Cyber resilient infrastructure infographic
•
7 likes•4,676 views
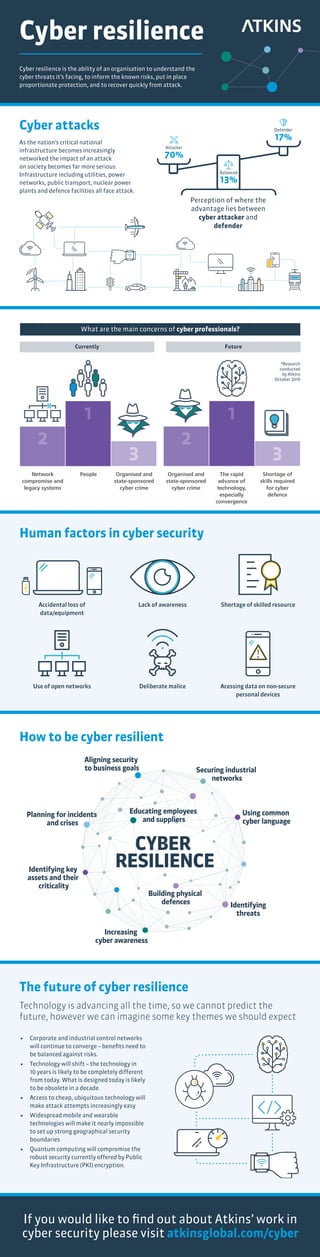
Cyber resilience is the ability of an organization to understand cyber threats, manage known risks, implement proportionate protections, and recover quickly from attacks. As critical infrastructure becomes more networked, attacks could seriously impact society. Infrastructure like utilities and transportation systems face threats from organized crime and state-sponsored attacks. The future of cybersecurity is uncertain as technology rapidly advances, but issues like converged networks, new technologies, easier attacks, mobile devices, and quantum computing will impact security.
Report
Share
Report
Share
Download to read offline
Recommended
Netpluz Cyber Intelligence Managed Security Pack for Small to Mid Business
A Cyber Protection Service That provides reactive mitigation and alerting before an event becomes an incident
Are you Cyber ready? Introducing Netpluz managed cyber security - cyber intel...

Are you Cyber ready? Introducing Netpluz managed cyber security - cyber intel...Netpluz Asia Pte Ltd
Recommended
Netpluz Cyber Intelligence Managed Security Pack for Small to Mid Business
A Cyber Protection Service That provides reactive mitigation and alerting before an event becomes an incident
Are you Cyber ready? Introducing Netpluz managed cyber security - cyber intel...

Are you Cyber ready? Introducing Netpluz managed cyber security - cyber intel...Netpluz Asia Pte Ltd
Vytautas Braziunas, Phoenix Contact UAB, Managing Director, LT
Rīga, 2019.gada 15.februāra
Forums "DIG-IN"
Video: http://straume.lmt.lv/lv/konferences/konferences/vytautas-braziunas/1037753Cyber Security in the Manufacturing Industry: New challenges in the informati...

Cyber Security in the Manufacturing Industry: New challenges in the informati...Ekonomikas ministrija
A talk about Critical Information Infrastructure (CII).National Critical Information Infrastructure Protection Centre (NCIIPC): Role...

National Critical Information Infrastructure Protection Centre (NCIIPC): Role...Cybersecurity Education and Research Centre
More Related Content
What's hot
Vytautas Braziunas, Phoenix Contact UAB, Managing Director, LT
Rīga, 2019.gada 15.februāra
Forums "DIG-IN"
Video: http://straume.lmt.lv/lv/konferences/konferences/vytautas-braziunas/1037753Cyber Security in the Manufacturing Industry: New challenges in the informati...

Cyber Security in the Manufacturing Industry: New challenges in the informati...Ekonomikas ministrija
A talk about Critical Information Infrastructure (CII).National Critical Information Infrastructure Protection Centre (NCIIPC): Role...

National Critical Information Infrastructure Protection Centre (NCIIPC): Role...Cybersecurity Education and Research Centre
What's hot (20)
I4ADA 2019 - Presentation Accountability & cyber security & cyber peace

I4ADA 2019 - Presentation Accountability & cyber security & cyber peace
Cyber Security in the Manufacturing Industry: New challenges in the informati...

Cyber Security in the Manufacturing Industry: New challenges in the informati...
Cybersecurity | D-fend: Counter drone solution for urban environments

Cybersecurity | D-fend: Counter drone solution for urban environments
What are the top Cybersecurity priorities for state and local governments in ...

What are the top Cybersecurity priorities for state and local governments in ...
Government and Enterprise Collaboration in Cybersecurity

Government and Enterprise Collaboration in Cybersecurity
Diversity in Cybersecurity Education - 2016 ICT keynote - M.Rosenquist

Diversity in Cybersecurity Education - 2016 ICT keynote - M.Rosenquist
Synopsis & toc sectoral capsule on cyber security market in india

Synopsis & toc sectoral capsule on cyber security market in india
Securing the Digital Economy: Reinventing the Internet 

Securing the Digital Economy: Reinventing the Internet
Extending CyberSecurity Beyond The Office Perimeter

Extending CyberSecurity Beyond The Office Perimeter
Deep Learning for Cybersecurity Innovation Insights from Patents

Deep Learning for Cybersecurity Innovation Insights from Patents
National Critical Information Infrastructure Protection Centre (NCIIPC): Role...

