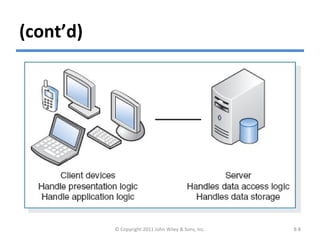
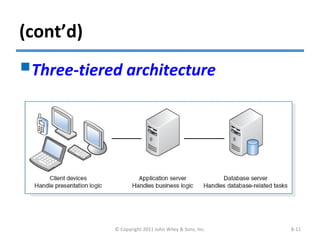
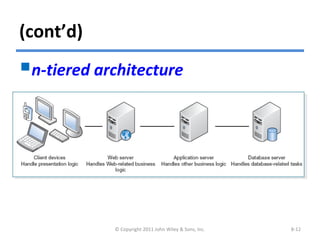
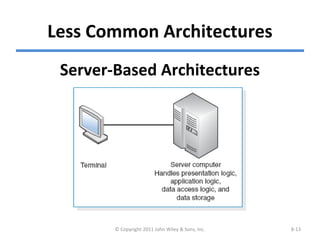
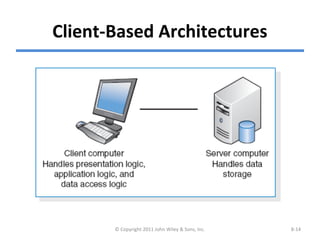
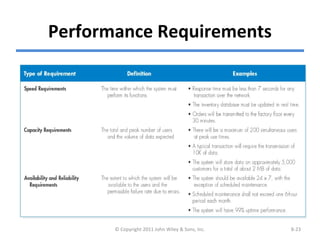
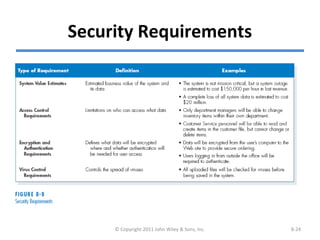
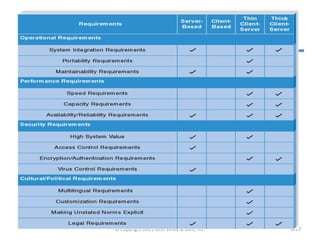
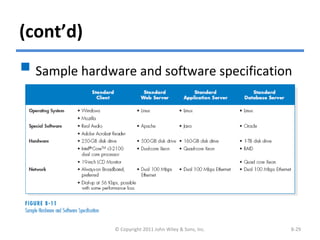
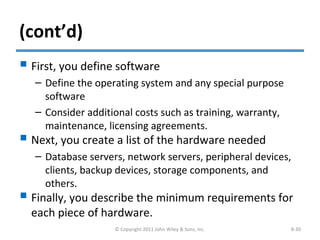
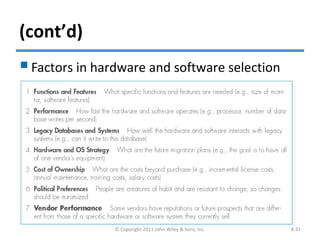
The chapter discusses architecture design for systems analysis and design. It covers elements of an architecture design including client-server architectures. Architecture design begins with nonfunctional requirements and considers factors like performance, security, and operations. Hardware and software specifications define the technical environment needed to support the application architecture.