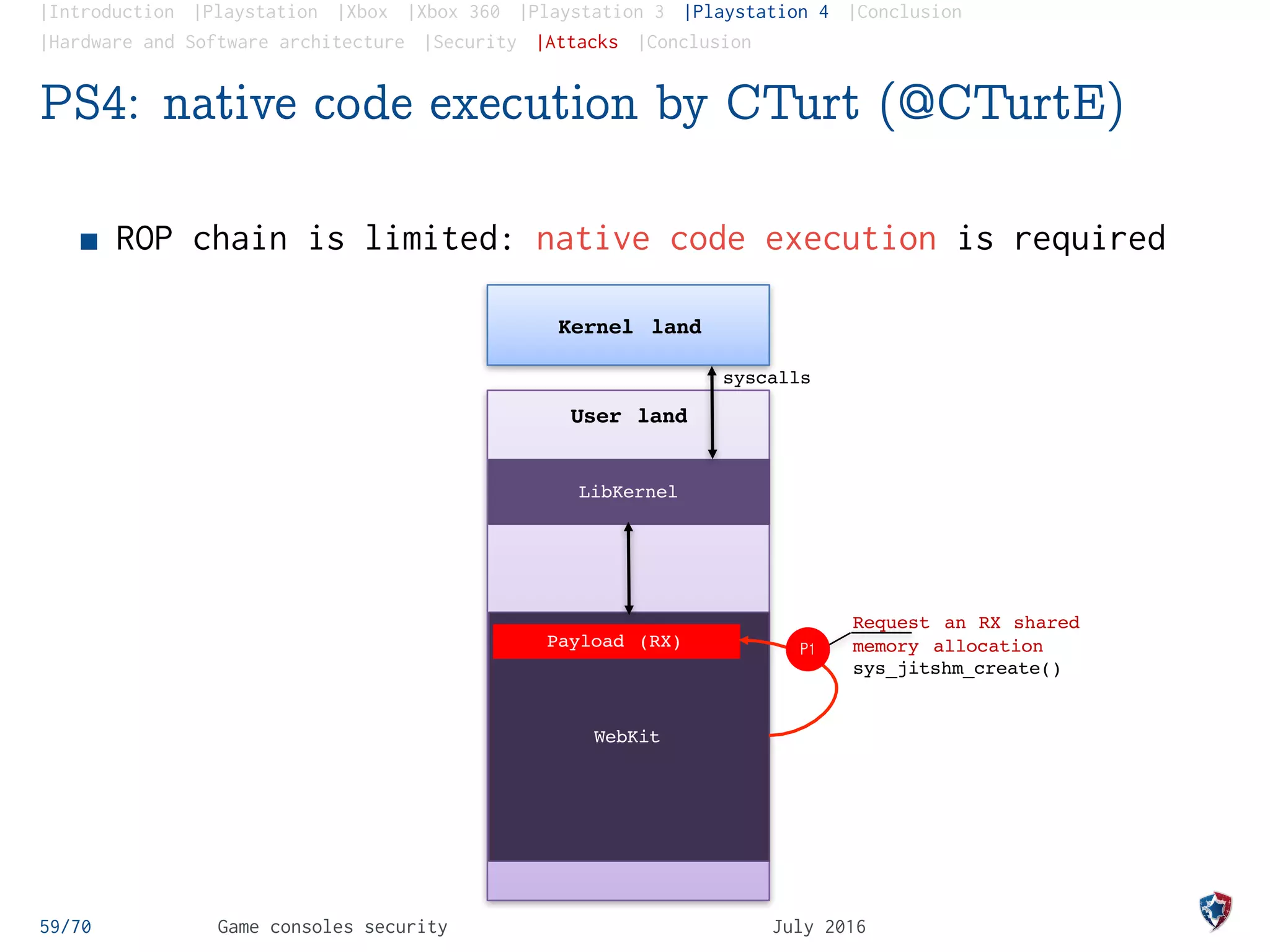
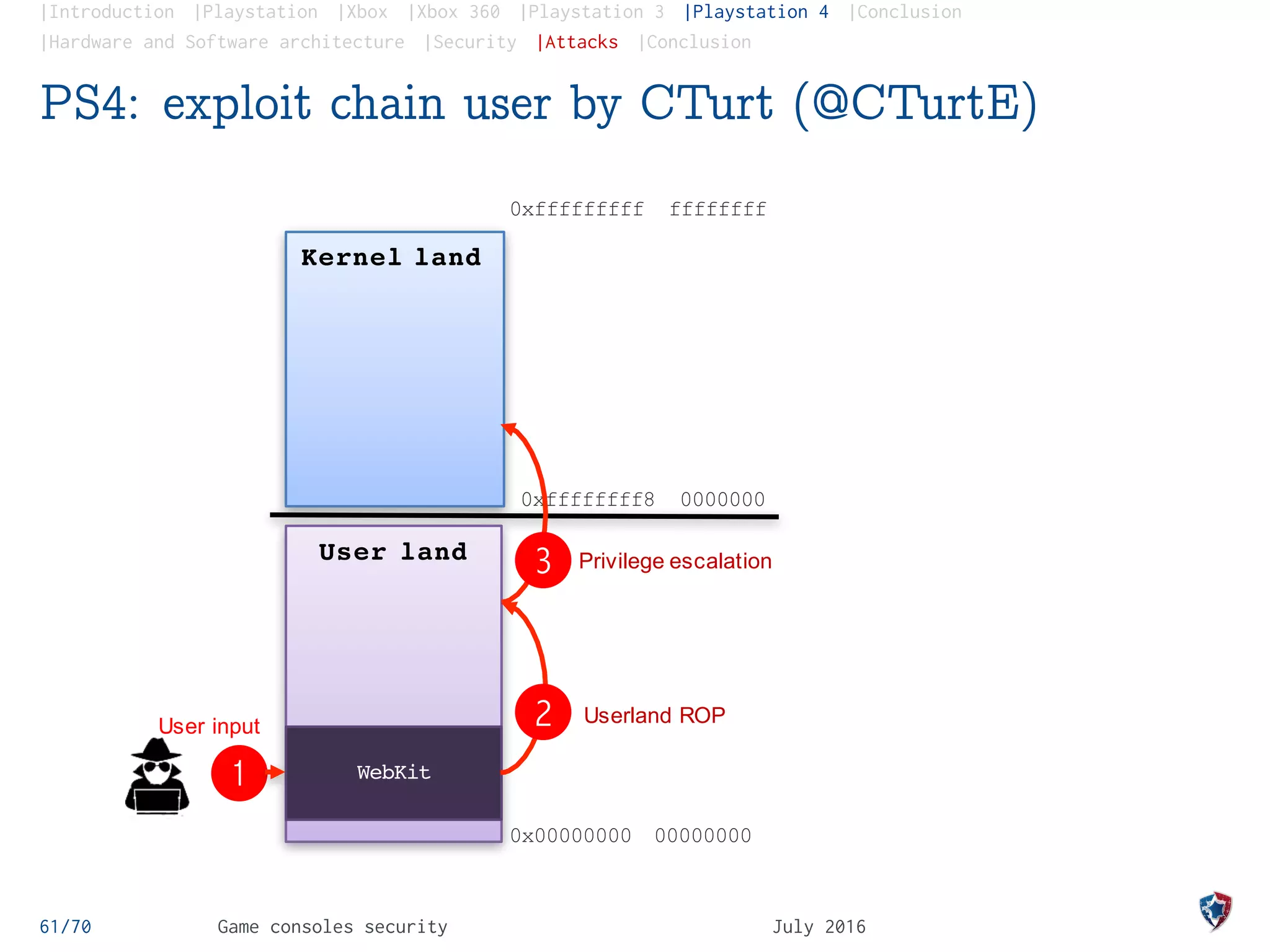
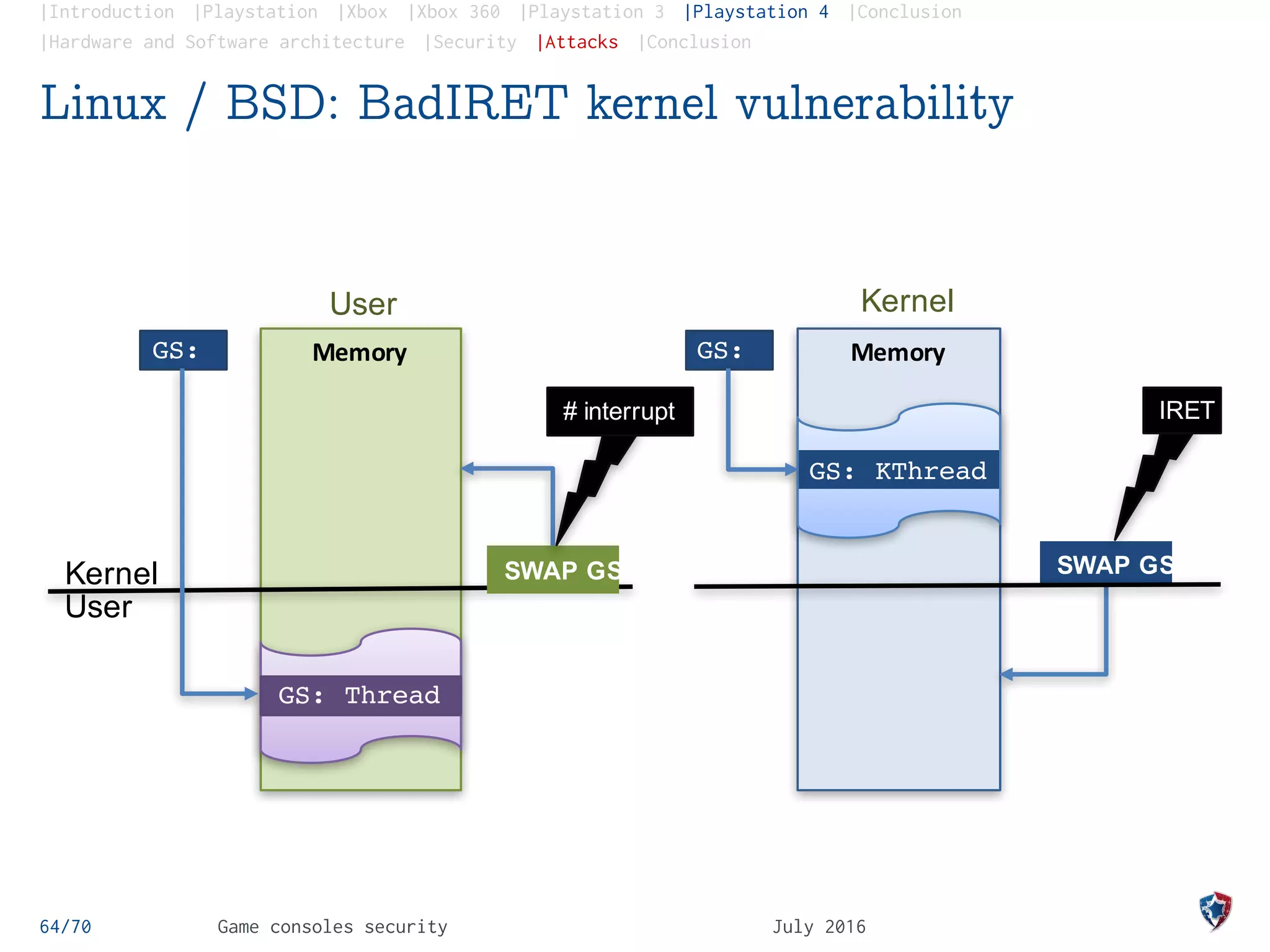
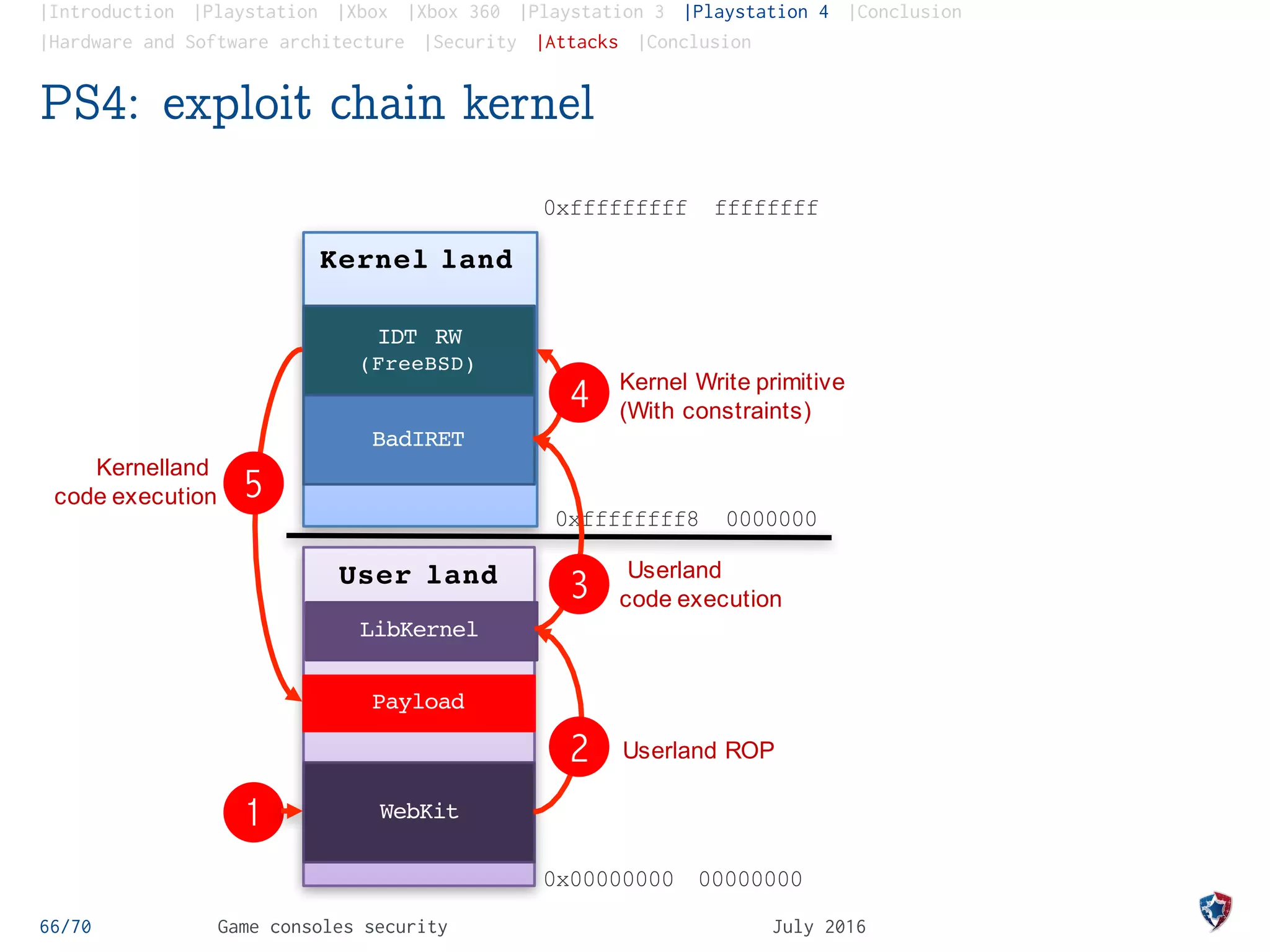
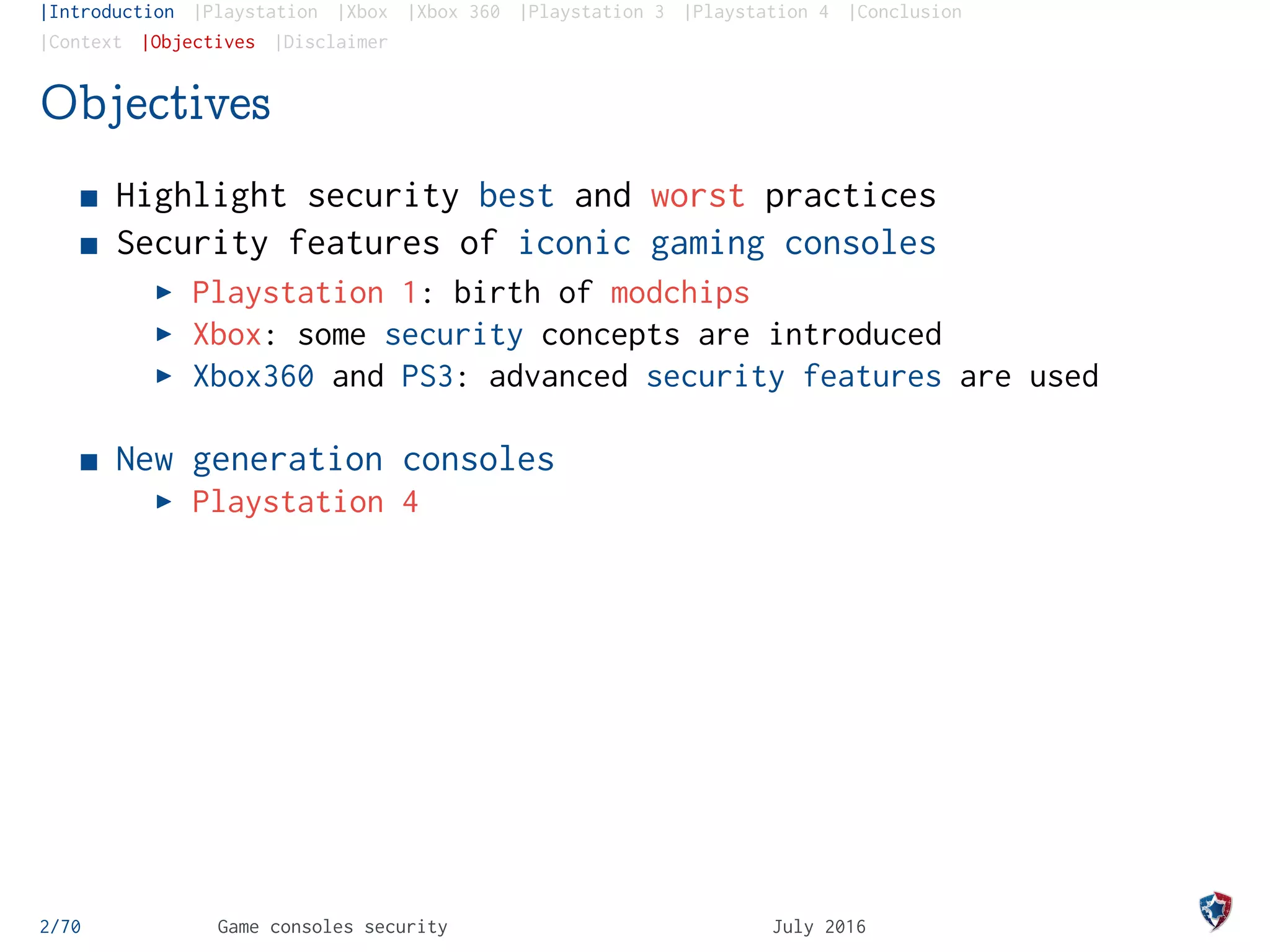
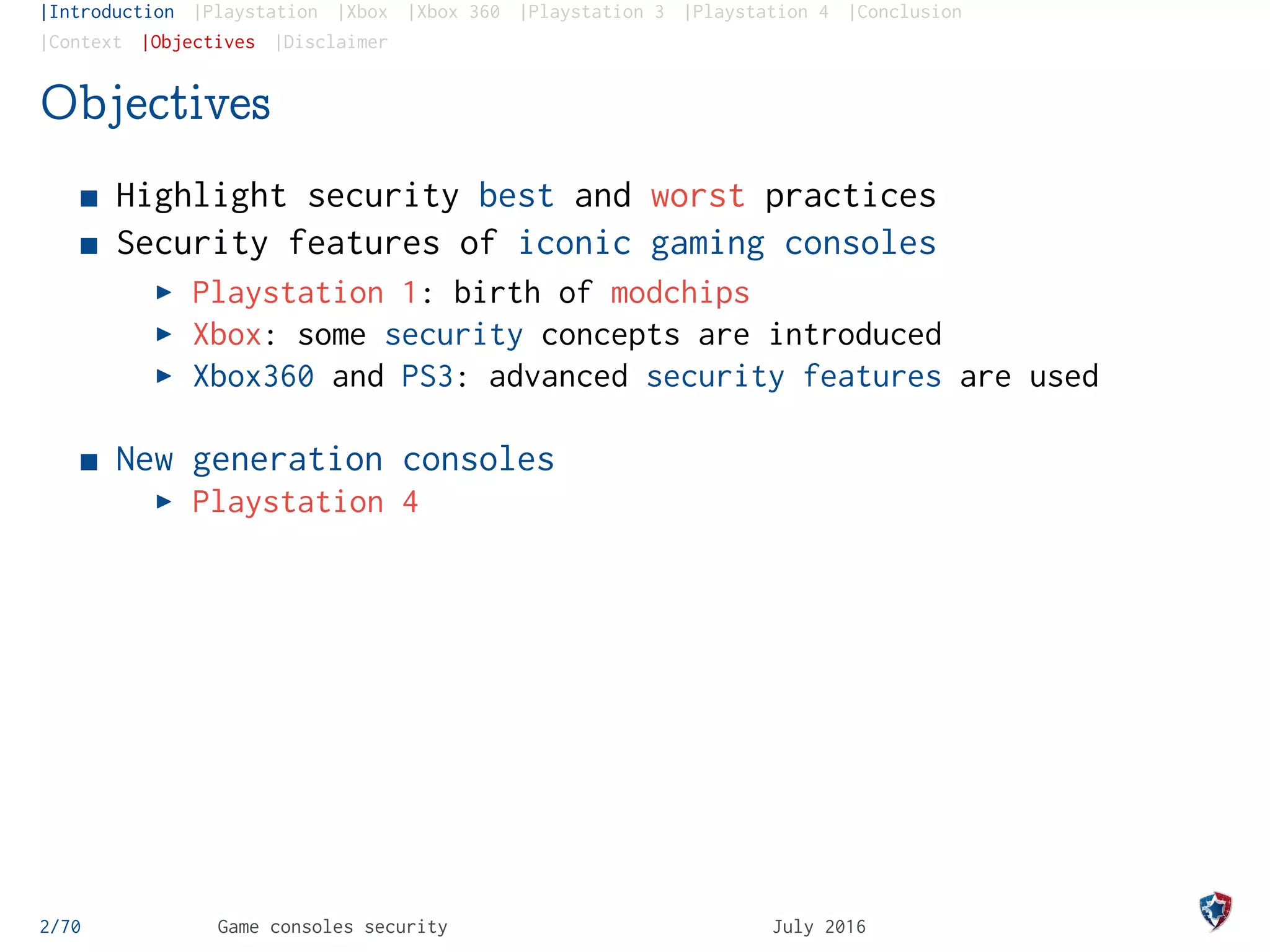
The document provides an analysis of security practices in video game consoles, focusing on architecture and vulnerabilities across different generations, particularly the PlayStation and Xbox. It explores the historical context of hacking, including the emergence of modchips and jailbreak techniques, as well as the evolution of security measures implemented by console manufacturers. The document emphasizes the need for ongoing security updates and the challenge of countering piracy and counterfeiting in the gaming industry.






















