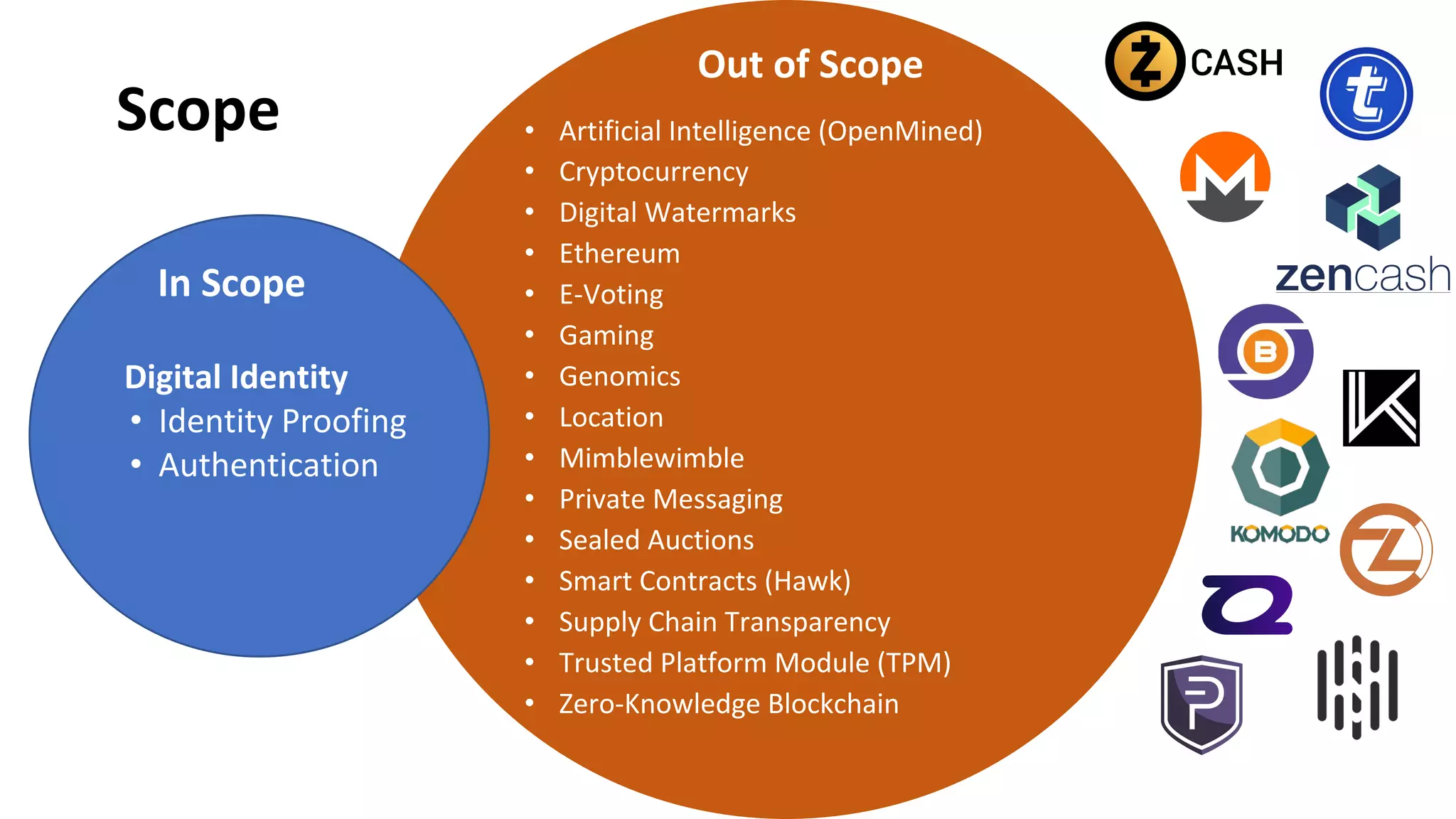
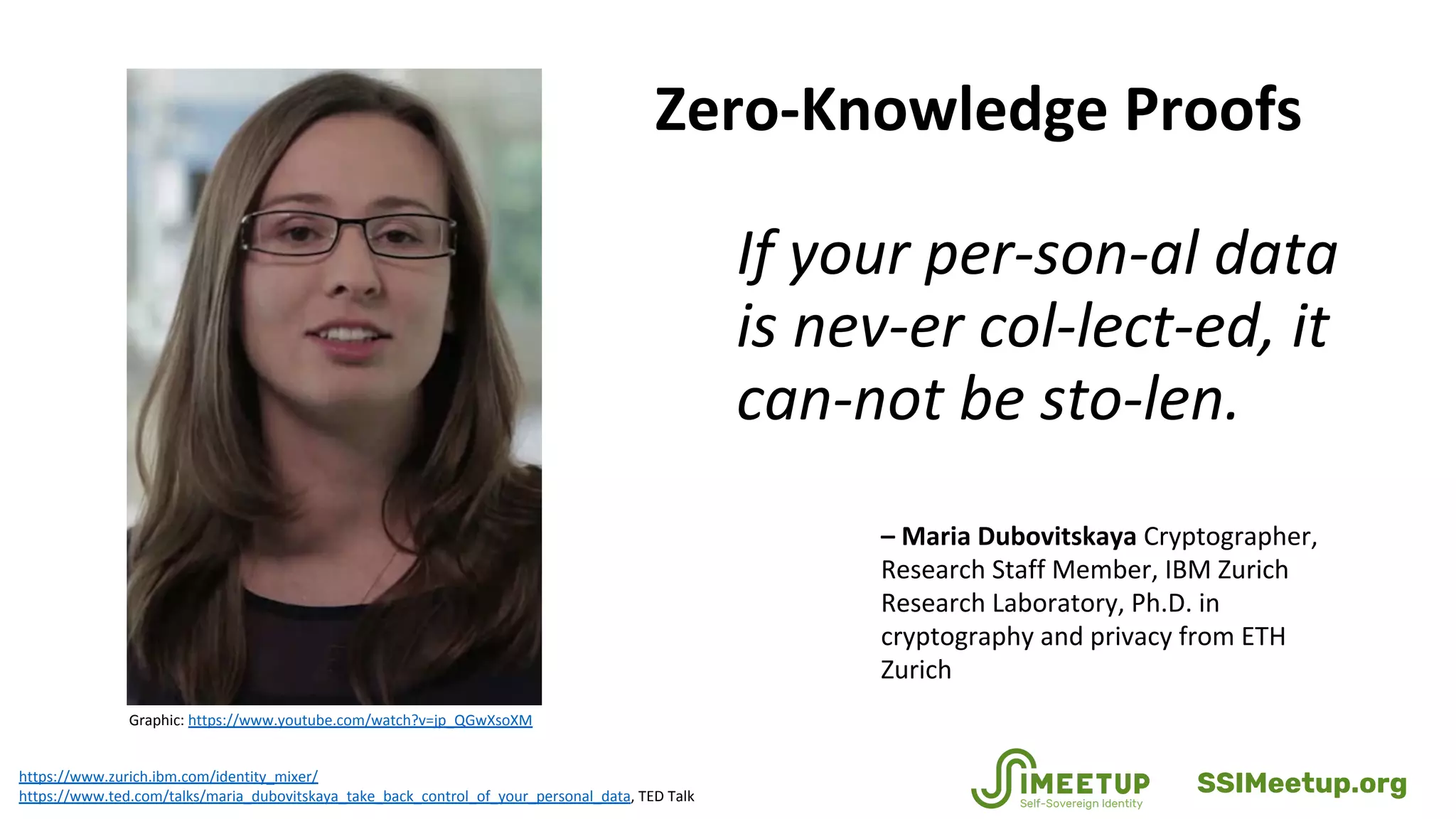
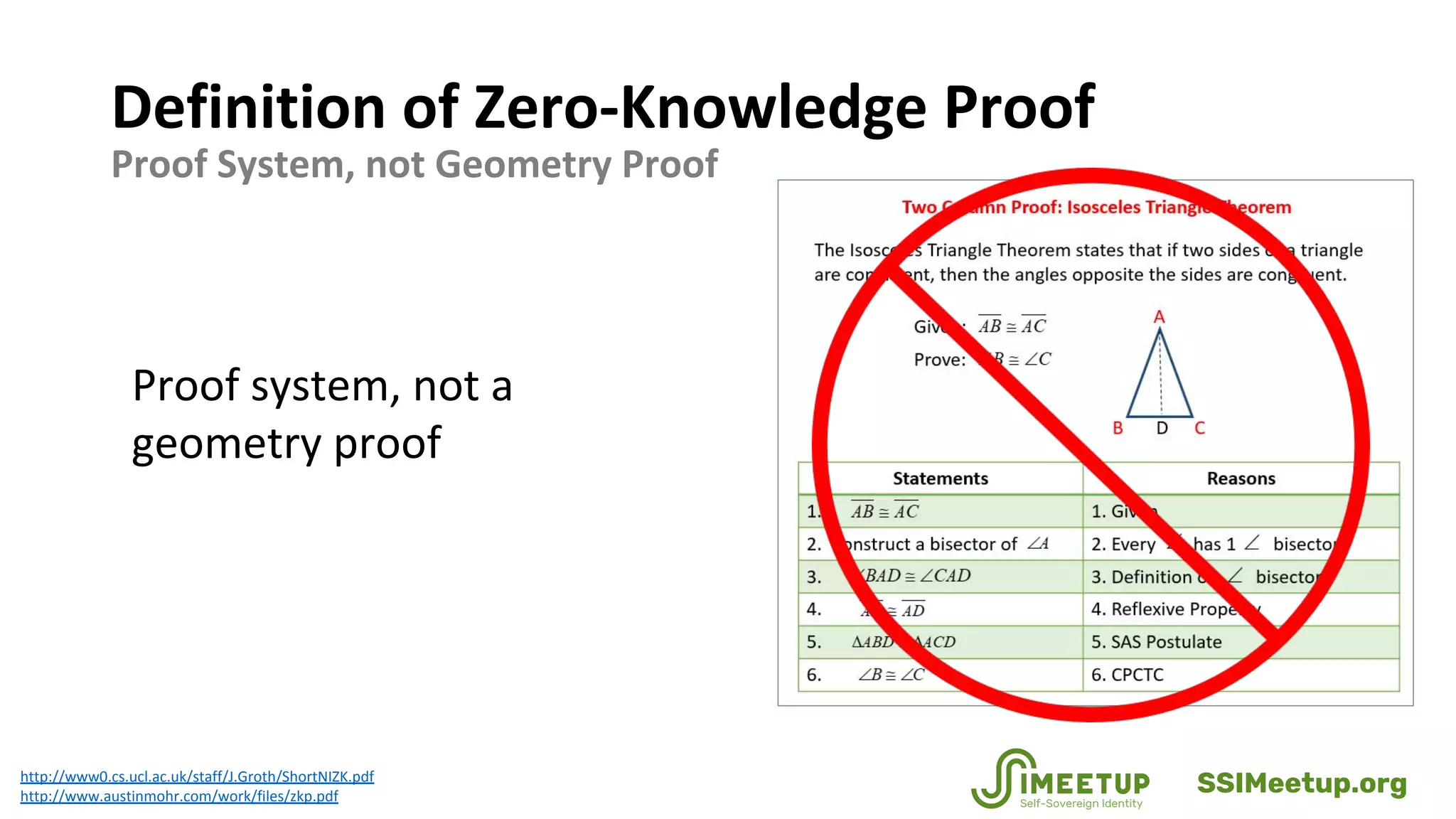
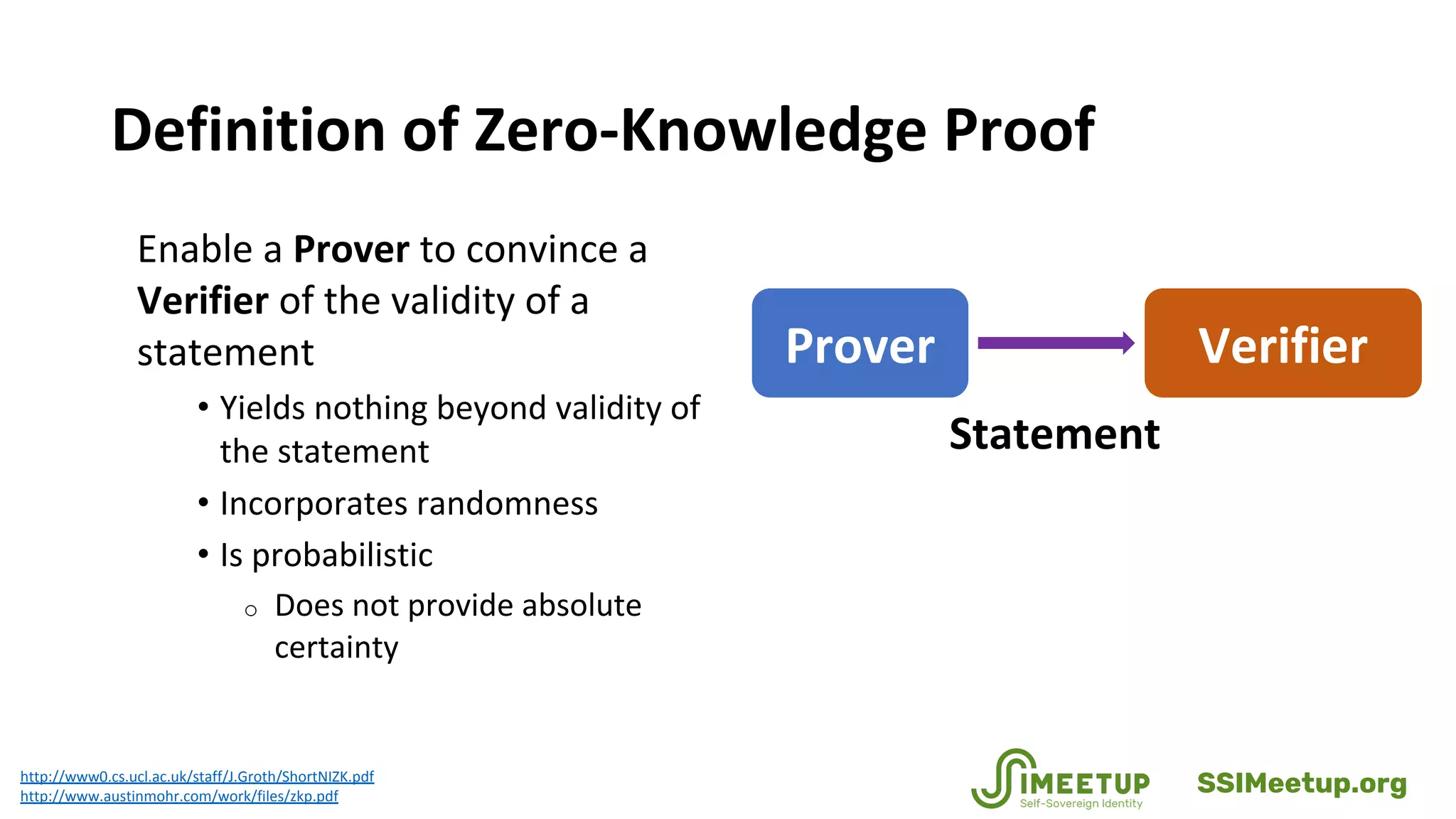
Zero-knowledge proofs (zkps) are cryptographic methods that enhance personal privacy while maintaining institutional integrity by allowing users to prove identities without revealing sensitive information. The document discusses various applications of zkps in digital identity, addressing challenges such as data breaches and identity theft, while promoting a balance between privacy and security. It also covers the technical aspects of zkps, their requirements, and the evolving standards in the field.
































