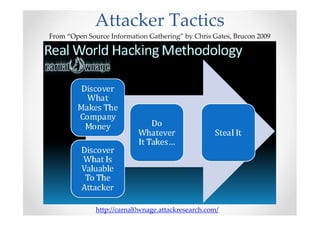
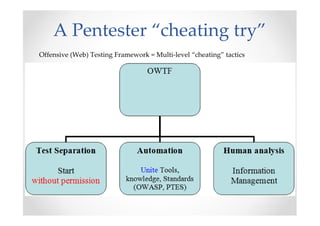
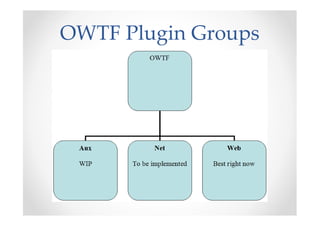
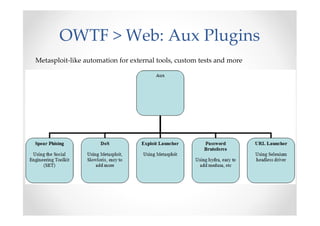
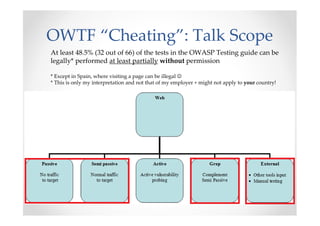
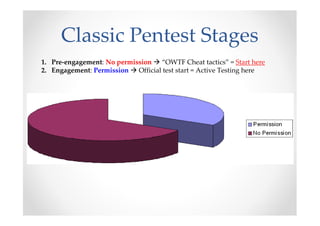
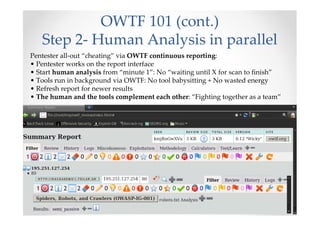
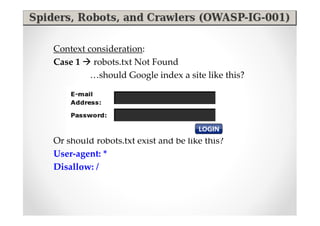
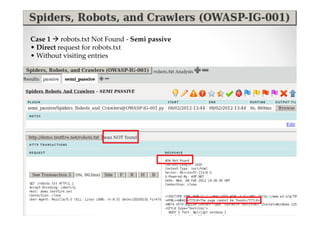
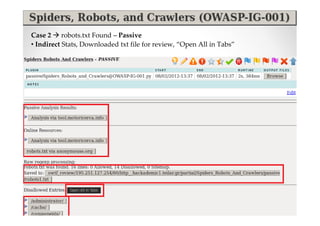
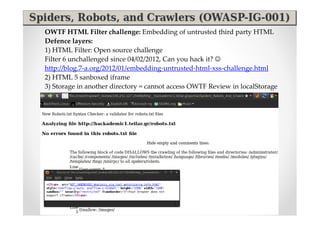
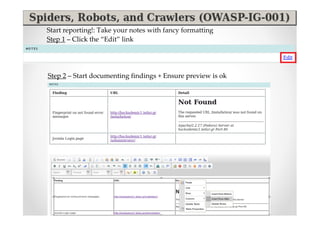
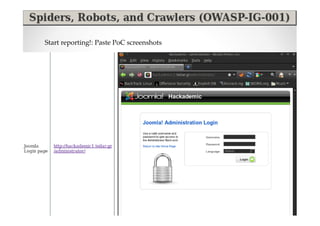
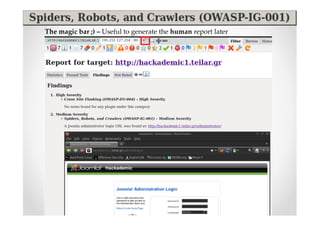
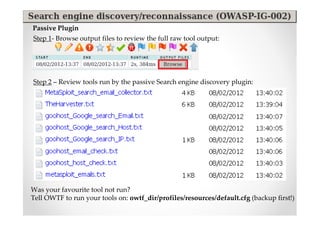
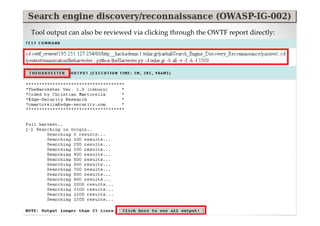
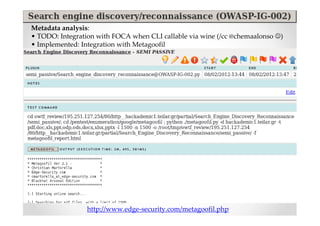
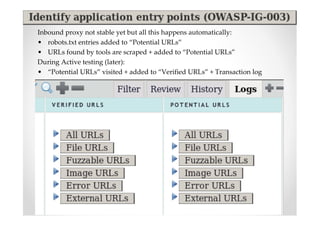
