Privacy KPIs.pdf
- 1. There is a governance framework in place, which defines the governance structures within the organisation to support the data protection / information governance, records management and information security management agendas Overall responsibility for information governance has been allocated at a Board level. There is a Data Protection Officer in place with designated responsibility for data protection compliance. The DPO role has operational independence and appropriate reporting mechanisms are in place to senior management Operational roles and responsibilities have been assigned for the day to day management of records management, information security and data sharing There is an Information Management Steering Group, or equivalent, in place, which is responsible for providing the general oversight for information governance and data protection compliance activity within the organisation. The Information Management Steering Group, or equivalent, has a work plan / action plan in place, for routinely monitoring and mandating data protection improvements. Information risks are managed throughout the organisation in a structured way so that management understands the business impact of personal data related risks and manages them effectively to assure the business of the organisation. There is a forum in place to facilitate operational staff raising data protection, records management, information security and data sharing issues and risks which are escalated to a central point. There is a policy framework for data protection, records management, information security management and data sharing management, which stems from an overarching information governance agenda endorsed by the Board through its strategic business planning process All policies, procedures and guidelines follow an agreed format and styling. They contain version control and document change history. There is a defined process implemented to ensure all new and existing policies and procedures are reviewed, ratified and approved. Policies and procedures are available on the organisations Intranet site. A formal sign off process is in place and contracted evidence to support the fact that employees have read and are aware of the policies published. A structure of producing weekly / monthly bulletins / news letters is in place to help disseminate and inform staff of new policies and subsequent updates. There is an overarching IG training programme in place which includes training for all staff on the following key policy areas: Data protection / GDPR Information security Records management Data sharing Requests for personal data Guidelines, posters or publications are written and used within the organisation for the purpose of promoting awareness of staff responsibilities toward data protection compliance. Written Contracts include all the compulsory details and terms as outlined in the GDPR Contracts include the technical and organisational security measures the processor will adopt (including encryption, pseudonymisation, resilience of processing systems and backing up personal data in order to be able to reinstate the system). There are procedures in place with all processors to ensure GDPR obligations in relation to the notification of personal data breaches, complying with the rights of individuals and data protection impact assessments are met. Routine compliance checks are conducted to provide assurances that all Processors have procedures in place to comply with their specific legal obligations outlined under the GDPR Routine compliance checks are conducted to test Processor staff data protection training completion, and their awareness and understanding of data protection policies and procedures. Routine compliance checks are conducted to test that the data security arrangements are effective and comply with contractual agreements. There is a programme of risk- based internal audit in place covering information governance / data protection. Routine compliance checks / audits are performed on manual and electronic files to assess adequacy and accuracy Policies and Procedures For any Processor acting on behalf of the organisation, the organisation monitors their compliance with information governance policies (as outlined in the written Contract) and regularly reviews the effectiveness of data handling and security controls. There is a written contract (or other legal act) in place to evidence and govern the working relationship with processor(s). Processors Management support and direction for data protection compliance, records management, information security and data sharing is set out in a framework of policies and procedures, which are approved by senior management and subject to routine review to ensure they remain fit-for-purpose. Governance & Accountability Scope: The extent to which information governance accountability, policies and procedures, performance measurement controls, and reporting mechanisms to monitor data protection compliance to both the GDPR and national data protection legislation are in place and in operation throughout the organisation. Risk: Without robust governance and accountability processes for evaluating the effectiveness of information governance policies and procedures there is a risk that personal data may not be processed in compliance with the regulations resulting in regulatory action and/or reputational damage. There is a management framework, including a delegated process of accountability and responsibility from the board down, to ensure there is effective oversight of data protection compliance. Management structures Control Domain Control measure
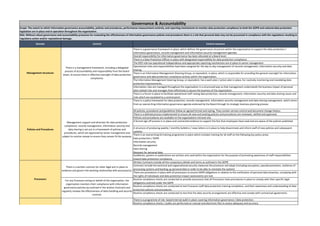
- 2. Routine compliance checks are conducted to test staff awareness and understanding of data protection policies and procedures. A central action plan is in place for data protection, information security, records management related audits. The organisation has identified a series of self assessment tools and external accreditation / certification providers or Codes of Conduct with a view of enhancing the control environment in place around data handling and information assurance. There are data protection Key Performance Indicators (KPI) in place, including reporting on SAR performance - volume of requests and % completed within statutory timescales There are data protection training Key Performance Indicators (KPI) in place, including % completion report for mandatory training covering data protection / information governance related topics There are information security Key Performance Indicators (KPI) in place, including number of security breaches, incidents and near misses and results of security spot checks such as clear desk sweeps. There are records management Key Performance Indicators (KPI) in place, including use of metrics such as file retrieval statistics, adherence to disposal schedules, performance of system in place to index and track paper files containing personal data Performance to IG KPIs is reported and reviewed regularly at senior management / Board level, which provides the Board with a high level view of organisational performance. An information flow mapping exercise has been completed to identify the various types of processing being carried out. There is an internal records of all processing activities undertaken by the organisation (controller) and any processors in line with the requirements set out in Article 30 of the GDPR. The lawful basis for processing personal data and special categories of personal data has been identified, defined and documented internally. The lawful basis for processing personal data and special categories of personal data has been explained in the organisations privacy information. Consent mechanisms used meet the GDPR requirements on being specific, granular, clear, prominent, opt-in, documented and easily withdrawn. There are records of when and how consent was obtained from individuals. Consents are regularly reviewed to check that the relationship, the processing and the purposes have not changed and there are processes in place to refresh consent at appropriate intervals. There are publicised processes in place to allow individuals withdraw their consent at any time, and individual requests to withdraw consent are acted on without delay. There are systems in place to verify individuals’ ages and to obtain and record parental or guardian consent where required when providing online services directly to children (where the organisation is relying on consent as the lawful basis for processing). When providing online services directly to children, privacy information is communicated in a clear plain way that a child will understand. Data minimisation & pseudonymisation There are internal policies and measures in place which outline the organisations approach to data minimisation and pseudonymisation. Transparency The organisation actively publishes / communicates privacy information to keep their service users or customers informed on how their data is collected, processed and/or shared. The information includes all the required information as outlined in the GDPR. Core privacy considerations have been built into existing project management and risk management methodologies and policies There is evidence to support that DPIA(s) are carried out prior to any type of processing which is likely to result in a high risk to individuals’ interests or for any major new project involving the use of personal data. The organisation monitors its own compliance with information governance policies and regularly reviews the effectiveness of data handling and security controls. Information on processing activities Data protection by design and default Compliance and Assurance There has been a review of the various types of processing the organisation carries out and the lawful basis for processing activities have been documented. Online services for children The use of 'Consent' as the lawful basis (or condition) for processing, Lawful basis for processing personal data Data protection impact assessments (DPIA)