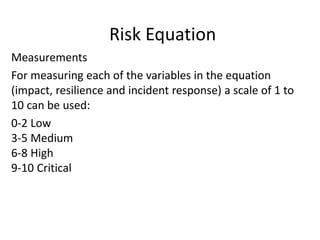
The document proposes a new risk equation that incorporates resilience and incident response alongside traditional probability and impact factors. This revised formula aims to give organizations a clearer understanding of their risk and improve their incident management strategies in response to evolving threats. Two examples demonstrate how to apply this equation to assess risks from cyber attacks and internal fraud, ultimately indicating a high level of risk for both scenarios.