More Related Content
Similar to GOV16_INFOGRAPHIC_ATT_P (1).PDF
Similar to GOV16_INFOGRAPHIC_ATT_P (1).PDF (20)
GOV16_INFOGRAPHIC_ATT_P (1).PDF
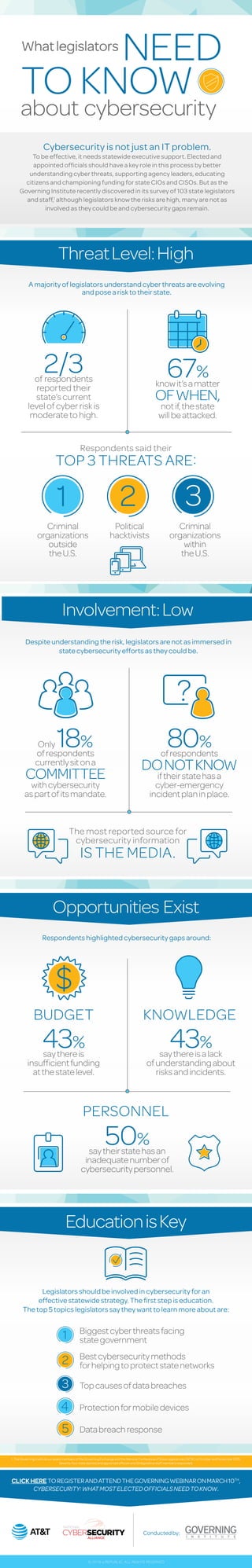
- 1. CybersecurityisnotjustanITproblem.
Tobeeffective,itneedsstatewideexecutivesupport.Electedand
appointedofficialsshould haveakey rolein this processby better
understandingcyberthreats,supportingagency leaders,educating
citizensandchampioningfundingfor stateCIOsandCISOs.Butasthe
GoverningInstituterecentlydiscoveredin its survey of 103statelegislators
andstaff,1
althoughlegislatorsknowtherisksarehigh,many arenotas
involvedastheycould beandcybersecurity gapsremain.
Whatlegislators
NEED
TOKNOW
about cybersecurity
ThreatLevel:High
Involvement:Low
Opportunities Exist
EducationisKey
2/3of respondents
reported their
state’scurrent
levelofcyberriskis
moderatetohigh.
Only18%
ofrespondents
currentlysitona
COMMITTEE
withcybersecurity
aspartofitsmandate.
Criminal
organizations
outside
theU.S.
Political
hacktivists
Criminal
organizations
within
theU.S.
Respondents said their
TOP 3 THREATS ARE:
PERSONNEL
The most reported source for
cybersecurity information
IS THE MEDIA.
Amajorityoflegislatorsunderstandcyberthreatsareevolving
andposearisktotheirstate.
Despiteunderstandingtherisk,legislatorsarenotasimmersedin
statecybersecurityeffortsastheycouldbe.
Legislatorsshouldbeinvolvedincybersecurityforan
effectivestatewidestrategy.Thefirststepiseducation.
Thetop5topicslegislatorssaytheywanttolearnmoreaboutare:
Respondentshighlightedcybersecuritygapsaround:
67%
knowit’samatter
OFWHEN,
notif,thestate
willbeattacked.
80%
ofrespondents
DONOTKNOW
iftheirstatehasa
cyber-emergency
incidentplaninplace.
43%
saythereis
insufficientfunding
atthestatelevel.
43%
saythereisalack
ofunderstandingabout
risksandincidents.
50%
saytheirstatehasan
inadequatenumberof
cybersecuritypersonnel.
?
BUDGET KNOWLEDGE
Biggestcyberthreatsfacing
stategovernment
Bestcybersecuritymethods
forhelpingtoprotectstatenetworks
Topcausesofdatabreaches
Protectionformobiledevices
Databreachresponse
Conductedby:
© 2016 e.REPUBLIC. ALL RIGHTS RESERVED
CLICKHERETOREGISTERANDATTENDTHEGOVERNINGWEBINARONMARCH10TH
,
CYBERSECURITY:WHATMOSTELECTEDOFFICIALSNEEDTOKNOW.
1.TheGoverningInstitutesurveyedmembersoftheGoverningExchangeandtheNationalConferenceofStateLegislatures(NCSL)inOctoberandNovember2015.
Seventy-fourstateelectedandappointedofficialsand29legislativestaffmembersresponded.