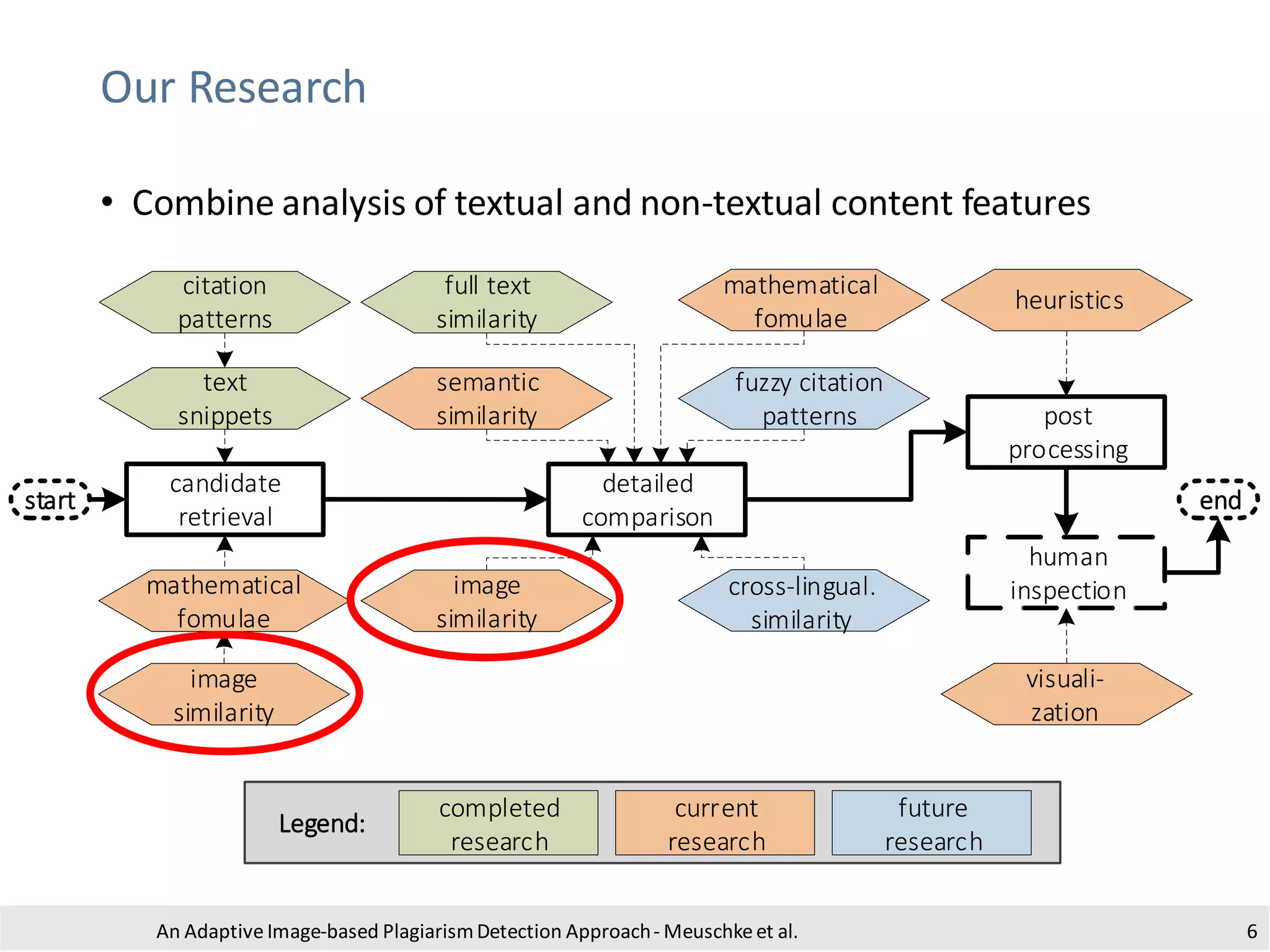
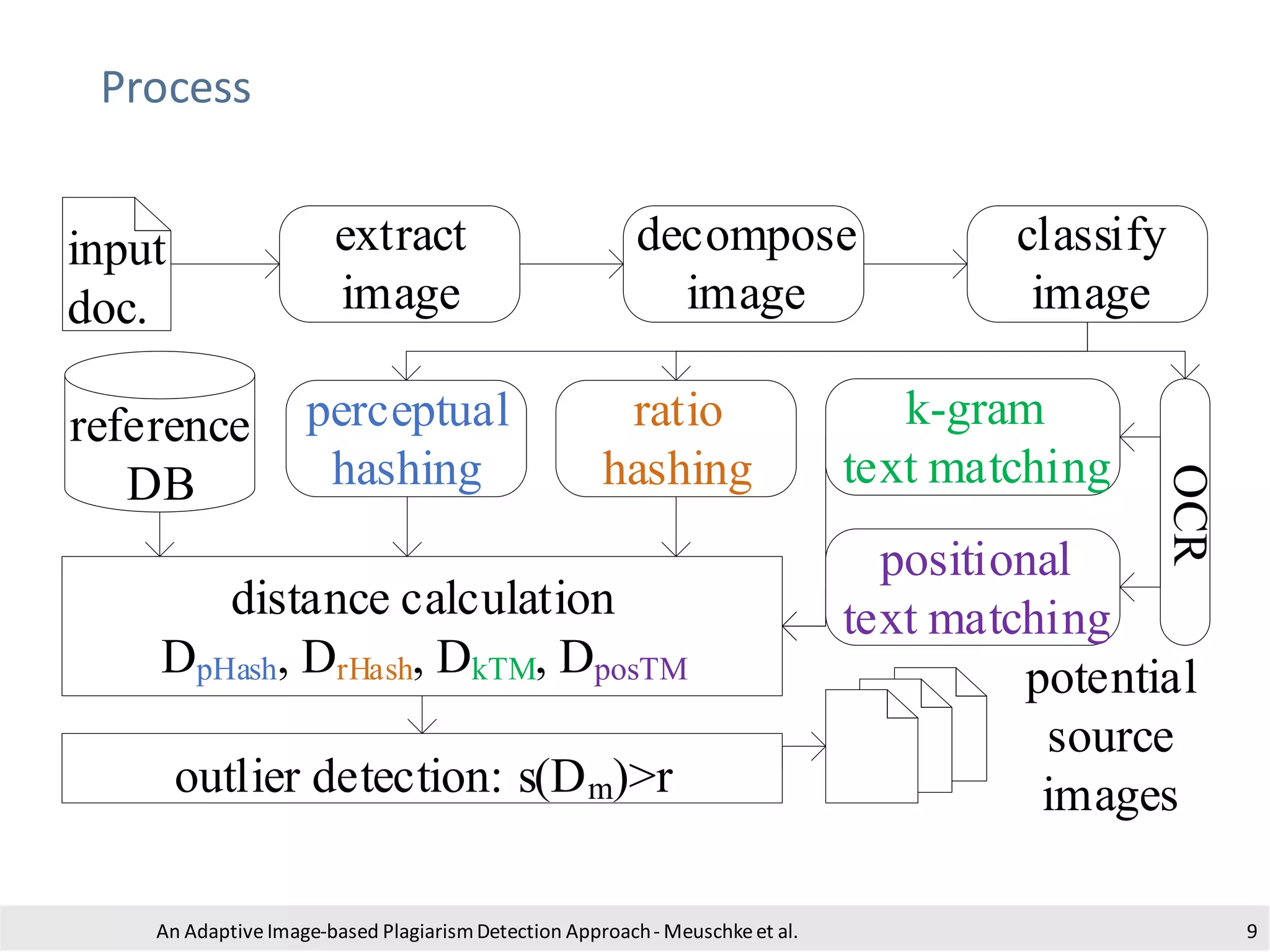
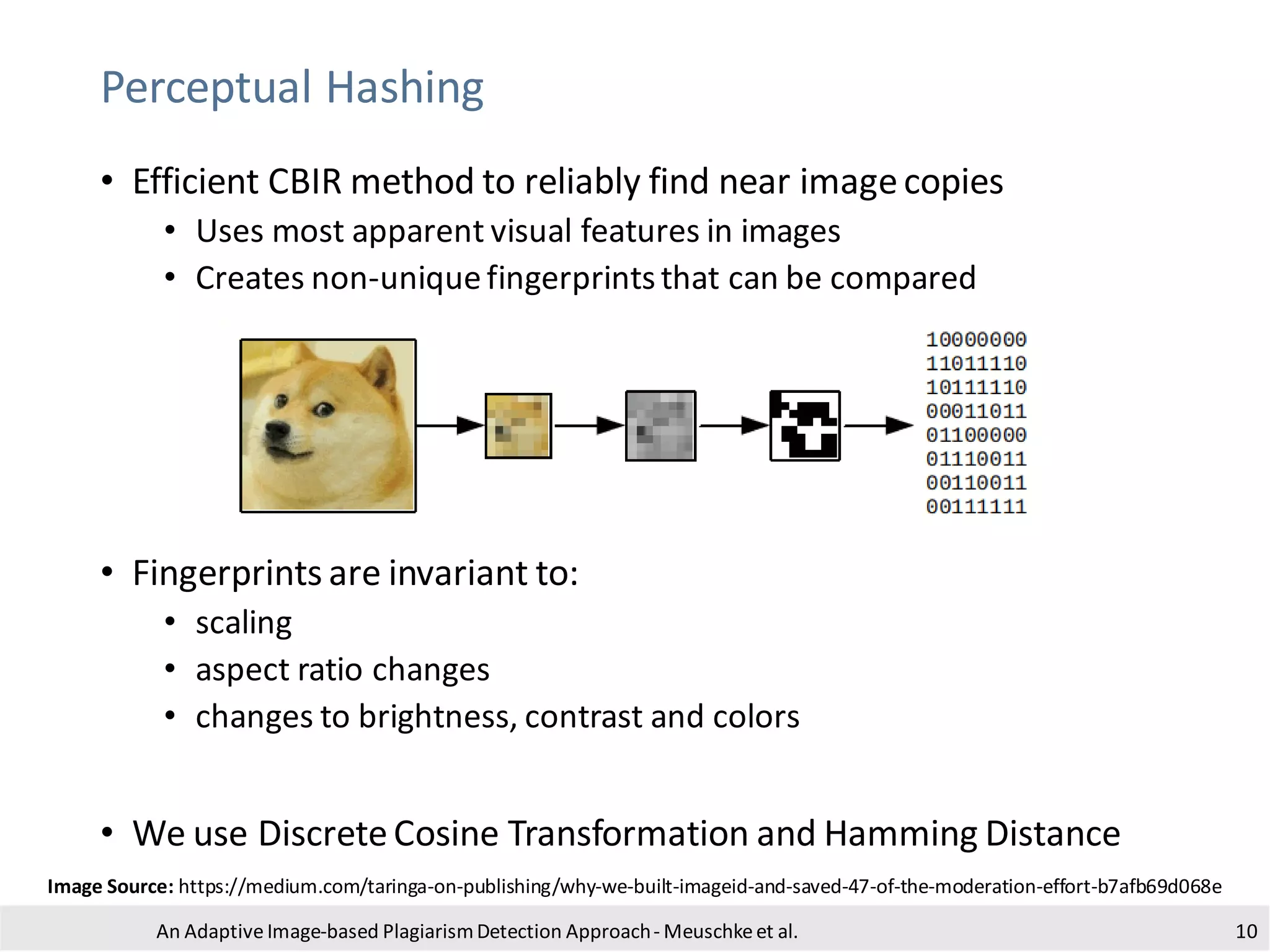
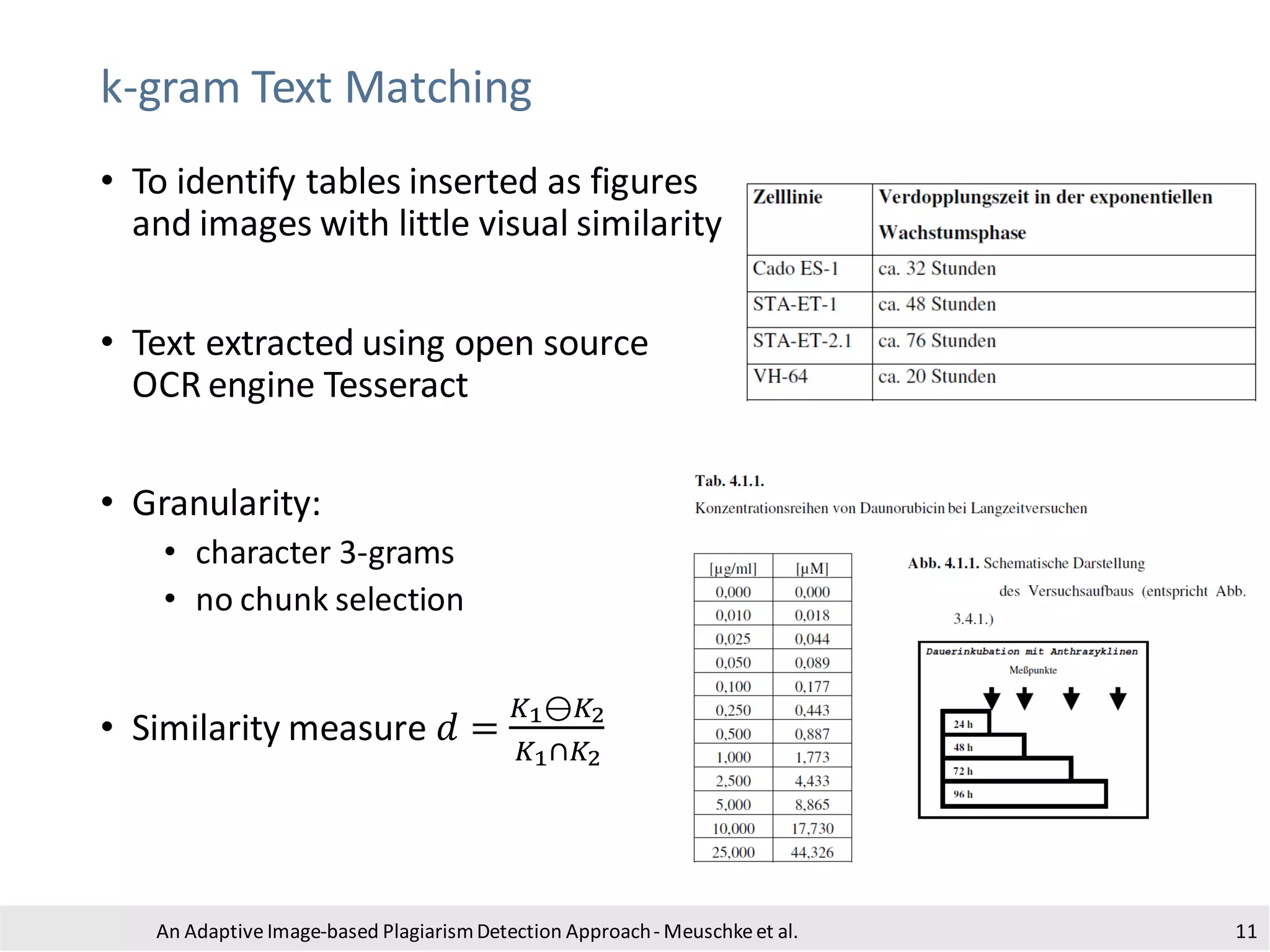
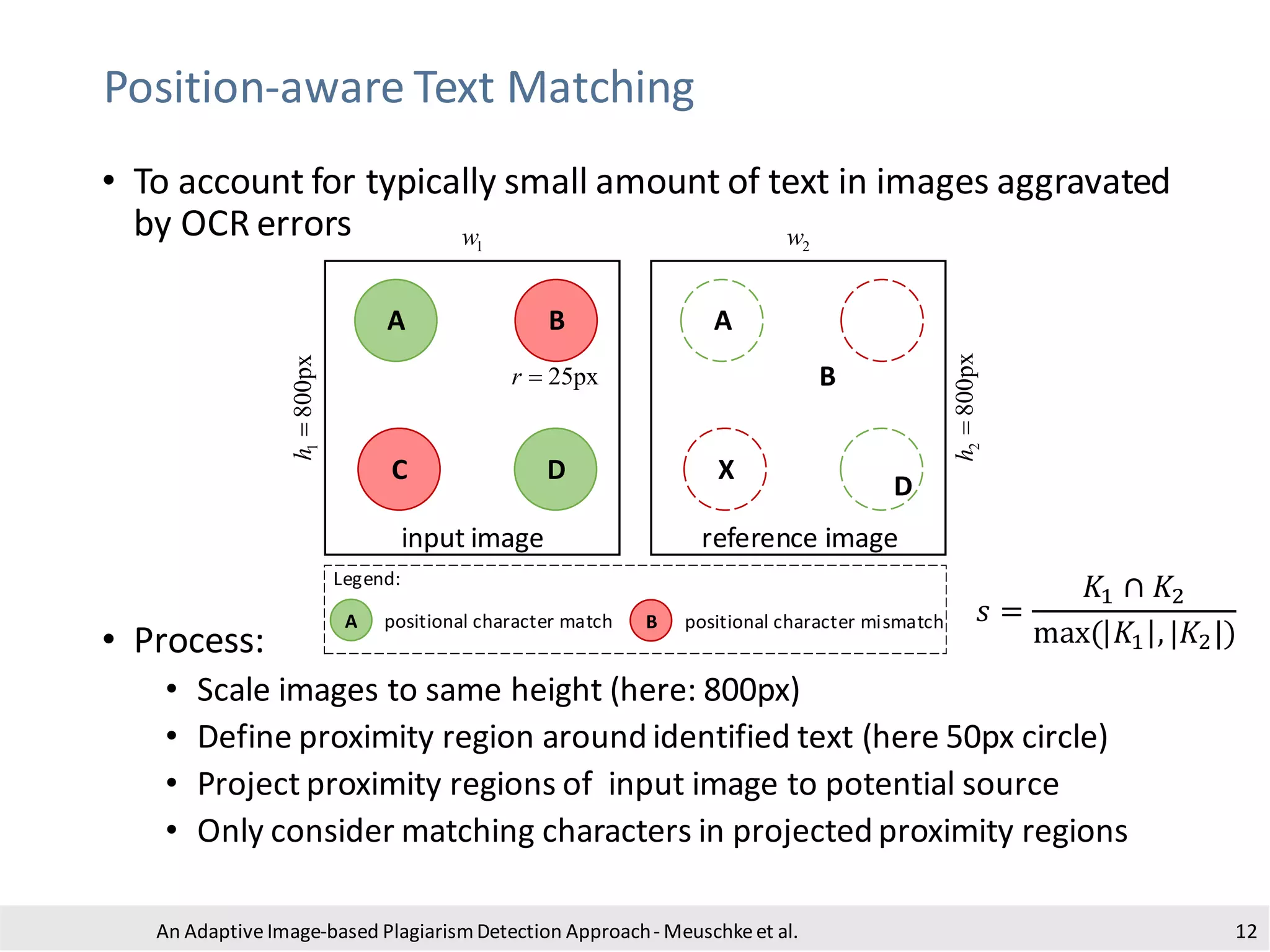
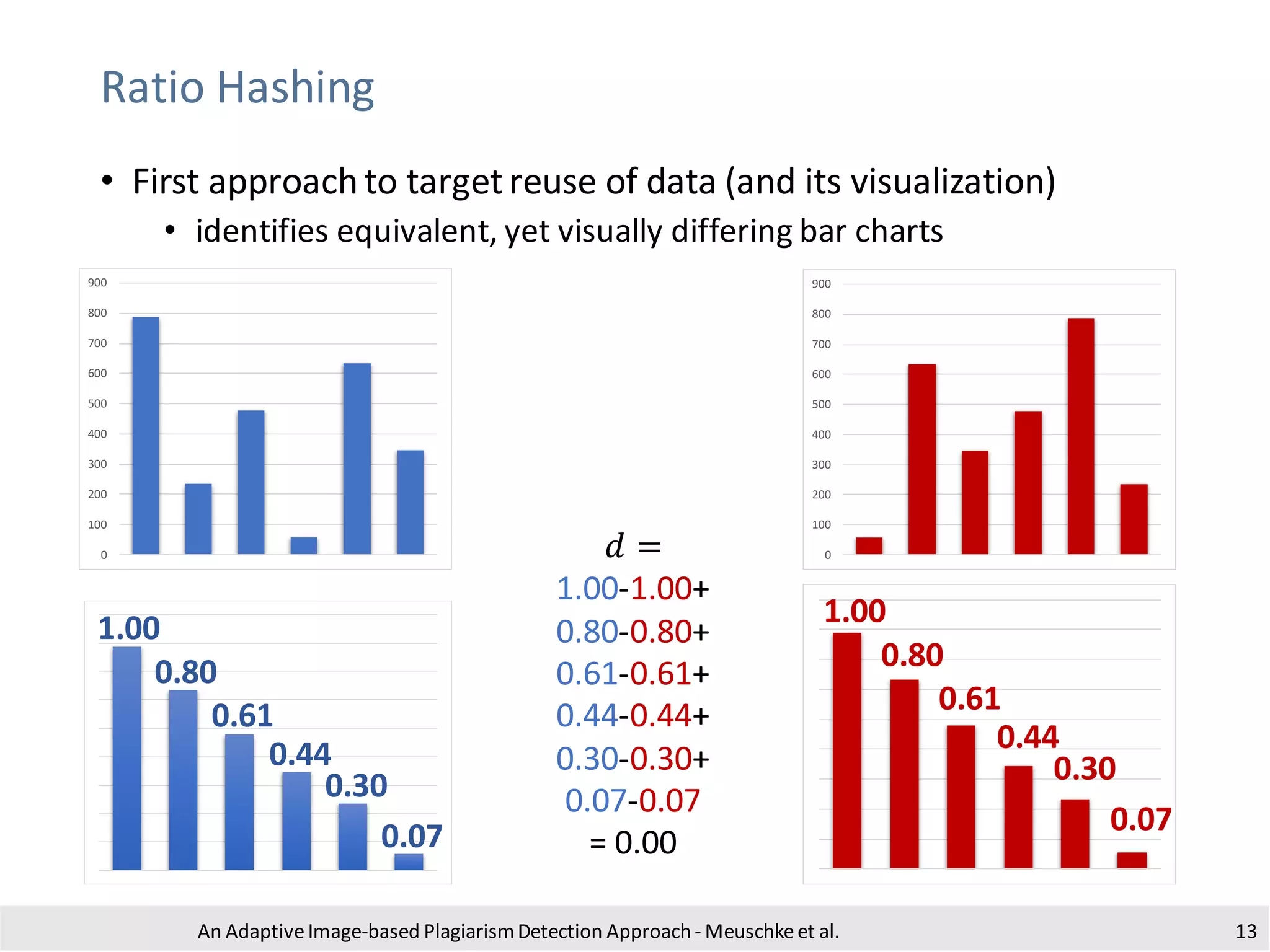
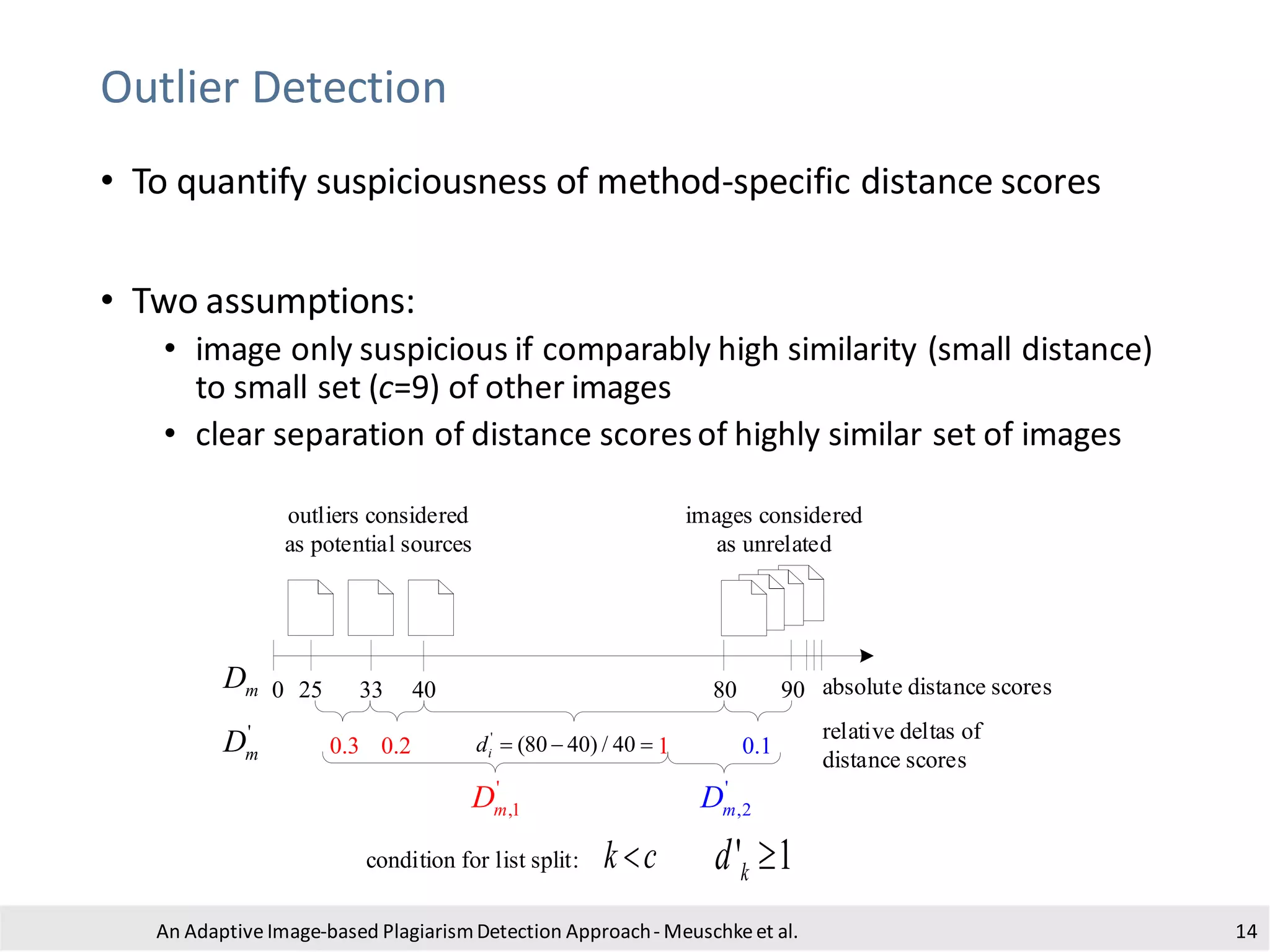
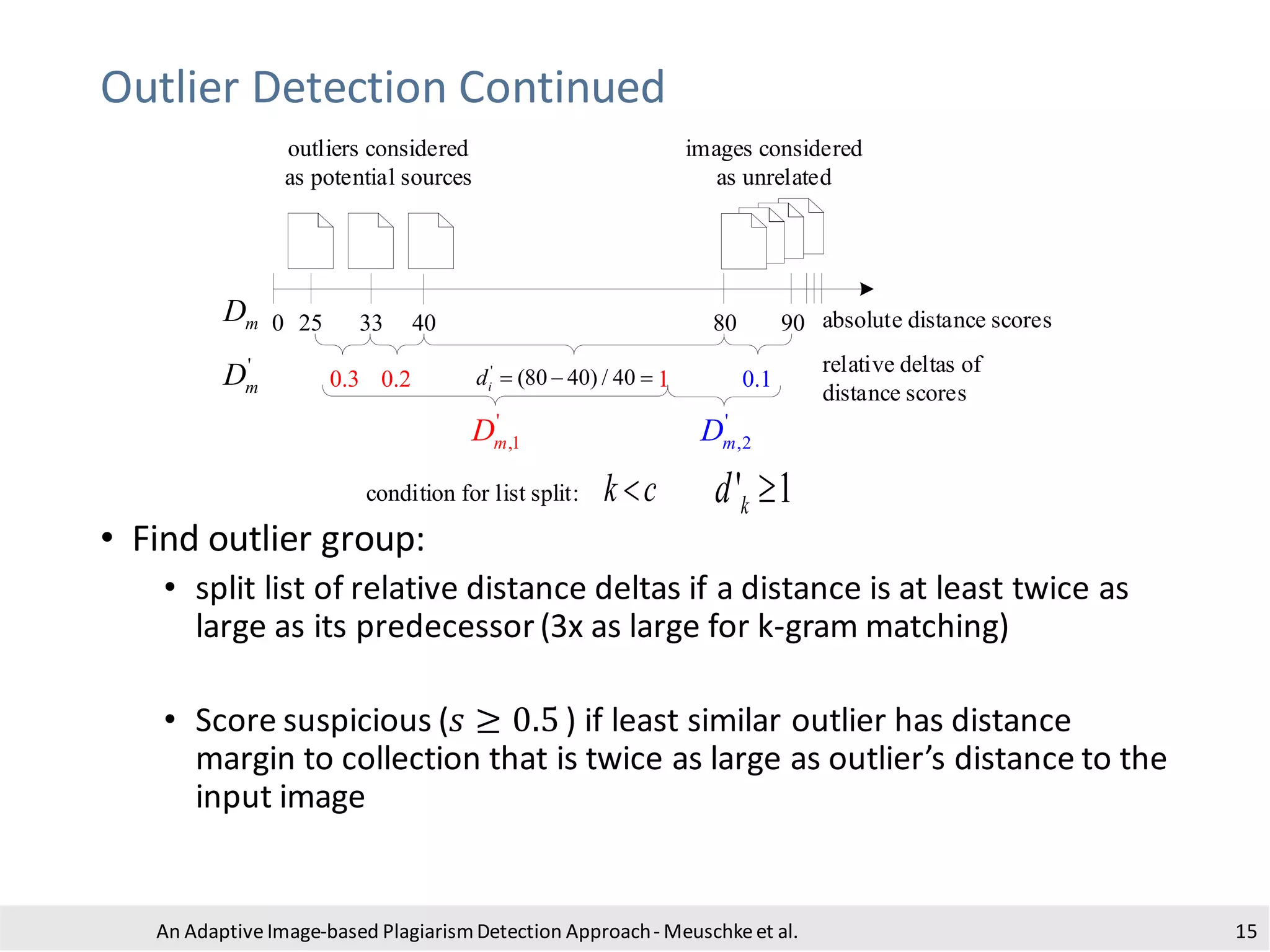
