digital forensic.docx
•Download as DOCX, PDF•
0 likes•10 views
This document outlines a course on digital forensics. It includes the course code, title, credits, and outcomes. The course has 5 units that cover incident response, file system data recovery, network and email forensics, system forensics, and image/video forensics. The units explore topics like data analysis methodology, hacking investigation tools, and detecting fraud in images/videos. Upon completing the course, students should be able to recognize attacks, design incident response, recover evidence, understand network attacks and tools, and analyze encrypted/steganographic images and fraud. The course references two textbooks and one additional reference book.
Report
Share
Report
Share
Recommended
Recommended
God is a creative God Gen 1:1. All that He created was “good”, could also be translated “beautiful”. God created man in His own image Gen 1:27. Maths helps us discover the beauty that God has created in His world and, in turn, create beautiful designs to serve and enrich the lives of others.
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...christianmathematics
More Related Content
Similar to digital forensic.docx
Similar to digital forensic.docx (20)
P.D.F System Forensics, Investigation, and Response ^Full.Pages By Chuck Easttom

P.D.F System Forensics, Investigation, and Response ^Full.Pages By Chuck Easttom
Computer forensics intro(Pendahuluan Komputer Forensik).ppt

Computer forensics intro(Pendahuluan Komputer Forensik).ppt
Recently uploaded
God is a creative God Gen 1:1. All that He created was “good”, could also be translated “beautiful”. God created man in His own image Gen 1:27. Maths helps us discover the beauty that God has created in His world and, in turn, create beautiful designs to serve and enrich the lives of others.
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...christianmathematics
Mehran University Newsletter is a Quarterly Publication from Public Relations OfficeMehran University Newsletter Vol-X, Issue-I, 2024

Mehran University Newsletter Vol-X, Issue-I, 2024Mehran University of Engineering & Technology, Jamshoro
Recently uploaded (20)
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...
UGC NET Paper 1 Mathematical Reasoning & Aptitude.pdf

UGC NET Paper 1 Mathematical Reasoning & Aptitude.pdf
Vishram Singh - Textbook of Anatomy Upper Limb and Thorax.. Volume 1 (1).pdf

Vishram Singh - Textbook of Anatomy Upper Limb and Thorax.. Volume 1 (1).pdf
Python Notes for mca i year students osmania university.docx

Python Notes for mca i year students osmania university.docx
This PowerPoint helps students to consider the concept of infinity.

This PowerPoint helps students to consider the concept of infinity.
Kodo Millet PPT made by Ghanshyam bairwa college of Agriculture kumher bhara...

Kodo Millet PPT made by Ghanshyam bairwa college of Agriculture kumher bhara...
Basic Civil Engineering first year Notes- Chapter 4 Building.pptx

Basic Civil Engineering first year Notes- Chapter 4 Building.pptx
Fostering Friendships - Enhancing Social Bonds in the Classroom

Fostering Friendships - Enhancing Social Bonds in the Classroom
digital forensic.docx
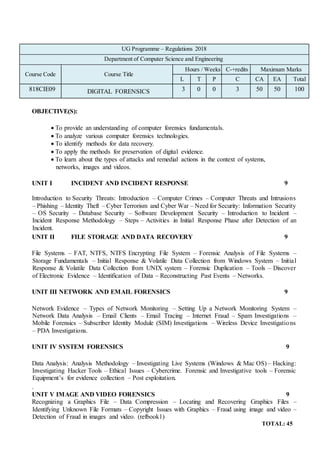
- 1. UG Programme – Regulations 2018 Department of Computer Science and Engineering Course Code Course Title Hours / Weeks C-+redits Maximum Marks L T P C CA EA Total 818CIE09 DIGITAL FORENSICS 3 0 0 3 50 50 100 OBJECTIVE(S): To provide an understanding of computer forensics fundamentals. To analyze various computer forensics technologies. To identify methods for data recovery. To apply the methods for preservation of digital evidence. To learn about the types of attacks and remedial actions in the context of systems, networks, images and videos. UNIT I INCIDENT AND INCIDENT RESPONSE 9 Introduction to Security Threats: Introduction – Computer Crimes – Computer Threats and Intrusions – Phishing – Identity Theft – Cyber Terrorism and Cyber War – Need for Security: Information Security – OS Security – Database Security – Software Development Security – Introduction to Incident – Incident Response Methodology – Steps – Activities in Initial Response Phase after Detection of an Incident. UNIT II FILE STORAGE AND DATA RECOVERY 9 File Systems – FAT, NTFS, NTFS Encrypting File System – Forensic Analysis of File Systems – Storage Fundamentals – Initial Response & Volatile Data Collection from Windows System – Initial Response & Volatile Data Collection from UNIX system – Forensic Duplication – Tools – Discover of Electronic Evidence – Identification of Data – Reconstructing Past Events – Networks. UNIT III NETWORK AND EMAIL FORENSICS 9 Network Evidence – Types of Network Monitoring – Setting Up a Network Monitoring System – Network Data Analysis – Email Clients – Email Tracing – Internet Fraud – Spam Investigations – Mobile Forensics – Subscriber Identity Module (SIM) Investigations – Wireless Device Investigations – PDA Investigations. UNIT IV SYSTEM FORENSICS 9 Data Analysis: Analysis Methodology – Investigating Live Systems (Windows & Mac OS) – Hacking: Investigating Hacker Tools – Ethical Issues – Cybercrime. Forensic and Investigative tools – Forensic Equipment’s for evidence collection – Post exploitation. . UNIT V IMAGE AND VIDEO FORENSICS 9 Recognizing a Graphics File – Data Compression – Locating and Recovering Graphics Files – Identifying Unknown File Formats – Copyright Issues with Graphics – Fraud using image and video – Detection of Fraud in images and video. (refbook1) TOTAL: 45
- 2. COURSE OUTCOMES: At the end of the course student should be able to CO1: Recognize attacks on systems. CO2: Design a counter attack incident response and incident response methodology. CO3: Illustrate the methods for data recovery, evidence collection and data seizure. CO4: Understand network and email attacks and forensic investigation with tools. CO5: Analyze various image encryption/decryption, steganography and fraud in image TEXT BOOKS: 1. Kevin Mandia, Jason T. Luttgens, Matthew Pepe, “Incident Response and Computer Forensics”, Tata McGraw-Hill, 2014 2. Bill Nelson, Amelia Philips, Christopher Steuart, “Guide to Computer Forensics and Investigations”, Cengage Learning, 2018. REFERENCE BOOKS: 1. John R. Vacca, “Computer Forensics”, Firewall Media, 2009. 2. .Rafay Baloch, “Ethical Hacking and Penetration Testing Guide”, Auerbach Publications, First Edition, 2014.