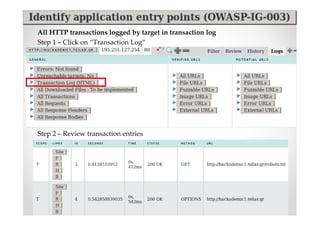
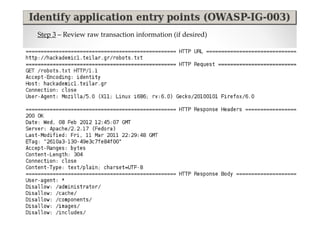
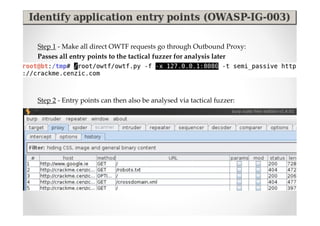
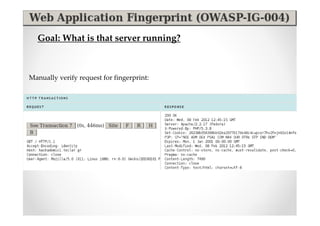
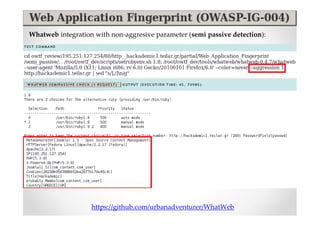
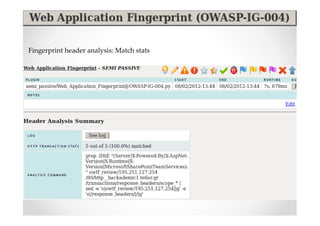
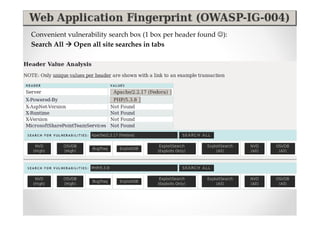
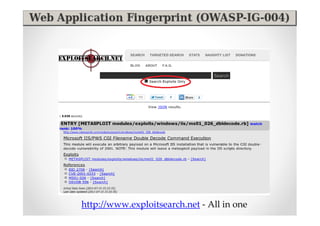
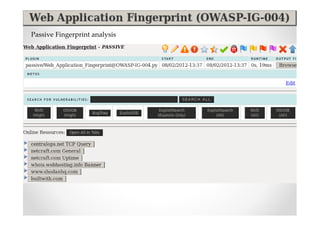
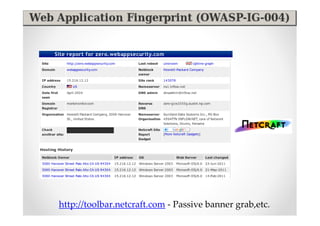
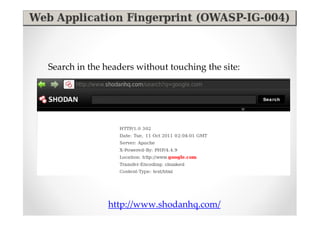
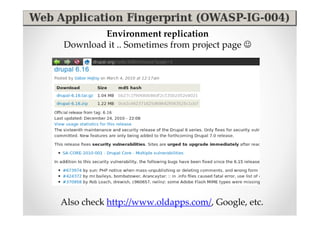
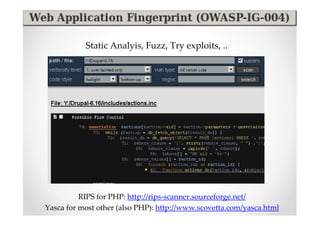
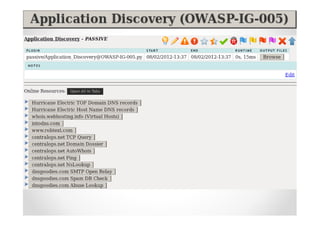
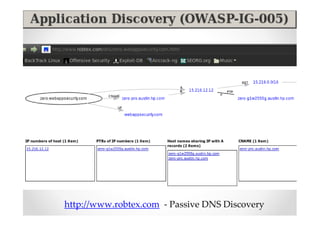
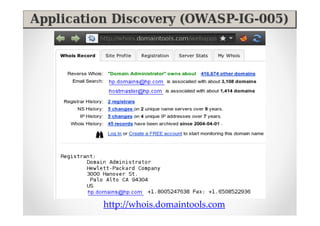
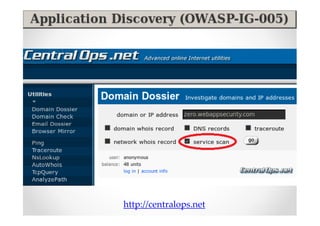
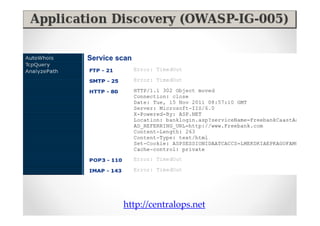
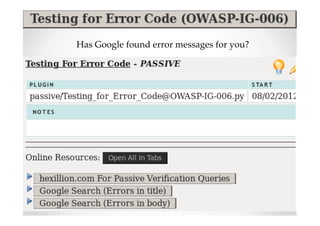
