AWS CSAA Certification - Mindmaps and StudyNotes
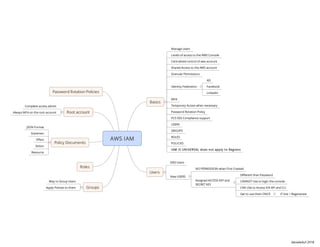
- 1. Basics Manage Users Levels of access to the AWS Console Centralized control of aws account Shared Access to the AWS account Granular Permissions Identity Federation AD Facebook Linkedin MFA Temporary Access when necessary Password Rotation Policy PCS DSS Compliance support USERS GROUPS ROLES POLICIES Users END Users New USERS NO PERMISSION when First Created Assigned ACCESS KEY and SECRET KEY Different than Password CANNOT Use to login the console CAN USe to Access VIA API and CLI Get to use them ONCE IF lost > Regenerate Groups Way to Group Users Apply Policies to them Roles Policy Documents JSON Format Statemen Effect Action Resource Root account Complete access admin Always MFA on the root account Password Rotation Policies danieleduf 2018
- 2. Basics SAFE PLACE to STORE FILES Store FILES - Photos, Flat Files Unlimited Storage Files stored in BUCKETS Key - Name of the Object Value - data, sequence of bytes Version ID Metadata Subresources Access Control List Torrent DATA SPREAD across Multiple Devices and Facilities https://s3-us-west-1.amazonaws.com/mybucket Availability Built for 99.99% Amazon guarantees 99.90% Durability 99.999999999% Tiered Storage Available Life Cycle Management Versioning Encryption Secure Data ACL Bucket Policies Read After Write Consistency Eventual Consistency (can take some time to propagate) 99.99% Availability 99.999999999% Durability Stored Redundantly accross Multipe Devices and Multiple Facilities Min object Size - 0 B Storage Duration - N/A Design to sustain Loss of 2 facilities SSL Support and Lifecycle Mgmgt Policies First Byte Latency of Milliseconds 99.99% Availability 99.999999999% Durability Data accessed Less frequently Rapid Access when needed Lower fee than S3 Fee for Retrieval Min object Size - 128 KB Storage Duration - 30 Days SSL Support and Lifecycle Mgmgt Policies First Byte Latency of Milliseconds 99.99% Availability 99.99% Durability Reduced Redundance Storage Access over a given year of Data that is easily Reproducible, ex: Thumbnails Facility Fault Tolerance = 1 SSL Support and Lifecycle Mgmgt Policies First Byte Latency of Milliseconds N/A Availability 99.999999999% Durability Very Cheap - $0.01 per GB/month ONLY for Archival 3-5h for retrieval/Restore Min object Size - 0 KB Storage Duration - 90 Days Lifecycle Policies YES Storage Requests Storage Management Pricing Data Transfer Pricing Transfer Acceleration Enables FAST EASY and SECURE Transfers over long distances Leverages CloudFront Edges Locations Data > Edge Locations > S3 Over optimized network path Uses CloudFront Edge Network to Accelerate uploads to S3 Link to Edge Location that will transfer to the buket S3 -Versioning Stores all versions of an Object Great Backup Tool Once enabled CANNOT BE DISABLED ONLY SUSPENDED Integrates with LifeCycle Management rules MFA Delete Capability - Additional Level of Security Only Owners of bucket can delete When deleting a DELETE MARKER is ADDED significant increase in the number of HTTP 503-slow down responses received for PUT or DELETE = having one or more objects in the bucket for which there are millions of versions enables automatic, asynchronous copying of objects across buckets in different AWS Regions buckets can be owned by different AWS accounts Versioning must be enabled in both source and destination bucket Regions must be unique Files in an existing buck are not replicated automatically All subsequent files will be Not Daisy Chaining - CANNOT replicate to multiple buckets DELETE MARKERS are replicated Deleting individual versions or delete markers - NOT REPLICATED S3 Must have permissions to replicate objects in your behalf Permissions are granted using IAM role Configuration Destination bucket Objects to be replicated All Subset providing Key Name prefix By Default, S3 uses