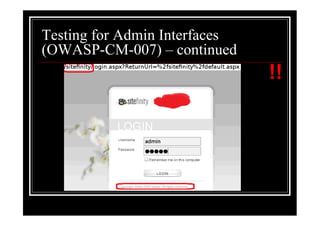
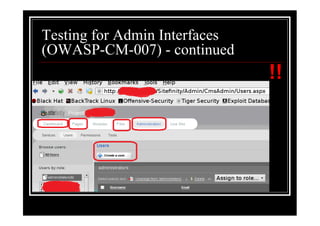
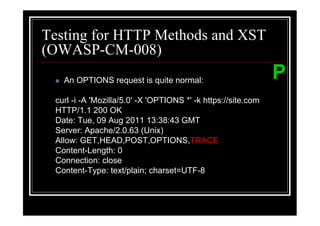
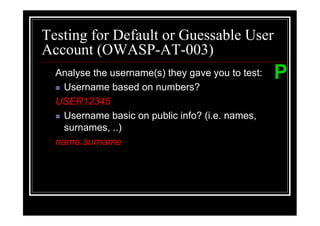
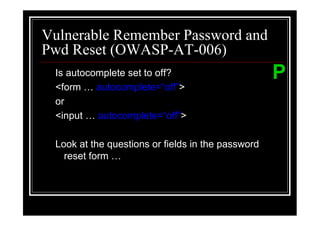
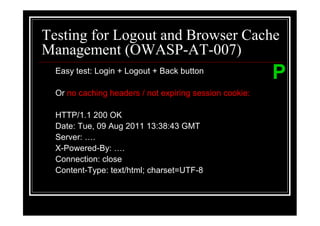
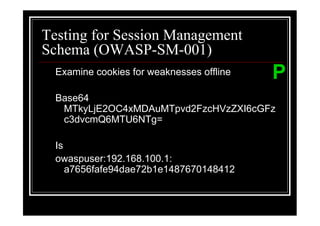
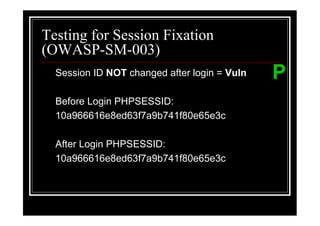
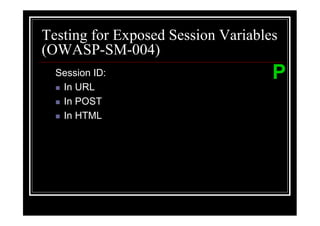
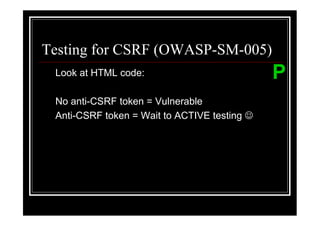
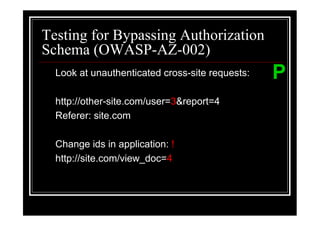
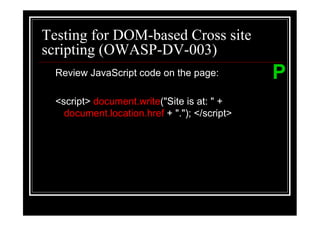
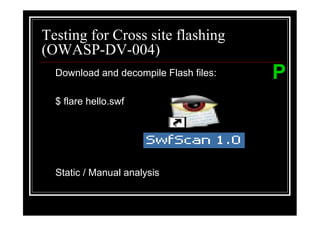
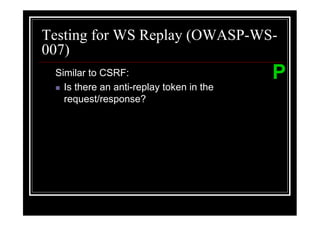
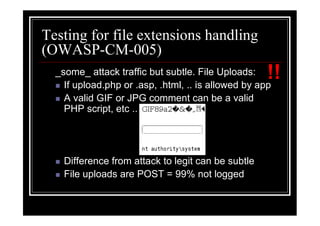
The document outlines various web application testing techniques that can be performed, many of which do not require permission, except in certain jurisdictions like Spain. It provides guidelines based on the OWASP testing guide, detailing methods for testing vulnerabilities, identifying application entry points, and analyzing the security of session management and user credentials. Additionally, the document emphasizes the importance of ethical considerations in testing practices.