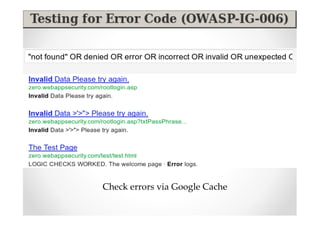
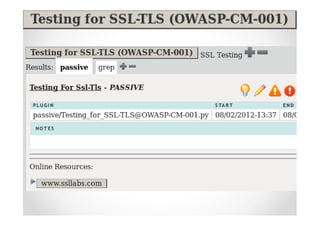
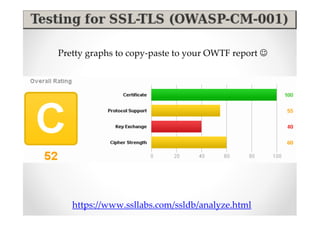
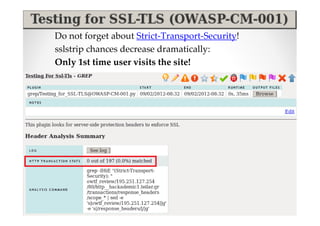
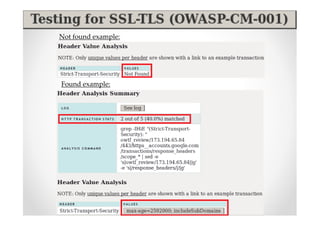
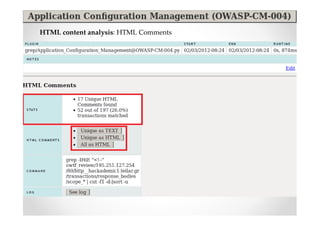
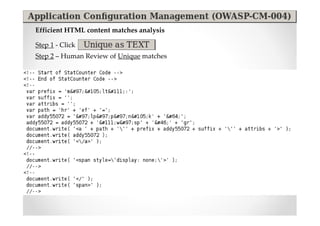
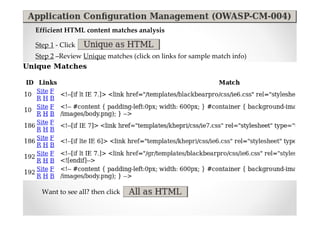
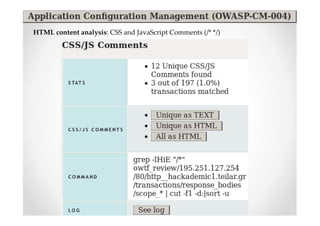
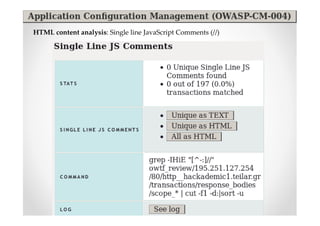
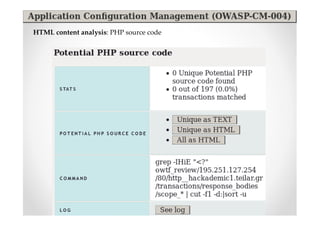
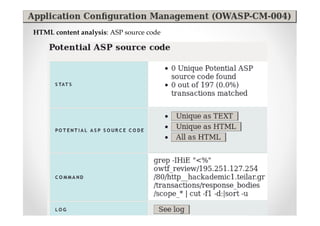
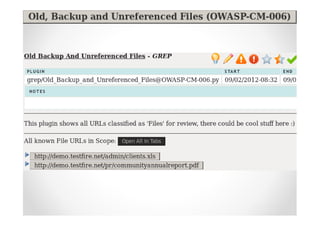
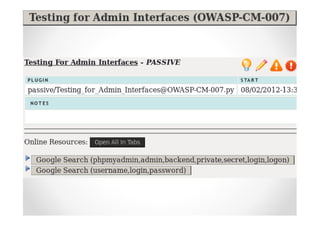
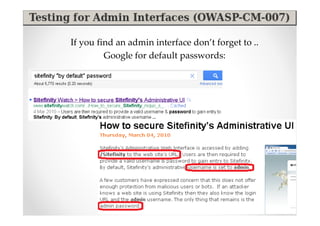
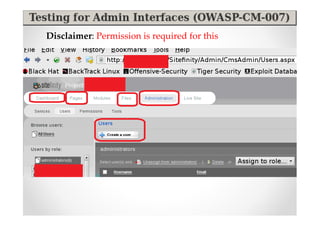
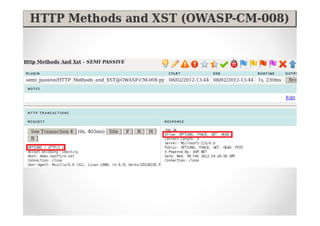
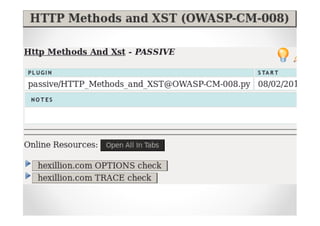