same storage class for replica Different Class can be set in the destination bucket Replication Same Key name and Metadata Same Storage class unless defined differently ACL Data is encrypted using SSL Use Case Scenarios CRR Multiple Geo Different AZ Dictates store data further distancess Closer to customers Compute clusters in different regions that use same data Owner override to restrict access to replicas Cross-Account source and destination different owners (AWS accounts) IAM role with permissions to replicate in destination via Policy Optionally - direct S3 to change ownership of replica to the AWS account that owns destination S3 - Lifecycle Management Used with Versioning Can be applied to current and previous versions Actions Transition Transition to S3 IA - 128Kb and 30 days after creation Archive to Glacier - 30d after IA Archive to Glacier - 1y after creation ExpirationPermanently Delete - Object expires Use cases Uploading of Periodic Logs Frequently Accesed file for a period of time then IA No real-time access required after Archive and then delete Archival Purposes Digital Media Archives Financial and Health Records Configuration APIPUT, GET, DELETE AWS SDK REST API Calls Content Delivery Network System of Distributed Servers that delivers Web Pages or web content based on geo location of user, origin of web server and content deliver server Edge Location - Where content is cached Separate Region or AZ READ AND WRITE CLEARING CACHED OBJECTS is CHARGED OriginOrigin of files, S3, EC2, ELB, Route 53 DistributionName given the CDN is a collection of Edge Locations Web Distribution RTMPUsed for media streaming By Default NEW BUCKETS are PRIVATE Access Control Bucket Policies Access Control List ACL Access Logs Log ALL Requests made to S3 Bucket Can be send to another bucket SSL/TLS Server Side - Each object encrypted with a unique key using multi-factor encryption. - strongest block ciphers (AES-256) - additional benefits and charges than SS3 - separate permissions for the use of an envelope key -provides added protection against unauthorized access - an audit trail of when your key was used and by whom. - option to create and manage encryption keys yourself, or use a default key that is unique to you, the service you're using, and the region you're working in. You manage the encryption keys Amazon S3 manages the encryption and decryption, when you access your objects. Client Side Encrypting data before sending it to Amazon S3 Using AWS KMS CMK Customer Managed Key client-side master key Connects On-Premise Software Appliance with Cloud-Based Storage Securely Store Data for Escalable Cost Effective Storage Is an Appliance, available as VM VMWare, Hyper V Types File Gateway (NFS) For FLAT Files Stored directly in S3 Volume Gateway (iSCSI) Stored Volumes Entire Dataset stored in S3 Asynchronously backed in to S3 In form of EBS snapshots 1GB - 16TB Cached Volumes Entire Dataset in S3 Most Frequently Accessed Data Cached onsite 1GB to 32TB Tape Gateway (VTL) Durable Cost Effective to Archive Data Virtual Tape Library Used for Backup and uses Backup apps like NetBackup Backup Exec Veeam AWS Export/Import Disk Accelerates moving large amount of data in/out AWS Cloud Portable Devices for Transport Transfers data via high-speed internal network, bypassing internet Types Snowball PETA-BYTE Scale data transport Secured Appliances Challenges addressed network costs long transfer tines Security Concerns 80TB Snowball in all regions Security Tamper resistant enclosures 256 bit Encryption Industy Standard Trusted Platform Module TPM Once uploaded, erasure of appliance Snowball Edge 100TB Data Transfer Onboard Storage and Compute capabilities temporary storage tier support local workloads in remote or offline locations Can Cluster SnowMobile EXABYTE-SCALE Transfer up to 100PB Extremely Large amount of data Container - Semitrailer Truck!!!
