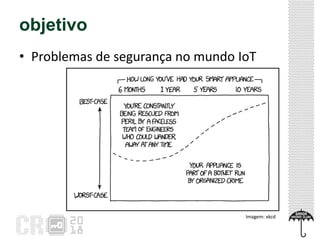
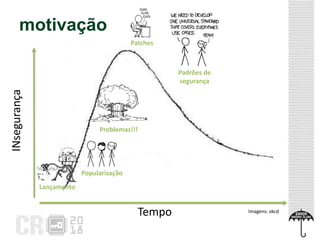
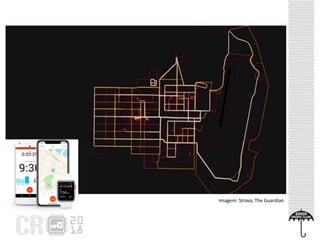
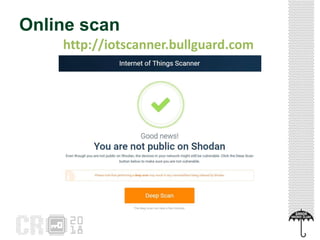
The document discusses the concept of 'Internet of Gossip' (IoT fofoqueiros), referring to IoT devices that can access personal data without authorization, leading to privacy risks. It highlights various security issues related to IoT, including unauthorized data sharing and instances of misuse in devices like smart TVs and robotic vacuums. The text also provides basic security precautions for users to safeguard their IoT devices.