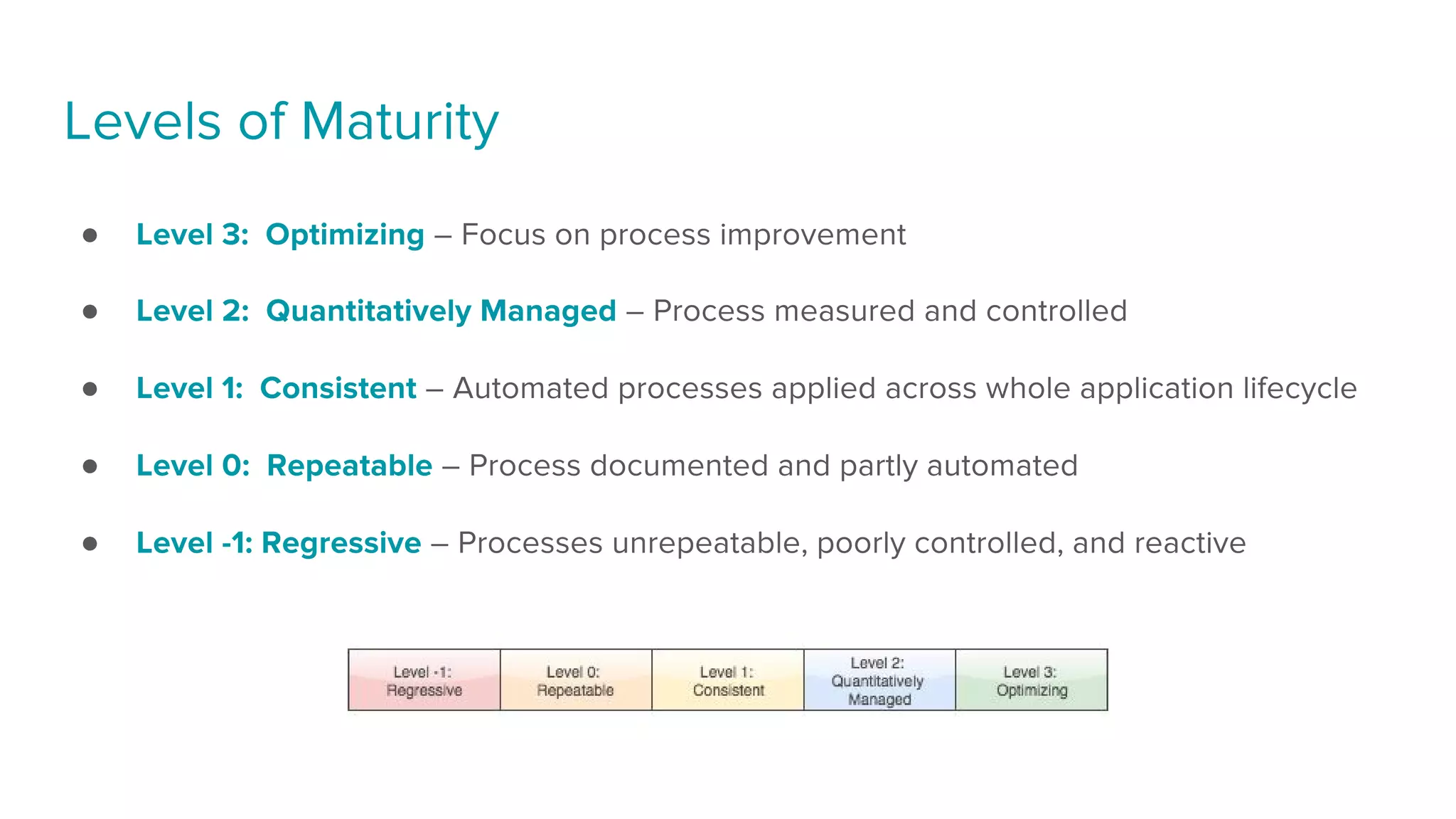
The document discusses the concept of Infrastructure as Code (IaC) and details a maturity model for organizations to assess and improve their infrastructure management processes. It outlines various levels of maturity from regressive to optimizing, along with associated business values such as reduced cycle time and defects. Additionally, it provides insights into automated tools and practices that promote efficient infrastructure management and continuous delivery in software development.






![HashiCorp Packer
{
"variables": {
"aws_access_key": "",
"aws_secret_key": ""
},
"builders": [{
"type": "amazon-ebs",
"access_key": "{{user `aws_access_key`}}",
"secret_key": "{{user `aws_secret_key`}}",
"region": "us-east-1",
"source_ami": "ami-fce3c696",
"instance_type": "t2.micro",
"ssh_username": "ubuntu",
"ami_name": "packer-example {{timestamp}}"
}]
}
Docker Dockerfile
FROM ubuntu:16.04
MAINTAINER Docker
RUN apt-key adv --keyserver
hkp://keyserver.ubuntu.com:80 --recv EA312927
RUN echo "deb http://repo.mongodb.org/apt/ubuntu" $(cat
/etc/lsb-release | grep DISTRIB_CODENAME | cut -d=
-f2)/mongodb-org/3.2 multiverse" | tee
/etc/apt/sources.list.d/mongodb-org-3.2.list
RUN apt-get update && apt-get install -y mongodb-org
RUN mkdir -p /data/db
EXPOSE 27017
ENTRYPOINT ["/usr/bin/mongod"]
https://github.com/hashicorp/terraform/blob/master/examples/aws-two-tier/main.tf](https://image.slidesharecdn.com/iacmaturitymodelfinal-161206052159/75/Infrastructure-as-Code-Maturity-Model-v1-8-2048.jpg)
![AWS CloudFormation
services:
sysvinit:
nginx:
enabled: "true"
ensureRunning: "true"
files:
- "/etc/nginx/nginx.conf"
sources:
- "/var/www/html"
php-fastcgi:
enabled: "true"
ensureRunning: "true"
packages:
yum:
- "php"
- "spawn-fcgi"
sendmail:
enabled: "false"
ensureRunning: "false"
HashiCorp Terraform
resource "aws_instance" "web" {
connection { user = "ubuntu" }
instance_type = "m1.small"
Ami = "${lookup(var.aws_amis, var.aws_region)}"
Key_name = "${aws_key_pair.auth.id}"
vpc_security_group_ids =
["${aws_security_group.default.id}"]
Subnet_id = "${aws_subnet.default.id}"
provisioner "remote-exec" {
inline = [
"sudo apt-get -y update",
"sudo apt-get -y install nginx",
"sudo service nginx start",
]
}
}](https://image.slidesharecdn.com/iacmaturitymodelfinal-161206052159/75/Infrastructure-as-Code-Maturity-Model-v1-9-2048.jpg)