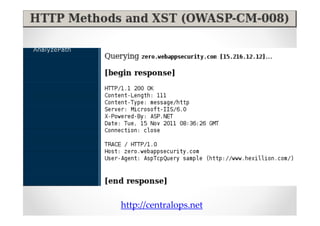
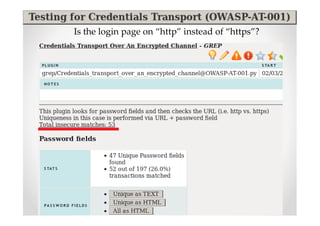
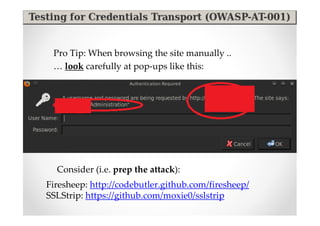
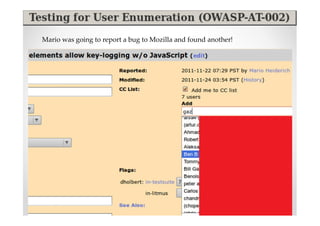
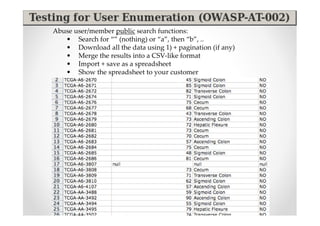
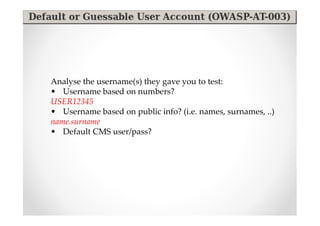
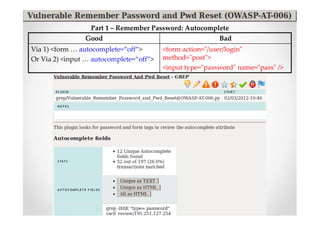
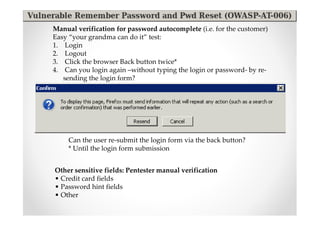
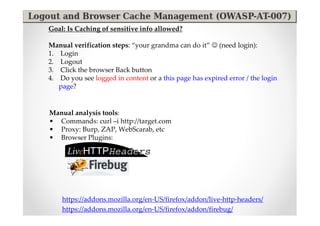
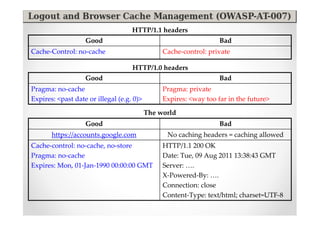
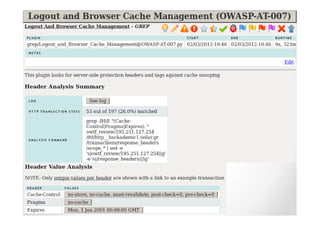
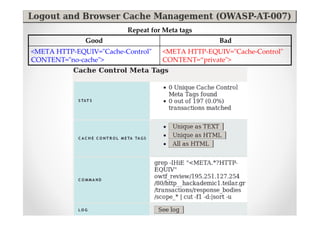
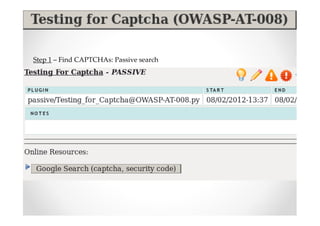
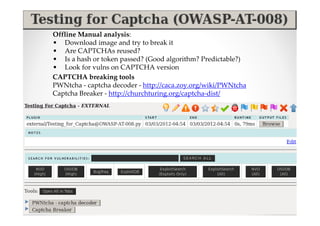
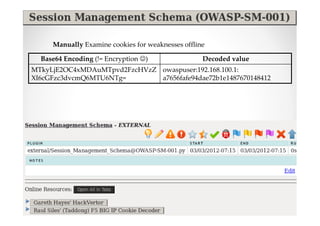
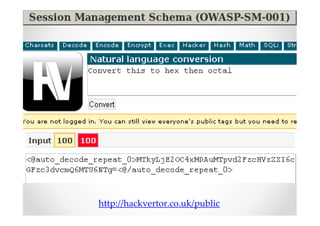
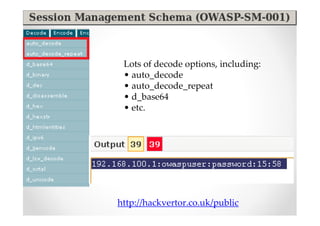
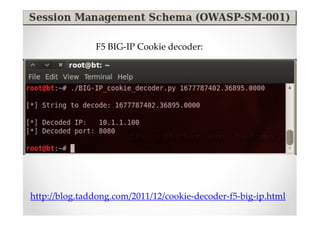
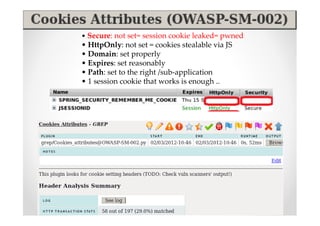
