Defining Cryptography (Cryptography fundamentals 1/2)
- 1. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 1 of 48 Defining Cryptography Study Notes v.1.1 | with video links +W Series – Technology Skills For Women.1 Foundation Level 1 Men too are allowed to read this, if they wish, as the language style and the document format are universal.
- 2. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 2 of 48 1. About “+W Series - Technology Skills for Women” Study Notes in the field of technology are put together under this category for the following reasons: To encourage girls and ladies, who wish to do so, to stand up and look over the fence into technology related topics. With no apprehension or fear. And perhaps consider embracing a career move into a technological path. Or simply to broaden their general knowledge; after all IT is already in most aspects of everyday life. No matter the ground for the decision, their skills, their professional strengths, and their contribution can only be something positive for any technological fields. Please enjoy!
- 3. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 3 of 48 2. Table of Contents 1. About “+W Series - Technology Skills for Women”..................................................................2 3. Foreword...............................................................................................................................................7 4. About this publication.......................................................................................................................8 4.1. Overview ................................................................................................................................................8 4.2. Learning Objectives ................................................................................................................................8 5. Keywords...............................................................................................................................................9 6. What is Cryptography .....................................................................................................................10 6.1. Introducing Cryptography ....................................................................................................................10 6.1.1. Introduction to cryptography........................................................................................................10 6.1.2. Why do we use cryptography?......................................................................................................10 6.1.3. How does cryptography work? .....................................................................................................11 6.2. Use of Cryptography through history ...................................................................................................11 6.2.1. Historical cryptography ................................................................................................................11 6.2.2. Transposition ciphers....................................................................................................................12 6.2.3. Substitution ciphers ......................................................................................................................13 6.2.4. Frequency analysis........................................................................................................................14 6.2.5. Polygraphic substitution ...............................................................................................................14 6.3. Cryptographic Terminology..................................................................................................................14 6.3.1. Cipher ...........................................................................................................................................14 6.3.2. Cryptosystem................................................................................................................................14 6.3.3. Plaintext and Ciphertext ...............................................................................................................14 6.3.4. Key and Code ................................................................................................................................15 6.3.5. Key management..........................................................................................................................15 6.3.6. Key exchange................................................................................................................................15 6.3.7. Block cipher and Stream cipher ....................................................................................................15 6.3.8. Hashing.........................................................................................................................................15 6.3.9. Mode of operation........................................................................................................................16 6.3.10. Number theory .............................................................................................................................16 6.3.11. Integer factorization .....................................................................................................................16 6.3.12. Cryptanalysis ................................................................................................................................16 6.3.13. Side-channel attack ......................................................................................................................16 6.4. Is Cryptography Difficult? .....................................................................................................................16 6.4.1. All cryptography can be broken or cracked...................................................................................16 6.4.2. Past cryptography is easily broken today .....................................................................................16 6.4.3. How to tell when a cryptographic algorithm is strong?................................................................17 6.4.4. DES, 3DES and AES........................................................................................................................17 6.4.5. How to determine how strong a crypto system or cipher is? ........................................................17 6.4.6. Using standards for cryptography ................................................................................................17 6.5. Identifying different types of Cryptography .........................................................................................18 6.5.1. Types of cryptography ..................................................................................................................18 6.5.2. Encryption algorithms tested a country’s institute of standards ..................................................18
- 4. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 4 of 48 6.6. Describing Export Controls and Limits on Cryptography ......................................................................18 6.6.1. Export controls and limits .............................................................................................................19 6.6.2. Wassenaar Arrangement..............................................................................................................19 6.6.3. Export or import control over cryptosystems................................................................................19 6.6.4. Licenses might be required ...........................................................................................................19 7. Purpose of Cryptography...............................................................................................................20 7.1. Describing Ways Cryptography Provides Confidentiality......................................................................20 7.1.1. Notion of confidentiality ...............................................................................................................20 7.1.2. Encryption requires use of secrecy................................................................................................20 7.1.3. Confidentiality is linked to a time frame .......................................................................................20 7.1.4. Confidentiality is between two parties or more............................................................................21 7.1.5. Always have a sort of recovery key...............................................................................................21 7.1.6. Traffic on an unencrypted network...............................................................................................21 7.2. Recognizing the Need for Data Integrity...............................................................................................21 7.2.1. About data integrity .....................................................................................................................22 7.2.2. Encryption and integrity are separate ..........................................................................................22 7.2.3. About Hash and Message Digest ..................................................................................................22 7.3. Defining Cryptography Authentication.................................................................................................23 7.3.1. Understanding Authentication in cryptography ...........................................................................23 7.3.2. Authentication codes or MACs (M-A-Cs).......................................................................................23 7.3.3. Authentication can include two parts...........................................................................................24 7.3.4. Asymmetric key encryption in authentication...............................................................................24 7.3.5. Session management....................................................................................................................24 7.3.6. Further Message Authentication Code MAC, HMAC.....................................................................24 7.4. Applying Non-repudiation to Cryptography .........................................................................................27 7.4.1. About non-repudiation .................................................................................................................27 7.4.2. Digital signatures..........................................................................................................................27 7.4.3. Purpose of non-repudiation..........................................................................................................28 7.4.4. Asymmetric encryption and non-repudiation ...............................................................................28 7.4.5. Non-repudiation implemented with digital signatures .................................................................28 8. Cryptographic Methods ..................................................................................................................29 8.1. Using a One-time Pad (OTP) .................................................................................................................29 8.1.1. Understanding One-time Pad .......................................................................................................29 8.2. Describing Substitution Ciphers............................................................................................................30 8.2.1. About substitution ciphers............................................................................................................30 8.2.2. Caesar shift...................................................................................................................................31 8.2.3. Vigenère cipher.............................................................................................................................31 8.2.4. Polyalphabetic ciphers..................................................................................................................31 8.2.5. Advantages of substitution ciphers...............................................................................................31 8.2.6. Substitution ciphers drawbacks ....................................................................................................31 8.3. Using Symmetric Algorithms ................................................................................................................31 8.3.1. Understanding symmetric algorithms ..........................................................................................32 8.3.2. Symmetric key algorithms ............................................................................................................32 8.3.3. Symmetric key is a shared secret ..................................................................................................32
