KTN ran a collaborators' workshop on 26 September 2019 in London to explain more about the Digital Security by Design Challenge announced by the government.
The Digital Security by Design challenge has been recently announced by the Department for Business, Energy & Industrial Strategy (BEIS). This challenge, amounting to £70 million of government funding over 5 years, was delivered by UK Research and Innovation (UKRI) through the Industrial Strategy Challenge Fund (ISCF).
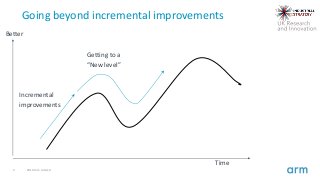
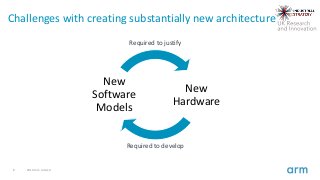
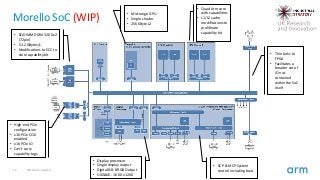
This Collaborators' Workshop provides an opportunity to hear more details of the challenge and forthcoming competitions.
A Scoping Workshop for this challenge was held on 30th May: http://ow.ly/oz6230pHlGl
Find out more about the Defence and Security Interest Group at https://ktn-uk.co.uk/interests/defence-security
Join the Defence and Security Interest Group at https://www.linkedin.com/groups/8584397 or Follow KTN_UK Defence group on Twitter https://twitter.com/KTNUK_Defence