Unpatched Security Flaws Openly Solicited by US Navy
•
0 likes•807 views
The US Navy is seeking information from qualified vendors to develop exploit products that integrate with commonly used cyber security frameworks. The Navy requires access to vulnerability intelligence, exploit reports, and operational exploit binaries affecting widely used commercial software. Vendors must be rated at CMMI Level 3 and provide a minimum of 10 unique exploit reports and binaries over a one year period. Responses are requested to provide company and technical capability information by June 18, 2015. This notice is to gather information only and is not a solicitation for proposals.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
Similar to Unpatched Security Flaws Openly Solicited by US Navy
Similar to Unpatched Security Flaws Openly Solicited by US Navy (20)
Agriculture Equipment Sector - Analysis and Commentary - AG Prices.pptx

Agriculture Equipment Sector - Analysis and Commentary - AG Prices.pptx
Driving customer retention using predictive analytics

Driving customer retention using predictive analytics
Global Automotive Sector - Analysis and Commentary - June 2022.pptx

Global Automotive Sector - Analysis and Commentary - June 2022.pptx
Debt Issues| Global Debt Crisis| Analysis and Commentary

Debt Issues| Global Debt Crisis| Analysis and Commentary
Questioning Data Quality and Troubleshooting Tracking Gaps (SMX Munich 2020)

Questioning Data Quality and Troubleshooting Tracking Gaps (SMX Munich 2020)
2019 Election| Employment | TFW - Temporary Foreign Workers | Canada| June 2019

2019 Election| Employment | TFW - Temporary Foreign Workers | Canada| June 2019
Employment and Labor Market - Canada - May 2022.pptx

Employment and Labor Market - Canada - May 2022.pptx
Geopolitical Risks - Pandemic - Canada and the World - WE June 4, 2022 .pptx

Geopolitical Risks - Pandemic - Canada and the World - WE June 4, 2022 .pptx
Public Sector - United States - How to Transform Government - June 2022.pptx

Public Sector - United States - How to Transform Government - June 2022.pptx
Agriculture and Farm Equipment Sector| February 2022

Agriculture and Farm Equipment Sector| February 2022
Canada| Small Business Survival| Analysis and Commentary

Canada| Small Business Survival| Analysis and Commentary
More from Waqas Amir
More from Waqas Amir (20)
Symantec Internet Security Threat Report Volume 2015

Symantec Internet Security Threat Report Volume 2015
Woman suing google for losing “thousands” due to google play store hack

Woman suing google for losing “thousands” due to google play store hack
Us in-flight-wi-fi-internet-could-be-hacked-warns-federal-watchdog-agency

Us in-flight-wi-fi-internet-could-be-hacked-warns-federal-watchdog-agency
Child Abuse Images Traded by Paedophiles for Bitcoin: Report

Child Abuse Images Traded by Paedophiles for Bitcoin: Report
Android App Used by Hackers in Sex Extortion Campaigns

Android App Used by Hackers in Sex Extortion Campaigns
Study reveals we are being tracked by our smartphones --- every 3 minutes

Study reveals we are being tracked by our smartphones --- every 3 minutes
Stingray Mobile Phone Surveillance Details to be unveiled.. Orders NY Court

Stingray Mobile Phone Surveillance Details to be unveiled.. Orders NY Court
FBI Admits Using Stingray Devices to Disrupt Phone Service.

FBI Admits Using Stingray Devices to Disrupt Phone Service.
DARPA Wants to Monitor The Arctic, offers $4 Million For An Unmanned Surveill...

DARPA Wants to Monitor The Arctic, offers $4 Million For An Unmanned Surveill...
Nsa hiding undetectable spyware in hard drives worldwide

Nsa hiding undetectable spyware in hard drives worldwide
BlackBerry, Boeing to Develop Self-Destruct Mission Impossible Style Phone.

