SELinux (Security Enhanced Linux) is an internal firewall that confines processes and protects the operating system through mandatory access controls. It prevents processes from accessing files or resources without permission. SELinux enforces a security policy that defines what subjects (users and programs) can access which objects (files, devices, ports). It provides confinement for untrusted programs and limits the damage that can be caused by malicious software.







![Getting SELinux (3/5)
SELinux userland packages [gse]
checkpolicy
policy compiler.
uses libsepol.
libselinux
library for security-aware applications.
uses libsepol.
libsemanage
library for policy management tools.
uses libsepol, libselinux.
10](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-10-2048.jpg)
![Getting SELinux (4/5)
SELinux userland packages [gse]
libsepol
library for binary policy manipulation.
no dependency.
policycoreutils
several policy-related utilities.
uses libselinux, libsepol, libsemanage.
sepolgen
python library that forms the core of modern audit2allow.
11](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-11-2048.jpg)
![Getting SELinux (5/5)
Policy
SELinux reference policy project [rpp]
12](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-12-2048.jpg)
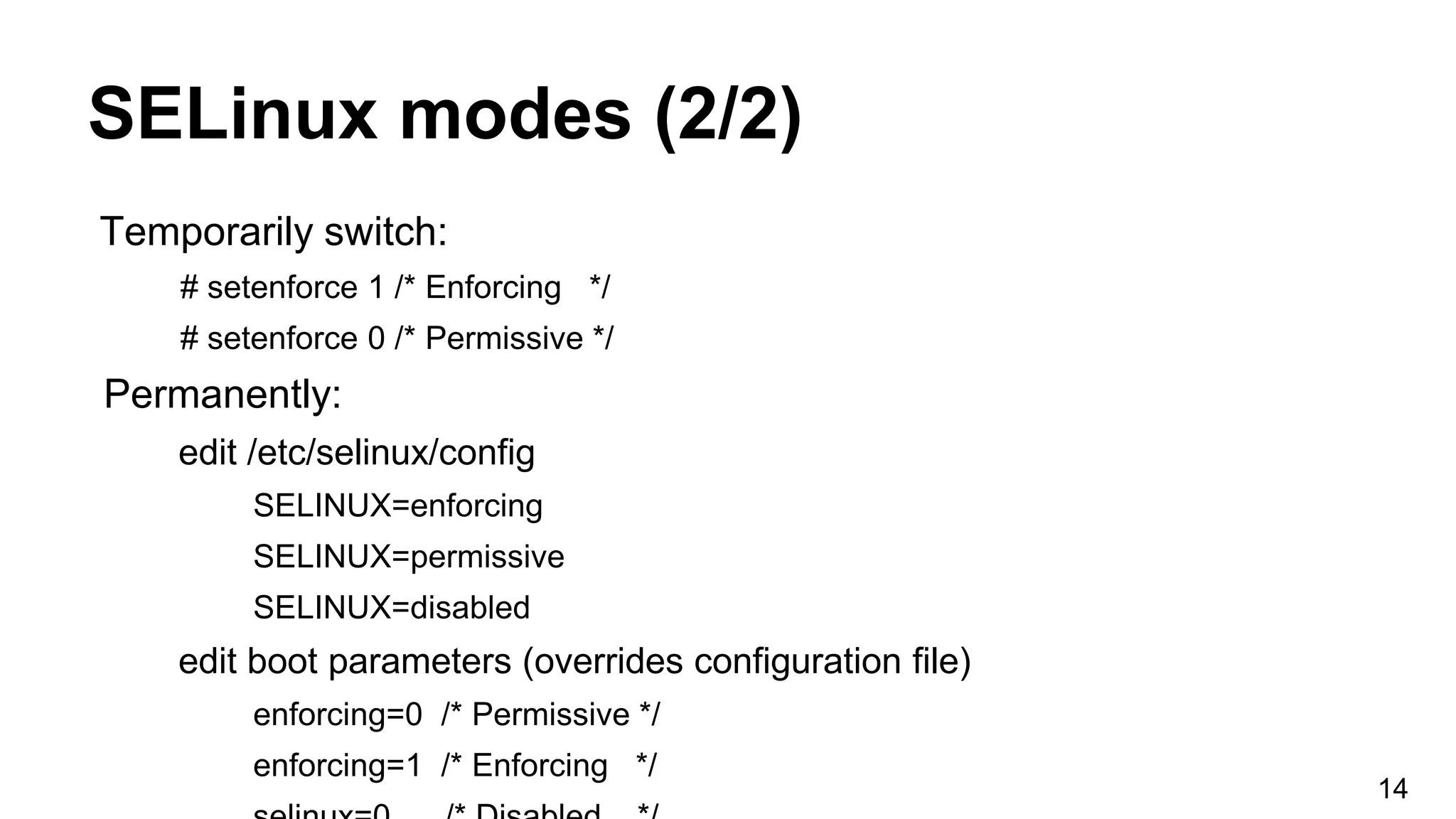
![SELinux modes (1/2)
Permissive
Log warnings instead of enforcing.
CONFIG_SECURITY_SELINUX_DEVELOP
extra: Permissive domain recipe [pdr]
Enforced
Security policy is enforced.
Disabled
Do not load security policy.
CONFIG_SECURITY_SELINUX_BOOTPARAM
Add selinux=0 to kernel bootline.
13](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-13-2048.jpg)
![Basic concepts (1/5)
Security context
Every process and object has a context.
Syntax: user:role:type[:range]
MLS range is optional.
Inherited from processes (on fork) or parent files/directories.
Users
Diff. from linux users*
SELinux users do not change during a user session, whereas a Linux user
might change via su or sudo.
suffix: *_u. e.g. user_u
associated to one or more roles that the SELinux user is allowed
to use.
15](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-15-2048.jpg)