- 5. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 5 of 48 8.4. Working with Asymmetric Algorithms..................................................................................................33 8.4.1. Notion of asymmetric algorithms .................................................................................................33 8.4.2. Private key and public key paired together...................................................................................34 8.4.3. Usage of asymmetric algorithms..................................................................................................34 8.5. Hiding Data Using Steganography ........................................................................................................34 8.5.1. About Steganography...................................................................................................................35 8.5.2. A software is needed for steganography ......................................................................................35 8.5.3. Illustrations of steganography......................................................................................................35 8.5.4. Advantages and disadvantages of steganography.......................................................................35 8.6. Using One-way Hashes .........................................................................................................................36 8.6.1. Understanding one-way hashes....................................................................................................36 8.6.2. One-way hashes: critical to many cryptographic systems ............................................................36 8.6.3. Common hashing algorithms........................................................................................................36 8.6.4. About MD5 common hashing algorithm.......................................................................................37 8.7. Describing Digital Signatures ................................................................................................................37 8.7.1. What is digital signature?.............................................................................................................37 8.7.2. What’s digital signature used for?................................................................................................38 8.7.3. Components of a digital signature................................................................................................38 8.7.4. Advantages of digital signatures ..................................................................................................38 8.7.5. Disadvantages of digital signatures..............................................................................................38 8.7.6. Digital signatures algorithms........................................................................................................38 9. Building Blocks of Cryptography.................................................................................................39 9.1. Distinguishing between Block and Key Sizes ........................................................................................39 9.1.1. Block ciphers.................................................................................................................................39 9.1.2. Key sizes........................................................................................................................................39 9.1.3. Block algorithms...........................................................................................................................39 9.1.4. Comparing algorithm block and key sizes.....................................................................................40 9.2. Using Padding.......................................................................................................................................40 9.2.1. About padding..............................................................................................................................40 9.2.2. Zero padding.................................................................................................................................40 9.2.3. Bit padding ...................................................................................................................................41 9.2.4. Byte padding.................................................................................................................................41 9.2.5. Byte padding illustrated................................................................................................................41 9.3. Formatting the Output .........................................................................................................................42 9.3.1. Understanding text encoding .......................................................................................................42 9.3.2. Text encoding format....................................................................................................................43 9.4. Using Nonces and the Initialization Vector...........................................................................................43 9.4.1. About initialization vectors (IV).....................................................................................................43 9.4.2. About Nonces ...............................................................................................................................44 9.5. Identifying and Using Entropy ..............................................................................................................44 9.5.1. Understanding entropy.................................................................................................................44 9.5.2. Weaknesses of using passwords...................................................................................................45 9.5.3. Using pseudorandom number generators (PRNGs) ......................................................................45 9.6. How cryptographic keys are generated? ..............................................................................................45
- 6. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 6 of 48 9.6.1. Types of cryptographic keys..........................................................................................................45 9.6.2. Generating keys............................................................................................................................46
- 7. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 7 of 48 3. Foreword Security management concepts and principles are inherent elements in a security policy and solution deployment. They define the basic parameters needed for a secure environment. They also define the goals and objectives that both policy designers and system implementers must achieve to create a secure solution. It is important for security professionals, as well as Information Systems Security learners, to understand these items thoroughly. The primary goals and objectives of security are contained within the CIA Triad (concepts of Confidentiality, Integrity, and Availability), which is the name given to the three primary security principles. The first principle of the CIA Triad is confidentiality. If a security mechanism offers confidentiality, it offers a high level of assurance that data, objects, or resources are restricted from unauthorized subjects. If a threat exists against confidentiality, unauthorized disclosure could take place. In general, for confidentiality to be maintained on a network, data must be protected from unauthorized access, use, or disclosure while in storage, in process, and in transit. Unique and specific security controls are required for each of these states of data, resources, and objects to maintain confidentiality. The second principle of the CIA Triad is integrity. For integrity to be maintained, objects must retain their veracity and be intentionally modified by only authorized subjects. If a security mechanism offers integrity, it offers a high level of assurance that the data, objects, and resources are unaltered from their original protected state. Alterations should not occur while the object is in storage, in transit, or in process. Thus, maintaining integrity means the object itself is not altered and the operating system and programming entities that manage and manipulate the object are not compromised. The third and last principle of the CIA Triad is availability, which means authorized subjects are granted timely and uninterrupted access to objects. If a security mechanism offers availability, it offers a high level of assurance that the data, objects, and resources are accessible to authorized subjects. Availability includes efficient uninterrupted access to objects and prevention of denial-of-service (DoS) attacks. Cryptography provides added levels of security to data during processing, storage, and communications. Thus, Security practitioners use cryptographic systems to meet four fundamental goals: confidentiality, integrity, authentication, and nonrepudiation.
- 8. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 8 of 48 4. About this publication 4.1. Overview Cryptography is essential to protecting data. Learn about how cryptography can be used to protect and secure data, different methods that exist to protect or transmit data securely, and the components that need to be understood to ensure data can be protected properly. 4.2. Learning Objectives After going through this publication, you should be able to: describe and identify the reasons for having and using cryptography use and identify basic cryptographic terminology describe why cryptography is difficult to get right and how poor cryptography can give you a false sense of security identify the different types of cryptography and how cryptographic algorithms can be verified and validated describe how cryptography can keep data confidential and within limits describe why data integrity is an integral part of cryptography define how cryptography can provide a means to authenticate an entity describe how OTP, or one-time pad cryptography can theoretically provide perfect secrecy but has some significant limitations describe and use a substitution cipher and understand the weaknesses that can be exploited by an attacker against these ciphers describe and identify the features and use cases for symmetric-key and asymmetric-key cipher algorithms describe the use of steganography in encryption products to hide the fact data is even encrypted describe the purpose of cryptographic hash functions and how they can be used in cryptography to provide data integrity describe a digital signature and how it can be used for authentication and non- repudiation recognize the difference between blocks and key sizes as they apply to cipher algorithms describe and perform padding operations to data for block ciphers describe how to encode encrypted data for easier storage or transport describe the purpose of an initialization vector for a cipher algorithm describe how entropy is used in generating random numbers and how that entropy is critical to the strength of a cryptographic key describe the creating, or generating, of keys and how the key strength is critical to cryptographic ciphers
- 9. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 9 of 48 5. Keywords Advanced Encryption Standard (AES) Asymmetric-Key Attacker Authentication Availability Basic Export Controls And Limits Block Ciphers Blocks Blowfish Cipher Cipher Algorithms Confidentiality Creating Keys Critical Cryptographic Cryptographic Algorithms Cryptographic Ciphers Cryptographic Key Cryptography Data Confidential Data Encryption Standard (DES) Data Integrity Datasets Digital Signature Encode Encrypted Data Encryption Entropy Generating Keys Hash Functions Initialization Vector Integrity International Data Encryption Algorithm (IDEA) Key Sizes Key Strength Nonces Non-Repudiation OTP, One-Time Pad Padding Operations Random Numbers Security Skipjack Steganography Substitution Cipher Symmetric-Key Triple DES (3DES) Types Of Cryptography
- 10. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 10 of 48 6. What is Cryptography 6.1. Introducing Cryptography 6.1.1. Introduction to cryptography Often, cryptography is simply referred to as crypto. It is the study of secure communications. Cryptography provides added levels of security to data during processing, storage, and communications. Over the years, mathematicians and computer scientists have developed a series of increasingly complex algorithms designed to ensure confidentiality, integrity, authentication, and nonrepudiation. While cryptographers spent time developing strong encryption algorithms, hackers and governments alike devoted significant resources to undermining them. This led to an “arms race” in cryptography and resulted in the development of the extremely sophisticated algorithms in use nowadays. 6.1.2. Why do we use cryptography? Security practitioners use cryptographic systems to meet four fundamental goals: Confidentiality: We can protect who can see a message. Data remains private while at rest, such as when stored on a disk, or in transit, such as during transmission between two or more parties. Integrity: We can assure that data has not been tampered with. When integrity mechanisms are in place, the recipient of a message can be certain that the message received is identical to the message that was sent. Authentication: We can confirm that a message is authentic and has not been forged. Authentication verifies the claimed identity of system users and is a major function of cryptosystems. Non-repudiation: We can verify that data originate in fact from the owner or the sender of a message. Non-repudiation provides assurance to the recipient that, the message was originated by the sender and not someone masquerading as the sender. It also prevents the sender from claiming that they never sent the message in the first place (also known as repudiating the message).
- 11. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 11 of 48 Achieving each of these four fundamental goals: confidentiality, integrity, authentication, requires the satisfaction of a number of design requirements, then again not all cryptosystems are intended to achieve all four goals. 6.1.3. How does cryptography work? Before a message is put into a coded form, it is known as a plaintext message and is represented by the letter P when encryption functions are described. The sender of a message uses a cryptographic algorithm to encrypt the plaintext message and produce a ciphertext message, represented by the letter C. This message is transmitted by some physical or electronic means to the recipient. Then the recipient uses a predetermined algorithm to decrypt the ciphertext message and retrieve the plaintext version. With encryption, we are scrambling or obfuscating data. To do that, we need some type of a key. Decryption is the act of revealing encrypted data (original message). It occurs only with the correct key. Hashing is the act of creating a unique value that can be used to authenticate the original message. It takes data, puts it through an algorithm, and results in a unique value called a hash value. Then we can recompute a hash value on data again. And, if the value is different, it means that the original data has changed. 6.2. Use of Cryptography through history 6.2.1. Historical cryptography https://youtu.be/L5lT6eFa-hM Cryptography has been used for thousands of years where its primary purposes are to protect data from unauthorized parties and to ensure that the data has not been tampered with. Cipher systems have long been used by individuals and governments interested in preserving the confidentiality of their communications. 6.2.1.1. Caesar Cipher One of the earliest known cipher systems was used by Julius Caesar to communicate with Cicero in Rome while he was conquering Europe. Caesar knew that there were several risks when sending messages - one of the messengers might be an enemy spy or might be ambushed while en route to the deployed forces.