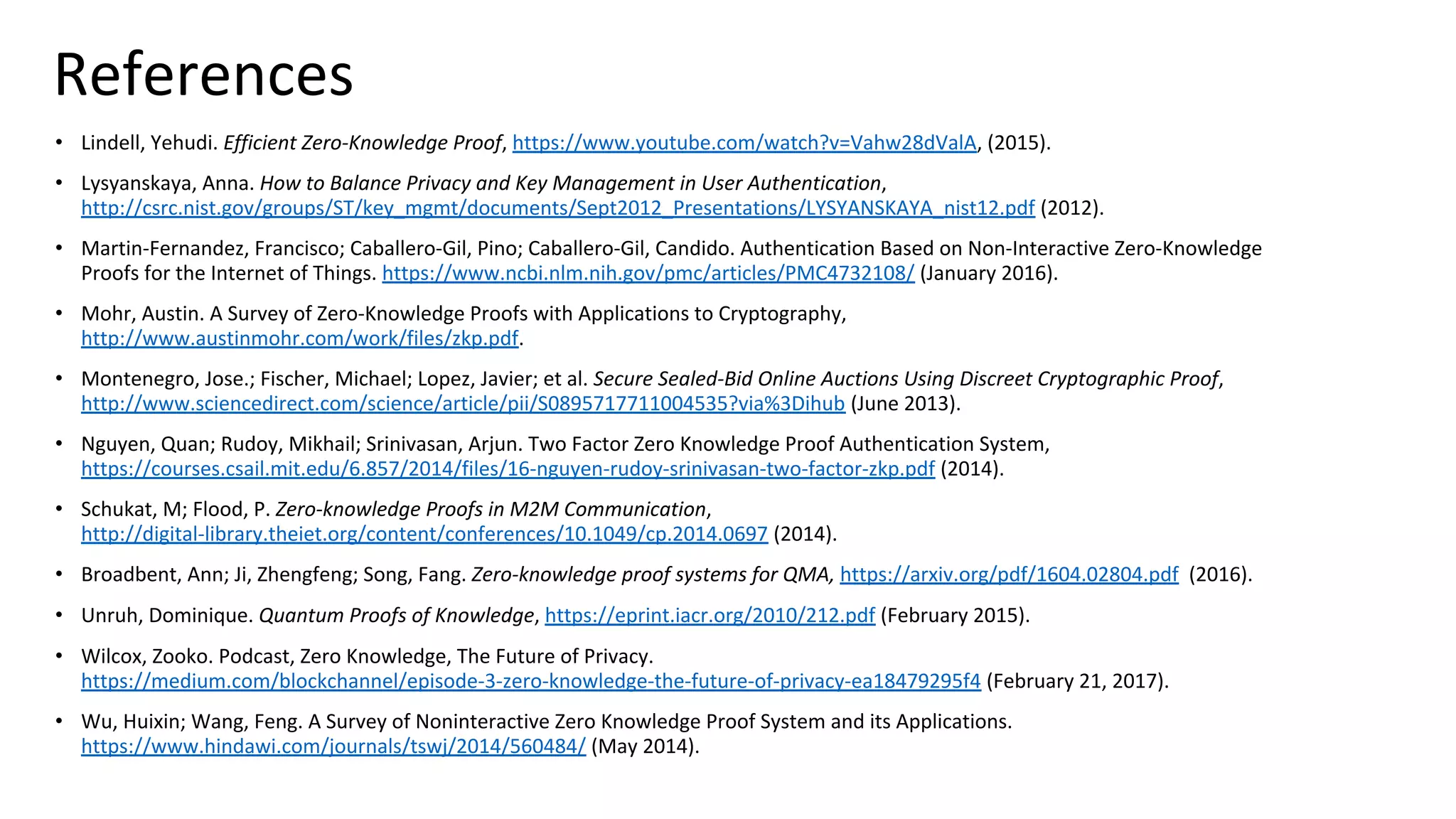
![References
• Groth, Jens. Short Pairing-Based Non-Interactive Zero-Knowledge Arguments, http://www0.cs.ucl.ac.uk/staff/J.Groth/ShortNIZK.pdf
(2010).
