Executive presentation3
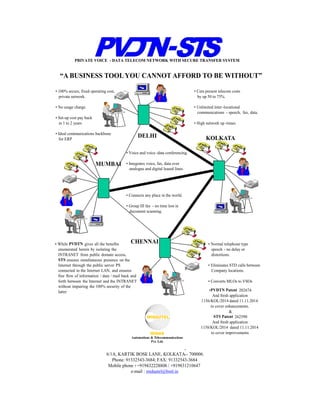
- 1. “A BUSINESS TOOL YOU CANNOT AFFORD TO BE WITHOUT” • 100% secure, fixed operating cost, private network. • No usage charge. • Set-up cost pay back in 1 to 2 years • Ideal communications backbone for ERP • Cuts present telecom costs by up 50 to 75%. • Unlimited inter -locational communications - speech, fax, data. • High network up -times. DELHI MUMBAI KOLKATA CHENNAI • Voice and voice -data conferencing. • Integrates voice, fax, data over analogue and digital leased lines. • Connects any place in the world. • Group III fax - no time lost in document scanning. • While PVDTN gives all the benefits enumerated herein by isolating the INTRANET from public domain access, STS ensures simultaneous presence on the Internet through the public server PS connected to the Internet LAN, and ensures free flow of information / data / mail back and forth between the Internet and the INTRANET without impairing the 100% security of the latter • Normal telephone type speech - no delay or distortions. • Eliminates STD calls between Company locations. • Converts MLOs to VSOs •PVDTN Patent 202674 And fresh application 1156/KOL/2014 dated 11.11.2014 to cover enhancements. & STS Patent 262590 And fresh application 1158/KOL/2014 dated 11.11.2014 to cover improvements - - - - PRIVATE VOICE - DATA TELECOM NETWORK WITH SECURE TRANSFER SYSTEM 6/1A, KARTIK BOSE LANE, KOLKATA - 700006. Phone: 91332543-3684; FAX: 91332543-3684 Mobile phone : +919432228808 / +919831210647 e-mail : midautel@bsnl.in
- 2. CYBER SECURITY – PRESENT MALAISE 1. All the problems with cyber security in the world due to 2. Catching the bull by the tail and running after it. 3. We let all the muck in and then try and detect and clean it.
- 3. THE SOLUTION 4. The only way to ensure 100% security of an organisation’s internal databases and WAN computing is a. To catch the bull by the horns and lock it out of the internal network. b. In other words isolate the INTRANET from any public domain access at LAN / MAN / WAN levels. c. MAN / WAN isolation shown in PVDTN WAN sketches of Figs. 1 and 2. d. Fig. 3 shows the separation at LAN level
- 4. IPPN SPLITTER pSTN IPPN SPLITTER pSTN + +PVDTN = NODE 2 NODE 1 PVDTN p2p leased line Circuit Switched pSTN (private switched telephone network routed by EPAXs at each location Packet Switched IPPN (IP private network) routed by data routers at each location X Y X+Y X+Y MAX (X,Y) PVDTN WAN Fig. 2 Fig.1
- 5. INTERNETPVDTN WAN IBN 2IBN 1 INTRANET LAN INTERNET LAN STS SS OD 2 SS OD 1 SSA Fig. 3 PROPOSED METHOD OF INTERNET CONNECTIVITY LAN Nodes VDS DB2 CS IS PSDB1 VDS CS – Company Communications Server PS – Company Web or Public Server IS – Intermediate Server which relays information / data / mail back and forth Between CS & PS. SSA – Automatic Secure Switch which connects IS to INTRANET and Internet LAN buses alternately in preset (adjustable) time. DB1, DB2 – Company’s internal databases. IBN1, IBN2 – Internet Browsing Nodes SSOD1, SSOD2 – On-demand Secure Switch. STS – Total Secure transfer system comprising of CS, IS, PS and SSA
- 6. ORGANISATIONS PRESENCE ON INTERNET 5. All organisations need presence on the Internet. 6. For this STS (secure transfer system) developed and patented. 7. For free flow of information / data / mail back and forth between the Internet and the INTRANET, automatically. 8. Without impairing the security of the INTRANET.
