Caller Anonymity Frustrates Subscribers
•
0 likes•48 views
Caller identification remains a key issue in the wireless industry as robocallers and spammers increasingly target subscribers by hiding behind a veil of anonymity, leading to the industry and FCC taking action and protecting mobile users by establishing a Robocall Strike Force. Cequint, a Transaction Network Services company, conducted a survey* among adult Android and iOS mobile phone users in the US to document how significant this issue is and identify areas of focus for the Strike Force.
Report
Share
Report
Share
Download to read offline
Recommended
Celebrities' emails stolen in cyber attack on law firm to the stars

Celebrities' emails stolen in cyber attack on law firm to the starsLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
Recommended
Celebrities' emails stolen in cyber attack on law firm to the stars

Celebrities' emails stolen in cyber attack on law firm to the starsLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
More Related Content
Viewers also liked
Viewers also liked (12)
TNS Infographic - Data Security Still Not a Top Priority for Some - August 2016

TNS Infographic - Data Security Still Not a Top Priority for Some - August 2016
TNS Asia Pacific POP Network - Overcome Cost and Complexity in Financial Markets

TNS Asia Pacific POP Network - Overcome Cost and Complexity in Financial Markets
Data Breaches Still Major Threat - Infographic from TNS August 2016

Data Breaches Still Major Threat - Infographic from TNS August 2016
Similar to Caller Anonymity Frustrates Subscribers
Similar to Caller Anonymity Frustrates Subscribers (20)
Generation Now: Diverse. Connected. On-the-go. (Keynote at Social Media Atlan...

Generation Now: Diverse. Connected. On-the-go. (Keynote at Social Media Atlan...
Security issues vs user awareness in mobile devices a survey

Security issues vs user awareness in mobile devices a survey
Ericsson ConsumerLab: Wi-Fi calling finds its voice

Ericsson ConsumerLab: Wi-Fi calling finds its voice
CONSUMER PERCEPTIONS ON SECURITY: DO THEY STILL CARE?

CONSUMER PERCEPTIONS ON SECURITY: DO THEY STILL CARE?
Cellcrypt - An Introduction to Secure Mobile Communications

Cellcrypt - An Introduction to Secure Mobile Communications
Truecaller_Insights_-_2022_U.S._Spam__Scam_Report.pdf

Truecaller_Insights_-_2022_U.S._Spam__Scam_Report.pdf
Mobile Cybercrime - Don’t Leave Your Customers Vulnerable

Mobile Cybercrime - Don’t Leave Your Customers Vulnerable
Mobile cloning modified with images and bettermented

Mobile cloning modified with images and bettermented
Recently uploaded
Recently uploaded (20)
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget

Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
How to Remove Document Management Hurdles with X-Docs?

How to Remove Document Management Hurdles with X-Docs?
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
Caller Anonymity Frustrates Subscribers
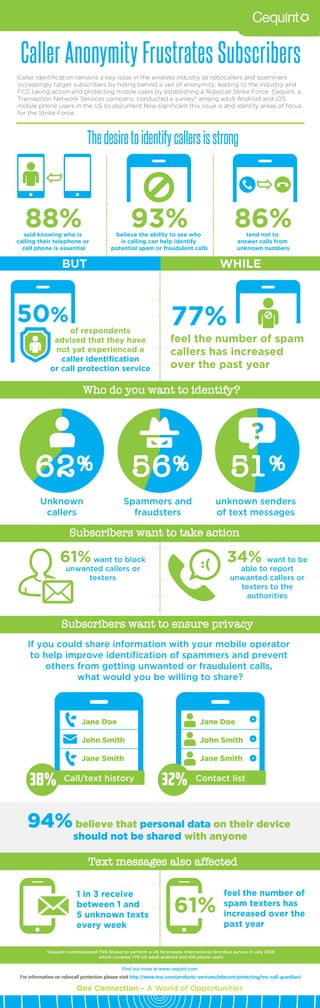
- 1. Caller identification remains a key issue in the wireless industry as robocallers and spammers increasingly target subscribers by hiding behind a veil of anonymity, leading to the industry and FCC taking action and protecting mobile users by establishing a Robocall Strike Force. Cequint, a Transaction Network Services company, conducted a survey* among adult Android and iOS mobile phone users in the US to document how significant this issue is and identify areas of focus for the Strike Force. Caller Anonymity Frustrates Subscribers Thedesiretoidentifycallersisstrong Who do you want to identify? Text messages also affected If you could share information with your mobile operator to help improve identification of spammers and prevent others from getting unwanted or fraudulent calls, what would you be willing to share? Subscribers want to take action Subscribers want to ensure privacy Unknown callers Spammers and fraudsters unknown senders of text messages 34% want to be able to report unwanted callers or texters to the authorities 61%want to block unwanted callers or texters *Cequint commissioned TNS Global to perform a US Ncompass International Omnibus survey in July 2016 which covered 778 US adult android and iOS phone users said knowing who is calling their telephone or cell phone is essential believe the ability to see who is calling can help identify potential spam or fraudulent calls tend not to answer calls from unknown numbers of respondents advised that they have not yet experienced a caller identification or call protection service feel the number of spam callers has increased over the past year 93%88% 50% 86% 77% 51%62% 56% 1 in 3 receive between 1 and 5 unknown texts every week feel the number of spam texters has increased over the past year 61% Jane Doe John Smith Jane Smith Jane Doe John Smith Jane Smith Call/text history Contact list 38% 32% 94%believe that personal data on their device should not be shared with anyone BUT WHILE For information on robocall protection please visit http://www.tnsi.com/products-services/telecom/protecting/tns-call-guardian/