Medical examiner’s preliminary report pt.1
•Download as PPTX, PDF•
1 like•459 views
Report
Share
Report
Share
More Related Content
Viewers also liked
Viewers also liked (13)
More from Office8
More from Office8 (17)
Recently uploaded
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptxnull - The Open Security Community
Recently uploaded (20)
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Artificial intelligence in the post-deep learning era

Artificial intelligence in the post-deep learning era
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx
Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget

Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget
Medical examiner’s preliminary report pt.1
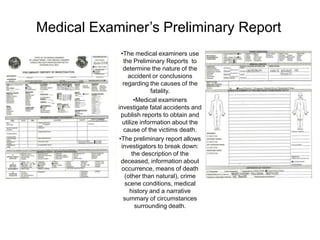
- 1. Medical Examiner’s Preliminary Report •The medical examiners use the Preliminary Reports to determine the nature of the accident or conclusions regarding the causes of the fatality. •Medical examiners investigate fatal accidents and publish reports to obtain and utilize information about the cause of the victims death. •The preliminary report allows investigators to break down: the description of the deceased, information about occurrence, means of death (other than natural), crime scene conditions, medical history and a narrative summary of circumstances surrounding death.