- 12. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 12 of 48 For that reason, Caesar developed a cryptographic system now known as the Caesar cipher. The system is rather simple: To encrypt a message, you simply shift each letter of the alphabet three places to the right. For example, A would become D , and B would become E. If you reach the end of the alphabet during this process, you simply wrap around to the beginning so that X becomes A , Y becomes B , and Z becomes C . For this reason, the Caesar cipher also became known as the ROT3 (or Rotate 3) cipher. Therefore, the Caesar cipher is a substitution cipher that is monoalphabetic; it’s also known as a C3 cipher. Here’s an illustration of the Caesar cipher in action. The first line contains the original sentence, and the second line shows what the sentence looks like when it is encrypted using the Caesar cipher: THE DIE HAS BEEN CAST WKH GLH KDV EHHQ FDVW To decrypt the message, you simply shift each letter three places to the left. 6.2.1.2. Classical ciphers Classical ciphers were usually based on either transposition or substitution. 6.2.1.3. Steganography Steganography was also and still is commonly used today. With steganography, it’s about concealing one message within another message. 6.2.2. Transposition ciphers Transposition ciphers use an encryption algorithm to rearrange the letters of a plaintext message, forming the ciphertext message. The decryption algorithm simply reverses the encryption transformation to retrieve the original message. Two common transposition ciphers include the route cipher and the rail fence cipher. 6.2.2.1. Rail fence cipher Rail fence cipher works by having each letter of the original plaintext message written on a separate line and spaced out. The resultant cyphertext or encrypted value is different than the original plaintext.
- 13. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 13 of 48 6.2.2.2. Route cipher Route cipher builds on the rail cipher, but it writes everything in a grid with a known dimension, and the data is spiraled around the original message to generate the encrypted strength. 6.2.3. Substitution ciphers Substitution ciphers use the encryption algorithm to replace each character or bit of the plaintext message with a different character. Therefore, substitution ciphers substitute either letters, words, or groups of characters with some other value, hence, substitution. There are many different types of substitution ciphers. Caesar cipher is the most common. The Caesar cipher shifts letters by some specific amount, for example, by three. So that, if we start off with the letter "a" and we're shifting by three, our result is letter "D."
- 14. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 14 of 48 However, we ran into a problem when we got to the end of the alphabet and ran out of letters. Also, these early cryptographic methods were attackable using frequency analysis. 6.2.4. Frequency analysis With frequency analysis, we can use knowledge of a language and the understanding that certain letters and combinations of letters occur more frequently than others. For example, in the English language, the letter "e" is very commonly used and is often followed by the letter "t." There are some attempts to prevent frequency analysis attacks. One is called polygraphic substitution, 6.2.5. Polygraphic substitution By polygraphic substitution, we have a group of plaintext values that get replaced by a predetermined character or an entire group of other characters. With polyalphabetic substitution, we're using multiple substitution alphabets. And this, in the end, will reduce the effectiveness of frequency analysis attacks. 6.3. Cryptographic Terminology It's important to have a solid understanding of cryptographic terms before being able to truly understand cryptography. https://youtu.be/j6304OEMbIo 6.3.1. Cipher A cipher is a cryptographic algorithm that encrypts or decrypts a message. 6.3.2. Cryptosystem A cryptosystem is a system that includes the cipher for encryption and decryption and a key generation and key management process. 6.3.3. Plaintext and Ciphertext Plaintext refers to the original, unencrypted message either before it's been encrypted or after it's been decrypted. Ciphertext refers to the encrypted representation of the original message or plaintext.
- 15. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 15 of 48 6.3.4. Key and Code A key is a set of bits that's used by a cipher to encrypt plaintext or to decrypt ciphertext. The correct key needs to be in our possession before we can decrypt encrypted messages. Code is a term that can mean to convert something into code – that is to encrypt it. A code can represent a key or word that was used in older cryptographic methods. 6.3.5. Key management With cryptography, key management is very crucial because keys are used for things like encryption and decryption. Key management refers to the generation, the exchange, the storage, and the revoking of keys. 6.3.6. Key exchange Key exchange is the process of securely exchanging keys, normally over a network. 6.3.7. Block cipher and Stream cipher Block ciphers operate on “chunks,” or blocks, of a message and apply the encryption algorithm to an entire message block at the same time. The transposition ciphers are examples of block ciphers. A block cipher operates on a single block of data, usually of 8- to 128-byte block. Stream ciphers operate on one character or bit of a message (or data stream) at a time. The Caesar cipher is an example of a stream cipher. The one-time pad is also a stream cipher because the algorithm operates on each letter of the plaintext message independently. Both block and stream ciphers result in ciphertext. 6.3.8. Hashing Hashing creates a one-way, fixed-length unique value that represents the original data that was passed to the hashing algorithm.
- 16. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 16 of 48 6.3.9. Mode of operation Mode of operation provides a method to encrypt and decrypt more than one block when we are using block ciphers. 6.3.10. Number theory Cryptography is based heavily on mathematics. With number theory, the mathematical study of integers for crypto and computationally complex problems related to things like factorization are used often. 6.3.11. Integer factorization An integer is a number that doesn't have any fraction, so it's a whole number. Integer factorization is the breakdown of a positive integer into two prime numbers. In crypto, prime numbers are often used because in mathematics prime numbers really don't have a discernible pattern. 6.3.12. Cryptanalysis Cryptanalysis is the study of breaking cryptographic ciphers or systems. The purpose is to determine the strength of that cryptosystem or that cipher. 6.3.13. Side-channel attack With the side-channel attack, we attack the physical infrastructure of a cryptosystem rather than the algorithms themselves with the end goal of capturing data related to the ciphertext or keys. 6.4. Is Cryptography Difficult? Assess if cryptography is difficult to get right and how poor cryptography can give us a false sense of security. https://youtu.be/PBpqcv9N1HY 6.4.1. All cryptography can be broken or cracked Cryptography strives to protect data, but despite our best efforts, all cryptography can be broken or cracked. It's really a question of the amount of time and effort one is willing to put in, to crack a given cryptography. The effort is often a calculable quantity given today's computing power. 6.4.2. Past cryptography is easily broken today Many good cryptographic systems from the past can easily be broken because of advances in mathematics and advances in computing power. But will today's strong cryptography be easily broken tomorrow? Chances are the answer is yes.
- 17. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 17 of 48 6.4.3. How to tell when a cryptographic algorithm is strong? It's not as simple as comparing one algorithm with another and saying this one is better than that one. We have to look at things like cipher key lengths. We also have to look at the specific implementation of an algorithm. So it's not just as simple as looking at the algorithm itself. 6.4.4. DES, 3DES and AES Crypto systems today must have a very large key space in order to prevent this kind of an attack. DES stands for the Digital Encryption Standard and was used by U.S. federal government agencies in the 1970s. It was then replaced by Triple DES or 3DES and eventually by AES – the Advanced Encryption Standard. DES uses a 56-bit keys. AES has three strengths – 128, 192, and 256 bits, depending on how the cipher gets used. AES 256 can encrypt data such as in image using Electronic Codebook or ECB. With crypto, if we can determine some kind of a pattern, then we have a potential way to crack that crypto system or that specific cipher. 6.4.5. How to determine how strong a crypto system or cipher is? Key length is part of that. So a 256-bit symmetric key means that there are 2^256 (two to the power of 256) possible keys in that key space. That's better than a 56-bit key, which has far fewer possible combinations. However, bigger key lengths don't always mean that we have a stronger algorithm 6.4.6. Using standards for cryptography Having standards for cryptography is very important. This way, we have many groups of people analyzing and attacking and determining the true strength of a crypto system or an individual cipher.