• Groth, Jens; Lu, Steve. “A Non-Interactive Shuffle with Pairing Based Verifiability,”
http://www0.cs.ucl.ac.uk/staff/J.Groth/AsiacryptPairingShuffle.pdf (2006).
• Groth, Jens; Ostrovsky, Rafail; Sahai, Amit. New Techniques for Non-interactive Zero-Knowledge,
http://www0.cs.ucl.ac.uk/staff/J.Groth/NIZKJournal.pdf (2011).
• Guillou, Quisqater, “How to Explain Zero-Knowledge Protocols to Your Children,” http://pages.cs.wisc.edu/~mkowalcz/628.pdf
(1998).
• Gupta, Anuj Das; Delight, Ankur. Zero-Knowledge Proof of Balance: A Friendly ZKP Demo,
http://blog.stratumn.com/zero-knowledge-proof-of-balance-demo/ (June 2017).
• Hardjono, Thomas; Pentland, Alex “Sandy”; MIT Connection Science & Engineering; Core Identities for Future Transaction Systems,
https://static1.squarespace.com/static/55f6b5e0e4b0974cf2b69410/t/57f7a1653e00be2c09eb96e7/1475846503159/Core-Identity-
Whitepaper-v08.pdf (October 7, 2016). [TBD: check back, right now it is a DRAFT, do not cite]
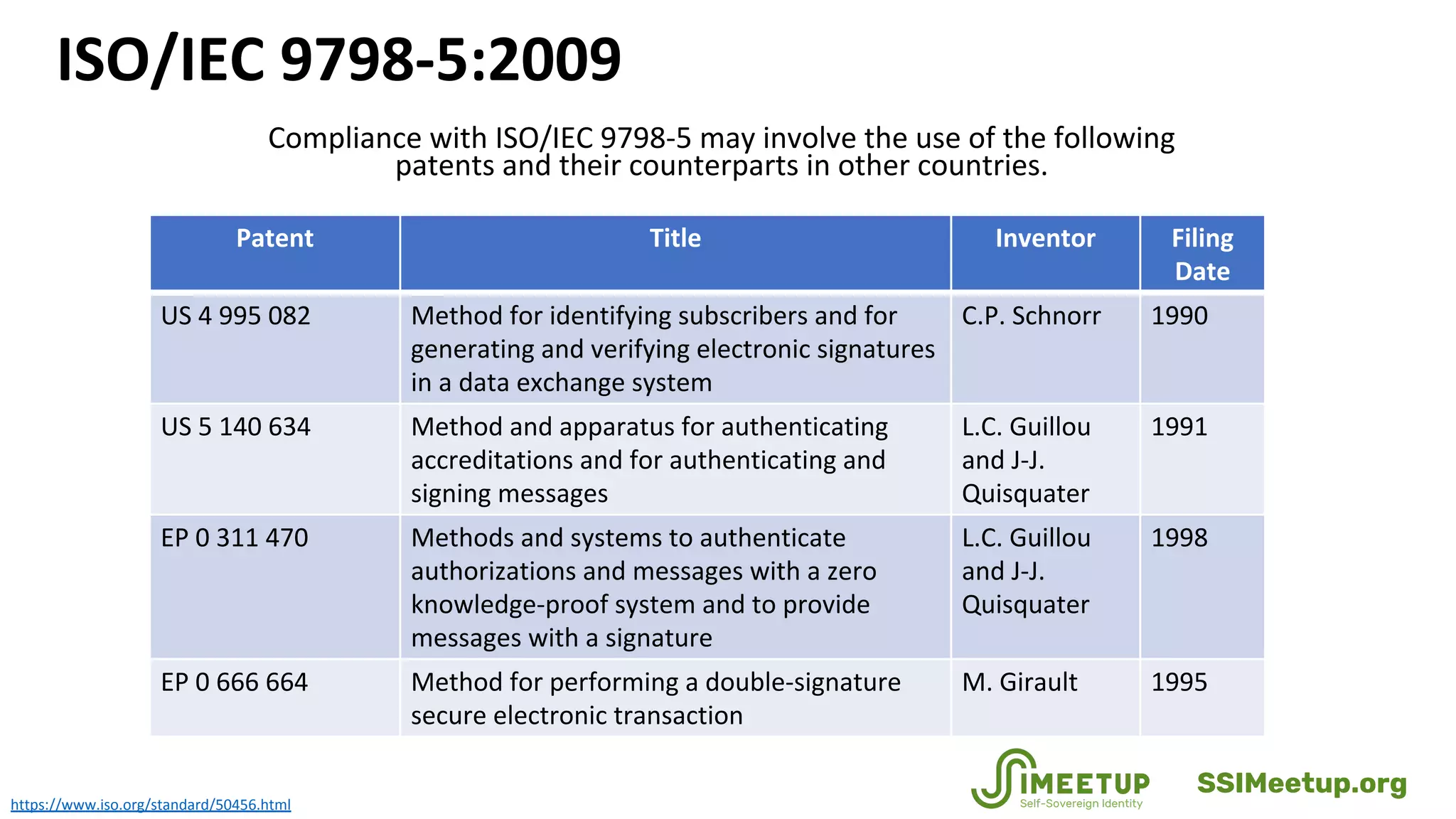
• ISO/IEC Information technology — Security techniques — Entity authentication — Part 5: Mechanisms using zero-knowledge
techniques, https://www.iso.org/standard/50456.html (2015).
• Johnstone, Mike; Why we need privacy-preserving authentication in the Facebook age,
