This document provides an overview and agenda for a presentation on object storage capabilities in IBM Spectrum Scale. The summary includes:
1. The agenda covers object protocol, administration including installation methods, object authentication, storage policies, unified file and object, multiregion, S3, creating containers/buckets and objects, and problem determination.
2. Administration of object protocol can be done through the Spectrum Scale installation toolkit or CLI commands. This includes enabling features like S3 and multiregion.
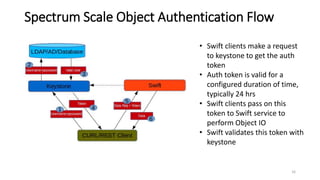
3. Authentication for object access can be configured with options like Active Directory, LDAP, local authentication, or an external Keystone service.







![spectrumscale config object
• To setup object protocol, run the installer
command-
spectrumscale config object [-h] [-l]
[-f FILESYSTEM] [-m MOUNTPOINT]
[-e ENDPOINT] [-o OBJECTBASE]
[-i INODEALLOCATION] [-t ADMINTOKEN]
[-au ADMINUSER] [-ap [ADMINPASSWORD]]
[-su SWIFTUSER] [-sp [SWIFTPASSWORD]]
[-dp [DATABASEPASSWORD]] [-s3 {on,off}]
[-mr MULTIREGION] [-rn REGIONNUMBER]
• This command must be run before running
“spectrumscale deploy”. After deploy,
object gets configured with these settings.
• This command can only be used during initial
deployment. It cannot be used on a cluster
with object deployed to configure or change
object protocol settings.
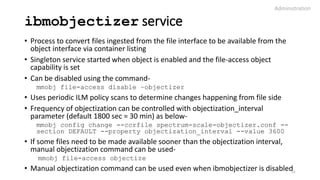
Administration
9
Sample clusterdefinition.txt
[object]
enable_s3 = True
filesystem = fs1
object_base = object_fileset
multiregion_file = /root/region
[protocols]
object = True
smb = False
nfs = False](https://image.slidesharecdn.com/spectrumscaleobject-deepdivetraining-171110094204/85/IBM-Spectrum-scale-object-deep-dive-training-9-320.jpg)
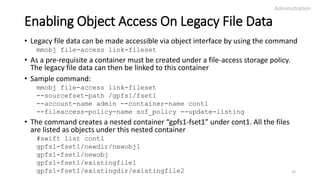
![mmobj swift base
• To setup object protocol using CLI after the initial cluster is setup, use
the command
mmobj swift base -g GPFSMountPoint --cluster-hostname CESHostname
[-o ObjFileset] [-i MaxNumInodes] [--ces-group CESGroup]
{{--local-keystone [--db-password Password] [--admin-token Token]}|
{--remote-keystone-url URL [--configure-remote-keystone]}}
--admin-password AdminPassword [--admin-user AdminUser]
[--swift-user SwiftUser] [--swift-password SwiftPassword]
[--enable-file-access] [--enable-s3] [--enable-multi-region]
[--region-number RegionNumber]
[--join-region-file RegionFile]
• This command can only be used for object deployment from scratch. It
cannot be used on a cluster with object deployed to configure or change
object protocol settings.
Administration
10](https://image.slidesharecdn.com/spectrumscaleobject-deepdivetraining-171110094204/85/IBM-Spectrum-scale-object-deep-dive-training-10-320.jpg)




![Install Toolkit Method (spectrumscale auth object)
• To setup object authentication, run the installer
command-
spectrumscale auth object [-h] [--
https] [--pki]
{local,external,ldap,ad}
• This will automatically open a template file for
you to fill with the required auth settings. TLS
and SSL related settings can also be done here.
Save the file and close it.
• If this install toolkit auth command has been
run, authentication will automatically be
enabled by the installer.
• This command must be run before running
“spectrumscale deploy”. After deploy,
object gets configured with these
authentication settings.
• This command can only be used during initial
deployment. It cannot be used on a cluster with
object deployed to configure or change object
auth.
• By default object is configured with local auth
Administration
18
Sample AD auth configuration file
[object]
remote_keystone = False
[object_auth]
enable_object_auth = True
backend_server = ad
# mandatory settings for object
authentication:
# Specifies the host name or IP address of
the authentication server.
servers =
# Specifies the base DN of the authentication
server.
base_dn =
# Specifies the DN for user search base.
user_dn =
# Specifies the user which will be assigned
the administrator role
# in Keystone.
admin_user =
# Specifies the AD user which will be used as
the swift service user.
# This user's details will be updated in
proxy-server.conf.
swift_user =
# Specifies the password of the swift_user.
# Leave as [prompt] to be prompted for the
password in
# a secure manner.
swift_password = [prompt]
Sample external keystone
auth configuration file
[object_auth]
# This installer will not
configure your external
keystone server
enable_object_auth = False
backend_server = external
[object]
remote_keystone = True
# Set to True to create swift
service, user and endpoint in
remote keystone
configure_remote_keystone =
False
# Supply the full URL for
your external keystone server
keystone_url =
http://extserver.com](https://image.slidesharecdn.com/spectrumscaleobject-deepdivetraining-171110094204/85/IBM-Spectrum-scale-object-deep-dive-training-18-320.jpg)




![Storage Policy Creation
• To create a storage policy run below command
mmobj policy create PolicyName
[-f FilesetName] [--file-system FilesystemName] [-i
MaxNumInodes]
{[--enable-compression --compression-schedule
"MM:HH:dd:ww"]}
{[--enable-encryption --encryption-keyfile
EncryptionKeyFileName [--force-rule-append]]}
[--enable-file-access]
• If FilesetName is not provided then a fileset with
name “Obj_PolicyName” is created
• Existing fileset can be used in –f option provided
it is not linked to any other storage policy
• If FilesystemName is not provided then the
fileset is created under default object filesystem
• Compression and encryption policies make use
of filesystem level compression and encryption
features
Administration
24
Examples:
File-access policy
mmobj policy create sof-policy --
enable-file-access
Compression policy
mmobj policy create CompressionTest --
enable-compression --compression-
schedule "50:23:15,30:0“
In the above example, the compression job has been
scheduled to run at 23.50 on every 15th and 30th of the
month and on all Sundays
Encryption policy
mmobj policy create encryptionPolicy --
enable-encryption --encryption-keyfile
/var/tmp/keyfile -–force-rule-append
In the above example the new encryption rule is added
to already established encryption policy, if any](https://image.slidesharecdn.com/spectrumscaleobject-deepdivetraining-171110094204/85/IBM-Spectrum-scale-object-deep-dive-training-24-320.jpg)