- 3. Relational Databases - OLTP Traditional Spreadsheet Database Table Rows Fields (Columns) - SQL Server - Oracle - MySQL Server - PostgreSQL - Aurora - MariaDB Non Relational Databases Database Collection = Table Document = Row Key Value Pairs No SQL OLAP OLTP vs OLAP Datawarehousing OLTP - Online Transaction Processing Ex: Order Number 53453 Pulls up Name, Date, Address, Delivery Status OLAP - Online Analytics Processing Ex: Net Profit in EMEA and Pacific Pulls Sum of Sales in EMEA, Sum of Sales in Pacific Deploy, Operate, Scale in-memory cache in the cloud Improves performace of web apps Good Fit for DB READ HEAVY and NOT PRONE to FREQUENT CHANGING Social Networking Gaming Media Sharing Q&A Portals retrieve information from fast managed, in-memory caches Supports open-source in-memory caching engines Types MEMCACHED Widely Adopted MEMORY OBJECT caching system protocol compliant with Memcached REDIS In memory Key Value Store Sorted sets Lists Supports Master/Slave replication Supports Multi AZ used to achieve cross AZ Redudancy Migrates production DB to AWS AWS Manages Data Type Transformation Compression Parallel Transfer - Faster data transfer AWS Schema conversion tool converts source DB schema - Custom code - views, stored procedures, functions to a COMPATIBLE FORMAT with target DB FAST Flexible NoSQL Service Scale DB on the FLY with no downtime RDS not so easy Fully Managed DB Models Supported document Key Value Data For apps that need consistent single digit millisecond latency at any scale Great fit for Mobile Web Gaming Ad-tech IoT Consistency Across all copies reached with seconds Repeating read after short time returns updated data BEST READ Performance Returns a result that reflects all writes that received a successfull response prior to read PRICING Provisioned Throughput Capacity Wirte TP - 0.0065 per hour per eveery 10 unitts Read TP - 0.0065 per hout per 50 units Storage Cost 0.25Gb per month Restoring Backups Automated or Snapshot Restored Version of DB will be NEW RDS Instance with new endpoint Allows recover DB any point in time within a "retention Period" (1 to 35 days) take full daily snapshots stores transactions logs thru day Recovery Process: - Choose Most recent daily backup - Apply Transaction logs relevant to that day - allows to do a point in time recovery down to 1 sec Backup Data Stored in S3You get free Storage = size of your DB Taken during a Window storage I/O may be suspended high latency Done MANUALLY - User Initiated at REST using AWS KMS MySQL, Oracle, SQL Server, PostgreSQL, Maria DB RDS Instace Encrypted Underlying Storage automated backups read replicas Snapshots Not Supported for existing DB MUST Create new Instance with Encryption ENABLED MIGRATE DATA have a copy of DB in another AZ MySQL, Oracle, SQL Server, PostgreSQL, Maria DB not improved performace - READ REPLICAS AWS handles replication and sync READ ONLY COPIES of DB MySQL Server PostgreSQL Maria DB Asyncronous Replication RR primarily for very READ-HEAVY DB workloads Must have automatic backup enabled UP to 5 Read Replicas of your DB Each Replica has its own DNS endpoint CANNOT have RR in Multi AZ CAN RR of source DB in Multi AZ RR can be promoted to be their own DB Breaks Replication RR in a Second Region MySQL Maria Fast, Powerfull Fully Managed Peta-Byte Scale DATA WAREHOUSE service in the cloud Configuration Single Node160 GB Multi-Node Leader Node Manages Client Connections Receives Queries Compute Node Store Data and Perform queries and computations up to 128 Compute Nodes Advanced Compression Multiple Compression Tecniques DOESNT Require indexes - Less Space When Loading Data - Automatically Samples your data Selects the most appropiate compression scheme Massively Parallel Processing Easy to add notes to DWH As it grows Pricing Compute Node Hours not for leader node BACK UP Data Transferwithin a VPC not outside Security In TransitSSL RestAES 256 encryption Takes cares of Key Management Manage your own keys w/ HSM w/ AWS KMS Availability Currently ONLY 1 AZ Can Restore Snapshots to new AZ in event of OUTAGE MySQL compatible Relational DB Engine Availability and Speed of High-End Commercial DBs Up to 5x better performance that MySQL SCALING Autoscalling Starts with 10Gb increments +10Gb Up to 64TB Compute Resourcesup to 32vCPUs and 244Gb of Memory 2 Copies in each AZ min 3 AZ 6 copies of your data! Design to handle loss of 2 copies of datawithout affecting DB Write Desing to handle loss of 3 copies of dataWithput affecting DB Read SELF HEALING Data Blocks and Disks are Continuosly scanned for errors And Repaired REPLICAS AURORA Replicas - currently 15 MySQL Read Replicas - currently 5