- 18. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 18 of 48 6.5. Identifying different types of Cryptography We need to need to learn to identify the different types of cryptography and how cryptographic algorithms can be verified and validated. https://youtu.be/lOWOxwiViD4 6.5.1. Types of cryptography 6.5.1.1. Effective cryptosystem solutions In order to have effective cryptosystem solutions in a marketplace we need standards. Entities, such as the NIST (National Institute of Standards and Technology) in the USA and others according to the country or region where we live, deals with many different standards, even outside of Information Technology. 6.5.1.2. Encryption algorithms recommended by government agencies But, when we look at the Information Technology we have a number of standards that are adhered to by vendors. Government agencies, in our region or country, adhere to standards that outline how data is dealt with, what encryption algorithms are recommended for use by government agencies, and others. 6.5.2. Encryption algorithms tested a country’s institute of standards This allows us to make sure that IT products meet very specific security specifications, and at least a minimum security standard. Therefore, encryption algorithms have to go through certain testing with institutes of standards according to the country where we operate. Also, institutes of standards, according to the country where we are, maintain list of validated cryptographic modules, which are considered to be safe cryptographic modules that can be used in our market. New algorithms can also be submitted and verified through these institutes of standards, where we live. There might be other sources and validations as well for IT security in our respective country or region, and we need to verify who they are too. 6.6. Describing Export Controls and Limits on Cryptography We should be able to describe basic export controls and limits that can be imposed on cryptography used in our own country or region and around the world. https://youtu.be/YrjzGVexjdI
- 19. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 19 of 48 6.6.1. Export controls and limits The main reason that a nation will apply export controls on hardware and software cryptography is due to national security threats. 6.6.2. Wassenaar Arrangement The Wassenaar Arrangement of the 1990s applies export controls for nations on dual- use goods and technologies. These are items built for both civilian and military use. There are around 40 participating countries. 6.6.3. Export or import control over cryptosystems Most countries have some form of export or import control over cryptosystems. Some countries may has relaxed its policies since the 2000s. However, depending on the country of origin and the country of destination, there may be legal issues that need to be overcome when exporting software or hardware with cryptographic capabilities. 6.6.4. Licenses might be required The export of such products that contains strong modern crypto might require us to register to get a license to export them. In some cases, countries have laws that can force suspects to decrypt or provide the keys to decrypt encrypted data.
- 20. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 20 of 48 7. Purpose of Cryptography 7.1. Describing Ways Cryptography Provides Confidentiality We should be able to describe the way cryptography can keep data confidential and within limits. https://youtu.be/SMm6COxYfBo 7.1.1. Notion of confidentiality Confidentiality ensures that data isn't disclosed to unauthorized parties. So, when data is transmitted over a network – if it's encrypted –confidentiality is provided of that transmission. The same thing applies if when saving a file on disk and then encrypting it. Confidentiality is provided by way of encryption. Confidentiality was the primary purpose for which cryptography was originally used, and this is still the case today. 7.1.2. Encryption requires use of secrecy Encryption requires the use of a secret, which is a key or a code, in order to encrypt and decrypt a message. That might come in the form of a pass phrase that a user will type in before being allowed to connect to an encrypted Wi-Fi network. Or it could be a key embedded on a smart card that a user must swipe before gaining access to a building or a secured computer system. 7.1.3. Confidentiality is linked to a time frame Confidentiality usually comes with a term – a time frame in which the information must be protected.
- 21. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 21 of 48 An example is credit card which has a valid lifetime of approximately three to five years. So using a cipher that would take 20-plus years to break by today's computing means should be a cipher good enough to use for a credit card. 7.1.4. Confidentiality is between two parties or more Confidentiality is generally between two parties – the sender and the receiver. However, cryptosystems have been built to split keys between more than two parties. Cryptosystems have also been built to allow multiple parties, each with their own unique key, to access the same data. 7.1.5. Always have a sort of recovery key Now the loss of the key should make the data unrecoverable in any reasonable expectation of time. So, when we implement confidentiality through encryption – whether it's network encryption or file encryption – it's important that we have some kind of a recovery key that a trusted party can generate. Otherwise, loss of the key that's used to decrypt encrypted data means that data is not accessible by anybody. 7.1.6. Traffic on an unencrypted network Traffic on an unencrypted network can easily be captured with a toll like Wireshark. The analyzed traffic might show there was a login for a particular user and the word password used. That would mean there is no data confidentiality. It would be in plaintext and has not been encrypted. 7.2. Recognizing the Need for Data Integrity We should be able to understand why data integrity is an integral part of cryptography. https://youtu.be/JXCld-cq9jY
- 22. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 22 of 48 7.2.1. About data integrity Data integrity is used to detect changes to data. The data changes can either be malicious or accidental, such as an attacker altering a message, or the changes might be accidental like data corruption during transit. However, data integrity isn't limited to being applied to network transmissions. Also, we could use data integrity to verify whether or not a record in a database has been tampered with. Or, we might use data integrity to verify that a file stored on disk has not changed. Although encryption can make a message look like random data, it makes it look scrambled. It doesn't generally provide a method to ensure the data has not been tampered with and that's where data integrity comes in. 7.2.2. Encryption and integrity are separate Hashing can be used to detect file changes. For instance, a unique hash can be generated from a file. Then, if changes are made and saved to that file, when we, once again, generate a hash from that same file – because that file has changed – the second hash will differ from the first. That would mean that the file is in a different state than it was when we first took the hash. Let's take a look at this in the Windows environment. 7.2.3. About Hash and Message Digest Hashing is also sometimes resultant in a message digest. So Hash and Message Digest are synonymous. Message Digests used with encryption can provide a check to validate if a message has been altered. Some modes of operation, when it comes to block ciphers, also reduce the risk of data being altered. Some of these block cipher modes tend to use the previous block of data as input to the next block of data. Therefore, a change to one block would be reflected in all of the following blocks. Still, this would not detect a truncation of the message.
- 23. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 23 of 48 7.3. Defining Cryptography Authentication We should be able to understand how cryptography can provide a means to authenticate an entity. https://youtu.be/8TqKGjKUpMg 7.3.1. Understanding Authentication in cryptography Authentication is the ability to verify the authenticity of a message. Authentication in cryptography can come in two forms. 7.3.1.1. Verifying sender really sent message The first of the two forms is verifying that the sender really sent the message. This can be done with the sender using their unique private key that was issued to them to sign a message. Only the sender would have access to their private key, nobody else would. The recipient could use the mathematically related public key of the sender to verify the signature created with the private key. 7.3.1.2. Verifying receiver received correct message The second of the two forms of authentication within crypto is verifying that the receiver received the correct message. Not only do we want to ensure the message came from who it says it came from. But we also want to make sure that the message was not tampered with. 7.3.2. Authentication codes or MACs (M-A-Cs) Message authentication codes or MACs (M-A-Cs) can be used to authenticate messages. MACs provide an additional string of data that's used to verify the authenticity of the message. A common MAC is the hashed key message authentication code or HMAC. HMAC can provide both data integrity as well as authentication.
- 24. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 24 of 48 7.3.3. Authentication can include two parts Remember authentication is the ability to verify the authenticity of a message. In cryptography, authentication can include two parts. The first part is to verify whether the sender has sent the message. The second part is to verify whether the receiver has received the correct message. 7.3.4. Asymmetric key encryption in authentication Asymmetric key encryption uses a mathematically related public and private key pair that would be issued, for instance, to every user. This can also provide authentication because the private key uniquely identifies a user and only that user would have access to the private key. Inversely, everybody would have access to everybody's public keys that would be used to verify signatures. 7.3.5. Session management Session management is a form of authentication where session keys can be used once the authentication has been completed. These session keys then authorize access to sort of a network resource. Sessions should also contain a session counter. This is a number that can be embedded in each message to ensure that a message can't be replayed and to allow one or both sides of the connection to know when a message failed to deliver. 7.3.6. Further Message Authentication Code MAC, HMAC It is easier for people to understand encryption (confidentiality), but it becomes tricky when we talk about integrity and authenticity. While Integrity is making sure the data is not modified since the last time we looked at, authenticity means that the recipient may reasonably be certain that a message was truly created by its purported author. Integrity and Authenticity serve different purposes, but they are related to a certain extend. 7.3.6.1. Confidentiality via Encryption Let us suppose Alice and Bob are exchanging a secret message (m) over an open channel. “Eve” on the other hand is listening to the channel. Using an encryption and a shared secret key, both Alice and Bob can exchange their messages without Eve knowing the content, thus confidentiality is ensured.