http://www.iaria.org/conferences2015/filesICSNC15/ICSNC_Keynote_v1.1a.pdf (November 2013).
• Kogta, Ronak. ZK-Snarks in English,
https://www.slideshare.net/rixor786/zksnarks-in-english?qid=0e3be303-84fc-43d2-be96-6db2085a28ff&v=&b=&from_search=3
(July 2017).](https://image.slidesharecdn.com/webinar14zero-knowledgeproofsclarenelson-181011205936/75/Zero-Knowledge-Proofs-Privacy-Preserving-Digital-Identity-with-Clare-Nelson-58-2048.jpg)

![Zero-Knowledge Proof, Formal Definition
http://www.cs.cornell.edu/courses/cs6810/2009sp/scribe/lecture18.pd
An interactive proof system (P, V) for a language L is zero-knowledge if
for any PPT verifier V∗
there exists an expected PPT simulator S such
that
∀ x ∈ L, z ∈ {0, 1} ∗
, ViewV∗
[P(x) ↔ V∗
(x, z)] = S(x, z)
As usual, P has unlimited computation power (in practice, P must be a
randomized TM).
Intuitively, the definition states that an interactive proof system (P, V)
is zero-knowledge if for any verifier V∗
there exists an efficient
simulator S that can essentially produce a transcript of the
conversation that would have taken place between P and V∗
on any
given input.
SSIMeetup.org](https://image.slidesharecdn.com/webinar14zero-knowledgeproofsclarenelson-181011205936/75/Zero-Knowledge-Proofs-Privacy-Preserving-Digital-Identity-with-Clare-Nelson-65-2048.jpg)