- 4. Definition: Provision logically Isolated section of AWS cloud to launch resources Data Center in the cloud Selection of own IP addresses Creation of subnets Route Tables Network Gateways Consists of IGWs (or Virtual Private Gateways Route Tables NACLs Subnets = 1 AZ Security Groups Default VPC Default is USER Friendly Allows you to deplloy instances inmediately All Subnets have route out to internet access Each EC2 Instance has both Private and Public IP VPC Peering Allows VPC connection to another via direct network route using Private IP addresses Instances behave as if they were in same private network Peer VPCs with Other AWS Accounts Peer as well with other VPC in the same account Peering is in STAR CONFIGURATION NO TRANSITIVE PEERING NAT Netowrk Address Translation to PROVIDE INTERNET ACCESS to EC2 Instances in Private Subnets NAT INSTANCES When creating disable source/destination check MUST BE on PUBLIC SUBNET MUST BE route out of the Private Subnet to NAT Instance Traffic Supported depends on Instance Size Bottlenecking? then increase size You can create HA using Autoscalling groups Multiple Subnets in different AZ Script to automate failover NAT GATEWAYS Preferred by the Enterprise Scale Automatically up to 10Gbps No Need to patch NOT Associated to Security Groups Public IP automaticall assigned Update route tables No need to disable source/dest checks More Secure than NAT Instance NACLs NACLs VPC comes with default NACL By default ALL IN OUT traffic is ALLOWED Custom NACL IN OUT Traffic DENIED Until Rules are created Each Subnet must be associated with a NACLIF NOT - Default NACL 1 NACL associated to multiple subnets 1 subnet only to 1 NACL Numbered rules - Starting with LOWEST 99 - 100 -200 IN and OUT Rules BLOCK IP with NALCs NOT Sec Groupts VPC Flow Logs CAPTURE Information IP Traffic to and from the VPC Interfaces Stored using CLOUDWATCH Logs After creating Flow Log View and retrieve in CloudWatch Logs Can be created at 3 leves VPC Subnet Network Interface CANNOT BE ENABLED for VPC Peered to your VPC Unless the Peer VPC is in your account CANNOT Tag a Flow Log CANNOT Change configuration once created Ex: Change IAM Role with FlowLog NOT MONITORED TRAFFIC Traffic generated when instances contact AWS DNS License Activation Windows Instances Traffic from-to 169.254.169.254 DHCP Traffic Traffic to reserved IP Address for default VPC router BASTIONS to SECURELY ADMINISTER EC2 Instances (SSH or RDP) in PRIVATE SUBNETS VPC Endpoints Internal GW rather than NAT Gateway Directly to Public EndPoints such S3 bucket
- 5. Resizable Compute Capacity in the Cloud VM in the cloud provisioned in mins You pay only for the capacity you use Reduces Time to boot servers Scale in capacity, both up and down, as required Fixed rate by the hour (or by the second) with no commitmennt Low cost and flexibility No Up-front payment Used for Applications with short term, spiky or unpredictable workloads that CANNOT be interrupted Applications being developed or tested for the first time Capacity Reservation Discount = hourly charge for an instance 1 to 3 years term Used for Steady State or Predictable Usage Apps that require reserved capacity Up-front payments to reduce costs Standard RI - up to 75% off Convertible RI - Up to 54% off Availability to change attributes of RI Scheduled RI - available to launch within the window time reserve Allows to match capacity reservation bid whatever price you want for instance capacity Greater savings if app have flexible start and end times enable you to request unused EC2 instances key differences between Spot Instances and On-Demand Instances are that Spot Instances can only be launched immediately if there is available capacity - Hourly price varies based on Demand - EC2 can interrupt and individual spot instance as the price for, availability