- 7. STS (SECURE TRANSFER SYSTEM) 9. The STS comprises of a. Company communications server (CS) connected to the INTRANET LAN b. The Company Web Server or public server (PS) connected to the Internet LAN c. The Intermediate or relay server (IS) connected to the secure switch (SS). d. The SS is a 3 position, electro-mechanical, microprocessor driven, RJ 45 switch which connects the IS either to the INTRANET or Internet alternately. e. Never to both together. f. Switch cycle periodicity may be set from 500 milli seconds upwards. g. SS designed developed and manufactured for MIDAUTEL exclusively. h. Covered by STS letter of patent 262590.
- 8. EXCHANGE OF INFORMATION / DATA / MAIL BETWEEN INTRANET & INTERNET 10. Information / data / mail transferred between two networks by alternate two-way synch between IS and CS, and IS and PS 11. All computer nodes in INTRANET LAN receive and send internal and external from and to the Company mail server (CMS). 12. External mail is routed via the STS and the Internet mail gateway (IMG) residing in the PS.
- 9. INTERNET BROWSING NODEs (IBNs) 13. Employees who need to browse the Internet are provided with Internet Browsing Nodes IBNs) comprising a. A switchable thin client with on-demand switching software embedded with the thin OS b. A SS (secure switch) operated by the on- demand switching software. c. Two VMs, one in the VDS (virtual desktop server) connected to the INTRANET LAN and one in the VDS connected to the Internet LAN. d. IBN users will work with the VMs on the INTRANET and Internet LANs. e. Hence two networks are kept separate. f. Obviates internal (mole) threats. g. See Fig. 3
- 10. ACCESS BY FIELD OFFICERS FROM MOBILE PHONES 1. The Company Web site will have two types of pages a. Read only - accessible to people in the public domain for all the publishable information they carry. b. Interactive – accessible to those with registered email IDs and passwords, and with registered mobile numbers which will receive OTP for access c. The field officers will have to leave their inputs on these interactive pages for onward transmission to the internal network via the STS system. They will not get direct access to the internal network from the field but via the Web server connected top the Internet. d. The answers they want from the Company will either be relayed to the interactive pages or via mail in the registered email ID.
- 11. PROTECTION AGAINST MALWARE SENT VIA EMAIL 1. Any one can send a mail to the Company mail ID containing malware. 2. To protect against this the IS (intermediate or relay server) is provided with anti-Malware software in addition with the anti-virus software. 3. The former displays the registry files and the CISO / and his team will be on constant watch for any suspicious files which would be promptly deleted. 4. IS – the only route via which such malware can get into the network during the two-way synch with PS and CS in the STS system. 5. Malware detected and eliminated with the help of the anti-malware software. 6. This activity of CISO / team restricted to Central location of the organisation or at best also in the DR (disaster recovery) site which will also have a STS system.
- 12. DEMONSTRATION OF CUSTOMISABLE STS EXCHANGE SOFTWARE 1. The STS exchange software depends on specific needs of each organisation and is custom built. 2. This can be demonstrated at the Organisation’s premises in a parallel demo site after getting the inputs from the CIO / team. 3. We will need three servers (CS, IS, PS) of appropriate size to suit the need of the organisation, and also a Secure Switch (SS). 4. To demo the typical IBN function we will need two high end PCs to act as the VDSs at the INTRANET and Internet LAN switches, each with two VMs (virtual machines), and two switchable thin clients each comprising a. One SS b. One switchable thin client with on- demand switching software embedded with the thin OS 5. The customised software developer will roll out the working model on successful completion of the demo. 6. The Organisation will be free to employ ethical hackers to hack through the STS system.
- 13. BENEFITS TO USERS 1. Ensures 100% security of internal databases, and WAN computing 2. Saves 50 to 75% of present telecom costs 3. Saves a substantial portion of inter-locational travelling costs through multiple simultaneous NET meetings for different work groups with people from their own work places at a moment’s notice, using a. Voice conferencing b. Voice-data conferencing 4. Smartens up company operations 5. The cost of re-engineering the present network can be recovered from the savings in telecom and travelling costs in 1 to 3 years. The more the communications the quicker the payback. 6. There is also an immeasurable saving from ensuring 100% security of internal databases and WAN computing – which could run into Crores INR – by ensuring the Company / Organisation functions without any data breaches