BlackBerry, Boeing to Develop Self-Destruct Mission Impossible Style Phone.
Citizenfour producers-face-legal-challenges-over-edward-snowden-leaks

Citizenfour producers-face-legal-challenges-over-edward-snowden-leaks
Citizenfour producers-face-legal-challenges-over-edward-snowden-leaks

Citizenfour producers-face-legal-challenges-over-edward-snowden-leaks
Court ruling : Parents may be responsible for what their kinds post on facebook

Court ruling : Parents may be responsible for what their kinds post on facebook
Fbi’s internal guide list to internet slangs revealed

Fbi’s internal guide list to internet slangs revealed
Nsa's talking points for friends and family - rebutted

Nsa's talking points for friends and family - rebutted
Recently uploaded
celebrity 💋 Agra Escorts Just Dail 8250092165 service available anytime 24 hour
Booking Now open +91- 8005736733
Why you Choose Us- +91- 8005736733
HOT⇄ 8005736733
Mr ashu ji
Call Mr ashu Ji +91- 8005736733
𝐇𝐨𝐭𝐞𝐥 𝐑𝐨𝐨𝐦𝐬 𝐈𝐧𝐜𝐥𝐮𝐝𝐢𝐧𝐠 𝐑𝐚𝐭𝐞 𝐒𝐡𝐨𝐭𝐬/𝐇𝐨𝐮𝐫𝐲🆓 .█▬█⓿▀█▀ 𝐈𝐍𝐃𝐄𝐏𝐄𝐍𝐃𝐄𝐍𝐓 𝐆𝐈𝐑𝐋 𝐕𝐈𝐏 𝐄𝐒𝐂𝐎𝐑𝐓
Hello Guys ! High Profiles young Beauties and Good Looking standard Profiles Available , Enquire Now if you are interested in Hifi Service and want to get connect with someone who can understand your needs.
Service offers you the most beautiful High Profile sexy independent female Escorts in genuine ✔✔✔ To enjoy with hot and sexy girls ✔✔✔$V15
★providing:-
• Models
• vip Models
• Russian Models
• Foreigner Models
• TV Actress and Celebrities
• Receptionist
• Air Hostess
• Call Center Working Girls/Women
• Hi-Tech Co. Girls/Women
• Housewife
celebrity 💋 Agra Escorts Just Dail 8250092165 service available anytime 24 hour

celebrity 💋 Agra Escorts Just Dail 8250092165 service available anytime 24 hourCall Girls in Nagpur High Profile
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandigarh Call Girls 🍌
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandig...

Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandig...Chandigarh Call girls 9053900678 Call girls in Chandigarh
Recently uploaded (20)
VIP Call Girls Bhavnagar 7001035870 Whatsapp Number, 24/07 Booking

VIP Call Girls Bhavnagar 7001035870 Whatsapp Number, 24/07 Booking
2024: The FAR, Federal Acquisition Regulations, Part 31

2024: The FAR, Federal Acquisition Regulations, Part 31
Call Girls Chakan Call Me 7737669865 Budget Friendly No Advance Booking

Call Girls Chakan Call Me 7737669865 Budget Friendly No Advance Booking
An Atoll Futures Research Institute? Presentation for CANCC

An Atoll Futures Research Institute? Presentation for CANCC
celebrity 💋 Agra Escorts Just Dail 8250092165 service available anytime 24 hour

celebrity 💋 Agra Escorts Just Dail 8250092165 service available anytime 24 hour
VIP Call Girls Agra 7001035870 Whatsapp Number, 24/07 Booking

VIP Call Girls Agra 7001035870 Whatsapp Number, 24/07 Booking
Chakan ( Call Girls ) Pune 6297143586 Hot Model With Sexy Bhabi Ready For S...

Chakan ( Call Girls ) Pune 6297143586 Hot Model With Sexy Bhabi Ready For S...
VIP Model Call Girls Kiwale ( Pune ) Call ON 8005736733 Starting From 5K to 2...

VIP Model Call Girls Kiwale ( Pune ) Call ON 8005736733 Starting From 5K to 2...
SMART BANGLADESH I PPTX I SLIDE IShovan Prita Paul.pptx

SMART BANGLADESH I PPTX I SLIDE IShovan Prita Paul.pptx
Postal Ballots-For home voting step by step process 2024.pptx

Postal Ballots-For home voting step by step process 2024.pptx
Nanded City ? Russian Call Girls Pune - 450+ Call Girl Cash Payment 800573673...

Nanded City ? Russian Call Girls Pune - 450+ Call Girl Cash Payment 800573673...
Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandig...

