of locking mechanism separates the locks based on their uses. Shared Lock (S) Read-only lock data item can be shared between transactions you will never have permission to update data a data item can be read as well as written Exclusive Lock (X) This is exclusive and can't be held concurrently on the same data item Transactions may unlock the data item after finishing the 'write' operation 12-04-2019 31by : Jyoti Lakhani
- 32. Concurrency Control: LOCKING PROTOCOL 12-04-2019 32by : Jyoti Lakhani
- 33. Concurrency Control: Locking Protocol Problem with Locking Protocol Starvation Deadlock Starvation is the situation when a transaction needs to wait for an indefinite period to acquire a lock. Deadlock refers to a specific situation where two or more processes are waiting for each other to release a resource or more than two processes are waiting for the resource in a circular chain. 12-04-2019 33by : Jyoti Lakhani
- 34. Concurrency Control: Two Phase Locking Protocol This locking protocol divides the execution phase of a transaction into three different parts • Growing Phase • Locked Phase • Shrinking Phase Growing Phase: In this phase transaction may obtain locks but may not release any locks. Shrinking Phase: In this phase, a transaction may release locks but not obtain any new lock 12-04-2019 34by : Jyoti Lakhani
- 35. Concurrency Control: Two Phase Locking Protocol 12-04-2019 35by : Jyoti Lakhani
- 36. Strict Two-Phase Locking Method Concurrency Control: Two Phase Locking Protocol Transaction Hold Locks until end of the Transaction 12-04-2019 36by : Jyoti Lakhani
- 37. Concurrency Control: Two Phase Locking Protocol 12-04-2019 37by : Jyoti Lakhani
- 38. Concurrency Control: Time Stamp based Protocol Uses a timestamp to serialize the execution of concurrent transactions This protocol ensures that every conflicting read and write operations are executed in timestamp order. The protocol uses the System Time or Logical Count as a Timestamp. 12-04-2019 38by : Jyoti Lakhani
- 39. Concurrency Control: Time Stamp based Protocol 12-04-2019 39by : Jyoti Lakhani
- 40. In Time Stamp Protocol ensures that any conflicting read and write operations are executed in time stamp order if not such an operation is rejected and transaction will be rolled back. The rolled back transaction will be restarted with a new Time Stamp. Concurrency Control: Time Stamp based Protocol 12-04-2019 40by : Jyoti Lakhani
- 41. Concurrency Control: Time Stamp based Protocol 12-04-2019 41by : Jyoti Lakhani
- 42. Advantages 1. Serializability 2. Ensures freedom from dead lock Disadvantage Starvation may occur due to continuously getting aborted and restarting the transaction. Concurrency Control: Time Stamp based Protocol 12-04-2019 42by : Jyoti Lakhani