![|Introduction |Playstation |Xbox |Xbox 360 |Playstation 3 |Playstation 4 |Conclusion
|Hardware architecture |Software architecture |Security |Attacks |Conclusion
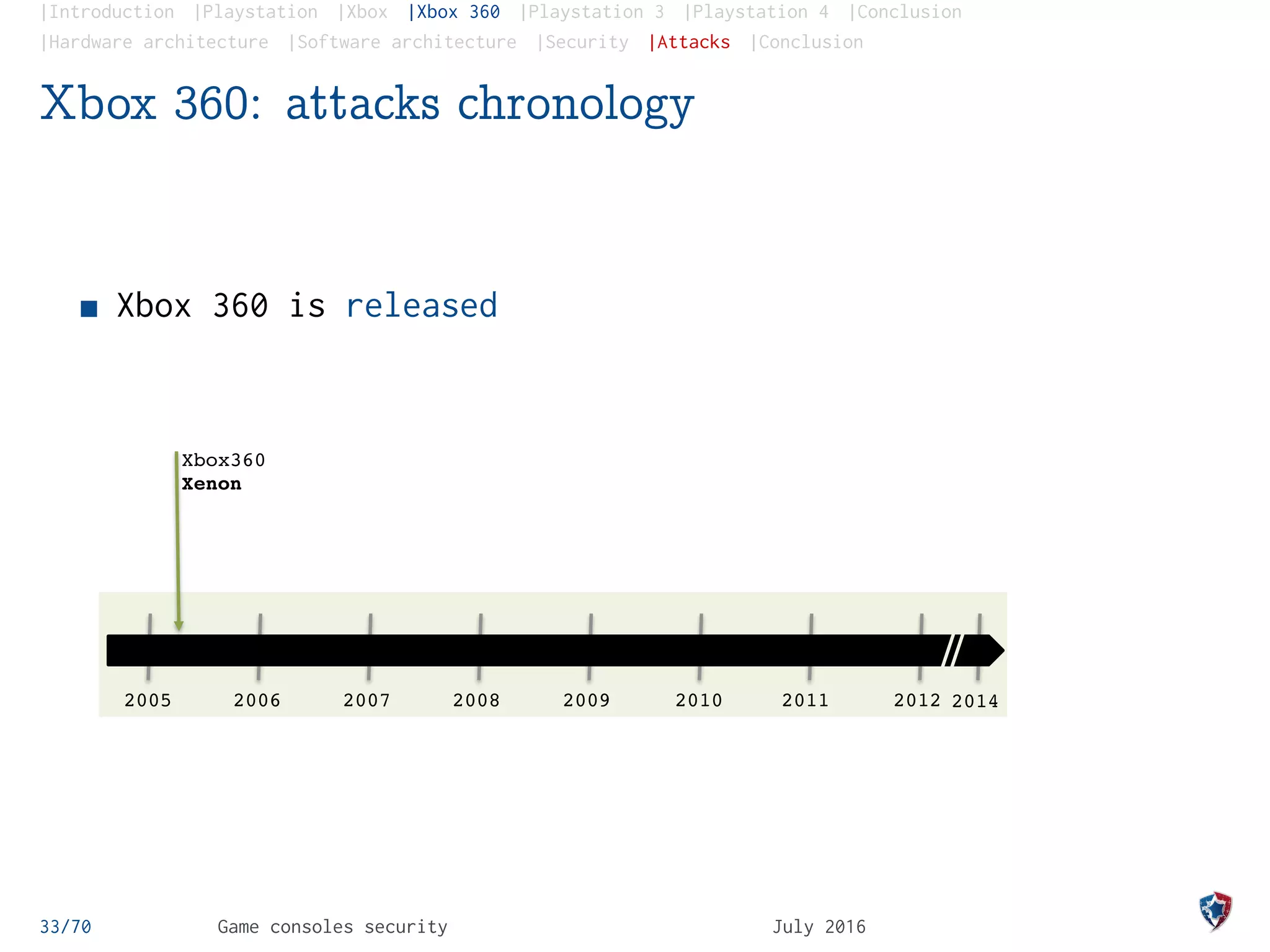
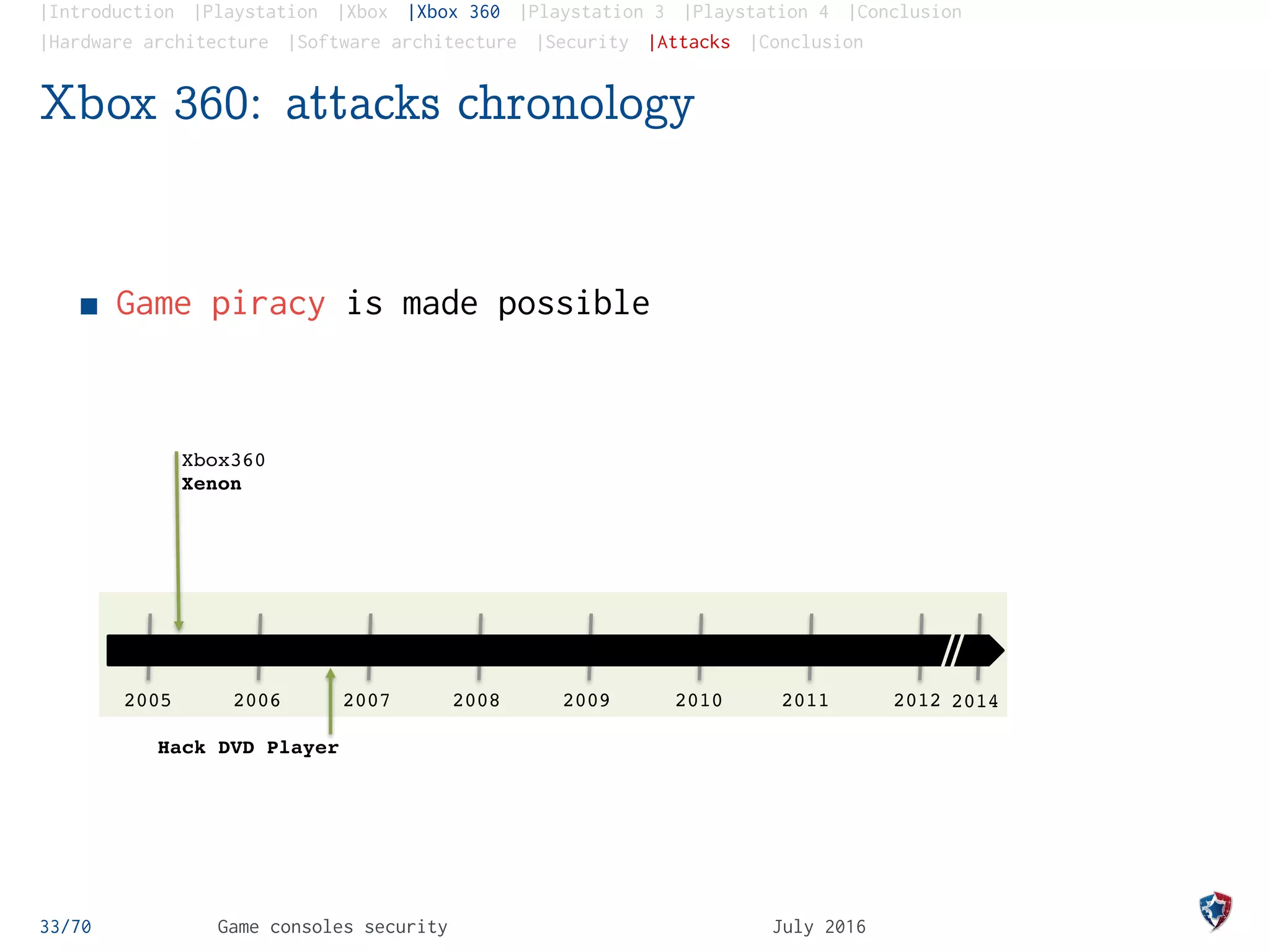
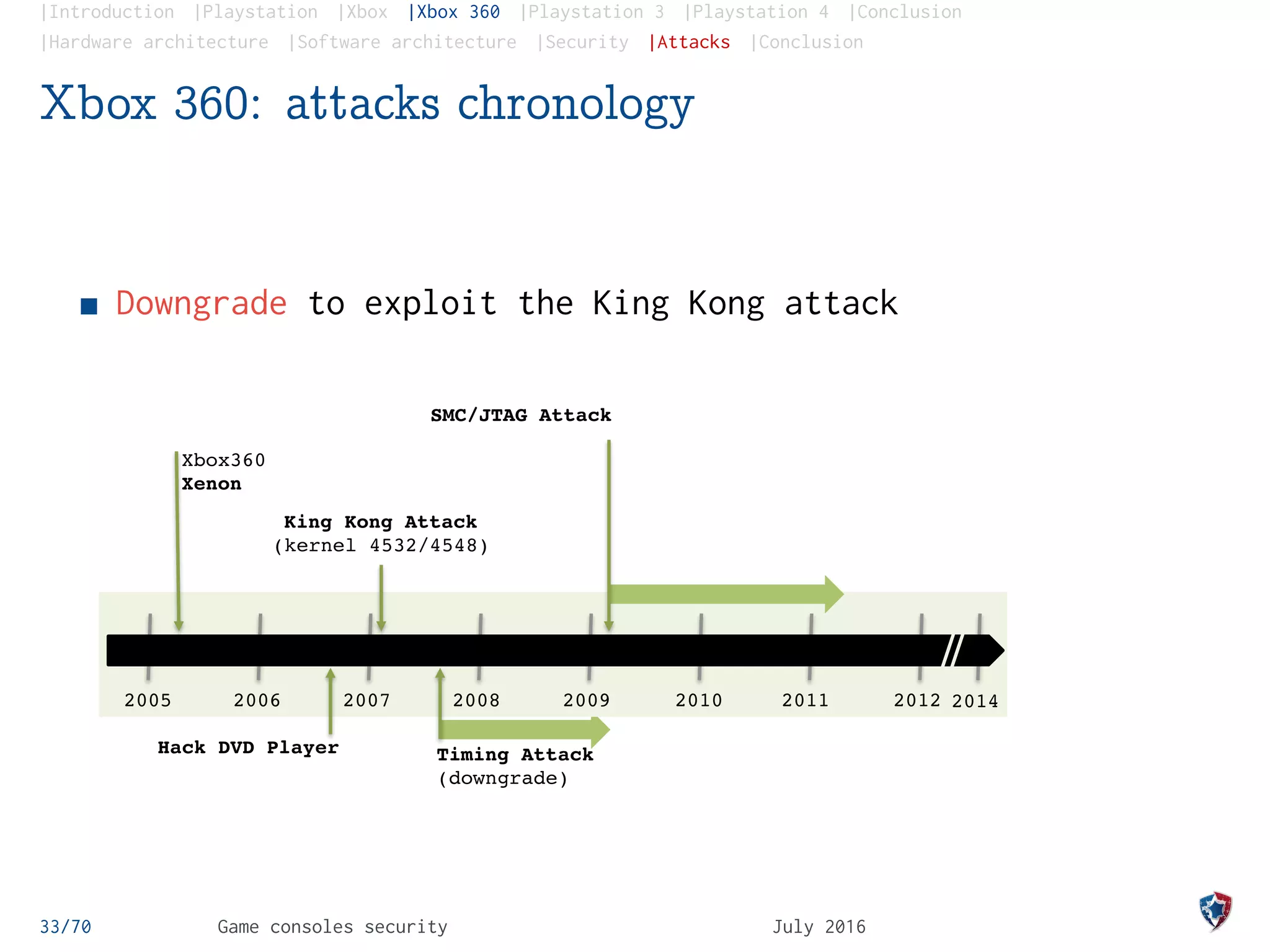
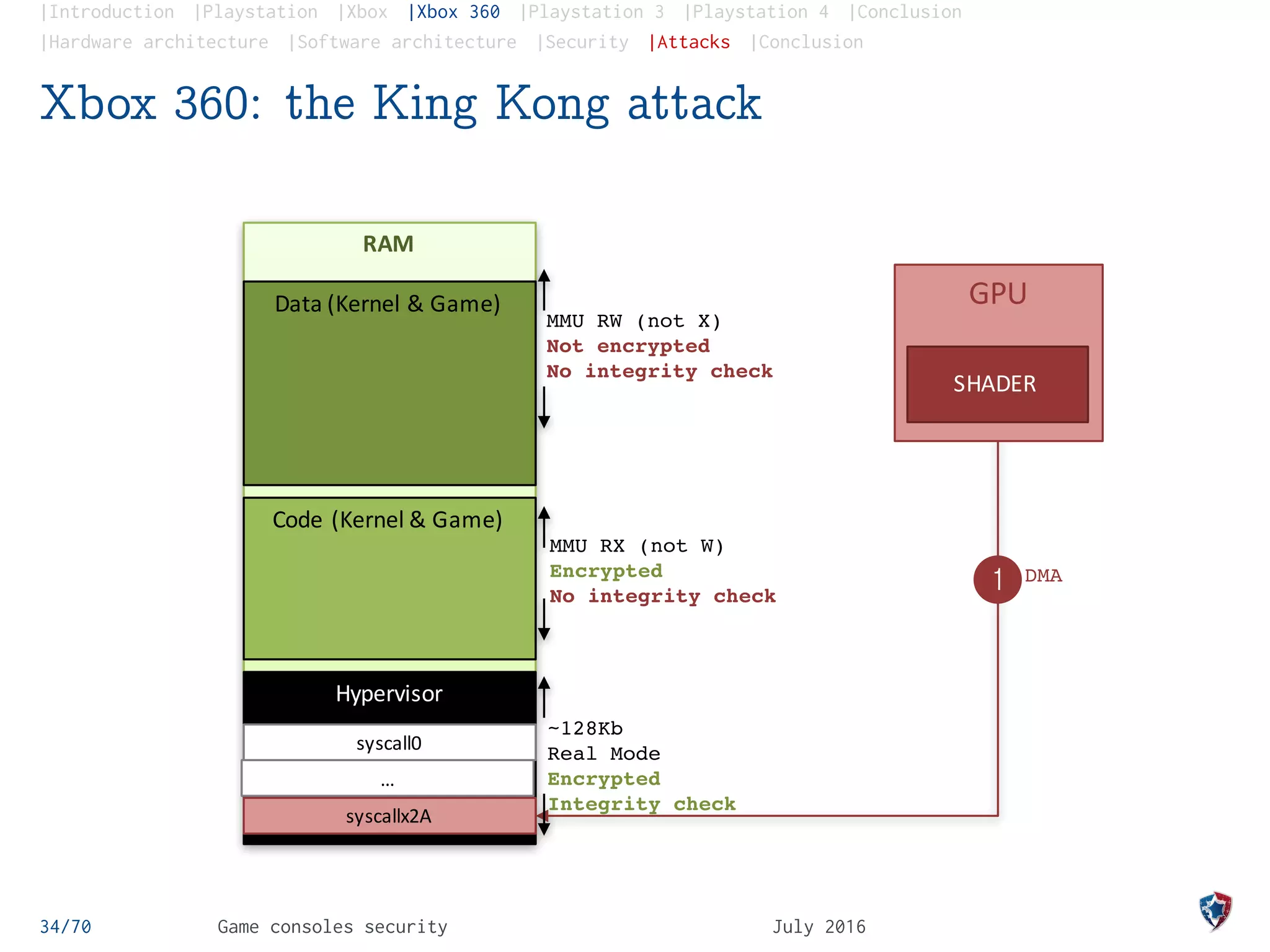
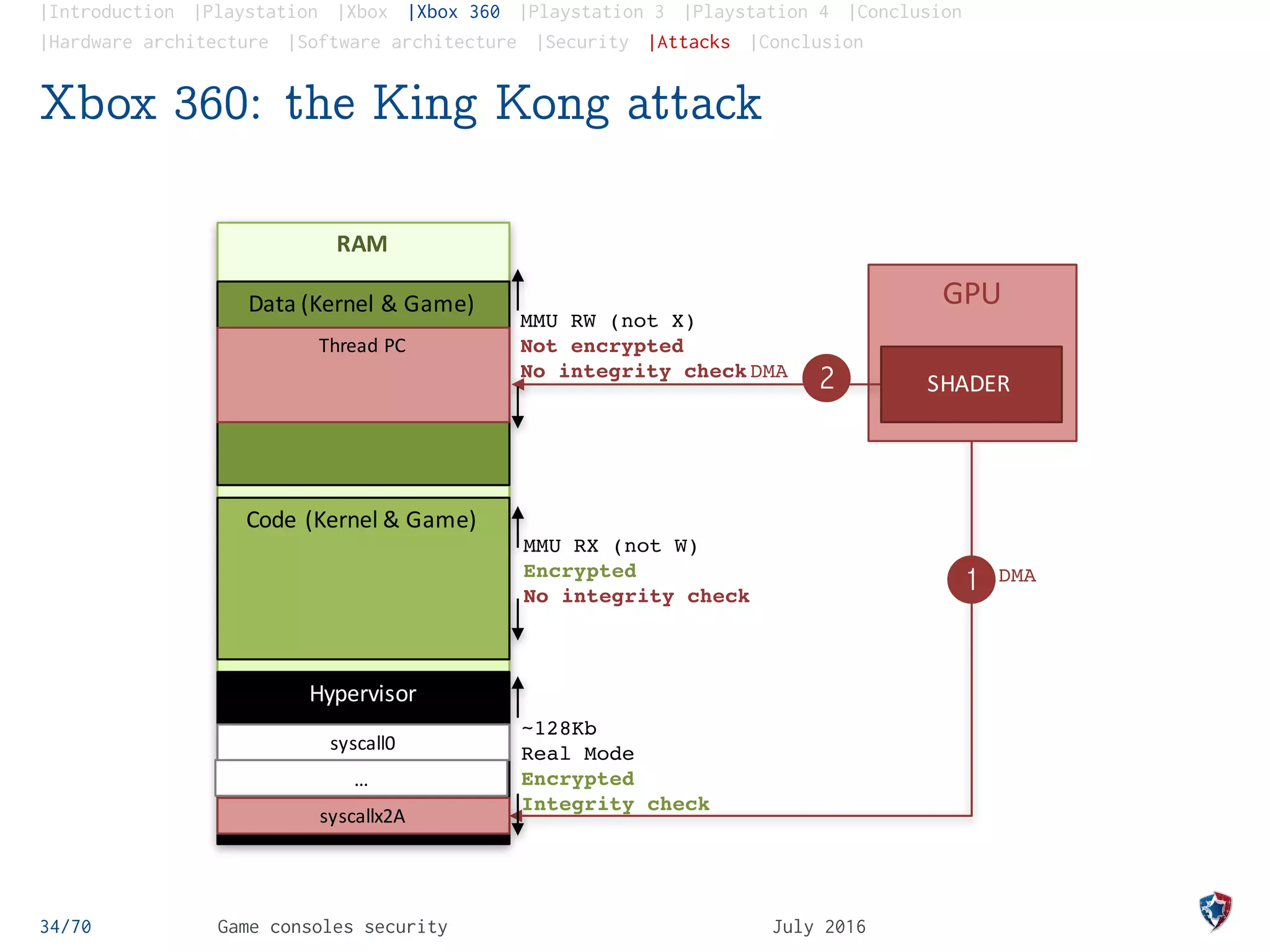
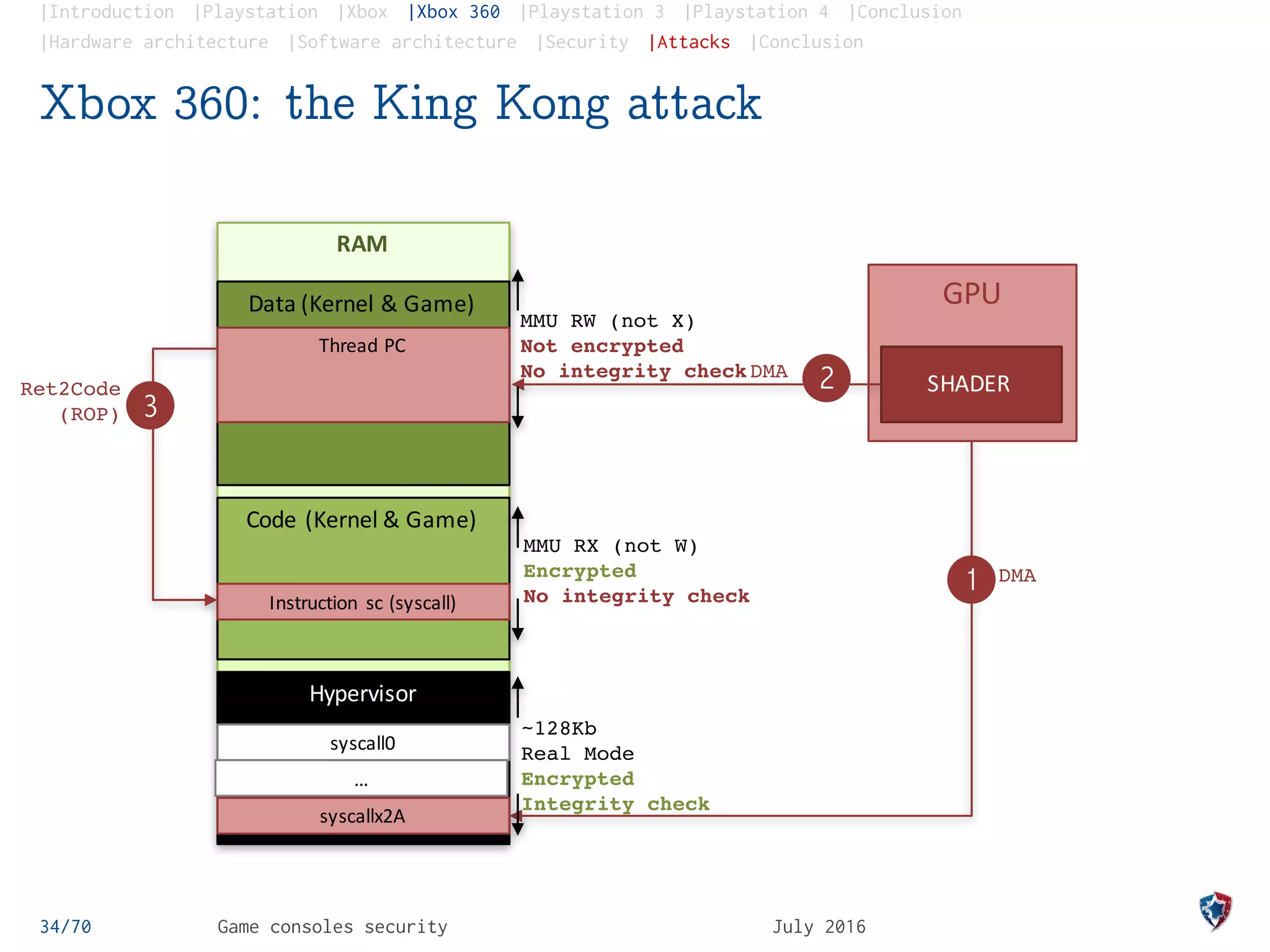
Xbox 360: the King Kong attack
The King Kong Attack, a purely software attack
Improper integer comparison in the hypervisor syscalls
handler
PSEUDO C CODE
extern u32 syscall_table[0x61]
void syscall_handler(r0, r3, r4, …) {
if((u32)r0 >= 0x61) {
goto bad_syscall;
}
r1 = (void*)syscall_table[(u64)r0];
r1();
}
34/70 Game consoles security July 2016](https://image.slidesharecdn.com/mrenard-rbenadjila-gamingconsolesecurityhip2016-160711132819/75/SECURITY-OFFENSE-AND-DEFENSE-STRATEGIES-VIDEO-GAME-CONSOLES-ARCHITECTURE-UNDER-MICROSCOPE-62-2048.jpg)