![Basic concepts (3/5)
17
Ranges
Security level.
if policy supports MCS / MLS.
Object classes
Categories of objects.
# ls /sys/fs/selinux/class
Each class has a set of permissions. [ocp]
# ls /sys/fs/selinux/class/tcp_socket/perms/
Rules
Specified using the type of the process and object.
e.g. allow user_t user_home_t:file { create read write };](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-17-2048.jpg)
![Basic concepts (4/5)
18
Booleans
are used to enable/disable policies.
# getsebool -a
# sesearch -b selinuxuser_execheap -AC
ET allow user_t kernel_t : system syslog_read ; [ user_dmesg ]
Rule will be allowed if corresponding boolean is true (T). And boolean is now enabled. (E)
Constraints
under which circumstances an operation is allowed.
circumstances that don't match are disallowed.
# seinfo --constrain
e.g. constrain dir_file_class_set { create relabelto relabelfrom } (
u1 == u2
or t1 == can_change_object_identity );](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-18-2048.jpg)
![Basic concepts (5/5)
19
Type transition
for objects (files):
# sesearch -T
type_transition [Creating Subject type] [Parent Object/Subject Type] : [Class
of new Object/Subject] [New Object/Subject Type]
for subjects (process):
# pstree -Z
# sesearch -T -c process
type_transtion [Parent process type] [Type of process] : process [New type of
the process created]](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-19-2048.jpg)
![Linux user mapping (1/1)
20
Map a linux user to only one
SELinux user. [ual]
Multiple linux users can be
mapped to same SELinux
user.
# semanage login -l
# semanage login -a -s staff_u
emrecan](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-20-2048.jpg)
![Multi-level security and MCS (1/2)
22
based on the Bell-La Padula model
“no write down” and “no read up”
user:role:type:sensitivity [:category,...] - sensitivity [:category,...]
| LEVEL | - | LEVEL |
| RANGE |
sensitivity: s0 lowest, s15 maximum
category: optional, c0.c255.
unordered and unrelated lists of "compartments".
level: combination of sensitivity and category.
translate to human readable form in setrans.conf
s0 = unclassified, s15 = top secret
c0 = finance, c100 = commercial, c255 = book](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-22-2048.jpg)

![SELinux policies (3/3)
Reference policy project [rpp]
basis for creating other policies.
well-written and good enough for PC distros.
many dependencies:
checkpolicy
policycoreutils
libsepol
libsemanage
python
26](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-26-2048.jpg)

![Userland tools (4/4)
restorecon, restorecond*
restores default context of a file.
customizable types [wct]
context is not reset during a standard relabel operation.
# cat /etc/selinux/targeted/contexts/customizable_types
runcon
change context of a program when started (temporary)
runcon system_u:system_r:crond_t:s0:c0.c255 /bin/bash
run_init [gs]
start services in the correct domain
run_init /etc/init.d/ssh start
30](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-30-2048.jpg)
![Performance (1/1)
Hard to measure.
Overhead app~ 7% for completely untuned
code. [faq] [ffq]
31](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-31-2048.jpg)
![License (1/1)
GNU General Public License (GPL) [sel]
32](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-32-2048.jpg)

![Questions about SELinux (1/1)
Can I use SELinux with grsecurity (and PaX)?
Yes, even recommended. However grsecurity’s ACL support is not used together
w/ SELinux. [gfq]
If root user can change, for example booleans, how is selinux more
secure than DAC of linux?
i.e. setsebool -P allow_execheap on/off
We don't need to have conditional policy. If we do, the enabled/disabled rules are
defined in the policy. DAC doesn't have predefined conditions like that.
Can we write a policy that doesn’t allow setenforce?
Yes, moreover we can even compile the kernel so permissive mode is disabled no
matter what the policy says.
34](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-34-2048.jpg)
![References (1/2)
[faq] http://www.crypt.gen.nz/selinux/faq.html
[gse] https://github.com/SELinuxProject/selinux
[gs] http://selinuxproject.org/page/Guide/Services
[rpp] https://github.com/TresysTechnology/…
[ocp] http://selinuxproject.org/page/ObjectCl…
[pdr] http://selinuxproject.org/page/Permissi…
[sqp] http://www.cs.virginia.edu/~jcg8f/SELi…
35](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-35-2048.jpg)
![References (2/2)
[sel] https://www.nsa.gov/research/selinux/l...
[ual] http://wiki.gentoo.org/wiki/SELinux/Use...
[wct] http://wiki.gentoo.org/wiki/SELinux/Tuto...
[gfq] http://wiki.gentoo.org/wiki/SELinux/FAQ
[ffq] http://docs.fedoraproject.org/en-US/Fed…
[use] http://www.fosteringlinux.com/category/…
[nb4] http://taiga.selinuxproject.org/~rhaines/
[mls] http://selinuxproject.org/page/MLSStat...
36](https://image.slidesharecdn.com/2wjz4uoesbw5j70i2eky-signature-92e1777e149e0993e474d76613c232e4456bea05d249877065a55a77526d7bae-poli-160203220417/75/Security-Enhanced-Linux-Overview-36-2048.jpg)