- 25. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 25 of 48 But there is another problem, Eve can do more than listening to the message if he can have a small control over the channel. In this way, Eve can change the message that Alice sent, so that Bob will receive a different message. The integrity of the message is compromised in this case. Actually, if Eve has control of the channel, he can do another nasty things. He can learn the message (m), record it and then resend it to Bob, or even delete the message completely so that Bob will not receive anything. 7.3.6.2. Hash functions alone does not equal integrity One solution to the integrity problem is that Alice could compute the hash of the message, and send both the message and the hash to Bob. Bob can then read the message, and then recompute the hash of the message and compare it with the hash value received from Alice. The problem here is that Eve could interrupt the message that Alice sent, create a new message and then send the new message and the hash of the new message to Bob. Bob then will do the same computation and he would think that the message was sent by Alice. 7.3.6.3. Message Authentication Code (MAC) Consider that Bob just received a message. Why should Bob believe the message came from Alice? This means that the message is completely useless. Eve as we talked before, could send a new message to Bob with a hash value to trick him. To resolve this problem, Authentication is introduced. Like encryption, authentication uses a secret key that Alice and Bob both know. We will call this the authentication key (Ka). When Alice sends the message m, the following occurs: 1. Alice and Bob share a secret authentication key Ka. 2. Alice computes a message authentication code, or MAC as a function of both the message m and the authentication key Ka. 3. Alice then sends both the message m and MAC to Bob. 4. Bob will receive both message m and the MAC. 5. Bob re-computes what the MAC value should be using his own copy of the authentication code Ka, and the received message m. 6. Bob checks if the received MAC value equals his computation of MAC. In this way, there is now way that Eve could change the message and send his own hash value, because he does not know what it takes to compute an authentic MAC, as he has no knowledge of the shared secret Ka.
- 26. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 26 of 48 Now Eve wants to modify the message m to a different message m2. Bob will then compute the MAC value as a function of (m2, Ka), and compare it to the received MAC value. But a good MAC function will not give the same result for two different messages, so Bob will recognize that the message is not correct. Eve can still do nasty things. For example, Eve can replay or resend the same messages to Bob or even change the order for messages. To sort this issue, a sequence numbering can be applied to each message, so that Bob can verify that order and uniqueness of incoming messages. 7.3.6.4. MAC modes So how MAC is computed? MAC is a function of a shared secret Ka, and the input message m. Both parties should share a secret authentication key before starting to use MAC. MAC can be computed via encryption or hashing as we will see next. 7.3.6.4.1. Via Encryption (CBC-MAC): Encryption can be used to compute MAC value, like when using CBC encryption. In this block cipher encryption mode, the message is encrypted using CBC mode, and then we throw away all but the last block of cipher text. 7.3.6.4.2. Via Hashing (HMAC) It is so trivial to use hash function to compute the MAC. To do this, you perform the following computation:
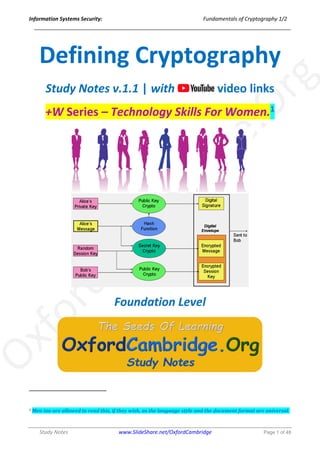
- 27. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 27 of 48 h(Ka XOR a || h(Ka XOR b || m)) XOR = Exclusive OR || = Concatenation h = hashing a,b = padding constants 7.4. Applying Non-repudiation to Cryptography We should be able to figure out how cryptography can be used to prove, with high certainty, that an action or statement is associated with an entity. https://youtu.be/BtP4AGHl6jA 7.4.1. About non-repudiation Non-repudiation is a legal term used to indicate that a statement or a document was signed or made by an individual. And in cryptography, it's a method of ensuring a message was sent or encrypted by a specific entity. The process by which this is done is via a cryptographic digital signature. 7.4.2. Digital signatures Digital signatures are created with a unique private key that gets issued to an entity, such as a user or a computing device. The signature could only have been created by the owner of the private key. Therefore, it's crucial that private keys are kept protected properly in order for this process to be trusted.
- 28. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 28 of 48 7.4.3. Purpose of non-repudiation The purpose of non-repudiation in cryptography is to protect both the sender and the receiver. The sender can verify that they send the message to the correct receiver and the receiver can verify the sender of the message. Depending on the implementation, it can also let the sender know that the message was received. Non-repudiation is usually used for digital documents and e-mail messages. So we can send an e-mail message in our mail program. And there is often a button we can click before we send it to sign the message. 7.4.4. Asymmetric encryption and non-repudiation Asymmetric encryption uses unique public and private key pairs that are issued to either computers or users. Non-repudiation usually comes in the form of having a private key to create a unique signature that gets verified on the other end with a mathematically related public key. Some issues can occur here, such as when a key is exposed or in transition as a key is rotated. Therefore, it's very important that private keys are kept safe, on one hand. On the other hand, public keys which are called public keys because they can be made public to everybody, don't need to be kept safe, unlike the private. 7.4.5. Non-repudiation implemented with digital signatures Non-repudiation is implemented with digital signatures. There can be three digital signature algorithms – DSA, RSA, and ECDSA.
- 29. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 29 of 48 8. Cryptographic Methods 8.1. Using a One-time Pad (OTP) We should be able to appreciate how OTP in cryptography can provide perfect secrecy but, at the same time, has some significant limitations. https://youtu.be/-lEYFSEA4Ng 8.1.1. Understanding One-time Pad A one-time pad is an extremely powerful type of substitution cipher. One-time pads use a different substitution alphabet for each letter of the plaintext message. One-time pads (OTP) when used properly can't be cracked. It's one of the few things in crypto that really can't be broken when implemented correctly. Nevertheless, in practice, one-time pads can have some significant drawbacks. The pad part of the name in one-time pad comes from the original use of pads of paper, where each page of the pad was used for a message, and then ripped off and destroyed. 8.1.1.1. Key has to be as long as the message One is that the key has to be as long as the message that's being sent. The key must also be truly random. Reusing a key significantly compromises the message and that's why it's called a one-time pad in the first place. We should never be reusing a key, because the key must be as big as the message, therefore the exchange of the keys or pads can be difficult. For instance, our one-time pad might consist of a uniquely random series of numbers such as 192837292623 and so on. The message to encrypt might be the text "hello world." Well, we might apply our one-time pad against the text that needs to be encrypted. Bear in mind that the key needs to be as long as the message to be encrypted, then we would end up with our encrypted ciphertext.
- 30. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 30 of 48 8.1.2. Distributing One-Time Keypads is difficult But the distribution of these One-Time Keypads is very difficult. Interception completely compromises the cipher. Interception attacks are sometimes called man-in-the-middle attacks. But, if we're going to be using a truly random key only once, that needs to be known on the other end of a connection. So how do we securely get that to the other side of the connection in the first place? One-time pad cryptography is also referred to as the Vernam cipher. Acquiring a truly random data value for the pad can be difficult. So using any nonrandom source that seems random will not work. 8.2. Describing Substitution Ciphers We should be able to describe and use a substitution cipher and understand the weaknesses that can be exploited by an attacker against these ciphers. https://youtu.be/uL6aEigu9-E 8.2.1. About substitution ciphers A substitution cipher alters elements of plaintext with substitutions and that result is ciphertext. Each plaintext items that are going to be encrypted is compared against a look-up table and then substituted by the value in the look-up table. As an illustration, let's say we wanted to encrypt the text abc. If we have a look-up table whereby a=T and b=L and c=P, this means the abc plaintext, when encrypted, results in TLP as ciphertext. Given the ciphertext or TLP, if we want to decrypt it, we have to have access to the same look-up table that was used to encrypt TLP. As a consequence, we would know then that L=b, P=c, and T=a. Therefore, we could decrypt TLP to its originating plaintext of abc.