![|Introduction |Playstation |Xbox |Xbox 360 |Playstation 3 |Playstation 4 |Conclusion
|Hardware architecture |Software architecture |Security |Attacks |Conclusion
Xbox 360: the King Kong attack
The King Kong Attack, a purely software attack
Improper integer comparison in the hypervisor syscalls
handler
PSEUDO C CODE
extern u32 syscall_table[0x61]
void syscall_handler(r0, r3, r4, …) {
if((u32)r0 >= 0x61) {
goto bad_syscall;
}
r1 = (void*)syscall_table[(u64)r0];
r1();
}
34/70 Game consoles security July 2016](https://image.slidesharecdn.com/mrenard-rbenadjila-gamingconsolesecurityhip2016-160711132819/75/SECURITY-OFFENSE-AND-DEFENSE-STRATEGIES-VIDEO-GAME-CONSOLES-ARCHITECTURE-UNDER-MICROSCOPE-63-2048.jpg)




![|Introduction |Playstation |Xbox |Xbox 360 |Playstation 3 |Playstation 4 |Conclusion
|Hardware architecture |Software architecture |Security |Attacks |Conclusion
Xbox 360: the timing attack
36/70 Game consoles security July 2016
New Try
FALSE
0.22ms0.21ms
CheckHMAC(char
*
RealHMAC,
char
*
TestHMAC,
int
len){
[..]
for(
i=0
;
i
<
len
;
i++)
if
(
RealHMAC[i]
!=
TestHMAC[i]
)
break;
[..]
}
TestHMAC = 0000000000000000000000000000000
GuessedHMAC = 0000000000000000000000000000000
I = 0
TRUE](https://image.slidesharecdn.com/mrenard-rbenadjila-gamingconsolesecurityhip2016-160711132819/75/SECURITY-OFFENSE-AND-DEFENSE-STRATEGIES-VIDEO-GAME-CONSOLES-ARCHITECTURE-UNDER-MICROSCOPE-72-2048.jpg)
![|Introduction |Playstation |Xbox |Xbox 360 |Playstation 3 |Playstation 4 |Conclusion
|Hardware architecture |Software architecture |Security |Attacks |Conclusion
Xbox 360: the timing attack
36/70 Game consoles security July 2016
0.21ms
CheckHMAC(char
*
RealHMAC,
char
*
TestHMAC,
int
len){
[..]
for(
i=0
;
i
<
len
;
i++)
if
(
RealHMAC[i]
!=
TestHMAC[i]
)
break;
[..]