Russian🍌Dazzling Hottie Get☎️ 9053900678 ☎️call girl In Chandigarh By Chandig...
WORLD DEVELOPMENT REPORT 2024 - Economic Growth in Middle-Income Countries.

WORLD DEVELOPMENT REPORT 2024 - Economic Growth in Middle-Income Countries.
Just Call Vip call girls Wardha Escorts ☎️8617370543 Starting From 5K to 25K ...

Just Call Vip call girls Wardha Escorts ☎️8617370543 Starting From 5K to 25K ...
Unpatched Security Flaws Openly Solicited by US Navy
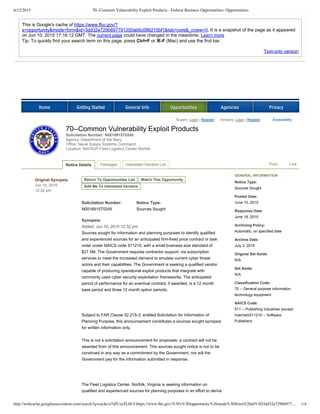
- 1. 6/12/2015 70--Common Vulnerability Exploit Products - Federal Business Opportunities: Opportunities http://webcache.googleusercontent.com/search?q=cache:o7dfUzaTL6UJ:https://www.fbo.gov/%3Fs%3Dopportunity%26mode%3Dform%26id%3D3dd32e729b6977… 1/4 Textonly version This is Google's cache of https://www.fbo.gov/? s=opportunity&mode=form&id=3dd32e729b697791350ab6c086210bf1&tab=core&_cview=0. It is a snapshot of the page as it appeared on Jun 10, 2015 17:16:12 GMT. The current page could have changed in the meantime. Learn more Tip: To quickly find your search term on this page, press Ctrl+F or ⌘F (Mac) and use the find bar. Solicitation Number: N0018915T0245 Notice Type: Sources Sought Buyers: Login | Register Vendors: Login | Register Accessibility Original Synopsis Jun 10, 2015 12:32 pm Return To Opportunities List Watch This Opportunity Add Me To Interested Vendors Synopsis: Added: Jun 10, 2015 12:32 pm Sources sought for information and planning purposes to identify qualified and experienced sources for an anticipated firmfixed price contract or task order under NAICS code 511210, with a small business size standard of $27.5M. The Government requires contractor support, via subscription services to meet the increased demand to emulate current cyber threat actors and their capabilities. The Government is seeking a qualified vendor capable of producing operational exploit products that integrate with commonly used cyber security exploitation frameworks. The anticipated period of performance for an eventual contract, if awarded, is a 12 month base period and three 12 month option periods. Subject to FAR Clause 52.2153, entitled Solicitation for Information of Planning Purpose, this announcement constitutes a sources sought synopsis for written information only. This is not a solicitation announcement for proposals: a contract will not be awarded from of this announcement. This sources sought notice is not to be construed in any way as a commitment by the Government, nor will the Government pay for the information submitted in response. The Fleet Logistics Center, Norfolk, Virginia is seeking information on qualified and experienced sources for planning purposes in an effort to derive GENERAL INFORMATION Notice Type: Sources Sought Posted Date: June 10, 2015 Response Date: June 18, 2015 Archiving Policy: Automatic, on specified date Archive Date: July 3, 2015 Original Set Aside: N/A Set Aside: N/A Classification Code: 70 General purpose information technology equipment NAICS Code: 511 Publishing Industries (except Internet)/511210 Software Publishers 70Common Vulnerability Exploit Products Solicitation Number: N0018915T0245 Agency: Department of the Navy Office: Naval Supply Systems Command Location: NAVSUP Fleet Logistics Center Norfolk Notice Details Packages Interested Vendors List Print Link
- 2. 6/12/2015 70--Common Vulnerability Exploit Products - Federal Business Opportunities: Opportunities http://webcache.googleusercontent.com/search?q=cache:o7dfUzaTL6UJ:https://www.fbo.gov/%3Fs%3Dopportunity%26mode%3Dform%26id%3D3dd32e729b6977… 2/4 a contract vehicle that will provide qualified personnel to support the Government’s mission in the following functional areas: This is a requirement to have access to vulnerability intelligence, exploit reports and operational exploit binaries affecting widely used and relied upon commercial software. These include but are not limited to Microsoft, Adobe, JAVA, EMC, Novell, IBM, Android, Apple, CISCO IOS, Linksys WRT, and Linux, and all others. The vendor must be rated to Capability Maturity Model Integration (CMMI) Level 3 or greater. The vendor shall provide the government with a proposed list of available vulnerabilities, 0day or Nday (no older than 6 months old). This list should be updated quarterly and include intelligence