- 31. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 31 of 48 8.2.2. Caesar shift The Caesar cipher is named after Julius Caesar who actually used it in some of his correspondence. It's a monoalphabetic substitution cipher, meaning it only uses substitutions from a single alphabet and replaces given letters with another letter that is offset from the original. 8.2.3. Vigenère cipher The Vigenère cipher is a polyalphabetic substitution cipher. This means that it uses more than one alphabet to perform the encryption that results in ciphertext. There are multiple ways to mitigate frequency analysis attacks. Frequency analysis attacks look for patterns that are known within certain languages and alphabets. In English, for example, often the letter E will appear followed by the letter T. 8.2.4. Polyalphabetic ciphers With polyalphabetic ciphers, multiple key spaces are used. Hence, the same element appearing later in a message could and would be substituted with a different ciphertext. Polyalphabetic ciphers can be difficult to attack as long as the text is kept short and the key doesn't get reused. Polygraphic ciphers use larger groups of elements that are used to flatten the frequency distribution. So, for example, we use groupings of items like two or three letter patterns. Although polygraphic ciphers have a much larger key space, some combinations are still more common. For example, the letters "ch" are much more common than "zz." 8.2.5. Advantages of substitution ciphers Some advantages of substitution ciphers are such that they're very easy to create and use. They generally have small keys, therefore are easy to remember. And they're still in use today as parts of more complex encryption algorithms like AES. 8.2.6. Substitution ciphers drawbacks But they do have their drawbacks. Substitution ciphers are vulnerable to frequency analysis. Substitution ciphers usually have a small key space. In this video, we discussed substitution ciphers. 8.3. Using Symmetric Algorithms We should be able to describe and identify the features and use cases for symmetric- key cipher algorithms. https://youtu.be/066z0MLwYdQ
- 32. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 32 of 48 8.3.1. Understanding symmetric algorithms In our everyday language usage symmetry means the same. Therefore, a symmetric algorithm is one that uses the same key for encrypting and decrypting. It's like using a key to lock a door and then later using that same key to unlock the same door. So it's the same key or symmetric key. 8.3.2. Symmetric key algorithms Symmetric key algorithms rely on a “shared secret” encryption key that is distributed to all members who participate in the communications. This key is therefore used by all parties to both encrypt and decrypt messages, so the sender and the receiver both possess a copy of the shared key. The sender encrypts with the shared secret key and the receiver decrypts with it. Symmetric key cryptography can also be called secret key cryptography and private key cryptography. 8.3.3. Symmetric key is a shared secret A symmetric key is a shared secret between entities that need to encrypt and decrypt. Nonetheless, key generation and distribution remains together a major source of weakness. 8.3.3.1. Advantages of symmetric algorithm One of the advantages of a symmetric algorithm is that we have a single key to generate and manage. We also have faster encryption and decryption than with the equivalent strength asymmetric algorithms. Asymmetric algorithms use different, yet mathematically related keys. Another advantage of a symmetric algorithm is that a relatively small key space such as 128 bit can still offer effective security. 8.3.3.2. Drawbacks of symmetric algorithm But there are drawbacks to symmetric algorithms.
- 33. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 33 of 48 One being that everyone shares the exact same key. Everybody knows the key. Another disadvantage is how we securely transport the shared key to everybody in a secured manner in the first instance. Also, we have to think about the fact that keys that are generated from weak entropy sources can affect the key space. Now a weak entropy source means there is a weak source of randomness. Incorrectly implemented algorithms can leave the cipher severely weakened. 8.4. Working with Asymmetric Algorithms We should be able to understand and identify the features and use cases for asymmetric-key cipher algorithms. https://youtu.be/PhZ2rtzJA3s 8.4.1. Notion of asymmetric algorithms Asymmetric key algorithms, also known as public key algorithms, provide a solution to the weaknesses of symmetric key encryption. In such systems, each user has two keys: a public key, which is shared with all users, and a private key, which is kept secret and known only to the user. A constrain: opposite and related keys must be used in tandem to encrypt and decrypt. In other words, if the public key encrypts a message, then only the corresponding private key can decrypt it, and vice versa. Asymmetric cryptography is also called public key cryptography, and it requires the use of two separate yet mathematically related keys – the first of which is the public key. This one is made public to everybody; for instance, is we have to export our public key on our computer to a file. Then, we might give that file to another party where they could import the public key. However, on a larger scale, it would make sense to publish public keys on a centralized directory service or address book. The verification of digital signatures requires that we
- 34. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 34 of 48 have access to the sender's public key whereas encrypting messages would require us to have access to the recipients' public key. The private key needs to be kept private because it uniquely identifies either a device or a user. The private key creates digital signatures and it decrypts messages. Asymmetric algorithms are built on hard-to-solve mathematical problems, such as integer factorization, elliptic curves, and discrete logarithms. 8.4.2. Private key and public key paired together As a result, the mathematical properties make it very difficult to calculate the private key given just the public key. The private key and the public key are paired together but they are not the same – hence asymmetric – but they are mathematically linked. 8.4.3. Usage of asymmetric algorithms Typical asymmetric algorithms include RSA and ElGamal. Common asymmetric use comes in the form of SSL – Secure Sockets Layer – and its successor TLS – Transport Layer Security. These are often used to secure transactions in a web browser but that's not the only place they can be used. GPG as well as PGP also uses asymmetric cryptography. Asymmetric algorithms are also used for key transport and distribution. For illustration, in HTTPS transactions or to establish a VPN tunnel. Digital signatures are also considered asymmetric. 8.4.3.1. Asymmetric algorithms advantages An advantage of asymmetric algorithms is that there is no secret or shared key that we need to exchange with the parties that we want to communicate with securely. We use a user's public key to send a message to that person so that...what happened if we're encrypting a message? The persons or the recipients, in this instance, would use their related private key to decrypt the message. Messages can be digitally signed by the sender to authenticate the sender to the receiver. This is part of public key infrastructure or PKI. Remember, that digital signatures are created by the sender with their private key. 8.4.3.2. Asymmetric algorithms disadvantages Some disadvantages to asymmetric algorithms include the fact that they are slower than symmetric algorithms partially because the key space is larger than it is with symmetric algorithms. In this video, we discussed asymmetric algorithms. 8.5. Hiding Data Using Steganography We should be able to comprehend the use of steganography in encryption products to hide the fact data is even encrypted. https://youtu.be/pkl-eZ9UPIM
- 35. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 35 of 48 8.5.1. About Steganography Steganography is the hiding of data inside of other data, while steganalysis is the study of steganography. With steganography a third-party would know, for instance, that a data exchange is taking place between communicating parties, or that third-party wouldn't know is that there are secret messages embedded within that communication. Encryption is different because with encryption we know that there is a secret message there, but we just can't decrypt this secret message if we don't have the correct decryption key. 8.5.2. A software is needed for steganography On a computer, specialized software is required to hide and then to reveal secret messages embedded in other data. There are also tools that can be used to detect abnormalities in files due to steganography. And these tools would be used by forensic technical experts. 8.5.3. Illustrations of steganography Steganography has been around for a long time and it has many different implementations. For instance, we could hide the encrypted file in the color bits of a JPEG file or we could hide an encrypted file in the noisy bits of an audio or video file. We could even send fake or damaged packets between two network devices, where to an external observer it would simply look like data corruption. Also, steganography can be used with printers, because they can add dots to a printed image that contains a unique identifier for a specific printer. Watermarking images or digital content can also be used for Digital Rights Management. This is used in cases involving anti-piracy. Indeed, we can also embed secret documents or messages within an image or an audio file among other types of files. 8.5.4. Advantages and disadvantages of steganography An advantage of steganography is that encrypted data is hidden, so it won't even gain attention like a regular encrypted file would. Disadvantages of steganography include the fact that it can be hard to hide the data in such a way that it's statistically undetectable because we are modifying the carrier file in which we're embedding our secret message. Moreover, a large source of data in which to embed the hidden data itself might be required. That means then, files might be much larger than they otherwise would be.