}
0.22ms
TestHMAC = 0100000000000000000000000000000
GuessedHMAC = 0000000000000000000000000000000
I = 1
FALSE TRUE
New Try](https://image.slidesharecdn.com/mrenard-rbenadjila-gamingconsolesecurityhip2016-160711132819/75/SECURITY-OFFENSE-AND-DEFENSE-STRATEGIES-VIDEO-GAME-CONSOLES-ARCHITECTURE-UNDER-MICROSCOPE-73-2048.jpg)
![|Introduction |Playstation |Xbox |Xbox 360 |Playstation 3 |Playstation 4 |Conclusion
|Hardware architecture |Software architecture |Security |Attacks |Conclusion
Xbox 360: the timing attack
36/70 Game consoles security July 2016
0.21ms
CheckHMAC(char
*
RealHMAC,
char
*
TestHMAC,
int
len){
[..]
for(
i=0
;
i
<
len
;
i++)
if
(
RealHMAC[i]
!=
TestHMAC[i]
)
break;
[..]
}
0.22ms
TestHMAC = 0200000000000000000000000000000
GuessedHMAC = 0000000000000000000000000000000
I = 2
FALSE TRUE
New Try](https://image.slidesharecdn.com/mrenard-rbenadjila-gamingconsolesecurityhip2016-160711132819/75/SECURITY-OFFENSE-AND-DEFENSE-STRATEGIES-VIDEO-GAME-CONSOLES-ARCHITECTURE-UNDER-MICROSCOPE-74-2048.jpg)
![|Introduction |Playstation |Xbox |Xbox 360 |Playstation 3 |Playstation 4 |Conclusion
|Hardware architecture |Software architecture |Security |Attacks |Conclusion
Xbox 360: the timing attack
36/70 Game consoles security July 2016
0.22ms0.21ms
CheckHMAC(char
*
RealHMAC,
char
*
TestHMAC,
int
len){
[..]
for(
i=0
;
i
<
len
;
i++)
if
(
RealHMAC[i]
!=
TestHMAC[i]
)
break;
[..]
}
TestHMAC = 0300000000000000000000000000000
GuessedHMAC = 0300000000000000000000000000000
I = 3
FALSE TRUE
New Try](https://image.slidesharecdn.com/mrenard-rbenadjila-gamingconsolesecurityhip2016-160711132819/75/SECURITY-OFFENSE-AND-DEFENSE-STRATEGIES-VIDEO-GAME-CONSOLES-ARCHITECTURE-UNDER-MICROSCOPE-75-2048.jpg)