of, Used for various fault-tolerant and flexible apps Test&Dev environments Stateless web servers image rendering Video Transcoding Run Analytics Machine Learning High Performance Computing (HPC) workloads For apps that are only Feasible at very low compute prices Physical EC2 server dedicated help reduce costs by allowing the use of extended server-bound software licenses Used for Regulatory Requirements Not Multi-tenant Virtualization Great for Licensing which does not support Multi-tenancy or cloud deployments Can be purchased on Demand (hourly) Can be purchased as a reservation for up to 70% off D2Dense StorageFile Servers/Data Warehousing/Hadoop R4RAM - Memory OptimizedMemory Intense apps/DBs M4Main Choice, General PurposeApplication Servers C4Compute OptimizedCPU Intesive Apps/DBs G2Graphic IntensiveVideo Encoding/3D App Steaming I2IOPS - High Speed StorageNoSQL DBs/ Data Warehousing F1FPGAHardware Acceleration of your code T2Cheapest General PurpuseWeb Servers/ Small DBs P2Pictures, General PurposeMachine Learning, Bitcoin mining X1X-treme Memory OptimizedSAP HANA/Apache Spark Storage Volumes attached to EC2 Create File System Run a DB Use as a Block Device Placed in specific AZ Automatically Replicated To prevent single point of Failure General Purpose SSD (GP2) Balances both price and performance Ratio of 3 IOPS per GB Up to 10.000 IOPS burst up to 3.000 IOPS for extended periods of time Provisioned IOPS (IO1) I/O Intensive Applications Large relational or No SQL For more than 10.000 IOPS can provision up to 20.000 IOPS per volume Throughput Optimized HDD (ST1) Large amount of sequencial Data Big Data Data Warehousing Log Processing CANNOT BE BOOT VOLUME COLD HDD (SC1) Lowest Cost Storage for IA Workloads File Server Cannot be boot volume Standard Lowest cost per gigabyte of ALL EBS Ideal for workloads of IA Data Apps where lowest cost storage is important Bootable ALL INBOUND Traffic is Blocked by Default ALL OUTBOUT is ALLOWED Changes take effect immediately Any number of EC2 within a group Multiple Sec Groups attached to EC2 Instances CANNOT BLOCK Specific IP - Use ACLs instead Can Specify Allow rules but not deny Volumes and Snapshots Volumes exist on EBSVirtual Hard Disk Snapshots on S3
- 6. Business Benefits of Cloud Almost Zero Upfront INFRASTRUCTURE investment just-in-time Infrastructure More efficient resource utilization Usage-based costing Technical Benefits of Cloud Automation Scriptable infra Auto-Scaling Proactive Scaling More Efficient Development lifecycle Improved Testability Disaster Recovery and Business Continuity Overflow the traffic to the cloud Understanding Elasticity Graphic Infrastructure cost vs Automated Elasticity + Scalability Scaling when needed Design for Failure Rule of thumb Be a Pessimist when designing architectures Assume things will fail Always design, implement and deploy for automated recovery from failure Assume Hardware will fail Outages will occur Disaster will strike Slammed by # of requests Software application will fail Decouple your components Build components w/out tight dependencies on others In case of failure, other components can continue to work Loose coupling isolates various layers and components so that each component interacts asynchronously and treats the others as a black box Examples Web App Architecture Isolate - App Server - Web Server - DB Batch Processing Architecture Asynchronous components Independent to each other Implement Elasticity Proactive Cycling Scaling - Daily - Weekly - Monthly - Quaterly Proactive Event-Based Scaling Scaling when expecting a BIG SURGE of traffic Ex: - New Product Launch - Marketing Campaigns AutoScalling Based on Demand Using Monitoring Service that can send triggers and take appropiate actions Scale up or down based on Metrics Utilization of Servers or network I/O Secure your Application Amazon EC2 Security Group Firewall Only permit WEB LAYER access to APP Layer Port 80 (HTTP) and 443 (HTTPS) Web Layer - Open to Internet Only Permit App Layer access to DB Layer Only port 22 (ssH) of App Layer Open to only developers in corporate office network All other traffic denied