and exploits affecting widely used software. The government will select from the supplied list and direct development of exploit binaries. Completed products will be delivered to the government via secured electronic means. Over a one year period, a minimum of 10 unique reports with corresponding exploit binaries will be provided periodically (no less than 2 per quarter) and designed to be operationally deployable upon delivery. Based on the Government’s direction, the vendor will develop exploits for future released Common Vulnerabilities and Exposures (CVE’s). Binaries must support configurable, custom, and/or government owned/provided payloads and suppress known network signatures from proof of concept code that may be found in the wild. Once a product is transferred from the vendor to the government, the government maintains a perpetual license to use, modify or share at the buyer’s discretion. The vendor shall accept vulnerability data to include patch code, proof of concept code, or analytic white papers from the government to assist with product development. Products developed under these conditions will not be available to any other customer and will remain exclusively licensed to the
- 3. 6/12/2015 70--Common Vulnerability Exploit Products - Federal Business Opportunities: Opportunities http://webcache.googleusercontent.com/search?q=cache:o7dfUzaTL6UJ:https://www.fbo.gov/%3Fs%3Dopportunity%26mode%3Dform%26id%3D3dd32e729b6977… 3/4 government. All delivered products will be accompanied by documentation to include exploit description, concept of operation and operator instructions. Technical support shall be provided by the vendor to the government for purposes of integrating, troubleshooting, bug fixes, feature enhancements, and OS and third party software compatibility testing. These services must be available Monday through Friday during normal working hours (0730 EST through 1630 EST). Reponses to this Sources Sought request shall include the following information in this format: 1. Company name, address, point of contact name, phone number, fax number and email address. 2. Contractor and Government Entity (CAGE) Code. 3. If the items can be solicited from a GSA schedule or existing Multiple Award Contract, provide the contract number. 4. Size of business Large Business, Small Business, Small Disadvantaged, 8(a), Hubzone, Womanowned and/or Veteranowned. 5. Capability statement displaying the contractor’s ability to successfully provide the subscription services detailed above. If past performance information is provided, please include only relevant past performance on the same/similar work within the last 3 years. Please also include in past performance information the contract numbers, dollar value, and period of performance for each contract referenced in the response to this sources sought. 6. Comments, questions and recommendations regarding contractor tasking detailed in the PWS are encouraged. 7. Include any other supporting documentation deemed necessary. Documentation of technical expertise must be presented in sufficient detail for the Government to determine that your company possesses the necessary functional area expertise and experience to compete for this acquisition. Standard company brochures will not be reviewed. Submissions are not to exceed eight (8) typewritten pages, singlespaced, in no less than 10 font size.
- 4. 6/12/2015 70--Common Vulnerability Exploit Products - Federal Business Opportunities: Opportunities http://webcache.googleusercontent.com/search?q=cache:o7dfUzaTL6UJ:https://www.fbo.gov/%3Fs%3Dopportunity%26mode%3Dform%26id%3D3dd32e729b6977… 4/4 For Help: Federal Service Desk Accessibility Responses should be emailed to Mr. David Biggs at david.a.biggs@navy.mil by 4:00 PM ET on 18 June, 2015. Again, this is not a request for a proposal. Respondents will not be notified of the results. Please note the information within this presolicitation synopsis will be updated and/or may change prior to an official synopsis/solicitation, if any, is issued. Contracting Office Address: N00189 NAVSUP Fleet Logistics Center Norfolk 1968 Gilbert Street,Suite 600 NORFOLK, VA Point of Contact(s): Mr. David Biggs (757)4431410 David Biggs Return To Opportunities List Watch This Opportunity Add Me To Interested Vendors