- 36. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 36 of 48 8.6. Using One-way Hashes A one-way function is a mathematical operation that easily produces output values for each possible combination of inputs but makes it impossible to retrieve the input values. Public key cryptosystems are all based on some sort of one-way function. We should be able to appreciate the purpose of cryptographic hash functions, and how they can be used in cryptography to provide data integrity. https://youtu.be/KMqgKQI58Zw 8.6.1. Understanding one-way hashes One-way hashes, also called cryptographic hash functions, are used to compute a fixed size representation of variable length input data. The hash value is virtually impossible to return back to its original source data. The value gets computed from a single input called the message. A one-way hashing algorithm then computes a fixed length binary digest, which is sometimes called a message digest or hash. 8.6.2. One-way hashes: critical to many cryptographic systems One-way hashes are critical to many cryptographic systems and implementations used today, including HMACs and digital signatures. One-way hashes generate a digest that is normally unique for any message. Yet, when two or more messages can generate the same digest, this is referred to as a collision and it's rather rare. Even a small change that gets made to a message would resolve in a new message digest, for that reason one-way hashing is often used to detect changes to data. 8.6.3. Common hashing algorithms Some common hashing algorithms include:
- 37. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 37 of 48 Message Digest 2 (MD2) – MD stands for message digest. Message Digest 5 (MD5) – MD stands for message digest. Secure Hash Algorithm (SHA-0, SHA-1, and SHA-2) Hashed Message Authentication Code (HMAC) RIPEMD, Tiger, Whirlpool, and more. 8.6.4. About MD5 common hashing algorithm If we were to look at the MD5 common hashing algorithm, we could see that it uses 64 bits to result in a 128 bit unique digest. One-way hashes though should not be used for encryption because brute force and dictionary attacks can potentially recover data, where the user might guess the original message, such as a password or a credit card number, but using a salt – which is randomized data – can reduce the effectiveness of these types of attacks. But the salt would need to be safely protected. 8.7. Describing Digital Signatures We should be able to explicate digital signature and how it can be used for authentication and non-repudiation. https://youtu.be/MvbLcGr6UEQ 8.7.1. What is digital signature? A digital signature is used by the receiver of a message to confirm that the message came from a particular sender. At one end, the signature gets generated by the sender using a private key. On the other end of the connection, the signature gets verified by the recipient using a mathematically related public key.
- 38. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 38 of 48 8.7.2. What’s digital signature used for? Digital signatures might be used to secure e-mail messages or to secure sensitive documents stored in the document management system. Digital signatures can be used to provide both authentication as well as non-repudiation. 8.7.3. Components of a digital signature Digital signatures use asymmetric and one-way hashing functions and usually consist of three components, including an asymmetric key pair, where one key is kept private and used to sign the message, and the second key is public and is used by the receiver to verify the message. The second component of a digital signature is having an algorithm that can generate a digest of the message. This is a hashing function that takes the original message and the unique private key of the sender to generate a signature for the message. The third component of a digital signature is an algorithm to verify a message and the digest. This is the same hashing function used by the sender. It's the same message, but it's a different key. We verify the signature with a public key. 8.7.4. Advantages of digital signatures An advantage to digital signatures is that the recipient has a reasonable assurance of message authenticity; because only the sender would possess their unique private key. The recipient must have access to the public key to verify the signature. Digital signatures provide better security than with physical documents, which can be intercepted, forged, or altered. 8.7.5. Disadvantages of digital signatures There are disadvantages to digital signatures, and one is key management. In the case of lost or stolen keys, it can take time to replace those keys that are used for digital signatures, which could offer an opportunity for an attacker. On the legal side, not every country has laws or protections for digitally signed messages. 8.7.6. Digital signatures algorithms Examples of digital signature algorithms include RSA, DSA, and ECDSA.
- 39. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 39 of 48 9. Building Blocks of Cryptography 9.1. Distinguishing between Block and Key Sizes We should be able to distinguish the difference between blocks and key sizes as they apply to cipher algorithms. https://youtu.be/OswuM_GwbwE 9.1.1. Block ciphers Block ciphers are designed to work with blocks of data to either be encrypted or decrypted. This data needs to be split into sections that match the block size of the algorithm. The block size is of a fixed value – like 16, 32, 64, or more bits. Then again, because the algorithm would require a block of data to work on, if the input data is less than the block size, then that input data needs to be padded. 9.1.2. Key sizes The key size of an algorithm is also called the key length and is the number of bits that are required for the key used within that cryptographic algorithm. It relates to the strength of the algorithm. Generally speaking, a larger key size means greater strength. 9.1.3. Block algorithms Block algorithms can support multiple key sizes, but usually they have a single block size. 9.1.3.1. Symmetric algorithms Let's take a look at some cases starting with symmetric algorithms. AES supports 128, 192, and 256-bit key sizes whereas DES supports 56-bit keys. 3DES supports a 168-bit key size, but in practice, it's really equivalent to 112 bits. 9.1.3.2. Asymmetric algorithms For asymmetric algorithms, the key sizes will vary. For instance, we might have a 1024- bit key up to a 4096-bit key. A 1024-bit key is about the equivalence of an 80-bit symmetric key.
- 40. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 40 of 48 9.1.4. Comparing algorithm block and key sizes If we were to compare algorithm block and key sizes, we would get an idea of their strength. For instance, with the AES algorithm, the block size is 128 bits; the key sizes are 128, 192, and 256. However, if we were to look – for instance – at DES, its block size is 64 and it has a number of key sizes including 56, 112, 168, and so on. Finally, SHA-2 – the Secure Hash Algorithm – has block sizes of 512 or 1024, and the key sizes range from 224-256-384-512. 9.2. Using Padding We should be able to understand and perform padding operations to data for block ciphers. https://youtu.be/EdICXZOJ42E 9.2.1. About padding Many cryptographic block algorithms require that data be a fixed block length. Nonetheless, some modes of operation that some algorithms can use don't require that data be a fixed block length. On the other hand, for those that data be a fixed block length, padding adds additional data to the end of the message to fit the block size. This means we can end up in encrypted data taking more room than the original message itself. For instance, if we've got a block size of 16, yet our original message is the text "hello world," we're going to need to add some padding beyond the text "hello world" to meet our block size. And there are various ways in which this can be done. 9.2.2. Zero padding With zero padding, sometimes called null padding, all of the padding or the padded bytes are set to a value of zero. Now this should only be used for text-based messages or when we know the message length. With binary data, the 0s can be confused with real data. And this is a problem. For example, if our original message is 101000, to pad it using this method, we would add 0s at the end of our message up to 16 bits.
- 41. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 41 of 48 Now, when the padding gets removed, we have a problem. Because the padding is all 0s, therefore, all of the 0s would be removed, leaving us with only 101. But the problem is the original message was 101000. 9.2.3. Bit padding With bit padding, a single bit is set to a value of 1. And it's added to the end of the message followed by all of the other bits set to a value of 0. Knowing the length of the data or having additional checks for invalid decryption is required. And this can be done with an extra block with fake padding. For illustration, let's say our original message is 101001. With bit padding, a binary 1 is added after our original message followed by binary 0s to meet the block size. No padding will be required if we have a message that is already 16 bits long and that's our block size. But assume that the last two binary digits are 10. This can be difficult because that looks like it's padding that needs to be removed when it's actually part of the original message. However, if we know the length of the original data, then we wouldn't confuse that with padding because we would know the entire message was 16 bits long. 9.2.4. Byte padding With the byte padding mechanism – otherwise called PKCS#7 – we work with bytes rather than individual bits. Byte padding calculates the number of padding bytes that are required and fills the last bytes with this value. Hence, the last value will be less than the block length. 9.2.5. Byte padding illustrated 9.2.5.1. Example 1 As an illustration, let's say our original message is the alphabetic characters A through to and including K. However we must pad it up to 16 bytes. Thus we're missing five placeholders. Therefore, with byte padding, 5 is the value that would be used for padding. Indeed, in this example, the last 5s aren't the ASCII variation of 5, but rather the binary representation of the number 5. With ISO 10126, it calculates the number of padding bytes and puts this number in the last byte with random bytes filling in the rest of the empty spaces. With the data ending on the block size boundary depending on the implementation of the algorithm, an extra block may be required.