National Critical Information Infrastructure Protection Centre (NCIIPC): Role...
Singapore Cybersecurity Strategy and Legislation (2018)

Singapore Cybersecurity Strategy and Legislation (2018)
Viewers also liked
How you can increase your customer retention with better Contact Center Solution that helps to deliver better customer satisfaction.Increase retention by 35% and avoid US$2.5 million penalties with a single so...

Increase retention by 35% and avoid US$2.5 million penalties with a single so...DRISHTI-SOFT SOLUTIONS PVT. LTD.
Viewers also liked (15)
8 ways to protect your digital footprint infographic

8 ways to protect your digital footprint infographic
The advent of digital engineering - a year in review

The advent of digital engineering - a year in review
Implementación de un sistema 3D de información de servicios en el subsuelo en...

Implementación de un sistema 3D de información de servicios en el subsuelo en...
Dealing with Information Security, Risk Management & Cyber Resilience

Dealing with Information Security, Risk Management & Cyber Resilience
How to create better wellbeing outcomes for students through design

How to create better wellbeing outcomes for students through design
Increase retention by 35% and avoid US$2.5 million penalties with a single so...

Increase retention by 35% and avoid US$2.5 million penalties with a single so...
Similar to Cyber resilient infrastructure infographic
Similar to Cyber resilient infrastructure infographic (20)
Powering up the shocking truth about cyber security in the energy industry - ...

Powering up the shocking truth about cyber security in the energy industry - ...
Varsha Sewlal- Cyber Attacks on Critical Critical Infrastructure

Varsha Sewlal- Cyber Attacks on Critical Critical Infrastructure
CYBER SECURITY TRANDS FOR FUTURE SMART GRID SYSTEMS

CYBER SECURITY TRANDS FOR FUTURE SMART GRID SYSTEMS
Capstone Team Report -The Vicious Circle of Smart Grid Security

Capstone Team Report -The Vicious Circle of Smart Grid Security
Need for Improved Critical Industrial Infrastructure Protection

Need for Improved Critical Industrial Infrastructure Protection
Board-toolkit-Introduction-to-cyber-security-for-board-members-briefing-pack....

Board-toolkit-Introduction-to-cyber-security-for-board-members-briefing-pack....
More from Atkins
More from Atkins (20)
Green Sky Thinking: bringing forest schools to the inner city

Green Sky Thinking: bringing forest schools to the inner city
A glance at Atkins' landscape architecture projects

A glance at Atkins' landscape architecture projects
Atkins: Preliminary results for the year ended 31 March 2016

Atkins: Preliminary results for the year ended 31 March 2016
Analyst presentation: Crossrail and our international tunnelling expertise - ...

Analyst presentation: Crossrail and our international tunnelling expertise - ...
Recently uploaded
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Recently uploaded (20)
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Cyber resilient infrastructure infographic
- 1. Cyber resilience Cyber resilience is the ability of an organisation to understand the cyber threats it’s facing, to inform the known risks, put in place proportionate protection, and to recover quickly from attack. Cyber attacks As the nation’s critical national infrastructure becomes increasingly networked the impact of an attack on society becomes far more serious. Infrastructure including utilities, power networks, public transport, nuclear power plants and defence facilities all face attack. Network compromise and legacy systems People Organised and state-sponsored cyber crime Organised and state-sponsored cyber crime The rapid advance of technology, especially convergence Shortage of skills required for cyber defence Currently Future 2 2 1 1 3 3 What are the main concerns of cyber professionals? *Research conducted by Atkins October 2016 The future of cyber resilience Technology is advancing all the time, so we cannot predict the future, however we can imagine some key themes we should expect • Corporate and industrial control networks will continue to converge – benefits need to be balanced against risks. • Technology will shift – the technology in 10 years is likely to be completely different from today. What is designed today is likely to be obsolete in a decade. • Access to cheap, ubiquitous technology will make attack attempts increasingly easy • Widespread mobile and wearable technologies will make it nearly impossible to set up strong geographical security boundaries • Quantum computing will compromise the robust security currently offered by Public Key Infrastructure (PKI) encryption. Aligning security to business goals Using common cyber language Building physical defences Identifying key assets and their criticality Planning for incidents and crises Increasing cyber awareness Identifying threats Securing industrial networks Educating employees and suppliers If you would like to find out about Atkins’ work in cyber security please visit atkinsglobal.com/cyber Human factors in cyber security Accidental loss of data/equipment Use of open networks Lack of awareness Deliberate malice Shortage of skilled resource Acessing data on non-secure personal devices Perception of where the advantage lies between cyber attacker and defender Attacker 70% Balanced 13% Defender 17% How to be cyber resilient