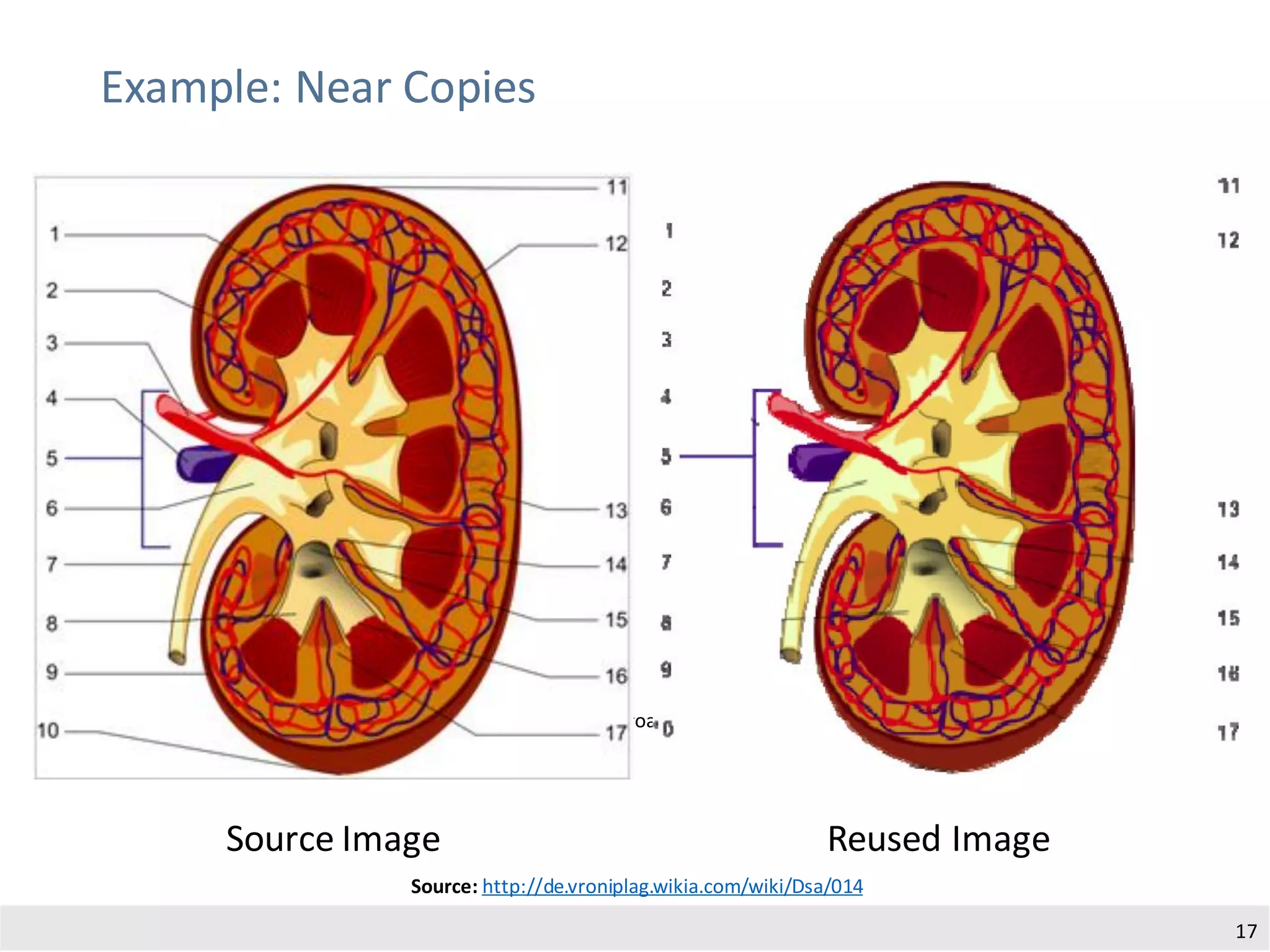
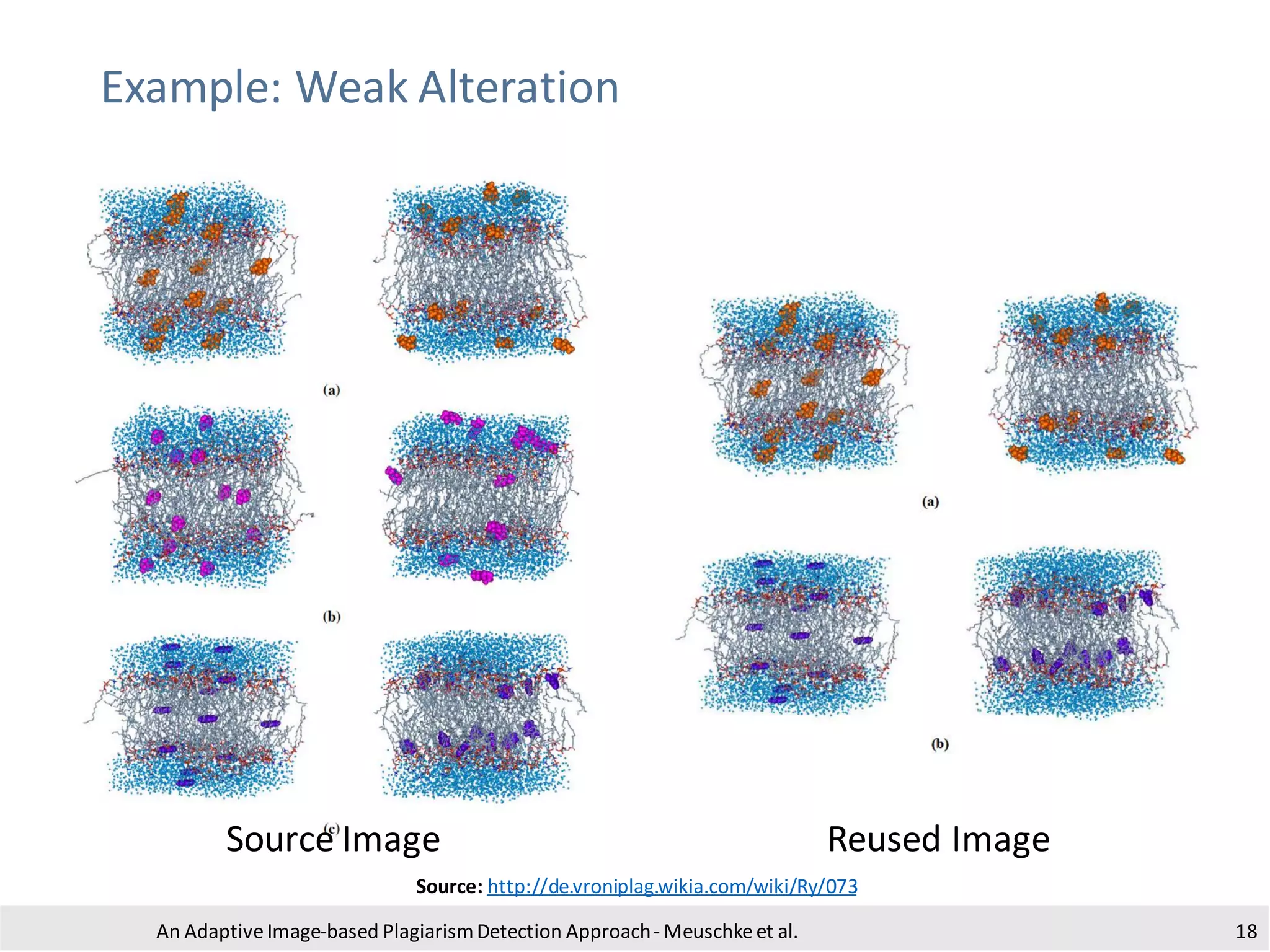
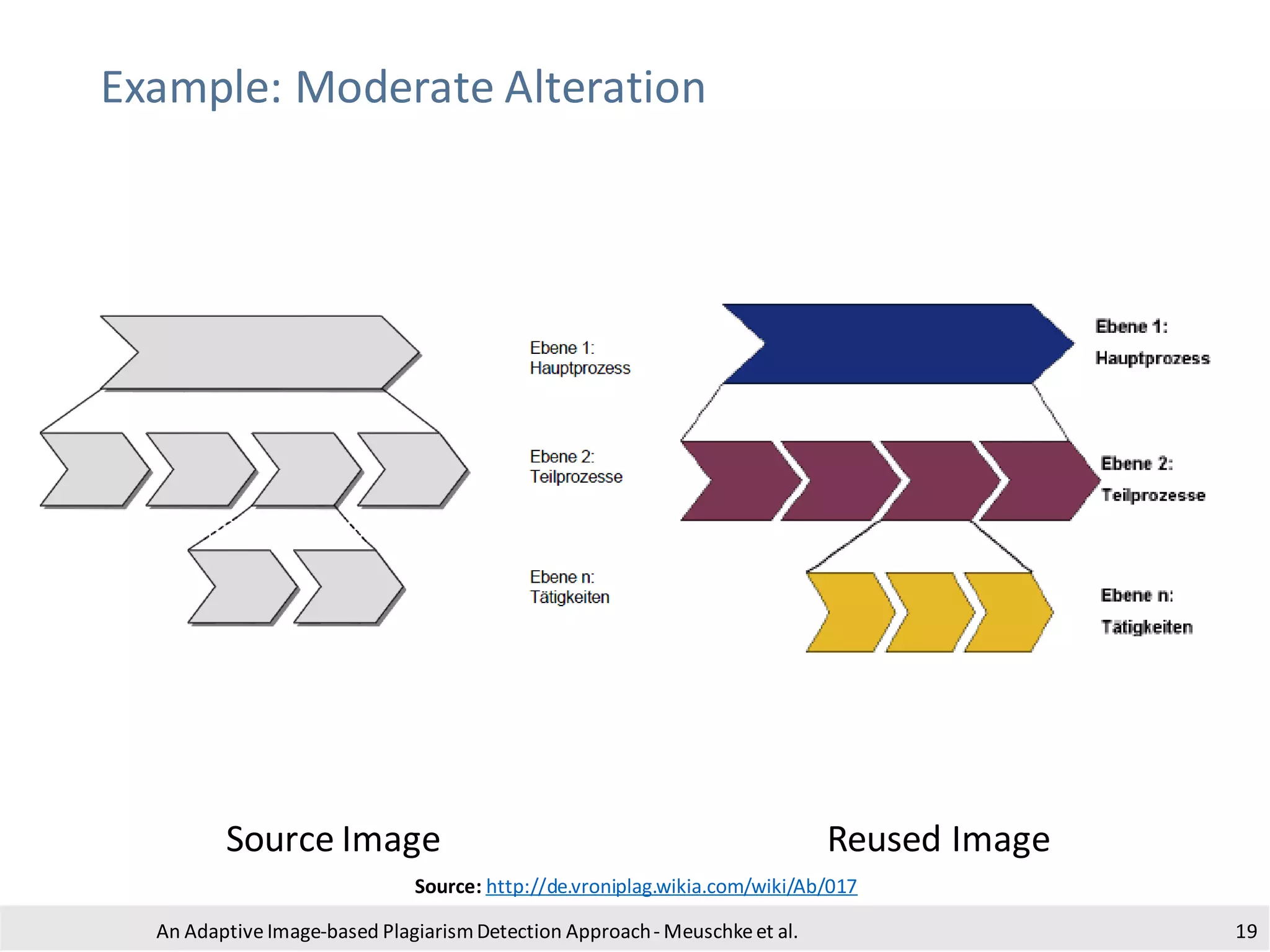
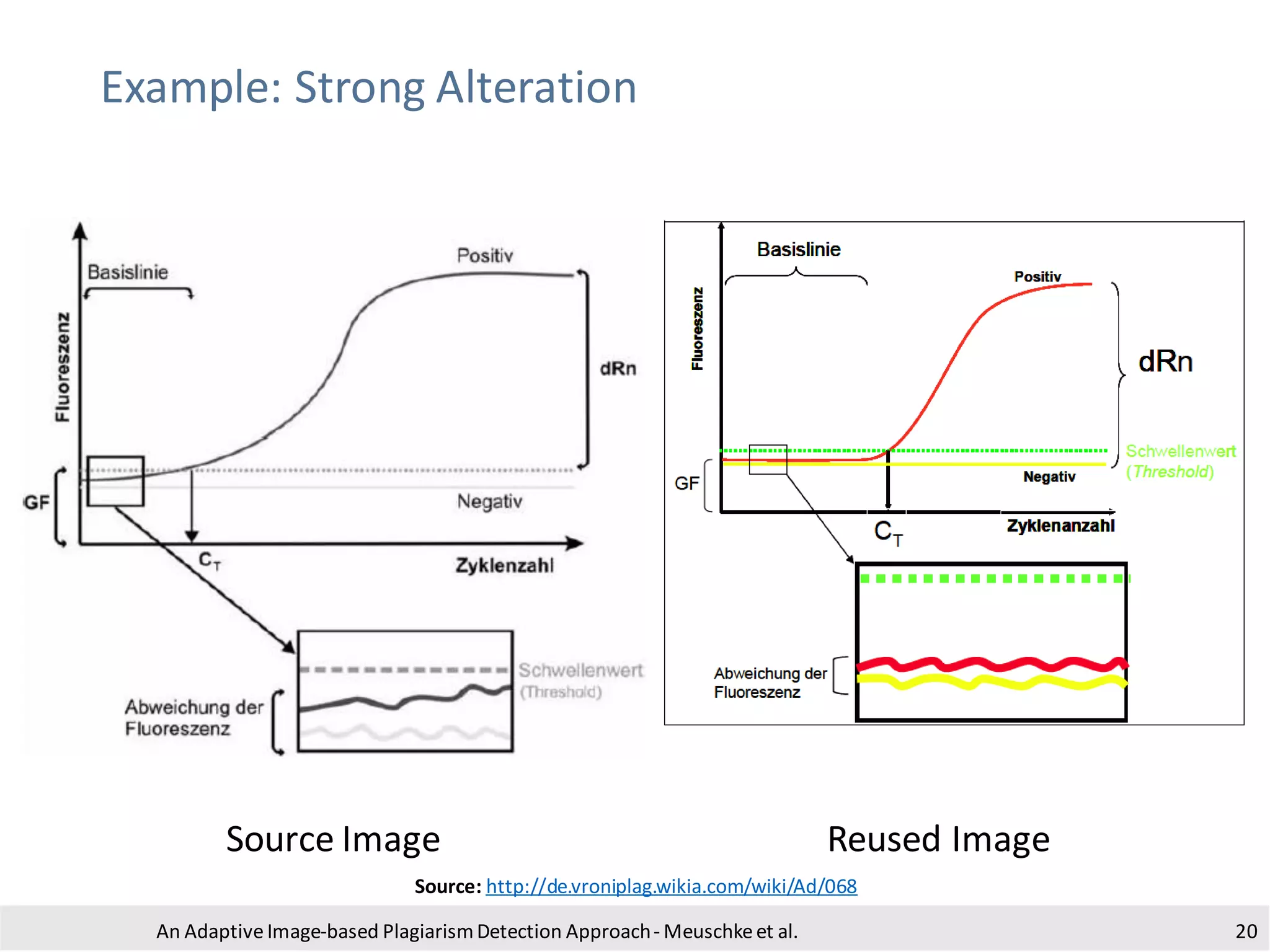
The document presents an adaptive image-based plagiarism detection approach developed by researchers from the University of Konstanz, focusing on analyzing both textual and non-textual