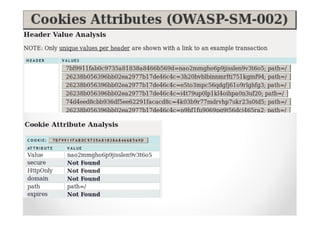
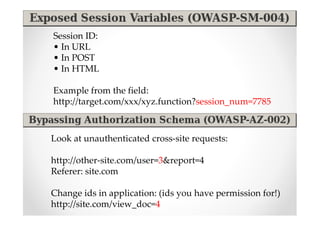
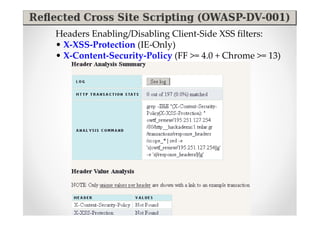
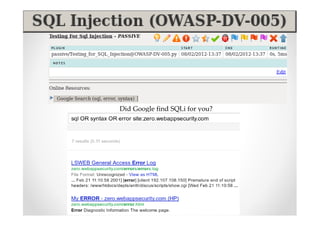
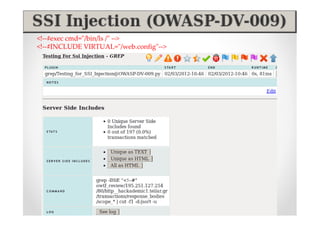
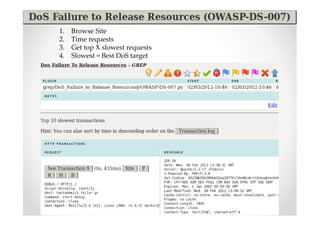
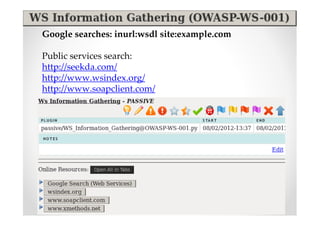
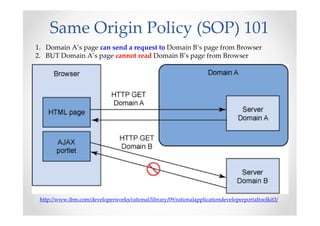
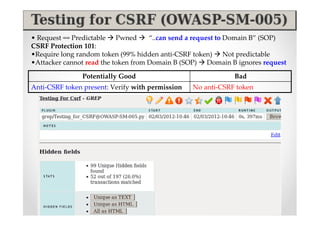
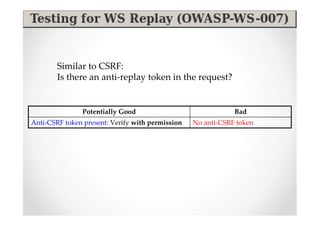
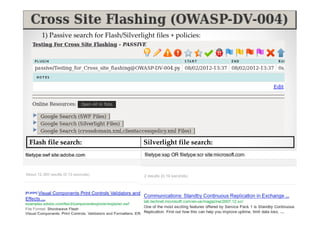
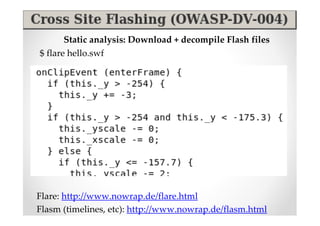
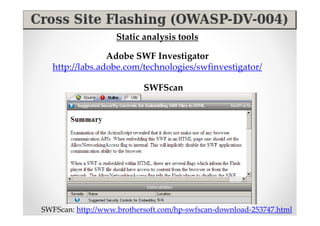
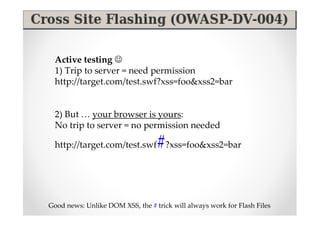
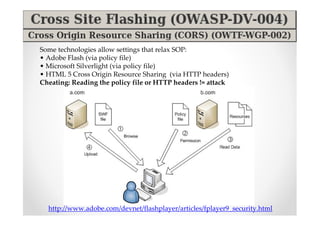
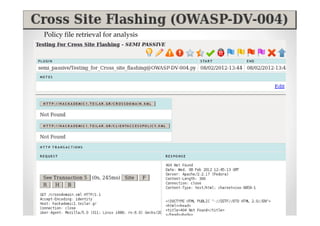
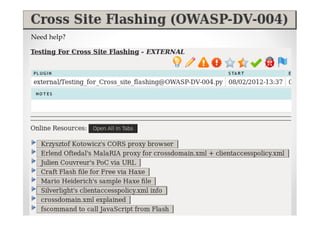
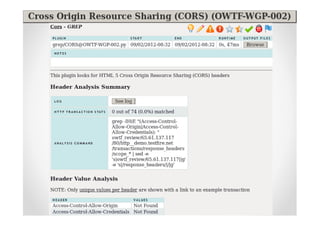
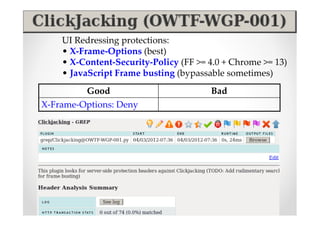
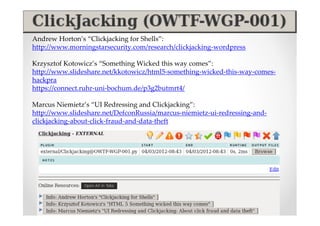
The document discusses efficient and legal web application testing techniques that can be performed without permission. It introduces the Open Web Testing Framework (OWTF) which allows pentesters to run tools and analyze results in parallel through a reporting interface. OWTF utilizes "cheating tactics" like passive information gathering and semi-passive testing to identify vulnerabilities and attack vectors before the official test begins. The document provides examples of how tools in OWTF can be used to profile websites, discover entry points, and identify vulnerabilities in a pre-engagement or reconnaissance phase without active interaction with the target.