ERA Poster - Measuring Disruption from Software Evolution Activities Using Graph-Based Metrics
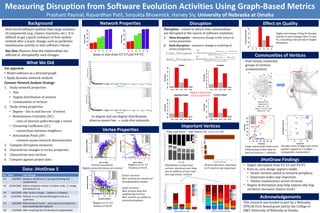
- 1. Measuring Disruption from Software Evolution Activities Using Graph-Based Metrics Prashant Paymal, Rajvardhan Patil, Sanjukta Bhowmick, Harvey Siy, University of Nebraska at Omaha Background Network Properties Disruption Effect on Quality Real-world software systems have large numbers Disruption – extent to which class relationships of components (e.g., classes, functions, etc.) It is are disrupted in the course of software evolution. Higher percentage of bug fix changes difficult to get a quick summary of how system 1. Value disruption – measures change in the values of relative to total changes after V3 and V5, coinciding with periods of higher evolved after a major change, such as perfective vertex properties. disruption. maintenance activity or new software release. 2. Rank disruption – measures change in ordering of vertex properties. Key Idea: Measure how the relationships are affected or disrupted by such changes. Jump in size from V2-V3 and V4-V5. Communities of Vertices Find closely connected What We Did groups of vertices Our approach: (communities). “DrawingView” • Model software as a directed graph • Apply dynamic network analysis. Dynamic Network Analysis Strategy: 1. Study network properties • Size Higher values from V2-V3 and V4-V5 • Degree distribution of vertices “Figure” • Communities of vertices Network of V1 Node size: CC 2. Study vertex properties Blues: BC ≤ 10 Greens: 10 < BC ≤ 100 • Degree – fan-in and fan-out of vertex Yellows: BC > 100 • Betweenness Centrality (BC) In-degree and out-degree distributions – ratio of shortest paths through a vertex observe power law → scale-free networks • Clustering Coefficient (CC) Important Vertices – connections between neighbors Vertex Properties “High importance” – high degrees, BC, or CC, or is AP. • Articulation Point (AP) – removal causes network disconnection 3. Compute disruption measures Large communities have more Average count of edges per vertex 4. Characterize changes in vertex properties relationships within than to appears capped at 3-4 edges → external vertices → modular manageable communities 5. Characterize new vertices 6. Compare against project data JHotDraw Findings Positive correlation Negative in V1, V2 Distribution of important Vertices that were important • Higher disruption from V2-V3 and V4-V5 Highly connected classes are central Positive in V4,V5 vertices decreases over time in V1 tend to stay important. Data: JHotDraw 5 due to addition of new (and • Even so, core design appears stable. less important) vertices. • Newer vertices added to network periphery. Ver Date Last Change Earlier versions: V1 3/9/2001 Merge to JHotDraw 5.2 (using JFC/Swing GUI New vertices are clusters of • Important nodes stay important. components) interdependent classes. • Similar communities across versions. V2 10/24/2001 before merge for version 5.3 (dnd, undo,...), merge • Degree of disruption may help explain why bug Latter versions: dnd (before 5.3) incidence increases (future work) New vertices have few V3 8/4/2002 after various merges... (before 5.4 release) neighboring vertices. V4 11/8/2002 Refactor to use StandardStorageFormat as a superclass. New vertices are added to Acknowledgements network periphery. V5 5/8/2003 Refactoring of Cursor: - java.awt.Cursor (class) has Negative in V1, V2 This research was funded in part by a Nebraska been sistematically replaced Positive in V4,V5 EPSCoR First Award grant and by the College of V6 1/9/2004 After renaming the CH.ifa.draw to org.jhotdraw IS&T, University of Nebraska at Omaha.
