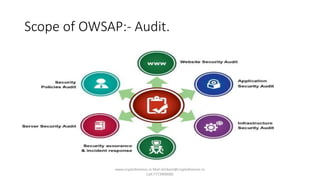
The document discusses an OWASP meetup on application security topics. It summarizes key areas like the top 10 security risks, cyber laws in India and internationally, governing bodies in India, and how application security maps to compliance standards like HIPAA and PCI DSS. It also provides an overview of Rapid7 solutions that can help test and remediate vulnerabilities related to firewalls, passwords, encryption, and application security best practices.