![|Introduction |Playstation |Xbox |Xbox 360 |Playstation 3 |Playstation 4 |Conclusion
|Hardware architecture |Software architecture |Security |Attacks |Conclusion
Xbox 360: the timing attack
36/70 Game consoles security July 2016
0.21ms
CheckHMAC(char
*
RealHMAC,
char
*
TestHMAC,
int
len){
[..]
for(
i=0
;
i
<
len
;
i++)
if
(
RealHMAC[i]
!=
TestHMAC[i]
)
break;
[..]
}
0.22ms
TestHMAC = 0300000000000000000000000000000
GuessedHMAC = 0300000000000000000000000000000
I = 0
TRUEFALSE
New Try](https://image.slidesharecdn.com/mrenard-rbenadjila-gamingconsolesecurityhip2016-160711132819/75/SECURITY-OFFENSE-AND-DEFENSE-STRATEGIES-VIDEO-GAME-CONSOLES-ARCHITECTURE-UNDER-MICROSCOPE-76-2048.jpg)


![|Introduction |Playstation |Xbox |Xbox 360 |Playstation 3 |Playstation 4 |Conclusion
|Hardware architecture |Software architecture |Security |Attacks |Conclusion
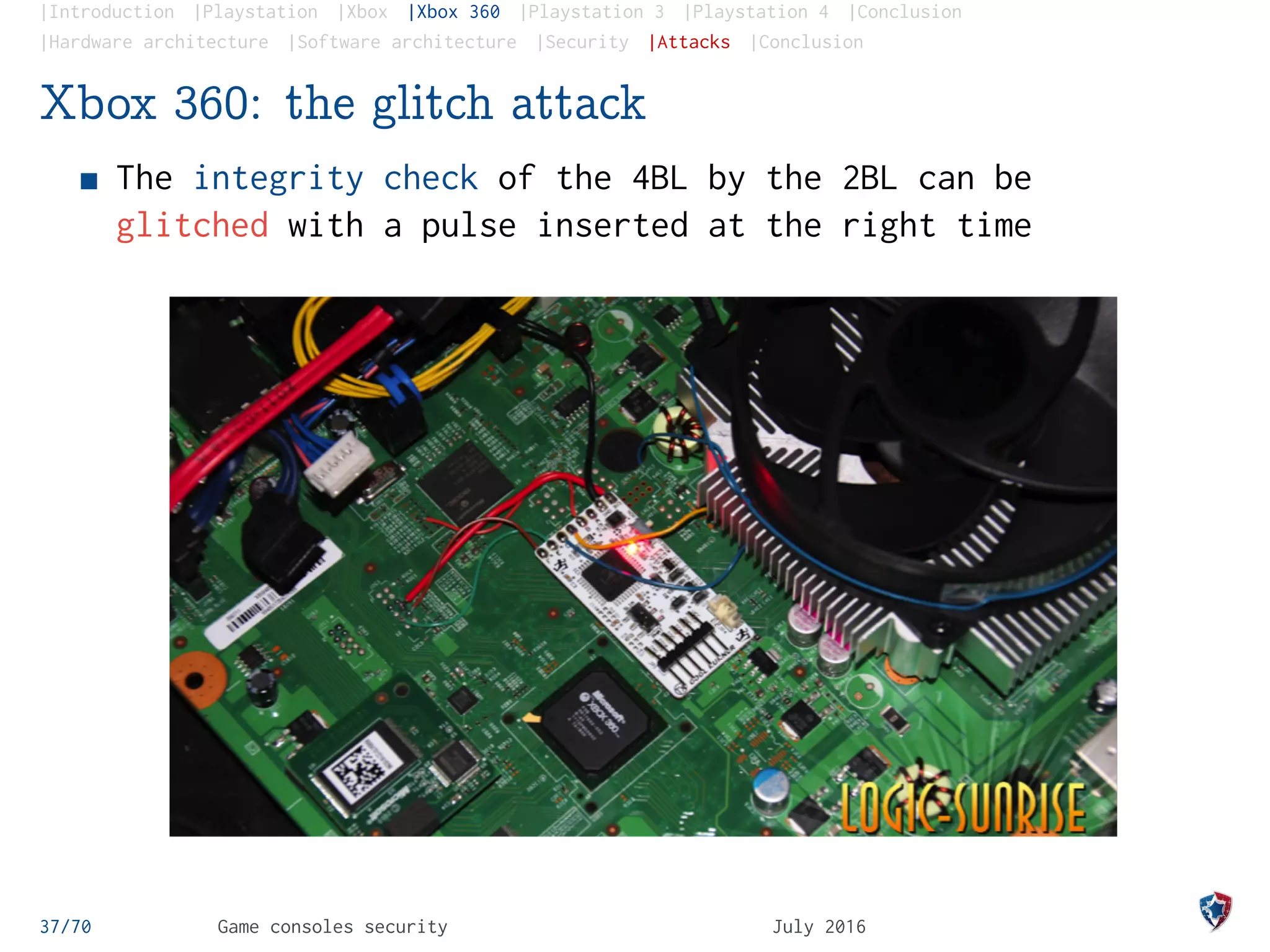
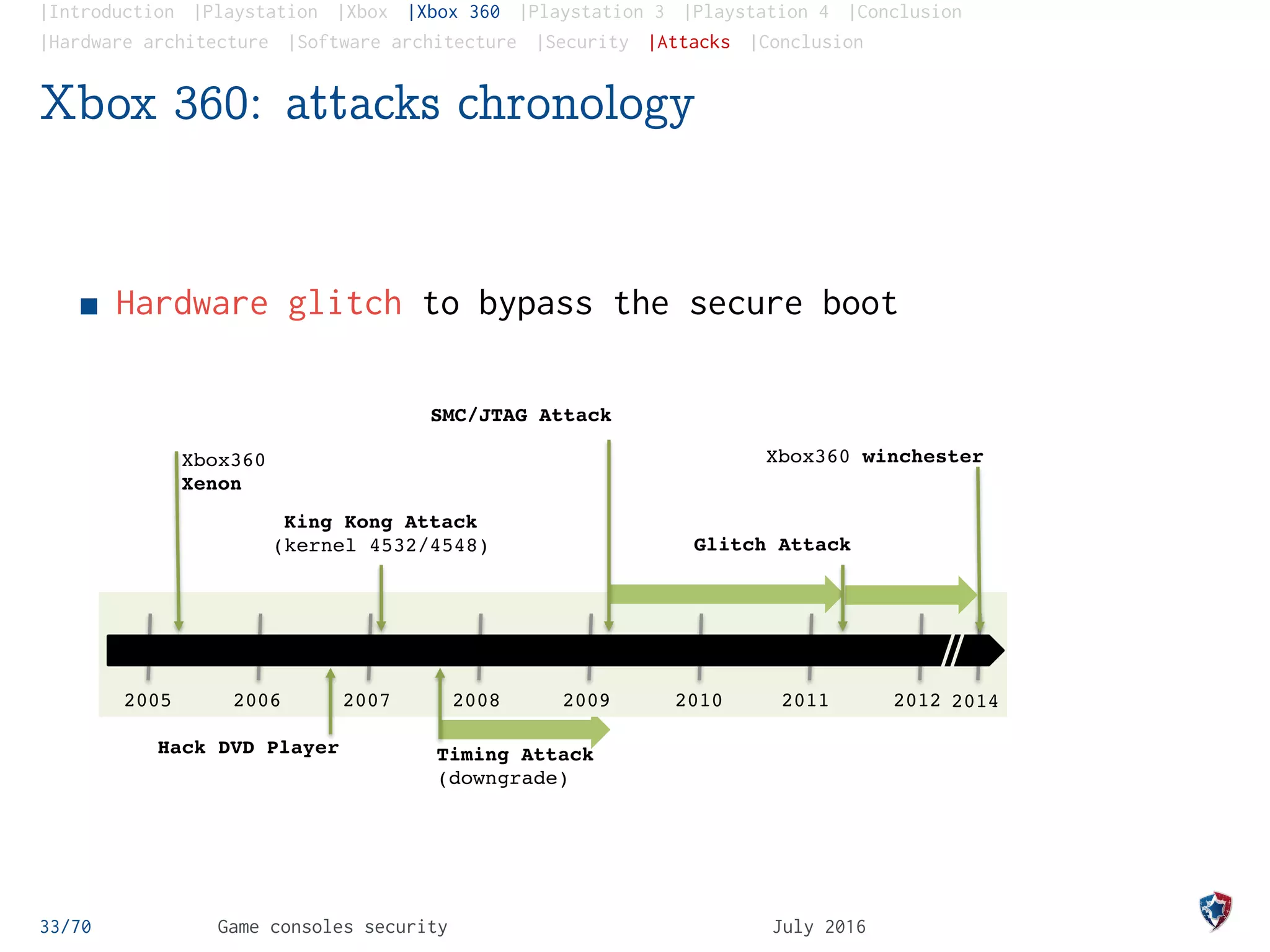
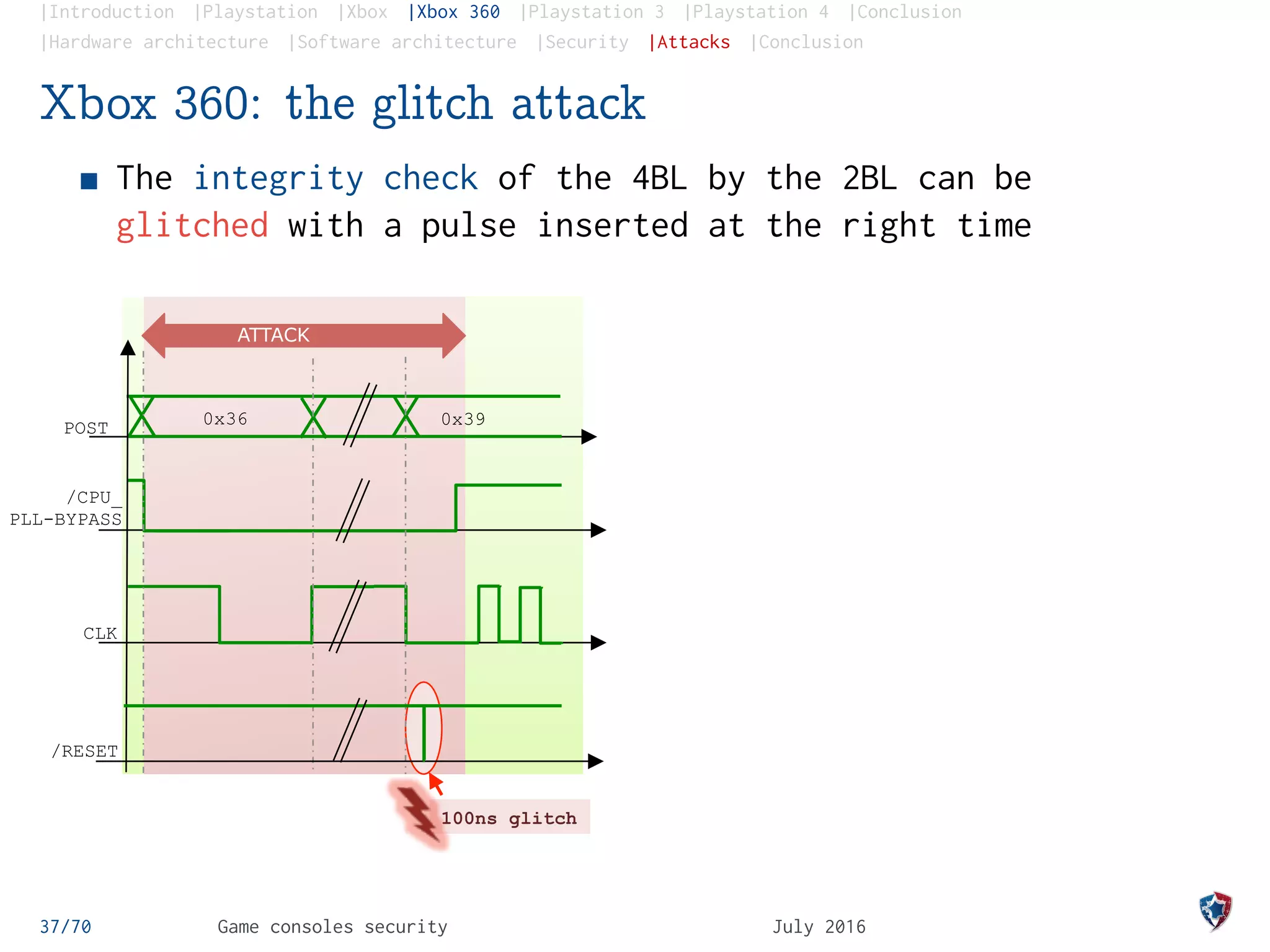
Xbox 360: the glitch attack
The integrity check of the 4BL by the 2BL can be
glitched with a pulse inserted at the right time
100ns glitch
CLK
0x36 0x39POST
ATTACK
/RESET
/CPU_
PLL-BYPASS
FALSE TRUE
Not Glitched
isHashValid(
h1,h2
,len)
{
[…]
Res
=
memcmp(h1,h2,len)
If
(res
==
0
){
return
TRUE
}
return
FALSE
}
Glitched
RAZ des registresReseting all registers >> Res = memcmp(h1,h2,len)
37/70 Game consoles security July 2016](https://image.slidesharecdn.com/mrenard-rbenadjila-gamingconsolesecurityhip2016-160711132819/75/SECURITY-OFFENSE-AND-DEFENSE-STRATEGIES-VIDEO-GAME-CONSOLES-ARCHITECTURE-UNDER-MICROSCOPE-80-2048.jpg)