elements in academic documents. It identifies various forms of plagiarism, introduces innovative detection methods like perceptual hashing and k-gram text matching, and reports on the effectiveness of these methods in evaluating academic integrity. The study highlights future research directions for improving detection techniques and scalability.




![Decomposition
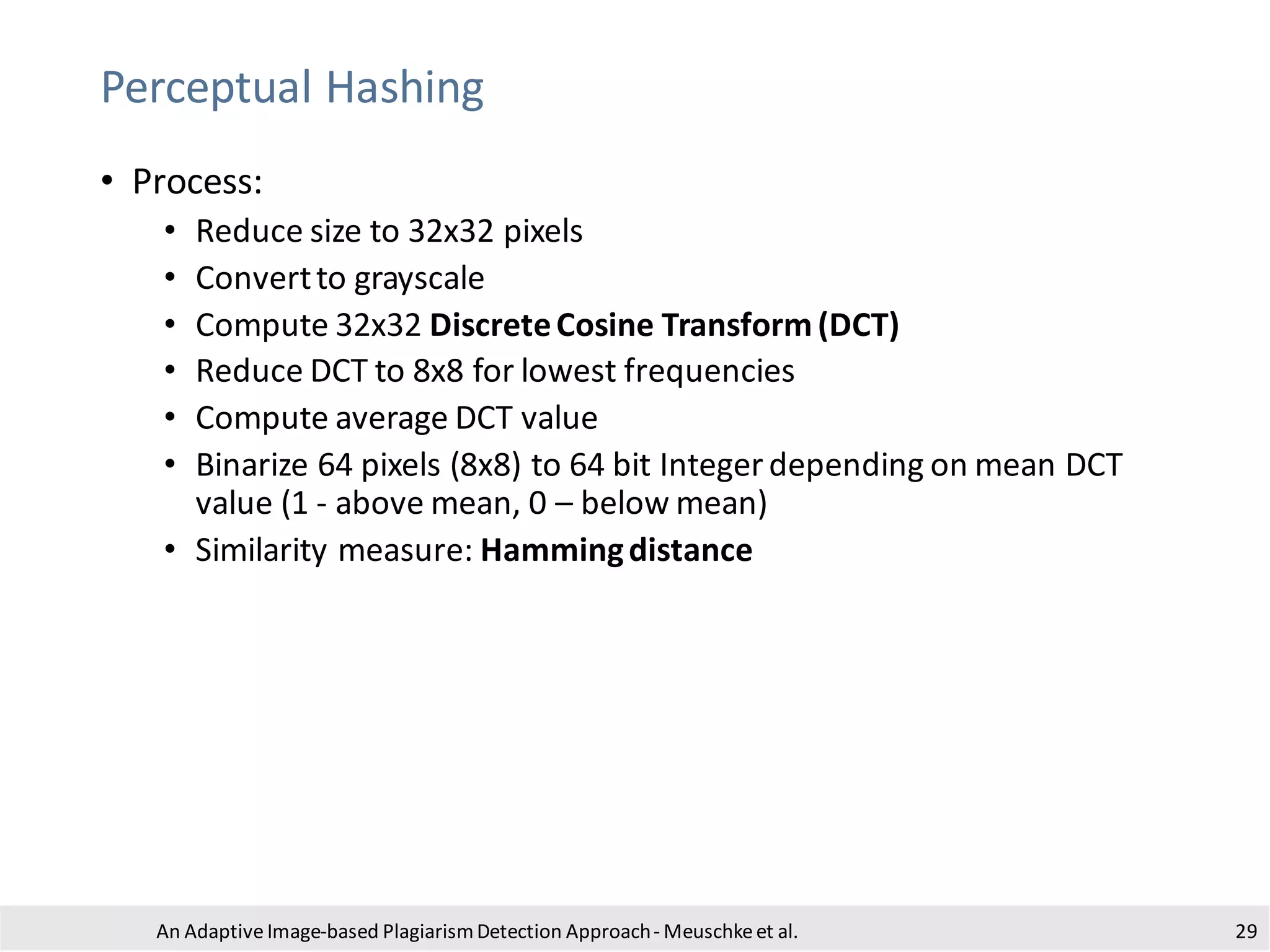
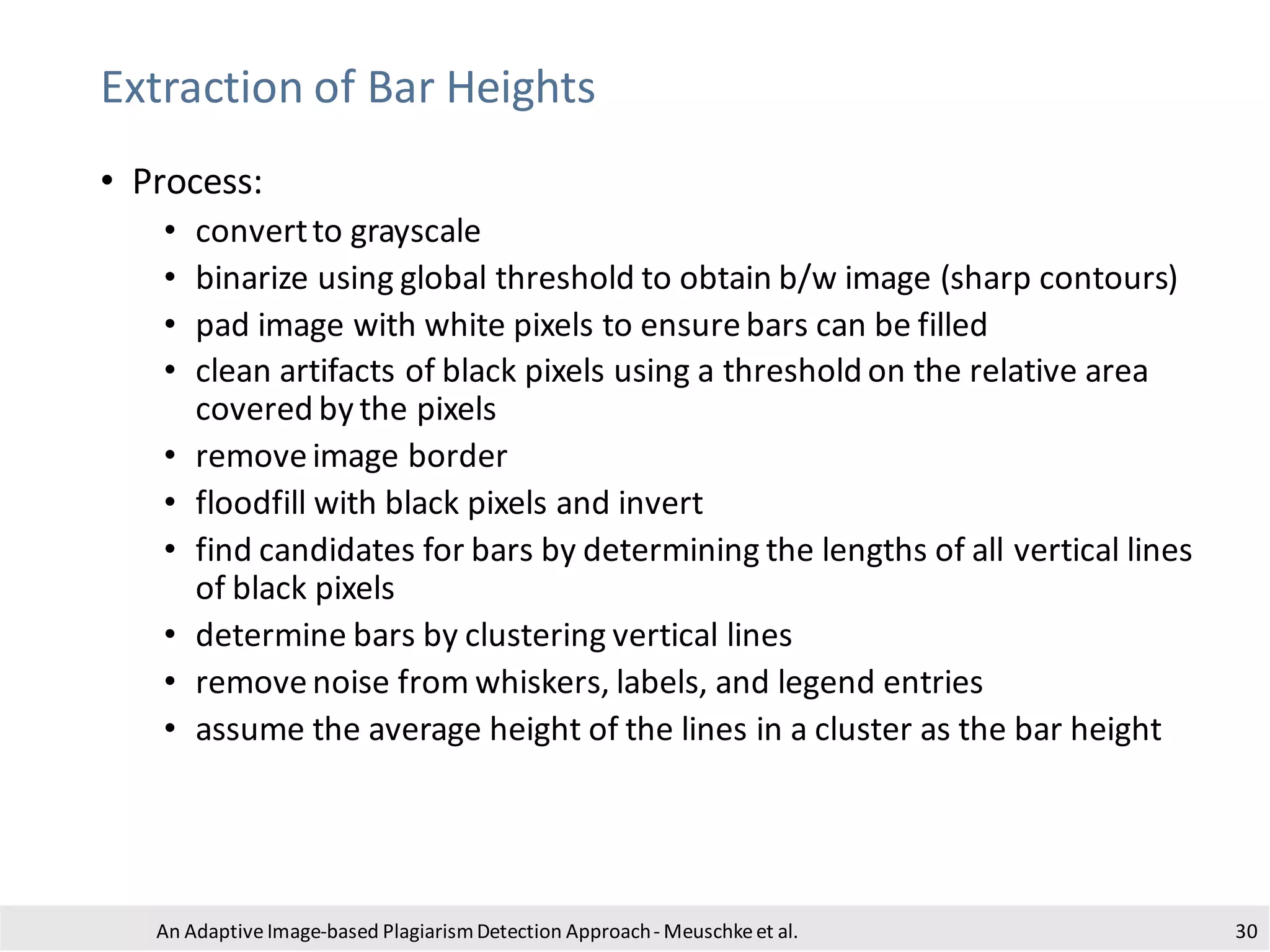
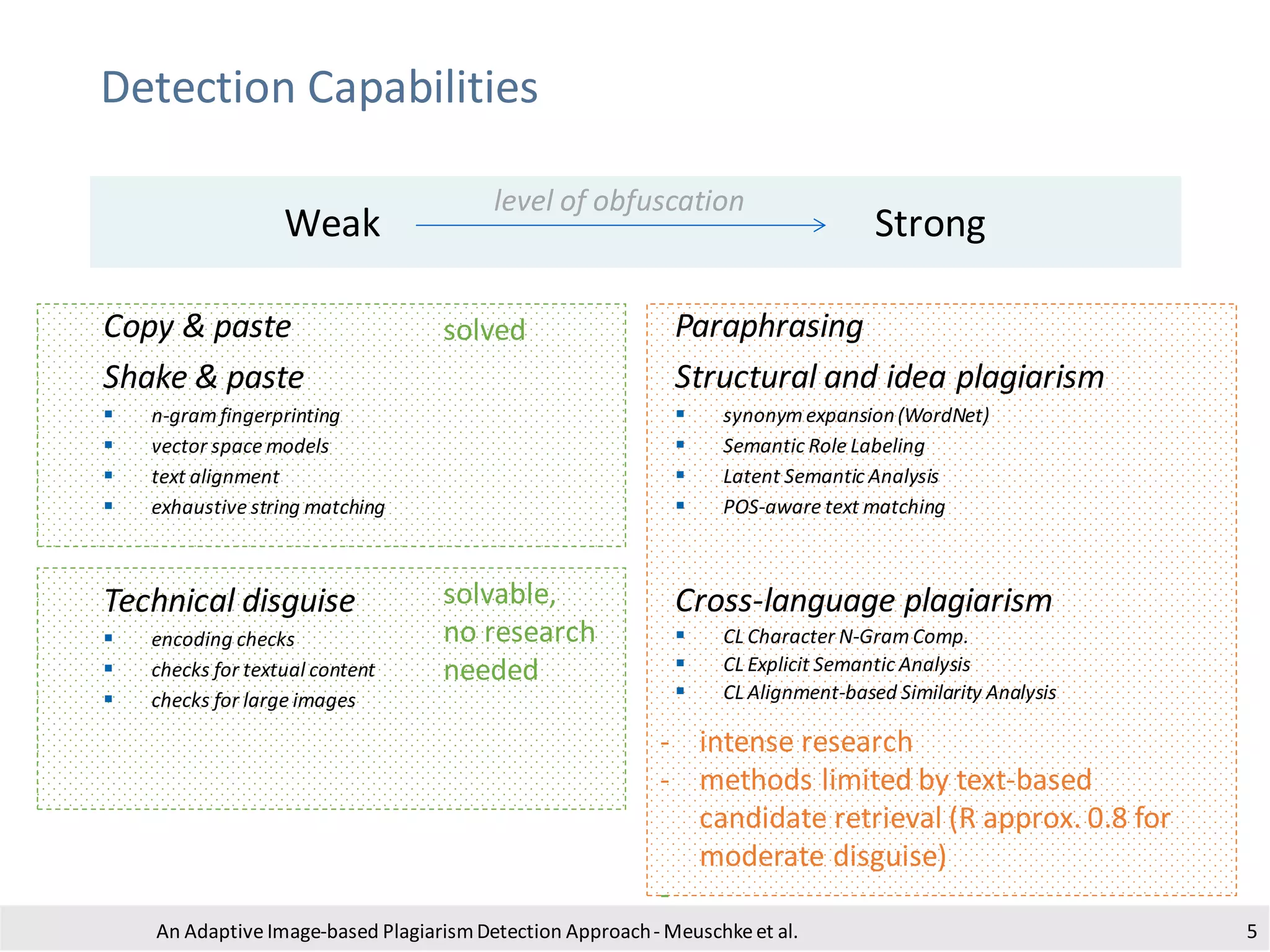
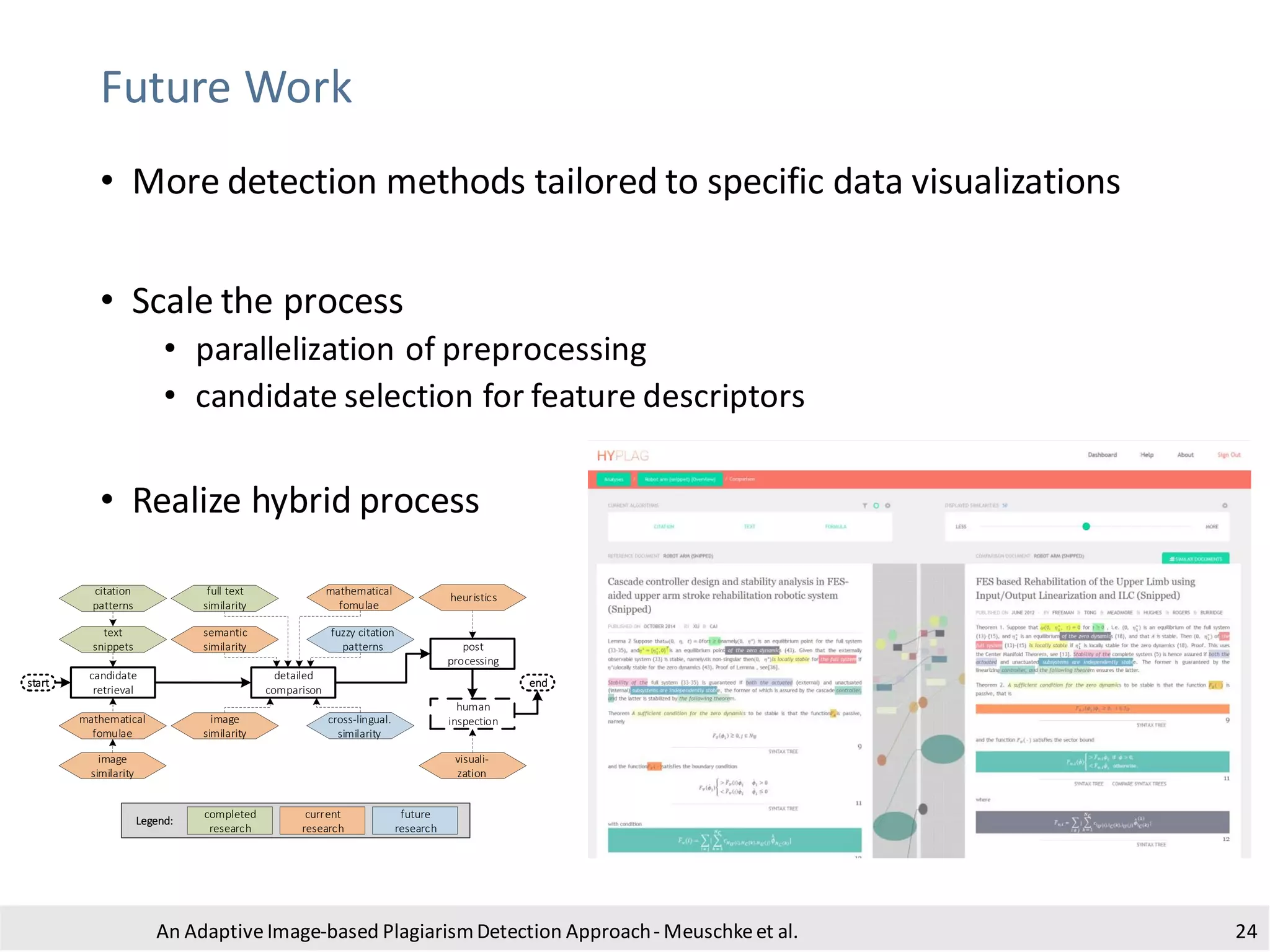
• Process:
• conversionto grayscale to reduceruntime
• padding with white pixels to removea potential border
• binarization using adaptive thresholdingto obtain a b/w image