- 7. Shared Responsability Model AWS Customer RISK AWS developed strategic business plan Risk Identification Controls to mitigate or mange risk Re-evaluates biannualy Identify Risk Areas or responsability address risks AWS Sec scans for vulnerabilities - NOT Customers Instances External Vulnerability assessments are performed by independent sec firms Findings & Recommendations Categorized Delivered to AWS leadership For health and viability Not meant to replace customers own vulnerability scans Required to meet their specific compliance requirements Compliance SOC 1 SOC 2 SOC 3 FISMA DIACAP FedRAMP PCI DSS Level 1 ISO 27001 ISO 9001 ITAR Industry Specific Standards HIPAA CSA - Cloud Security Alliance MPAA - Motion Picture Association of America
- 8. Shared Security Model AWS responsible for underlying infrastructure that supports the cloud AWS Protects Global Infra Hardware Software Networking Facilities AWS Responsible for config of its products - Managed Services DynamoDB RDS Redshift Elastic MapReduce Workspaces We are responsible for what we put or connect in the cloud IAAS - All sec configuratiosn EC2 VPC S3 Account Management - User Access Recomm. MFA SSL/TLS CloudTrail with logging for API/User Activity Storage Decommissioning When Storage reaches end of useful life Procedures to prevent data to be exposed Subtema 3 Network Security Transmission Protection You can connect to an AWS AP via HTTP or HTTPS using SSL to protect against tampering, message forgery VPC provides private subnet VPC provides ability to use IPSec Corporate Segregation Production Network is segregated from corporate network Complex set of network security and segregation devices Network Monitoring and Protection DDoS MITM Attacks IP Spoofing host-based firewall denies an instance to send traffic with a source IP or MAC address other than its own Vulnerability Test - Request Permission in advance Port Scanning Packet Sniffing by other Tenants AWS Credemtials Passwords MFA Access Keys Key Pairs X.509 Certificates AWS Trusted Advisor Inspects AWS environment and makes recommendations when there is opp to save money improve system performance close security gaps Alerts on misconfigurations Leaving opened ports Creating IAM accounts for internal users Allowing Public Access to S3 Not logging activity not ussing MFA Instance Isolation Instances running on same physical machine are isolated via de Xen Supervisor AWS Firewall resides within the Hypervisor layer in the middle of the physical network iinterface and the instances virtual interface ALL packets must pass through this layer Physical RAM is separateed similarily Instances have no acess to raw disk devices Other Considerations Guest OS Virtual Instances completely comtrolled by YOU YOU have FULL root access AWS HAVE NO any access rights to your instances or Guest OS Ecryption Is recommended EBS encryption with AES-256 Encryption occurs on the servers that host the EC2 instances, providing encrypt of data as it moves between EC2 instances and EBS storage Encryption feature available in more poweful instances types: M3, C3, R3, G2 Firewall EC2 Provides a complete FW Solution Inboound Firewall . Default DENY ALL Outboud - ALLOWED EC2 Customers must open ports when needed ELB SSL Termination on LB is SUPPORted Allows to identigy originating IP of a client connecting to your servers Whether using HTTPS or TCP load balancing Direct Connect Bypass ISP Dedicated Ciciuts - MLPS Using industry 802.1q VLANS Network Separation between public and private environments
- 9. S3 Import/Export Move large amount of data Storage Gateway Connects on-premise software appliance with Cloud Based Storage Provides Seamless and Secure integration Enables secure store data to AWS for scalable cost effective storage SG is a software appliance and CAN BE DOWNLOADED as a VM SG is installed in your datacenter Needs to be associated with your AWS console account Activation Process GW Cached Volumes Allows you to use S3 as primary data retaining some portion locally in a cache for FA data Minimize need to scale your on premises storage infrastructure up to 32 TB GW Stored Volumes ALL your data Backup mechanism 1TB Pricingfor what you use GW Usage / moth Snapshot Storage Usage - GB/moth Volume Storage Usage - GB/month Data Transfer Out - GB/month Elemento principal 5 Elemento principal 4