- 42. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 42 of 48 9.2.5.2. Example 2 To illustrate again, let's say for our message we've got A through to K inclusive which needs to be padded once again to 16 bytes. In accordance with ISO 10126, we've got five placeholders. Consequently, a value of 5 is put in as the last byte. Thus, between the message and the last byte, we have a series of random bytes. Then, let's say we've got a 16-bit block size and our binary message ends with 11. Since the last byte in this is 11, this would remove 11 characters of padding which really is part of the original message. Next, ANSI X.923 calculates the number of padding bytes and puts this number as the last byte of padding with 0s filling in the empty spaces. The last byte gets checked, and if it's less than the block size, it checks for the right number of 0s. If it's correct, therefor the padding is removed; otherwise, it's just data that ended right on the block boundary. 9.2.5.3. Example 2 For instance, if our original message once again consists of the letters A through to and including K, then we must pad it up to 16 bytes. With ANSI X.923, we've got five placeholders that must be padded, which means the value of 5 is put as the last byte. And then we've got 0s between the original message and the last byte. 9.3. Formatting the Output We should be able to know how to encode encrypted data for easier storage or transport. https://youtu.be/DQ-RCh0hZxQ 9.3.1. Understanding text encoding Text encoding is used to convert raw binary output into a text-friendly representation. Sometimes this is required by some applications or for readability. Encoding, however, does not protect data – that's what encryption is for. Both encryption and encoding are reversible whereas hashing values are not. For instance, if we possess the correct encryption key, we can decrypt back to the original plaintext.
- 43. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 43 of 48 9.3.2. Text encoding format The most common text encoding format for cryptographic operations is hex, which stands for hexadecimal or base 16 where we use characters 0 through to 9 as well as A through to F where A would equal 10, B would equal to 11, and so on. With hexadecimal, each byte is converted into two alphanumeric characters. For instance, 255 in decimal would equate to FF in hexadecimal. "Hello World" would encode to 48 65 6C 6C and so on. Encrypted or hashed raw data can't be easily stored, for example in a database, or even transferred using e-mail. ASCII control characters – those with decimal values less than 32 – and ANSI characters from 128 to 255 may display as junk characters or not be displayed at all. Thus, text encoding solves these types of issues. There are many encoding formats available – some common ones include base16, base32, base64, and uuencoding. These usually make the text longer than the original raw data. However, when encoded, it's still shorter than the hexadecimal equivalent which approximately doubles the size. 9.4. Using Nonces and the Initialization Vector We should be able to describe the purpose of an initialization vector for a cipher algorithm and how Nonces can be used to protect small datasets. https://youtu.be/3ZlIHKABKbg 9.4.1. About initialization vectors (IV) Initialization vectors are also called starting variables, nonces, or IVs. And an IV is used when encrypting or decrypting multiple blocks of data. An IV is normally used on the first block to be encrypted. It is a random fixed-length string similar to a key. However, it doesn't need to be protected like the key itself does. For block ciphers, the IV is the same length as the block length. Therefore, the primary purpose of an IV is to add randomization to each block being encrypted to prevent
- 44. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 44 of 48 patterns from showing up in the encrypted data. To illustrate, let's say we're encrypting the text ABCABC without the use of an IV. ABCABC then might encrypt to A3E54EA3E54E. As such, this isn't good because there is a repeatable pattern. 9.4.2. About Nonces Cryptography often gains strength by adding randomness to the encryption process. One method by which this is accomplished is through the use of a nonce. A nonce is a random number that acts as a placeholder variable in mathematical functions. When the function is executed, the nonce is replaced with a random number generated at the moment of processing for one-time use. The nonce must be a unique number each time it is used. If we were to add an IV, or initialization vector, then the encrypted data would look more random. This way there wouldn't be a repeatable pattern. The initialization vector can also be unique for each block encrypted. In this case, it's referred to as a nonce. Nonces are integers and may increment like a counter for each block of data. They are commonly used for disk encryption where the nonce is the sector of the disk. Nonetheless, it exists not so good implementations of IVs notably with Wi-Fi encryption WEP. WEP or Wired Equivalent Privacy uses IVs. However, the problem is that the IV is only 24 bits long. Consequently there are not that many variations, and it’s pretty much guaranteed to have a repeatable pattern given enough traffic. 9.5. Identifying and Using Entropy We should be able to comprehend how entropy is used in generating random numbers and how that entropy is critical to the strength of a cryptographic key. https://youtu.be/-fgbPWUeF9c 9.5.1. Understanding entropy A cryptographic cipher is only as strong as its key, which is only as strong as the entropy that was used to create it. But what is entropy? Entropy is randomness and the more of it, the stronger the key. Therefore, one could say entropy adds disorder and confusion to data.
- 45. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 45 of 48 9.5.2. Weaknesses of using passwords However, using passwords to generate keys presents a weakness because, rather than attacking the cipher or the key an attacker would find it easier to go for the password that was used to create the key. Effectively, this has reduced the key space from the key size all the way down to the password strength. We should be using multiple sources of randomness to generate keys that are effectively secure. As a weakness in any source of entropy reduces the strength of the protected data because the key that protected the data is derived from the source of entropy. Using just a cipher and a key is not good enough if the key is not truly random. 9.5.3. Using pseudorandom number generators (PRNGs) Most operating systems contain a random number generator that uses operating system events to gather entropy or randomness from various sources such as mouse movements, keyboard typing, network communications, memory usage, audio noise, disk drive timings, and so on. These systems can use a pseudorandom number generator, often called a PRNG. Such randomness generators use a seed and cryptographic algorithms to generate a sequence of data that approximates the properties of real random data. 9.6. How cryptographic keys are generated? We should be able to recognize the generating of keys and how the key strength is critical to cryptographic ciphers. https://youtu.be/sxcGHUqHxbg 9.6.1. Types of cryptographic keys For most cryptography, there are two types of keys. 9.6.1.1. Symmetric key Firstly, we have a symmetric key, which is a single shared or secret key. All communicating parties that wish to communicate in a secured manner must have knowledge of this secret key. The problem is that the key needs to be safely distributed to communicating parties in the first place. Symmetric keys are often used with file encryption and VPN tunnel establishment to name just a few uses.
- 46. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 46 of 48 9.6.1.2. Asymmetric key Secondly, there are asymmetric keys which are mathematically pair of related public and private key. The public key can be made available to everybody, but the private key must be available only to the owner. Asymmetric keys are used with digital signatures for documents or e-mail messages as well as for e-mail message encryption. 9.6.2. Generating keys Key generation can occur within an operating system. 9.6.2.1. In Linux For instance, in Linux, we can use the /dev/random device to generate keys. We could also use the ssh-keygen command to generate keys used for SSH authentication. Since SSH allows Linux administrators to remotely connect over the network to the host for command line administration. 9.6.2.2. In Linux Microsoft Windows Regarding Windows, in PowerShell, we could use the System.Security.Cryptography provider to generate keys. 9.6.2.2.1. Using PKI Certificate Authorities (CA) The major strength of public key encryption is its ability to facilitate communication between parties previously unknown to each other. This is made possible by the Public Key Infrastructure (PKI) hierarchy of trust relationships. These trusts permit combining asymmetric cryptography with symmetric cryptography along with hashing and digital certificates, giving us hybrid cryptography. A PKI Certificate Authority could be used to generate keys as well. That means we could either have an internal Certificate Authority or have keys generated from a trusted third- party Certificate Authority. Either way, the Certificate Authority (CA) generates PKI certificates, which are also called X.509 certificates. A unique public and private key pair would be issued to each entity, such as a user or a computer. In addition, the public and private key pair will be stored within the certificate. The keys in the certificate are mathematically related to one another.
- 47. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 47 of 48 9.6.2.3. Asymmetric keys creation How asymmetric keys get created? First – two large prime numbers must be chosen. For illustration purpose, they are being denoted as p and q. Next, we must calculate a value, which we'll call n where n equals p multiplied by q (n = p x q). The idea is that prime numbers have no discernible pattern. Therefore, when we build keys from prime numbers, we have a stronger key. Consequently, we get a stronger encryption.
- 48. Information Systems Security: Fundamentals of Cryptography 1/2 ______________________________________________________________________________ Study Notes www.SlideShare.net/OxfordCambridge Page 48 of 48 10. Summary Cryptographers and cryptanalysts are in a never-ending race to develop more secure cryptosystems and advanced cryptanalytic techniques designed to circumvent those systems. We were exposed to the basic cryptography concepts, and explored a variety of private key cryptosystems. Also we were introduced to the basic principles behind both private (symmetric) and public (asymmetric) key cryptography. We learned that symmetric key cryptosystems require both communicating parties to have the same shared secret key, creating the problem of secure key distribution. We also learned that asymmetric cryptosystems avoid this hurdle by using pairs of public and private keys to facilitate secure communication without the overhead of complex key distribution systems.