• dilation to ensureblack pixels are connected
• floodfill of white areas with black pixels
• subtract original image
• invert image
• blob detection using the algorithm of Suzuki and Abe [1]
• estimate boundingbox by looking for large contoursaligned along
the image axes
• crop and store the identified sub-images
[1] Satoshi Suzuki and Keiichi Abe. 1985. Topological Structural Analysis of Digitized Binary Images by
Border Following. CVGIP 30, 1 (1985).
An Adaptive Image-based PlagiarismDetection Approach- Meuschkeet al. 27](https://image.slidesharecdn.com/jcdl18anadaptiveimage-basedplagiarismdetectionapproachnormanmeuschke-180607210411/75/An-Adaptive-Image-based-Plagiarism-Detection-Approach-28-2048.jpg)
![Image Classification
• Depp CNN realized using Caffe and AlexNet architecture [2]
• CNN classifies images into:
• photographs(pHash only)
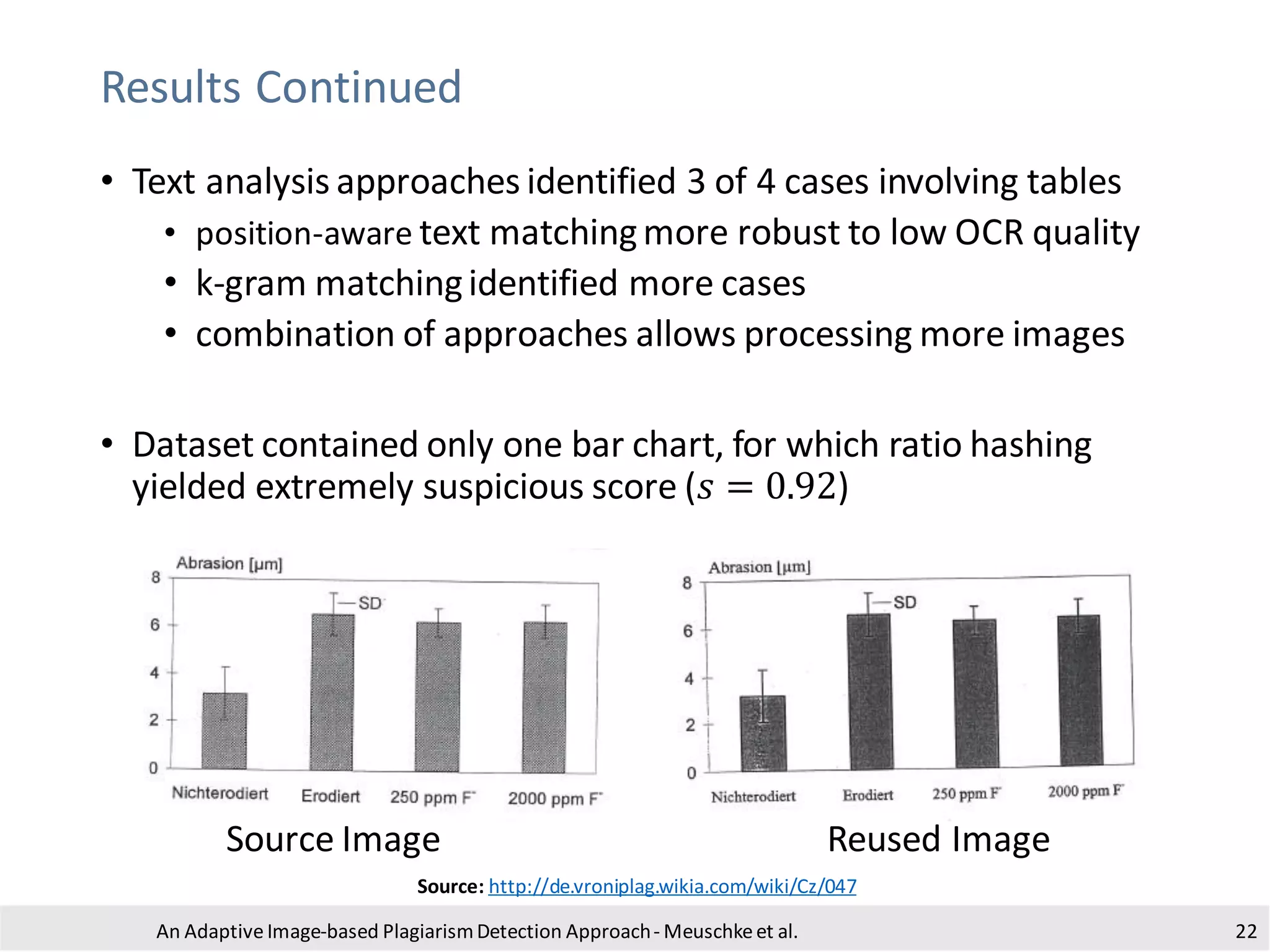
• bar charts (ratio hashing only)
• other image types (pHash and OCR text matching)
• Manual checks of 100 classified images
• Accuracy 0.92 for photographs and 1.00 for bar charts
An Adaptive Image-based PlagiarismDetection Approach- Meuschkeet al. 28](https://image.slidesharecdn.com/jcdl18anadaptiveimage-basedplagiarismdetectionapproachnormanmeuschke-180607210411/75/An-Adaptive-Image-based-Plagiarism-Detection-Approach-29-2048.jpg)